🍃프로그래머스 백엔드 데브코스 4기 교육과정을 듣고 정리한 글입니다.🍃
OAuth
- 애플리케이션에서 사용자가 하나의 계정으로 여러 서비스에 로그인하지 않고도 서로 다른 서비스들 간에 데이터 및 기능을 공유하고 상호 작용할 수 있도록 해줌
주요 용어 4가지
- Resource Owner: 서비스를 이용하는 사용자이자, 리소스 소유자
- Client: 리소스 소유자를 대신하여 보호된 리소스에 액세스하는 응용 프로그램
- 카카오, 네이버를 이용하는 우리가 만들 제 3의 서비스
- Resource Server: 보호받는 리소스를 호스팅하고 액세스 토큰을 사용하는 클라이언트의 요청을 수락하고 응답할 수 있는 서버
- 카카오, 네이버 등의 리소스 서버
- Authorization Server: 클라이언트 및 리소스 소유자를 성공적으로 인증한 후 액세스 토큰을 발급하는 서버
- 카카오, 네이버 등의 인증 서버
Authorization Server에게 토큰을 요청하는 4가지 방법
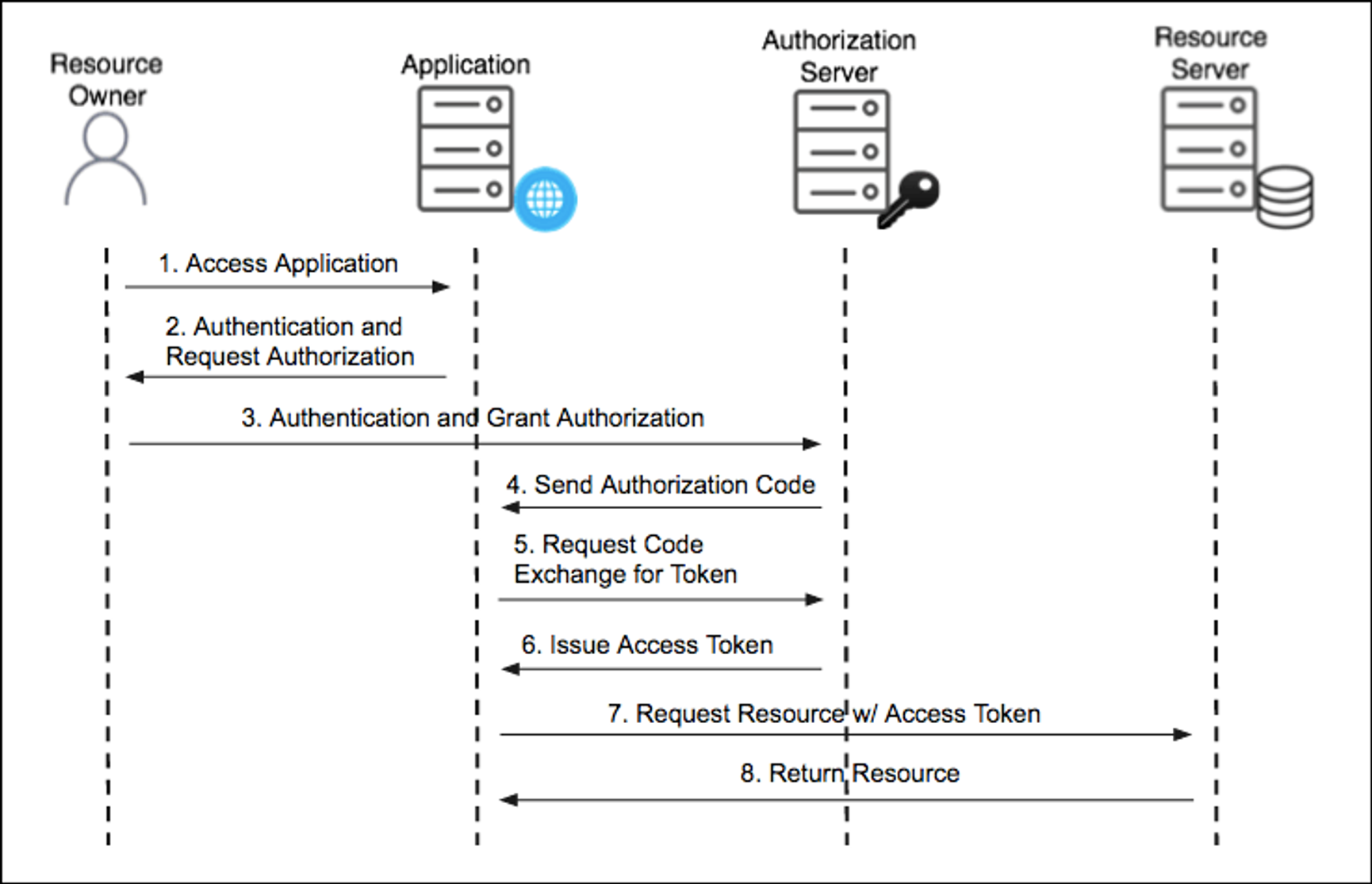
Authorization Code Grant(가장 중요)
- Oauth2.0에서 가장 중요하고, 많이 사용되는 방법이며, 백엔드 서버가 존재하는 웹/모바일 서비스에 적합함
- 사용자 인증 후 Callback을 통해 authorization 코드를 받고, 이를 client-id, client-secret과 함께 Access-Token으로 교환함
- Callback 처리는 백엔드 서버에서 이루어지기 때문에, Access-Token이 외부에 노출되지 않아서 보안상 안전
Implicit Grant
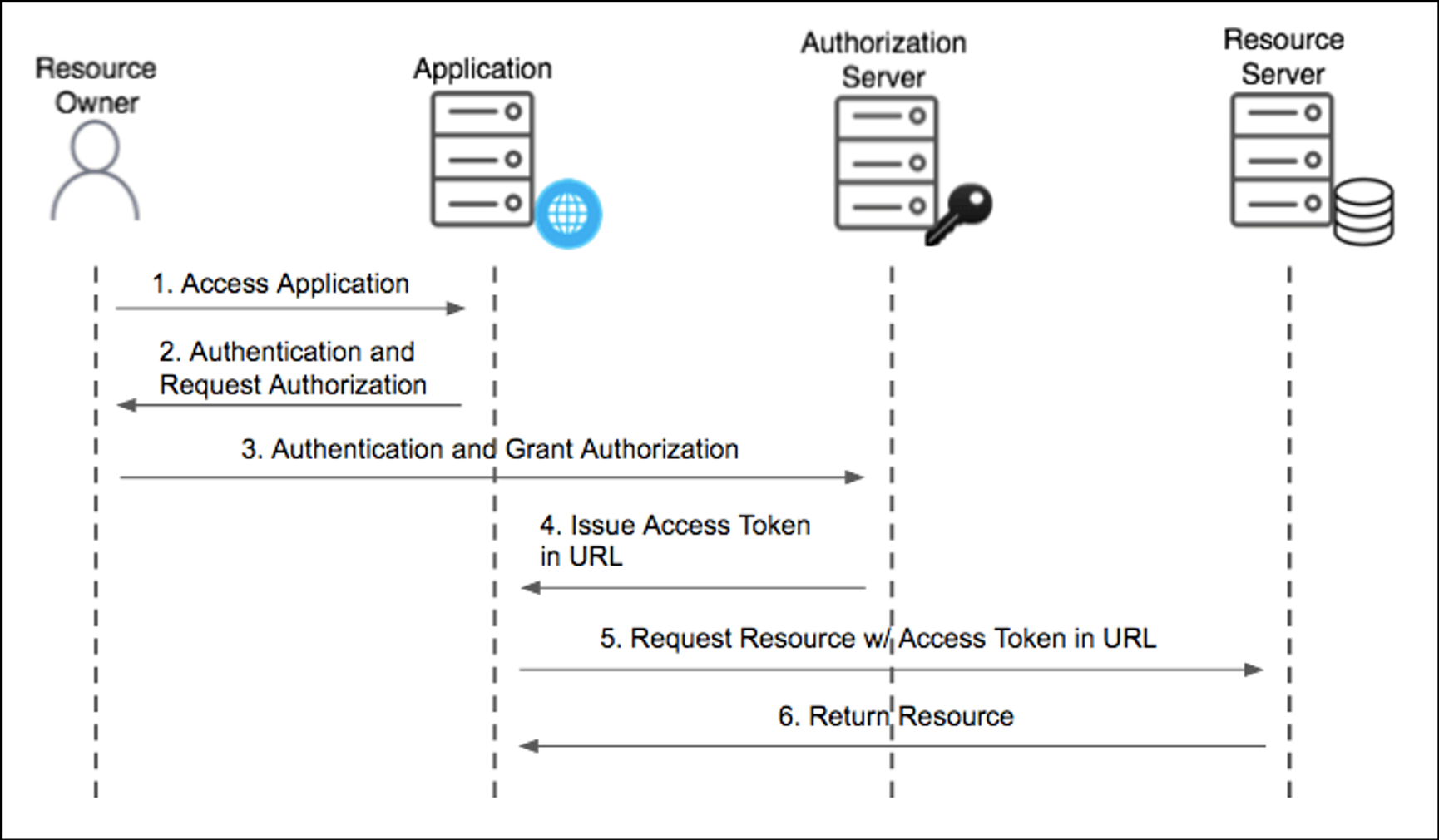
- Authorization Code Grant 방식과 비교했을 때, Authorization Response 단계에서 Access-Token이 전달되고 Token Request 단계가 생략됨
- Access-Token이 URL에 노출되기 때문에 보안상 리스크가 있음
- 백엔드 서버가 없는 제한적인 환경에서만 사용을 권장함
- 브라우저에서 자바스크립트와 같은 스크립트 언어로 동작하는 클라이언트
Client Credentials Grant
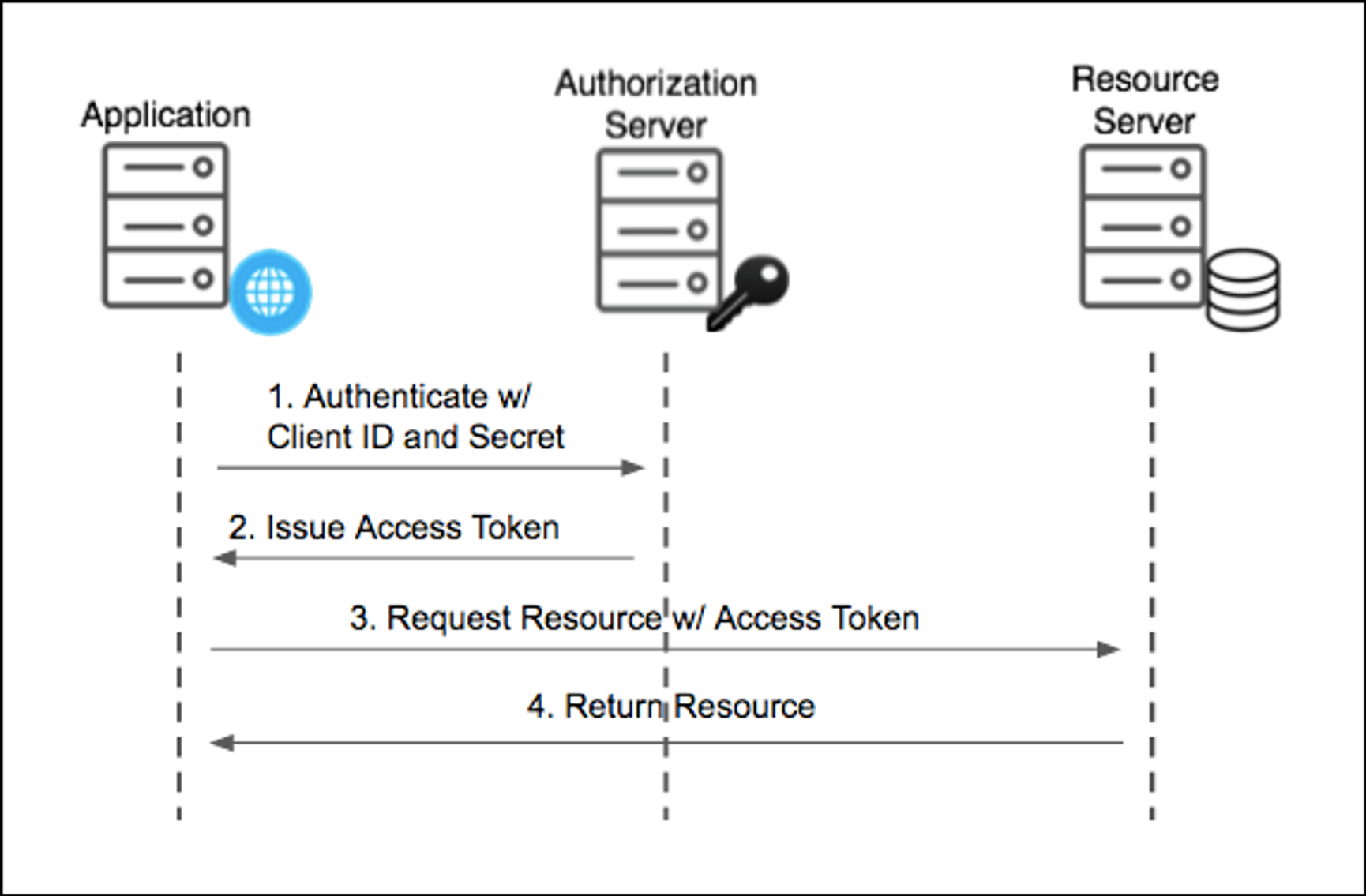
- client_id, client_secret 파리미터만 가지고 Access-Token을 발급할 수 있으며, 사용자는 전혀 관여하지 않음
- 사용자의 직접적인 상호 작용 없이 백그라운드에서 실행해야 하는 서버 간 상호 작용에 사용
Resource Owner Password Credentials Grant
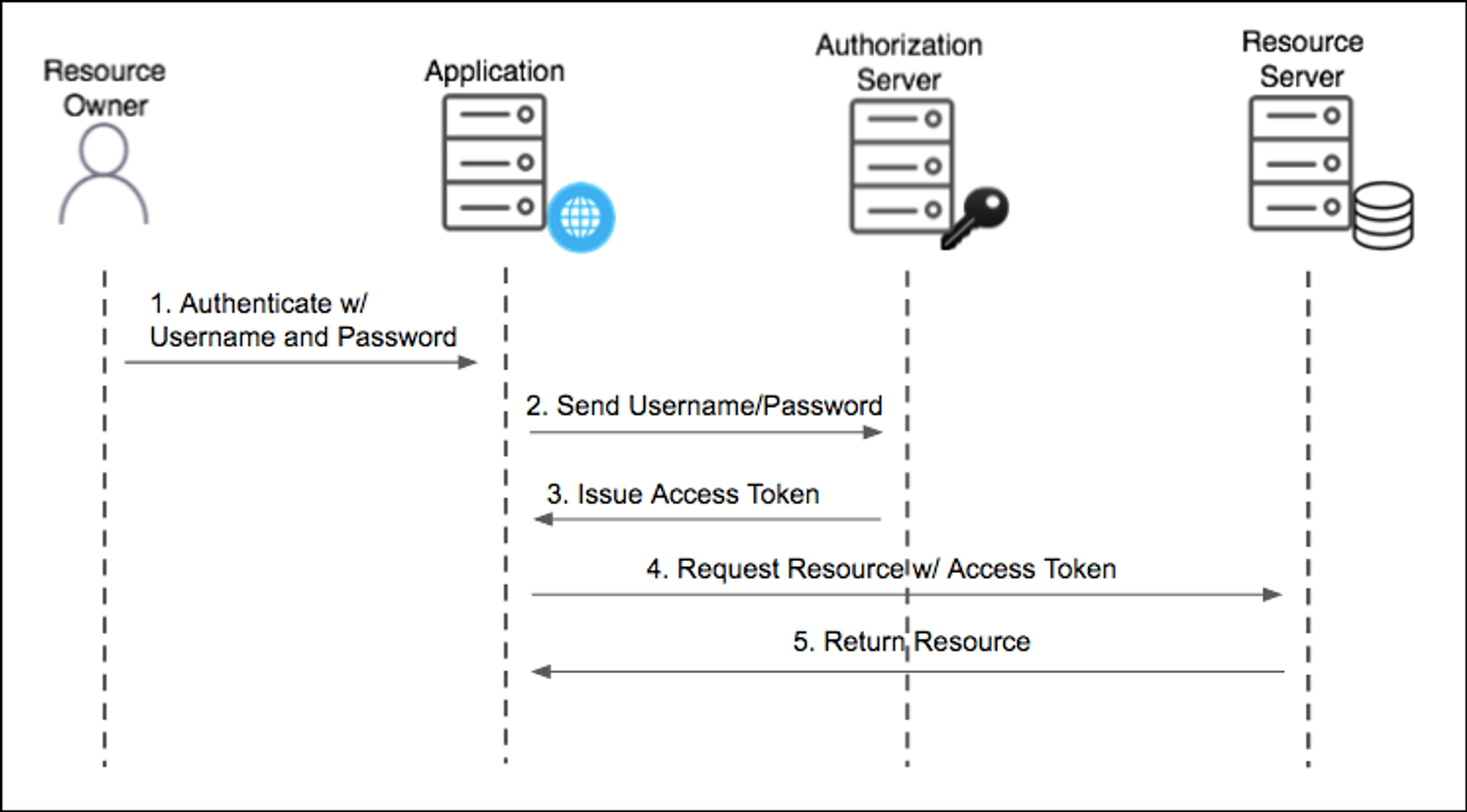
- Client Credentials Grant 방식과 매유 유사하지만, client_id, client_secret 대신 사용자 비밀번호로 인증됨
- 즉, 일반 로그인 아이디/비밀번호 인증
- 클라이언트를 완전히 신뢰할 수 있을 때 사용
Spring Security OAuth2.0 Client (카카오 인증 연동)
카카오 Application 생성
-
카카오 개발자 사이트에서 어플리케이션을 하나 등록함
- 요약 정보의 REST API 키 값을 OAuth2.0에서 client_id 값으로 사용됨
-
카카오 로그인 설정을 활성화하고, Redirect URI 부분에
http://localhost:8080/login/oauth2/code/kakao주소를 입력 -
동의 항목 설정에서 profile_nickname, profile_image 필드를 필수 동의로 설정
- 해당 값은 scope 값으로 사용됨
-
보안 설정에서 Client Secret을 활성화하고, 코드를 생성
- 해당 값은 client_secret 값으로 사용됨
Spring Security OAuth2.0 의존성 추가 및 설정
implementation 'org.springframework.boot:spring-boot-starter-oauth2-client'- gradle 파일에 oauth2 의존성 추가
spring:
security:
oauth2:
client:
registration:
kakao:
client-name: kakao
client-id: e77125b43bb728c04d2f3a40bc2db4a0
client-secret: xyqgyjDW66KF0FAYxjGxZlJGVAg3Jwtz
scope: profile_nickname, profile_image
redirect-uri: "http://localhost:8080/login/oauth2/code/{registrationId}"
authorization-grant-type: authorization_code
client-authentication-method: client_secret_post
provider:
kakao:
authorization-uri: https://kauth.kakao.com/oauth/authorize
token-uri: https://kauth.kakao.com/oauth/token
user-info-uri: https://kapi.kakao.com/v2/user/me
user-name-attribute: id- redirect-uri: 카카오 로그인 설정에서 입력한 Redirect URI 주소의 마지막 부분은 kakao 대신, {registrationId} 변수로 처리
- authorization-uri: 액세스 토큰 발급을 위해서 사전에 1회성 인증 코드를 받기 위한 api
- token-uri: authorization-uri를 통해서 받은 1회성 인증 코드를 이용해 엑세스 토큰을 발급 받기 위한 api
- user-info-uri: 액세스 토큰을 이용해서 카카오에서 사용자 정보를 가져오기 위한 api
- user-name-attribute: user-info-uri를 통해서 카카오 사용자의 정보를 가져왔을때 사용자의 고유 식별키를 추출하기 위한 식별키 필드명
- 카카오 OAuth 공식 문서
public class OAuth2AuthenticationSuccessHandler extends SavedRequestAwareAuthenticationSuccessHandler {
//필드 생략
public OAuth2AuthenticationSuccessHandler(Jwt jwt, UserService userService) {
this.jwt = jwt;
this.userService = userService;
}
@Override
public void onAuthenticationSuccess(HttpServletRequest request, HttpServletResponse response, Authentication authentication) throws ServletException, IOException {
if (authentication instanceof OAuth2AuthenticationToken) {
OAuth2AuthenticationToken oauth2Token = (OAuth2AuthenticationToken) authentication;
OAuth2User principal = oauth2Token.getPrincipal();
String registrationId = oauth2Token.getAuthorizedClientRegistrationId();
User user = processUserOAuth2UserJoin(principal, registrationId);
String loginSuccessJson = generateLoginSuccessJson(user);
response.setContentType("application/json;charset=UTF-8");
response.setContentLength(loginSuccessJson.getBytes(StandardCharsets.UTF_8).length);
response.getWriter().write(loginSuccessJson);
} else {
super.onAuthenticationSuccess(request, response, authentication);
}
}
//private 메서드 생략
}- 카카오 인증이 완료되었을 때 후처리를 담당할 AuthenticationSuccessHandler 인터페이스 구현체 추가
- 카카오 인증이 완료된 사용자가 신규 사용자라면 사용자를 가입 시킴
- 서비스 접근을 위한 JWT 토큰 생성 및 응답
- 위의 코드에서는 단순히 JSON 포맷으로 응답을 생성하지만, 앱 연동을 위해 앱 전용 스킴을 설계하고 데이터를 전달할 수 있음
@Service
public class UserService {
// ... 생략 ...
@Transactional
public User join(OAuth2User oauth2User, String provider) {
checkArgument(oauth2User != null, "oauth2User must be provided.");
checkArgument(isNotEmpty(provider), "authorizedClientRegistrationId must be provided.");
String providerId = oauth2User.getName();
return findByProviderAndProviderId(provider, providerId)
.map(user -> {
log.warn("Already exists: {} for (provider: {}, providerId: {})", user, provider, providerId);
return user;
})
.orElseGet(() -> {
Map<String, Object> attributes = oauth2User.getAttributes();
@SuppressWarnings("unchecked")
Map<String, Object> properties = (Map<String, Object>) attributes.get("properties");
checkArgument(properties != null, "OAuth2User properties is empty");
String nickname = (String) properties.get("nickname");
String profileImage = (String) properties.get("profile_image");
Group group = groupRepository.findByName("USER_GROUP")
.orElseThrow(() -> new IllegalStateException("Could not found group for USER_GROUP"));
return userRepository.save(
new User(nickname, provider, providerId, profileImage, group)
);
});
}
}- OAuth 2.0을 통한 사용자 인증 및 가입을 처리하는 서비스
- 이미 가입된 사용자일 경우
- findByProviderAndProviderId 메서드를 호출하여 해당 providerId와 authorizedClientRegistrationId로 이미 데이터베이스에 저장된 사용자를 검색
- 검색 결과가 있으면 해당 사용자 정보를 반환하고 로그를 출력
- 새로운 사용자 등록
- 이미 가입된 사용자가 없을 경우, oauth2User 객체에서 사용자 속성을 추출하여 새로운 사용자를 생성 및 저장
- 사용자의 닉네임, 프로필 이미지 등을 추출하여 새로운 User 객체를 생성
- groupRepository를 사용하여 사용자 그룹을 검색하고, 해당 그룹을 사용자에게 할당
- userRepository를 사용하여 새로운 사용자를 저장
@Bean
public OAuth2AuthenticationSuccessHandler oauth2AuthenticationSuccessHandler(Jwt jwt) {
return new OAuth2AuthenticationSuccessHandler(jwt, userService);
}- 위에서 만든 핸들러를 빈으로 등록
@Bean
public SecurityFilterChain filterChain(HttpSecurity http, Jwt jwt) throws Exception {
return http
.oauth2Login(auth -> auth
.successHandler(oauth2AuthenticationSuccessHandler(jwt)))
.addFilterAfter(jwtAuthenticationFilter(jwt), SecurityContextHolderFilter.class)
.build();
} - SecurityFilterChain에 OAuth2AuthenticationSuccessHandler가 설정된 oauth2Login을 등록
Spring Security OAuth2.0 동작
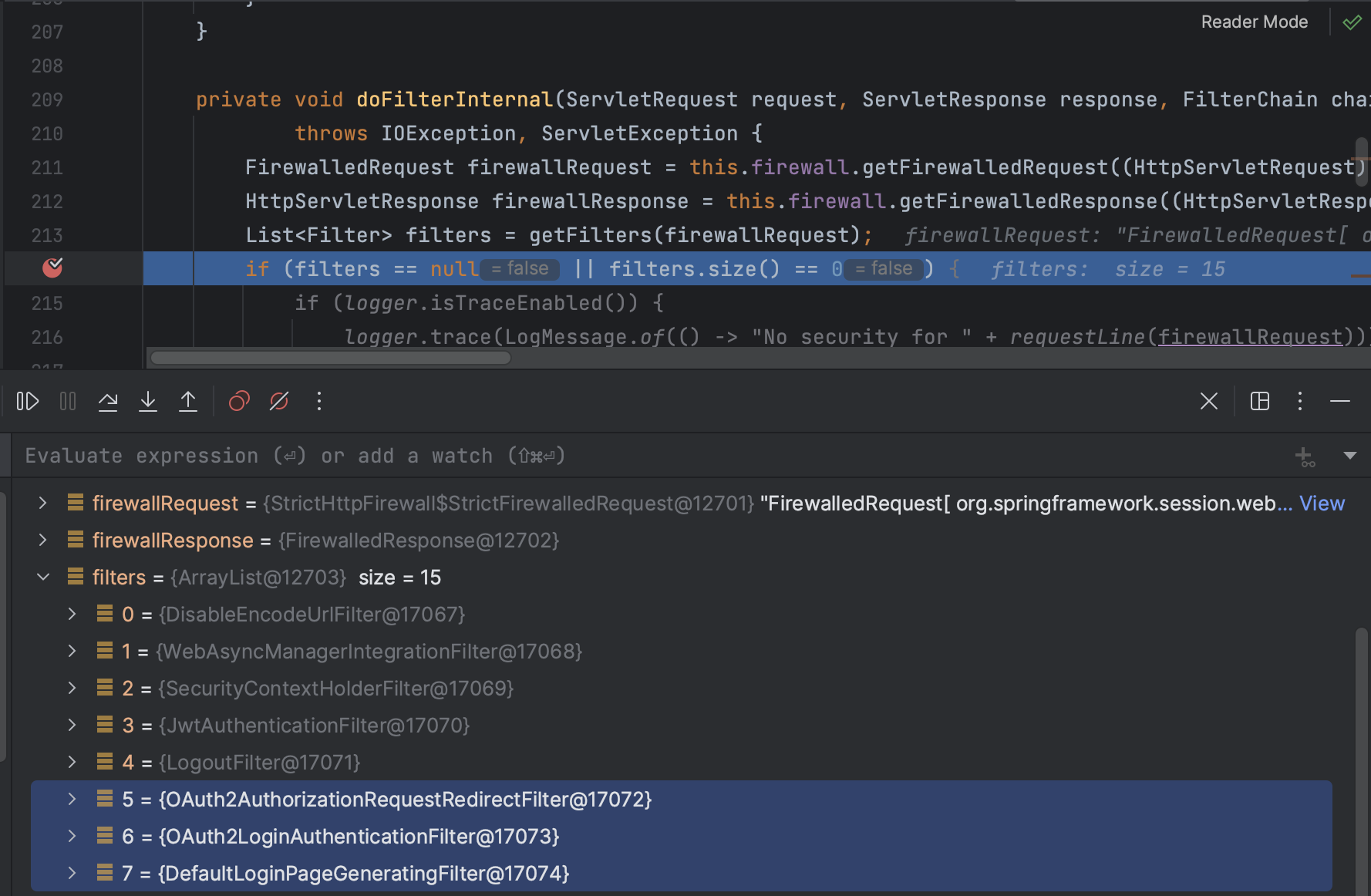
- 지금까지 설정한 애플리케이션을 디버깅하면, filterChainProxy를 살펴보면 이렇게 3개의 필터가 추가되는것을 볼 수 있음
DefaultLoginPageGeneratingFilter
로그인 페이지 생성 필터
- 로그인 전략에 따라 Form 로그인 페이지, OAuth2.0 로그인 페이지 등이 생성됨
- /oauth2/authorization/kakao: 카카오 OAuth 인증 요청 링크
- OAuth2AuthorizationRequestRedirectFilter에서 해당 요청을 처리하게됨
OAuth2AuthorizationRequestRedirectFilter
카카오 인증서버로 사용자를 리다이렉트 시킴
- /oauth2/authorization/{registrationId} 패턴의 URL 요청을 처리함 (기본값)
- {registrationId} 부분에는 인증 Provider 식별키(kakako 같은)가 입력됨
- AuthorizationRequestRepository 인터페이스 구현체에는 application.yml 파일에 설정한 OAuth 연동 정보가 저장되어 있음
- 인증 Provider 식별키로 AuthorizationRequestRepository 인터페이스에서 OAuth 연동 정보를 가져옴
- authorization-uri 주소로 사용자를 리다이렉트 시킴
OAuth2LoginAuthenticationFilter
Authorization Response를 수신하고, Token Request를 인증 서버로 요청
- OAuth2LoginAuthenticationToken
- OAuth2.0 인증 처리를 명시적으로 나타내는 Authentication 인터페이스 구현체
- OAuth2LoginAuthenticationProvider
- OAuth2LoginAuthenticationToken 타입 인증 요청을 처리할 수 있는 AuthenticationProvider 인터페이스 구현체
- Authorization Server에서 Access-Token 및 Refresh-Token을 가져옴
- 발급 받은 Access-Token 을 이용해, 사용자 데이터를 조회해옴: OAuth2User 객체로 표현됨
추가적인 개선
동작 과정
- OAuth2AuthorizationRequestRedirectFilter
- authorizationRequestRepository를 통해 authorizationRequest 저장
- OAuth2LoginAuthenticationFilter
- authorizationRequestRepository를 통해 authorizationRequest 조회
- authorizationRequest 조회가 안되면 오류 처리
authorizationRequestRepository 인터페이스 기본 구현체가 HttpSessionOAuth2AuthorizationRequestRepository 클래스로 Session을 사용하지만, API 서버는 Session을 사용하지 않기 때문에 HttpCookieOAuth2AuthorizationRequestRepository 구현을 추가하여, Session 대신 Cookie을 사용하도록함
public class HttpCookieOAuth2AuthorizationRequestRepository implements AuthorizationRequestRepository<OAuth2AuthorizationRequest> {
private static final String OAUTH2_AUTHORIZATION_REQUEST_COOKIE_NAME = "OAUTH2_AUTHORIZATION_REQUEST";
private final String cookieName;
private final int cookieExpireSeconds;
public HttpCookieOAuth2AuthorizationRequestRepository() {
this(OAUTH2_AUTHORIZATION_REQUEST_COOKIE_NAME, 180);
}
public HttpCookieOAuth2AuthorizationRequestRepository(String cookieName, int cookieExpireSeconds) {
this.cookieName = cookieName;
this.cookieExpireSeconds = cookieExpireSeconds;
}
@Override
public OAuth2AuthorizationRequest loadAuthorizationRequest(HttpServletRequest request) {
return getCookie(request)
.map(this::getOAuth2AuthorizationRequest)
.orElse(null);
}
@Override
public void saveAuthorizationRequest(OAuth2AuthorizationRequest authorizationRequest, HttpServletRequest request, HttpServletResponse response) {
if (authorizationRequest == null) {
getCookie(request).ifPresent(cookie -> clear(cookie, response));
} else {
String value = Base64.getUrlEncoder().encodeToString(SerializationUtils.serialize(authorizationRequest));
Cookie cookie = new Cookie(cookieName, value);
cookie.setPath("/");
cookie.setHttpOnly(true);
cookie.setMaxAge(cookieExpireSeconds);
response.addCookie(cookie);
}
}
@Override
public OAuth2AuthorizationRequest removeAuthorizationRequest(HttpServletRequest request, HttpServletResponse response) {
return getCookie(request)
.map(cookie -> {
OAuth2AuthorizationRequest oauth2Request = getOAuth2AuthorizationRequest(cookie);
clear(cookie, response);
return oauth2Request;
})
.orElse(null);
}
private Optional<jakarta.servlet.http.Cookie> getCookie(HttpServletRequest request) {
return ofNullable(WebUtils.getCookie(request, cookieName));
}
private void clear(Cookie cookie, HttpServletResponse response) {
cookie.setValue("");
cookie.setPath("/");
cookie.setMaxAge(0);
response.addCookie(cookie);
}
private OAuth2AuthorizationRequest getOAuth2AuthorizationRequest(Cookie cookie) {
return SerializationUtils.deserialize(
Base64.getUrlDecoder().decode(cookie.getValue())
);
}
}OAuth2LoginAuthenticationFilter 구현의 마지막 부분에서 OAuth2AuthorizedClient (OAuth2.0인증 완료된 사용자 정보) 저장
- authorizedClientRepository 기본 구현체가 AuthenticatedPrincipalOAuth2AuthorizedClientRepository 클래스이며 내부적으로 InMemoryOAuth2AuthorizedClientService 클래스를 사용해 OAuth2AuthorizedClient 객체를 저장함
- 따라서, OAuth2.0 으로 인증되는 클라이언트가 많아지면 OOME 발생 가능성이 있음
- 또한 인증된 사용자 정보가 특정 서버 메모리에만 저장되고 있기 때문에 특정 서버 장애 발생 시 사이드 이펙트가 발생할 수 있음
- 다행히 InMemoryOAuth2AuthorizedClientService 클래스는 OAuth2AuthorizedClientService 인터페이스 구현체이며, InMemoryOAuth2AuthorizedClientService 를 대체할 수 있는 JdbcOAuth2AuthorizedClientService 클래스가 있음
최종 Configuration 설정
설정 변경 부분
- HttpCookieOAuth2AuthorizationRequestRepository -> HttpSessionOAuth2AuthorizationRequestRepository Bean을 대체
- JdbcOAuth2AuthorizedClientService -> InMemoryOAuth2AuthorizedClientService Bean을 대체
- AuthenticatedPrincipalOAuth2AuthorizedClientRepository -> JdbcOAuth2AuthorizedClientService 의존성 주입
코드
@Bean
public AuthorizationRequestRepository<OAuth2AuthorizationRequest> authorizationRequestRepository() {
return new HttpCookieOAuth2AuthorizationRequestRepository();
}
@Bean
public OAuth2AuthorizedClientService authorizedClientService(JdbcOperations jdbcOperations, ClientRegistrationRepository clientRegistrationRepository) {
return new JdbcOAuth2AuthorizedClientService(jdbcOperations, clientRegistrationRepository);
}
@Bean
public OAuth2AuthorizedClientRepository oAuth2AuthorizedClientRepository(OAuth2AuthorizedClientService authorizedClientService) {
return new AuthenticatedPrincipalOAuth2AuthorizedClientRepository(authorizedClientService);
}
@Bean
public SecurityFilterChain filterChain(HttpSecurity http, Jwt jwt, OAuth2AuthorizedClientService authorizedClientService) throws Exception {
return http
//생략
.oauth2Login(auth -> auth
.successHandler(oauth2AuthenticationSuccessHandler(jwt))
.authorizationEndpoint(authorizationEndpointConfig -> authorizationEndpointConfig.authorizationRequestRepository(authorizationRequestRepository()))
.authorizedClientRepository(oAuth2AuthorizedClientRepository(authorizedClientService)))
.addFilterAfter(jwtAuthenticationFilter(jwt), SecurityContextHolderFilter.class)
.build();
}