[8/9 TIL] SPRING SECURITY(Stateful, Stateless, JWT, REST API with JWT, JwtAuthenticationFilter)
프로그래머스 백엔드 데브코스 4기
목록 보기
38/40
🍃프로그래머스 백엔드 데브코스 4기 교육과정을 듣고 정리한 글입니다.🍃
Stateful, Stateless
Stateful 아키텍처
- Session을 사용하고 있으면, Stateful 하다고 할 수 있음
- 수평확장(Scale-Out) 과정이 쉽지 않음
- Session Cluster 반드시 필요
- Session Cluster의 장애 또는 성능 병목이 서비스 전체에 큰 영향을 줄수 있음
- 단일 사용자의 다중 로그인 컨트롤, 사용자 유효성 체크, 강제 로그아웃 기능 구현이 쉬움
Stateless 아키텍처
- Session을 전혀 사용하지 않아야함
- HTTP 프로토콜 자체가 Stateless
- 수평확장이 매우 쉬움
- Session Cluster 필요 없음
- 단일 사용자의 다중 로그인 컨트롤, 사용자 유효성 체크, 강제 로그아웃 기능 구현이 어려움
- 완전한 Stateless 아키텍처 기반으로 유의미한 서비스 개발이 어려움
- 완전한 Stateless 서비스는 정적 리소스(html, css, javascript, 이미지 등)를 AWS S3로 서비스 하는데 적합함
- 서버는 어떤식으로는 사용자를 식별할 수 있어야 함 (단, Session 사용 금지)
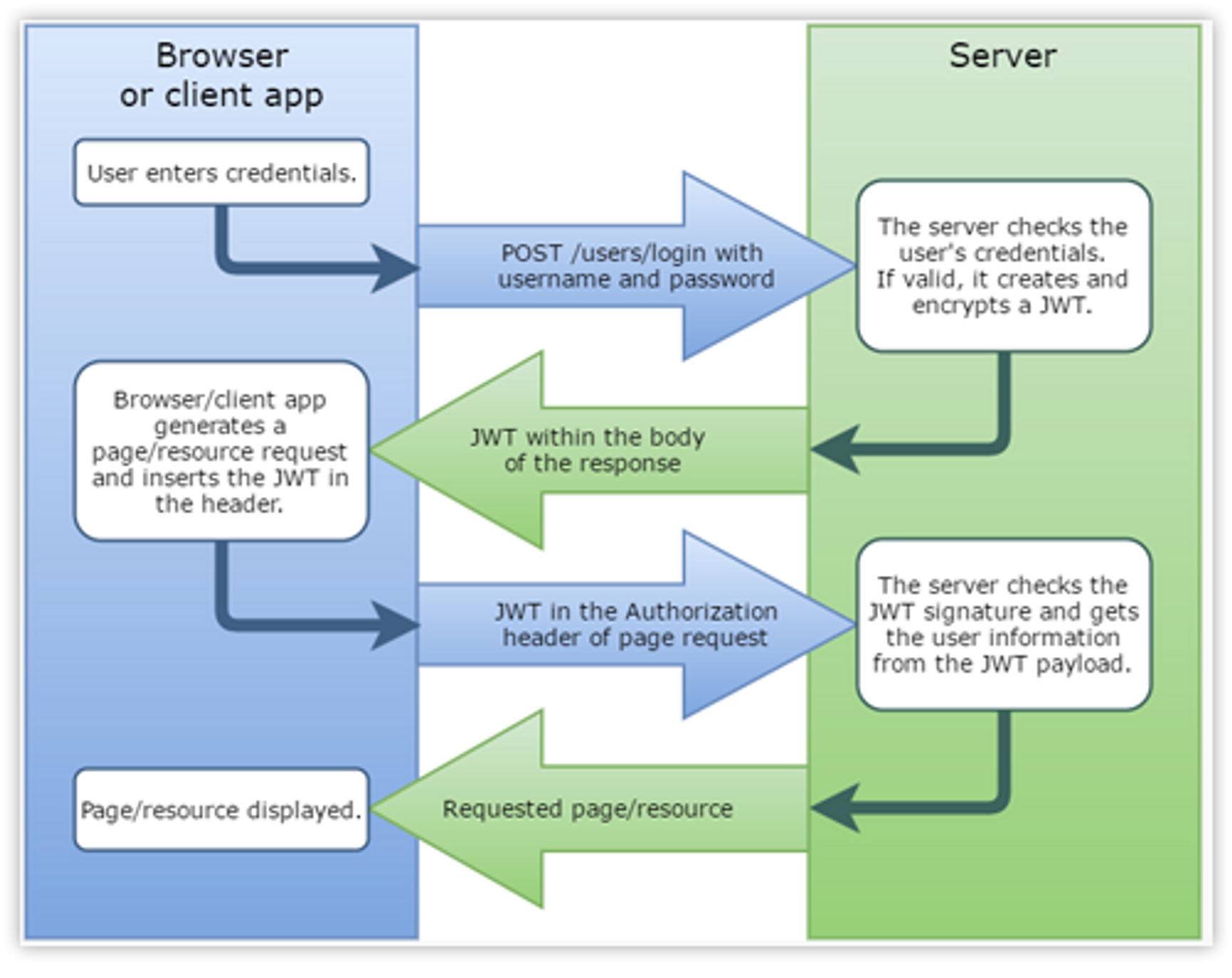
JWT (Json Web Token)
- JWT는 Stateless 상태를 유지하며, 서버에서 사용자를 식별할 수 있는 수단을 제공
- 동작 과정
- 서버에서 사용자가 성공적으로 인증되면 JWT를 반환함
- 클라이언트는 JWT를 로컬 영역에 저장하고, 이후 서버에 요청을 보낼 때 JWT를 HTTP 헤더에 포함시킴
- 서버는 클라이언트가 전달한 JWT를 통해 사용자를 식별할 수 있음
JWT 개요
-
자체 포함형 (Self-Contained): JWT는 토큰에 필요한 모든 정보를 내부에 포함하여 저장
- 토큰에 대한 메타정보(토큰 타입, 사용된 해시 알고리즘), 사용자 정의 데이터 및 토큰 유효성 검증을 위한 데이터 등을 포함함
-
인터넷 전달 용이성: JWT는 URL-Safe한 텍스트로 구성되어 있어 HTTP 프로토콜의 어느 위치에든 쉽게 전달 가능
- 일반적으로 HTTP 헤더에 포함되어 사용
-
위변조 검증 가능: JWT는 데이터의 무결성을 보장하기 위해 서명(Signature)을 포함하며, 이 서명을 통해 토큰이 위변조되지 않았음을 검증
- 토큰의 내용이 수정되면 서명이 무효화되므로 위변조 여부를 확인
JWT 구조
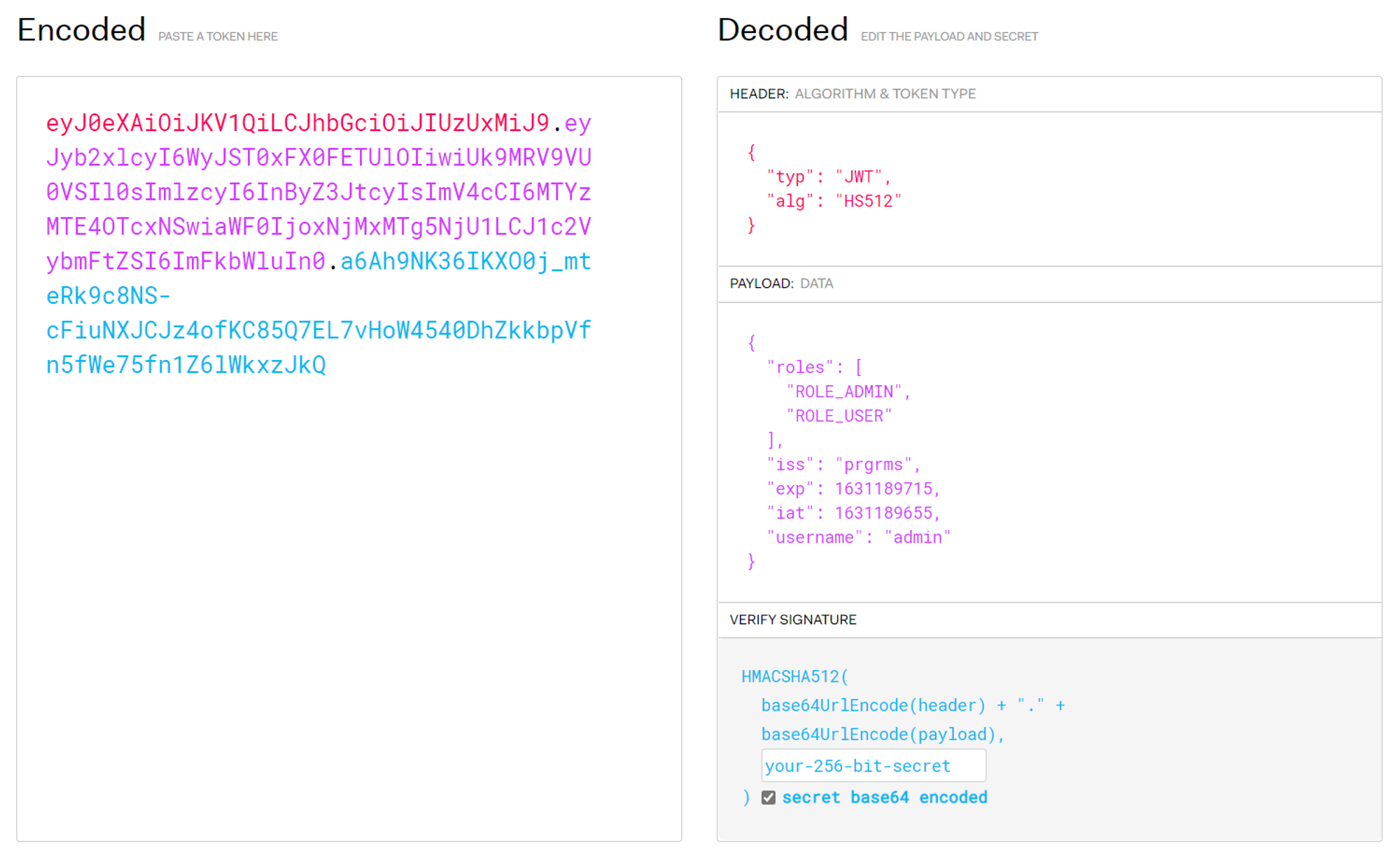
- Header, Payload, Signature 세 부분으로 구성됨
- Header, Payload, Signature 세 부분을 Base64 Url-Safe 방식으로 인코딩하고 dot(.)을 구분자로 결합함
- Header: JWT를 검증하는데 필요한 정보를 담고 있음 (토큰 타입, 사용된 알고리즘)
- 알고리즘은 HMAC, RSA 방식을 지원
- 위의 그림에서 HS512는 HMAC using SHA-512를 의미
- HMAC 알고리즘에서 비밀키는 최소한 알고리즘의 서명 길이만큼의 비트를 가지고 있어야함 (HS512 — 64byte)
- Payload: JWT를 통해 전달하고자 하는 데이터, Claim-Set(Key-Value) 이라고 함
- JWT 자체는 암호화되는 것이 아니기 때문에 민감정보를 포함해서는 안됨
- Reserved Claims, Public Claims, Custom Claims 으로 구분됨
- Reserved Claims: 미리 등록된 Claims으로, 필수적으로 사용할 필요는 없지만 사용을 권고함
- iss: 토큰을 발급한 발급자 (Issuer)
- exp: 만료시간이 지난 토큰은 사용불가
- nbf: Not Before의 의미로 해당 시간 이전에는 토큰 사용불가
- iat: 토큰이 발급된 시각
- jti: JWT ID로 토큰에 대한 식별자
- Public Claims: 사용자 마음대로 쓸 수 있으나 충돌 방지를 위해 미리 정의된 이름으로 사용을 권고함
- Custom Claims: 사용자 정의 Claims으로, Reserved, Public 에 정의된 이름과 중복되지 않도록함
- Signature: 토큰 생성 주체만 알고 있는 비밀키를 이용해 헤더에 정의된 알고리즘으로 서명된 값
- 토큰이 위변조 되지 않았음을 증명함
JWT 장단점
-
장점
-
자체 포함형 데이터
- JWT는 필요한 모든 정보를 토큰 자체에 포함
- 서버는 별도의 스토리지나 세션 클러스터를 유지할 필요가 없음
- 이는 수평 확장을 쉽게 할 수 있으며, 서버의 확장성을 향상 시킴
-
Active User 관리 용이성
- 세션을 사용하면 각 Active User마다 세션을 저장해야 하기 때문에 스토리지 관리가 복잡함
- 하지만 JWT는 토큰 자체가 필요한 정보를 포함하므로 스토리지 관리가 훨씬 간단함
-
-
단점
-
토큰 크기 제한
- JWT를 항상 HTTP 요청에 포함해야 하기 때문에 토큰 크기를 작게 유지해야 함
- 토큰이 커지면 네트워크 부하가 증가하며, 이는 성능에 영향을 줄 수 있음
-
강제적인 만료 처리 어려움
- 유효기간이 남아 있는 정상적인 토큰에 대해 강제적으로 만료 처리를 하기 어려움
- 만료된 토큰은 더 이상 유효하지 않지만, 유효기간이 남은 토큰은 계속 사용될 가능성이 있음
-
상태 관리의 어려움
- JWT는 상태를 내부에 포함하지 않기 때문에 토큰 내부의 정보가 변경되면 해당 변경 사항을 효과적으로 업데이트하는 것이 어려움
- 예를 들어, 사용자의 권한이 변경되면 해당 정보가 토큰 내부에 반영되어야 함
-
REST API with JWT
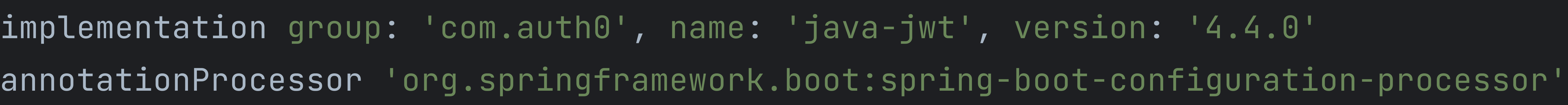
gradle 의존성 추가
yml 설정
@Component
@ConfigurationProperties(prefix = "jwt")
@Data
public class JwtConfigure {
private String header;
private String issuer;
private String clientSecret;
private int expirySeconds;
}- 만료시간을 1분으로 하는 JWT 토큰 설정을 추가
- header: HTTP Header 이름
- issuer: 토큰 발급자
- client-secret: HS512 알고리즘으로 서명을 수행할 것이기 때문에 키 길이를 64바이트로 해야함
- expiry-seconds: 토큰 만료 시간 (초)
Jwt 클래스
public final class Jwt {
private final String issuer;
private final String clientSecret;
private final int expirySeconds;
private final Algorithm algorithm;
private final JWTVerifier jwtVerifier;
public Jwt(String issuer, String clientSecret, int expirySeconds) {
this.issuer = issuer;
this.clientSecret = clientSecret;
this.expirySeconds = expirySeconds;
this.algorithm = Algorithm.HMAC512(clientSecret);
this.jwtVerifier = com.auth0.jwt.JWT.require(algorithm)
.withIssuer(issuer)
.build();
}
public String sign(Claims claims) {
Date now = new Date();
JWTCreator.Builder builder = com.auth0.jwt.JWT.create();
builder.withIssuer(issuer);
builder.withIssuedAt(now);
if (expirySeconds > 0) {
builder.withExpiresAt(new Date(now.getTime() + expirySeconds * 1000));
}
builder.withClaim("username", claims.username);
builder.withArrayClaim("roles", claims.roles);
return builder.sign(algorithm);
}
public Claims verify(String token) throws JWTVerificationException {
return new Claims(jwtVerifier.verify(token));
}
// ... 생략 ...
static public class Claims {/*생략*/}
}- JWT 발행을 위한 sign 메소드
- JWT 검증을 위한 verify 메소드
JwtAuthenticationFilter
구현
public class JwtAuthenticationFilter extends GenericFilterBean {
private final Logger log = LoggerFactory.getLogger(getClass());
private final String headerKey;
private final Jwt jwt;
public JwtAuthenticationFilter(String headerKey, Jwt jwt) {
this.headerKey = headerKey;
this.jwt = jwt;
}
/**
* HTTP 요청 헤더에 JWT 토큰이 있는지 확인
* JWT 토큰이 있다면, 주어진 토큰을 디코딩 하고,
* username, roles 데이터를 추출하고, UsernamePasswordAuthenticationToken 생성
* 이렇게 만들어진 UsernamePasswordAuthenticationToken 참조를 SecurityContext에 넣어줌
*/
@Override
public void doFilter(ServletRequest req, ServletResponse res, FilterChain chain) throws IOException, ServletException {
HttpServletRequest request = (HttpServletRequest) req;
HttpServletResponse response = (HttpServletResponse) res;
if (SecurityContextHolder.getContext().getAuthentication() == null) {
String token = getToken(request);
if (token != null) {
try {
Jwt.Claims claims = verify(token);
log.debug("Jwt parse result: {}", claims);
String username = claims.username;
List<GrantedAuthority> authorities = getAuthorities(claims);
if (isNotEmpty(username) && authorities.size() > 0) {
UsernamePasswordAuthenticationToken authentication = new UsernamePasswordAuthenticationToken(username, null, authorities);
authentication.setDetails(new WebAuthenticationDetailsSource().buildDetails(request));
SecurityContextHolder.getContext().setAuthentication(authentication);
}
} catch (Exception e) {
log.warn("Jwt processing failed: {}", e.getMessage());
}
}
} else {
log.debug("SecurityContextHolder not populated with security token, as it already contained: '{}'", SecurityContextHolder.getContext().getAuthentication());
}
chain.doFilter(request, response);
}
private String getToken(HttpServletRequest request) {
//생략
}
private Jwt.Claims verify(String token) {
return jwt.verify(token);
}
private List<GrantedAuthority> getAuthorities(Jwt.Claims claims) {
//생략
}
}- HTTP 요청 헤더에서 JWT 토큰이 있는지 확인
- JWT 토큰에서 loginId, roles을 추출하여 UsernamePasswordAuthenticationToken을 생성
- 앞서 만든 UsernamePasswordAuthenticationToken를 SecurityContext에 넣어줌
위치 설정
@Configuration
public class WebSecurityConfigure {
private final JwtConfigure jwtConfigure;
@Bean
public Jwt jwt() {
return new Jwt(
jwtConfigure.getIssuer(),
jwtConfigure.getClientSecret(),
jwtConfigure.getExpirySeconds()
);
}
public JwtAuthenticationFilter jwtAuthenticationFilter(Jwt jwt) {
return new JwtAuthenticationFilter(
this.jwtConfigure.getHeader(),
jwt
);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http
/**
* Jwt 필터 추가
*/
.addFilterAfter(jwtAuthenticationFilter(jwt), SecurityContextHolderFilter.class)
.build();
}
}- JWT 필터는 Spring Security 필터 체인에 추가
- SecurityContextHolderFilter 필터 바로 뒤에 설정
- SecurityContextHolderFilter 필터 앞에 위치하게 되면, SecurityContextHolderFilter 필터가 SecurityContext를 덮어 써버림

많은 도움이 되었습니다, 감사합니다.