완성 아키텍처
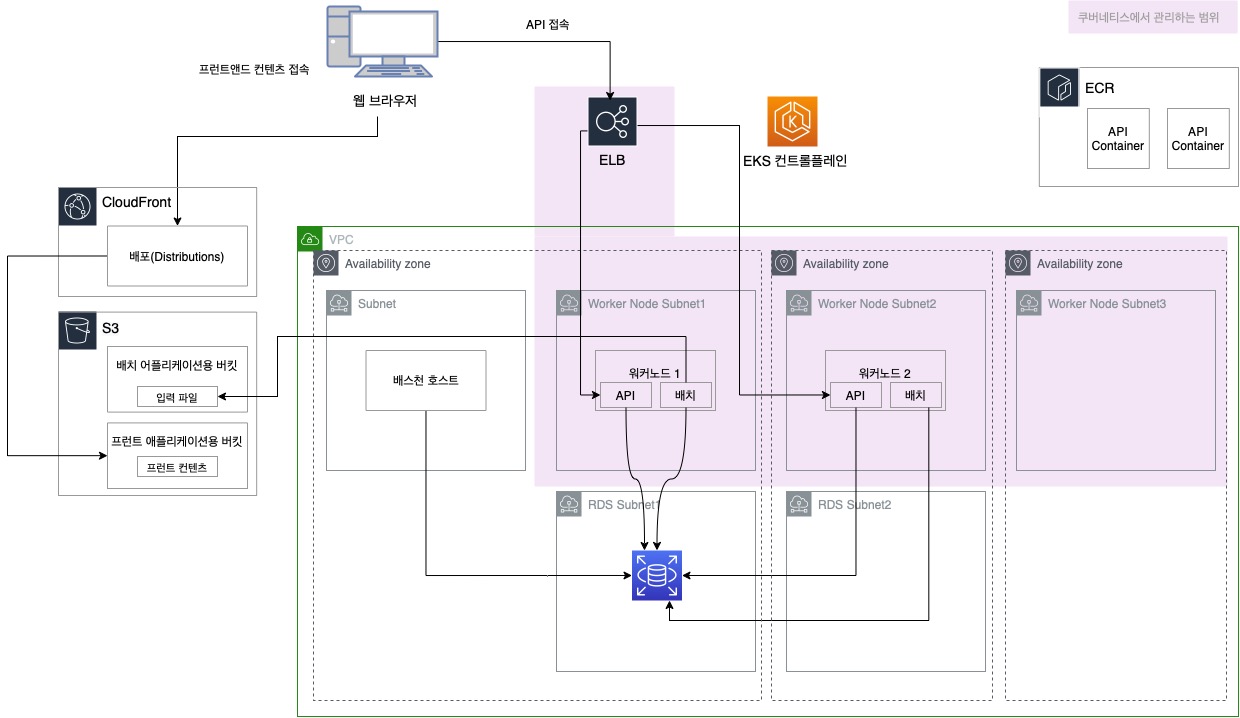
- 본 포스팅은 클라우드 네이티브를 위한 쿠버네티스 실전 프로젝트 내용을 기반으로 작성 되었습니다.
- 소스 코드를 아래 깃헙에서 다운 받은 후 작업해주세요.https://github.com/yuran777/k8s-aws-book.git
1. Base environment
- Region: 서울 리전 (ap-northeast-2)
- AZ: 3개 리전 사용 (ap-northeast-2a, ap-northeast-2b, ap-northeast-2c)
- Subnet: Worker Node 용 3개 + 베스천 호스트용 1개 + RDS용 2개
- IGW 통해서 외부와 통신할 수 있게 Routing table 설정
아래 Cludformation 템플릿으로 스택 생성
https://github.com/yuran777/k8s-aws-book/blob/master/eks-env/01_base_resources_cfn.yaml
2. EKS 클러스터 구축(워커 노드 2개 만들기)
2.1 eksctl 명령어로 클러스터 구축
eksctl create cluster \
--vpc-public-subnets <subnet ID> \ #subnet-0a43a15d4c3f2db30 형태의 subnet id 3개
--name eks-work-cluster \ #eks cluster 이름
--region ap-northeast-2 \ #cluster 만들 리전
--version 1.19 \
--nodegroup-name eks-work-nodegroup \ #nodegroup 이름
--node-type t2.medium \ #노드 크기
--nodes 2 \ #노드 갯수
--nodes-min 2 \ #노드 최소 갯수
--nodes-max 5 #노드 최대 갯수2.2 클러스터 구축시 EKS 클러스터 접속을 위한 인증 정보가 kubeconfig 파일에 업데이트 됨
참고) 파일 저장 경로: 맥 /home/USER명/.kube/config
kubectl config get-contexts
2.3 노드 상태 확인
kubectl get ndoes
NAME STATUS ROLES AGE VERSION
ip-주소.ap-northeast-2.compute.internal Ready <none> 2d23h v1.19.15-eks-9c63c4
ip-주소.ap-northeast-2.compute.internal Ready <none> 2d23h v1.19.15-eks-9c63c43. 데이터베이스 설정
- 데이터베이스 구축
- 베스천 호스트 구축
- 베스천 호스트 설정
3.1 데이터베이스 구축
https://github.com/yuran777/k8s-aws-book/blob/master/eks-env/10_rds_ope_cfn.yaml
위 Cludformation 템플릿으로 스택 생성
- 초기 파라미터 값 설정이 필요한 항목: VPC, OpeserverRoutetable
3.2 DB 및 베스천 호스트 생성 후 베스천 호스트에서 사용할 기본 도구 설치
- git
- postgreSQL
3.2.1 git 설치
sudo yum install git -y3.2.2 postgreSQL 설치
sudo amazon-linux-extras install -y postgresql113.2.3 github에서 클론하기
cd /home/ssm-user
git clone https://github.com/yuran777/k8s-aws-book.git3.2.4 CloudFormation으로 만든 데이터 베이스 정보 확인
CloudFormation 템플릿 중 아래 부분을 통해 만들어 짐.
EksWorkDB:
Type: "AWS::RDS::DBInstance"
Properties:
DBInstanceIdentifier: eks-work-db
Engine: postgres # https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/aws-properties-rds-database-instance.html#aws-properties-rds-database-instance-properties
EngineVersion: 11 # https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/CHAP_MySQL.html#MySQL.Concepts.VersionMgmt
DBInstanceClass: db.t2.micro
AllocatedStorage: 30
StorageType: gp2
DBName: eksworkdb
MasterUsername: !Join ['', ['{{resolve:secretsmanager:', !Ref RdsMasterSecret, ':SecretString:username}}' ]]
MasterUserPassword: !Join ['', ['{{resolve:secretsmanager:', !Ref RdsMasterSecret, ':SecretString:password}}' ]]
DBSubnetGroupName: !Ref EksWorkDBSubnetGroup
PubliclyAccessible: false
MultiAZ: false
PreferredBackupWindow: 18:00-18:30
PreferredMaintenanceWindow: sat:19:00-sat:19:30
AutoMinorVersionUpgrade: false
DBParameterGroupName: !Ref EksWorkDBParameterGroup
VPCSecurityGroups:
- !Ref RdsSecurityGroup
CopyTagsToSnapshot: true
BackupRetentionPeriod: 7
DeletionProtection: false
RdsMasterSecret:
Type: AWS::SecretsManager::Secret
Properties:
GenerateSecretString:
SecretStringTemplate: '{"username": "eksdbadmin"}'
GenerateStringKey: 'password'
PasswordLength: 16
ExcludeCharacters: '"@/\'''
Name: RdsMasterSecret
RdsUserSecret:
Type: AWS::SecretsManager::Secret
Properties:
GenerateSecretString:
SecretStringTemplate: '{"username": "mywork"}'
GenerateStringKey: 'password'
PasswordLength: 16
ExcludeCharacters: '"@/\''{}#%&*<>[]^`|'
Name: RdsUserSecret
RdsSecretAttachment:
Type: AWS::SecretsManager::SecretTargetAttachment
Properties:
SecretId: !Ref RdsMasterSecret
TargetId: !Ref EksWorkDB
TargetType: AWS::RDS::DBInstance
3.2.5 데이터 베이스 엔드포인트 주소 확인

- 데이터 베이스 관리자 비밀 번호 확인
AWS Secrets Manager > 보안 암호 > RdsMasterSecret 클릭 후, 보안 암호 값 > 보안 암호 검색
- 애플리케이션용 데이터베이스 사용자 비밀번호 확인
AWS Secrets Manager > 보안 암호 > RdsUserSecret 클릭 후, 보안 암호 값 > 보안 암호 검색
3.3 데이터베이스 세부 작업
- 애플리케이션용 데이터베이스 사용자 생성
- 애플리케이션용 데이터베이스 생성
- DDL 실행
3.3.1 애플리케이션용 데이터베이스 사용자 생성
createuser -d -U eksdbadmin -P -h <rds 엔드포인트> mywork
#앞에 두번 mywork사용자으 비밀번호 입력 : 위에서 찾은 RdsUserSecret 비밀 번호 사용하면 됨
#마지막은 eksadmin으 비밀번호를 입력 : 위에서 찾은 RdsMasterSecret 비밀번호 사용하면 됨참고: postgresql createuser 명령어 옵션
https://postgresql.kr/docs/11/app-createuser.html
3.3.2 애플리케이션용 데이터베이스 생성
createdb -U mywork -h <rds 엔드포인트> -E UTF8 myworkdb
#password는 앞에서 만든 mywork 사용자의 비밀 번호참고: postgresql createdb 명령어 옵션
https://postgresql.kr/docs/11/app-createdb.html
3.3.3 DDL 실행과 예제 데이터 불러오기
psql -U mywork -h <rds 엔드포인트 주소> mywork
myworkdb=> \i k8s-aws-book/backend-app/scripts/10_ddl.sql
myworkdb=> \i k8s-aws-book/backend-app/scripts/20_insert_sample_data.sql
myworkdb=> \q