Hashing 이란 무엇인가?
- 하나의 문자열을 보다 빨리 찾을 수 있도록 주소에 직접 접근할 수 있는 짧은 길이의 값이나 키로 변환하는 것
- 문자열을 찾을 때 문자 하나하나를 비교하며 찾는 것보다는 문자열에서 해시 키를 계산하고 그 키에 해당하는 장소에 문자열을 저장해 둔다면, 찾을 때는 한 번의 해시 키 계산만으로도 쉽게 찾을 수 있게 됨
- 데이터를 매핑하고 압축하는 것
- 해시 알고리즘을 사용하여 데이터에 대한 코드 표현을 만들고 코드는 일련의 문자열로 작용하여 지문 구성
- 해싱의 기본 개념은 데이터에 지문과 유사한 디지털 아이디를 제공하는 것
출처:
https://blog.naver.com/deathtaker/222875773488
https://terms.naver.com/entry.naver?docId=861623&cid=42346&categoryId=42346
https://blog.naver.com/softwidesec/222536537576
(영문 해석)
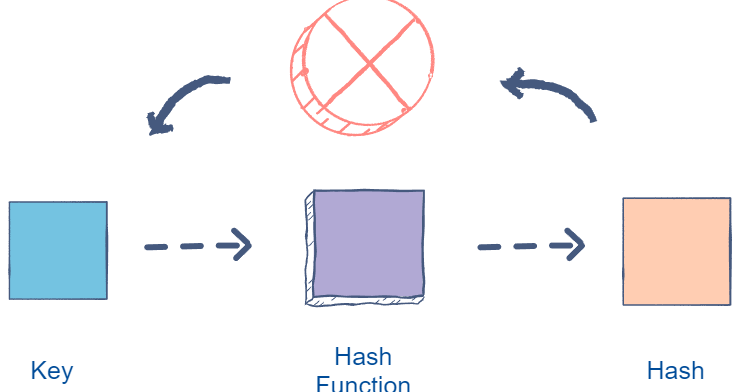
What is Hashing?
- Hashing is the process of converting a given key into another value.
- A hash function is used to generate the new value according to a mathematical algorithm.
- The result of a hash function is known as a hash value or simply, a hash.
- A good hash function uses a one-way hashing algorithm, or in other words, the hash cannot be converted back into the original key.
What are the benefits of Hashing?
One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
Hashing is also used to verify the integrity of a file after it has been transferred from one place to another, typically in a file backup program like SyncBack. To ensure the transferred file is not corrupted, a user can compare the hash value of both files. If they are the same, then the transferred file is an identical copy.
In some situations, an encrypted file may be designed to never change the file size nor the last modification date and time (for example, virtual drive container files). In such cases, it would be impossible to tell at a glance if two similar files are different or not, but the hash values would easily tell these files apart if they are different.
Source:
https://www.techtarget.com/searchdatamanagement/definition/hashing
https://www.2brightsparks.com/resources/articles/introduction-to-hashing-and-its-uses.html
https://www.educative.io/answers/what-is-hashing
