시스템해킹
1.System Hacking-Entrance

시스템 해킹은 프로그램 행위를 조작하여 공격자가 원하는 행동을 실행하도록 하는 공격 전반을 일컬음공격 대상 프로그램이 구동되는 서버의 임의 유저와 같은 권한 획득C언어void fun (int x, int y){ int z; char buf100;}int main (i
2.[포너블] 리눅스 메모리 구조

리눅스의 메모리는 5가지의 세그먼트로 구분한다. 코드, 데이터, BSS, 힙, 스택 세그먼트다.실행 가능한 기계코드가 위치하는 영역, CPU는 읽기와 실행 권한이 부여된다. 대부분의 운영체제는 쓰기 권한을 제거한다.초기화가 이뤄진(initialized) 전역 변수/상수
3.[포너블] 환경 구축
드림핵 시스템 해킹 강의를 위해 아래 주소에서 dbg 다운로드https://github.com/pwndbg/pwndbg다운로드가 완료되면 다음과 같은 화면이 나온다.소스코드gdb debugee로 디버깅 시작리눅스의 실행파일은 ELF 형식을 가지고 있다. ELF
4.[포너블] pwntools

아래와 같은 코드로 파이썬을 통해 공격 페이로드 생성, 프로그램 전달로 익스플로잇 수행이 가능하다.근데 사실상 한줄로 모든걸 수행하기는 어렵다. 하단 코드는 socket 모듈을 사용한 초기 파이썬 익스플로잇 스크립트의 예다.리틀 엔디언 바이트 배열로 바꾸고 이를 역으로
5.[포너블] Exploit Tech: Shellcode

본 문서는 드림핵 강의를 요약한 문서입니다.익스플로잇(Exploit) 이란 상대 시스템을 공격하는 것을 말한다.셸코드(Shellcode) 란 익스플로잇을 위해 제작된 어셈블리 코드 조각을 일컫는다. 일반적으로 셸을 획득하기 위한 목적으로 셸코드를 사용한다. 왜냐하면 일
6.[포너블] Calling Convention
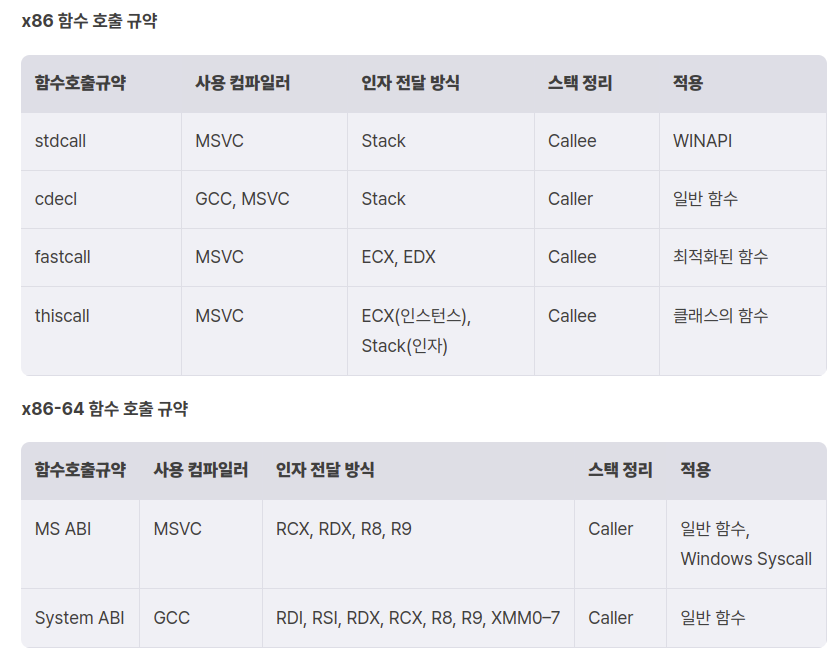
본 문서는 드림핵 커리큘럼 강의를 수강하고 요약한 문서입니다.함수 내에서 다른 함수를 호출할 때에는 호출자의 상태(스택 프레임), 반환 주소를 저장해야한다. 그리고 호출자는 피호출자가 요구하는 인자를 전달해줘야 한다. 피호출자의 실행이 종료되면 호출자는 반환 값을 전달
7.[포너블] Stack Buffer Overflow

본 문서는 드림핵 커리큘럼 강의(https://learn.dreamhack.io/60스택은 그 크기가 동적으로 확장될 수 있다. 스택 오버플로우는 확장이 너무 많이된 경우에 발생하는 버그다. 반면 스택 버퍼 오버플로우는 스택에 위치한 버퍼보다 큰 데이터가 입력
8.[포너블] Basic exploitation
워게임 출처: 드림핵이 문제는 서버에서 작동하고 있는 서비스(basic_exploitation_000)의 바이너리와 소스 코드가 주어집니다. 프로그램의 취약점을 찾고 익스플로잇해 셸을 획득한 후, "flag" 파일을 읽으세요.0x80 길이를 갖는 buf가 선언되고 in
9.[포너블] Mitigation: Stack Canary

본 문서는 드림핵 커리큘럼 강의를 요약한 문서입니다.지난번에는 스택 버퍼 오버플로우를 통해 스택의 반환 주소를 조작하고 실행 흐름을 획득했다. 이로부터 보호하는 기법이 바로 스택 카나리(Stack Canary) 다.이 기법은 버퍼와 반환주소 사이에 카나리 값을 집어 넣
10.[포너블] ssp_001
문제 출처 드림핵SSP 방어 기법을 우회하여 셸을 획득하고 flag 파일을 읽는 것이 목표다.먼저 들어가기 전에 사양을 확인해보자.Canary와 NX가 적용되어 있다. NX가 뭔지 몰라 찾아보니 스택영역에서 코드를 실행하지 못하게 하여 버퍼 오버플로우를 통한 공격을 막
11.[포너블] Return Address Overwrite

본 문서는 드림핵 커리큘럼 강의를 수강하고 요약한 문서입니다. 주어진 코드 사실 여기서 보면 scanf 함수의 %s를 통해 입력길이 제한을 두지 않음을 볼 수 있다. 따라서 scanf의 %s 포맷 스트링은 절대로 사용하지 말아야 한다. 반드시 %[n]s 형태로 사용
12.[포너블] Mitigration: NX & ASLR

문서 내용 출처: 드림핵No-eXcute(NX) 는 실행에 사용되는 메모리 영역과 쓰기에 사용되는 메모리 영역을 분리하는 보호 기법이다. gdb에서 vmmap을 통해 NX 전후의 메모리 맵을 조회하고, 메모리 영역별 권한을 살펴볼 수 있다.checksec을 통해 바이너
13.[포너블] Library - Static Link vs Dynamic link

문서 내용 출처: 드림핵컴퓨터 시스템에서, 프로그램들이 함수나, 변수를 공유해서 사용할 수 있게 한다. 자주 쓰이는 함수, 변수들의 저으이를 하나로 묶어서 미리 만들어 놓고 공유하는 것이다. libc는 우분투에 기본적으로 탑재된 라이브러리다.Link(링크) 는 많은 프
14.[포너블] Exploit Tech: Return to Library

출처 드림핵 / 예제파일NX로 스택에 실행권한이 없어졌다면, 아직 실행 권한이 남아있는 코드 영역으로 반환주소를 덮으면 되는 것이다. 일반적으로 실행 권한이 있는 메모리 영역은 바이너리 코드영역과 라이브러리 코드 영역이다. 이 중 라이브러리에는 공격에 유용한 함수들이
15.[포너블] basic_rop_x64
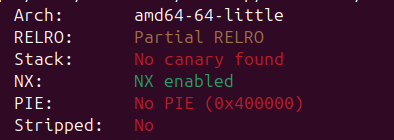
카나리는 없고, NX만 적용되어 있다.(1) system 함수와 /bin/sh가 코드 내에 없다. 주소를 구해야한다.(2) read 함수 실행에 페이로드를 입력해서 스택 버퍼 오버플로우를일으킬 수 있다. 이번에는 ret2main 기법을 활용할 것이다.최종 목표는 sys
16.[포너블] PIE & RELRO
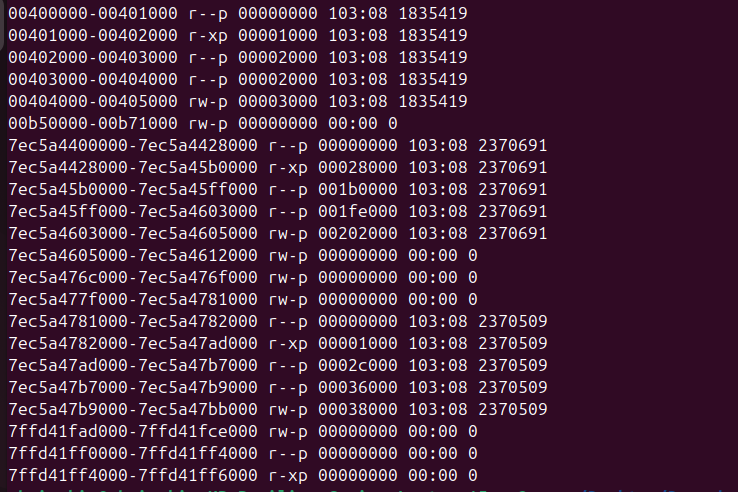
출처 드림핵PIC는 Position-Independent Code의 약자로 재배치가 가능한 성질을 만족하는 코드를 말한다. 리눅스의 공유오브젝트(Share Object)가 대표적인 예시다. PIC 적용이 되지 않은 바이너리 파일은 printf 함수에 문자열을 전달할 때
17.[포너블] Exploit Tech: Hook Overwrite

0. 서론 Hooking(후킹)은 운영체제가 어떤 코드를 실행하려 할 떄, 이를 낚아채어 다른 코드가 실행되게 하는 것을 말한다.malloc()과 free()와 함께 호출되는 Hook이 함수 포인터 형태로 존재하는데, 이 함수 포인터를 임의의 함수 주소로 오버라이트 하
18.[포너블] Out of Bounds

출처 드림핵 1. Out of Bounds 1.1 배열의 속성 배열이 점유하는 공간의 크기는 요소의 개수와 요소 자료형의 크기를 곱한 값이 된다. 요소의 개수를 우리는 배열의 길이라고 부른다. 배열의 각 주소는 배열의 주소, 요소의 인덱스, 요소 자료형의 크기를 이용
19.[포너블] Format String Bug
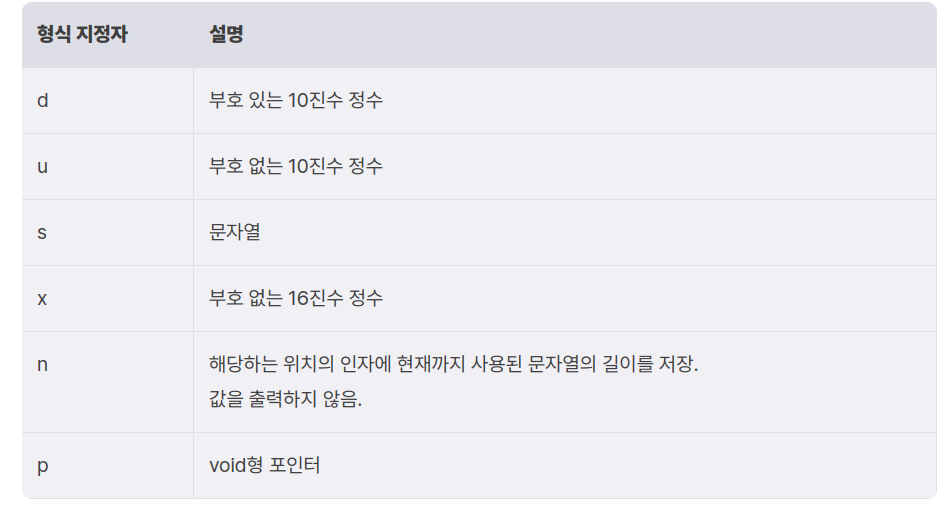
출처 드림핵(https://learn.dreamhack.io/114\`printf\`, scanf, sscanf등의 함수들은 포맷 스트링을 처리하며, 이 포맷 스트링을 채울 값들을 레지스터나 스택에서 가져온다. 문제는 포맷 스트링이 필요로 하는 인자의 개수와
20.[포너블] Exploit Tech: Format String Bug
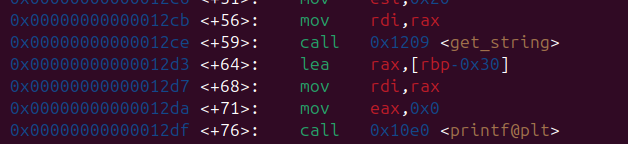
출처 드림핵 강의(https://learn.dreamhack.io/110포맷 스트링 버그는 포맷 스트링을 사용하는 모든 함수에서 발생할 수 있다. 리눅스 라이브러리 함수에서는 printf, fprintf, sprintf와 같은 함수들을 사용할 때 유의해야한다.
21.[포너블] basic_exploitation_002
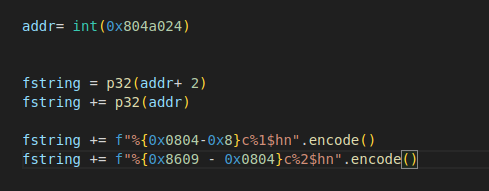
1. 분석 1.1 보안 기법 분석 먼저 checksec을 통해 적용된 보안 기법을 분석해보자. 32비트 환경에서 실행되는 것을 확인할 수 있다. NX가 적용되었고, Partial RELRO 이므로 GOT 영역을 Overwrite 할 수도 있겠다. 스택 카나리는 보이지
22.[포너블] basic_exploitation_003
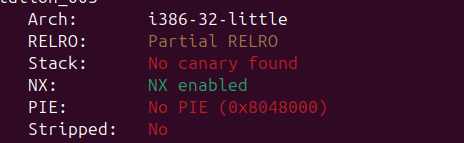
Partial RELRO와 NX가 적용되어있다. PIE와 Canary는 적용되지 않았다. 32비트 환경에서 실행되는 걸 알 수 있다.heap_buf에 read를 통해 값을 입력하고, sprintf를 거쳐 stack_buf에 전달되어 printf를 통해 출력된다.get_
23.[포너블] Background: ptmalloc2
출처 : 드림핵 강의(https://learn.dreamhack.io/569\*\*Memory Allocator\*\*: 한정된 메모리 자원을 각 프로세스에 효율적으로 배분한다. 이를 위해 사용하는 알고리즘은 운영체제마다 다르다.리눅스 - ptmalloc2구글
24.[포너블] Memory Corruption: Use After Free

Use-After-Free는 메모리 참조에 사용한 포인터를 메뫃리 해제 후에 적절히 초기화하지 않아서, 또는 해제한 메모리를 초기화하지 않고 다음 청크에 재할당해주면서 발생하는 취약점이다.이 글에서 잠깐 언급한 적이 있다.free 함수는 청크를 ptmalloc에 반환하
25.[포너블] Exploit Tech: Use After Free
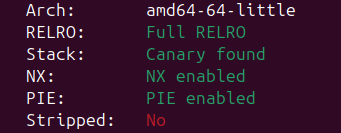
출처 : 드림핵 강의(https://learn.dreamhack.io/119먼저 아래의 소스코드에서 취약점을 찾아보자.여태까지 배운 모든 보호 기법이 적용되어있다. FULL_RELRO 때문에 GOT를 덮어쓰는 것은 어렵다. 라이브러리 내의 훅 또는 코드에서 사
26.[포너블] Memory Corruption: Double Free Bug

출처: 드림핵 강의(https://learn.dreamhack.io/116임의의 청크에 대해 free를 두 번이상 적용할 수 있다는 것은. 같은 청크를 free list에 여러번 추가할 수 있음을 의미한다. 해커들은 free list에 중복해서 존재하는(dup
27.[포너블] Exploit Tech: Tcache Poisoning

0. 서론 free list에 중복으로 연결된 청크를 재할당하면, 그 청크는 해제된 청크이자, 할당된 청크다. 이를 이용하면 공격자는 임의 주소에 청크를 할당할 수 있고, 그 청크르 이용하여 임의 주소의 데이터를 읽거나 조작할 수 있게 된다. 이를 Tcache Pois
28.[포너블] Tcache_dup
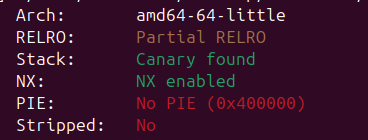
카나리와 NX가 적용되어있다. PIE는 적용되어있지 않다.문자열 포인터 배열 ptr에 malloc과 free를 통해 청크를 할당하고 있다. 별도의 초기화 과정은 이뤄지지 않고 있다. 따라서 Double Free Bug를 활용하여 실행흐름을 get_shell()로 가져가
29.[포너블] Tcache dup2

tcache_dup 문제와 풀이는 비슷하다. 다만 이번 문제에서는 DFB를 탐지하기 때문에 key값을 조정해주어야 한다. 다행히 modify가 있어서 dangling pointer를 이용해 key를 수정해 주었다. 이로써 DFB가 가능하고 puts_got에 get_sh
30.[포너블] Logical Bug: Type Error
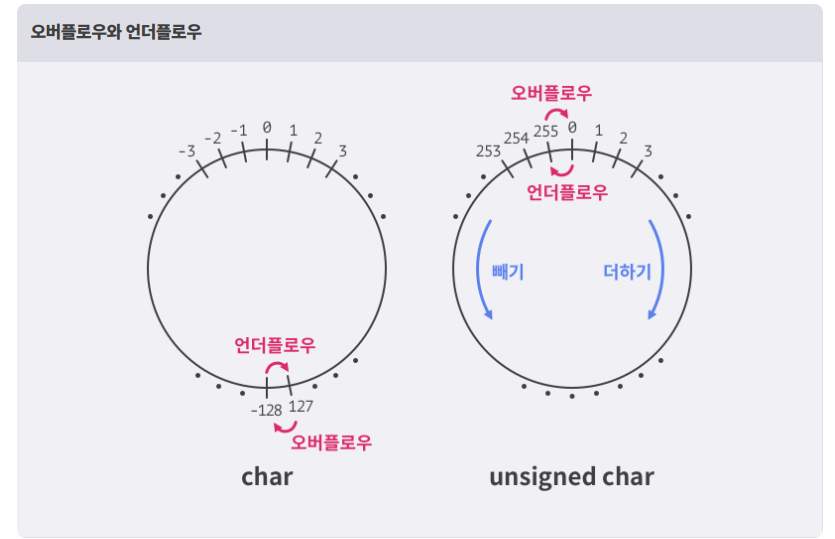
출처 드림핵 강의(https://learn.dreamhack.io/118같은 자료형이라도 운영체제에 따라 크기가 달라질 수 있다. 이 문서의 자료형 챕터를 참고하라.변수에 어떤 값을 대입할 때, 그 값이 변수에 저장될 수 있는 범위를 벗어나면, 저장할 수 있는
31.[포너블] sint
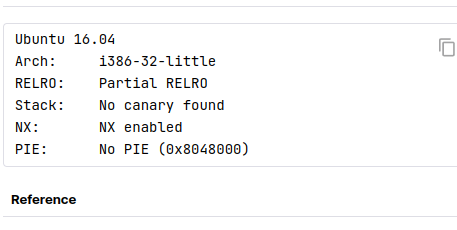
카나리는 없지만 NX가 적용되어 있다.잘 보면 read가 size-1만큼 입력을 받는다. 이 인자는 값을 unsigned int로 받는다. 하지만 size는 int 형이며, 자료크기의 검사는 0이상 256이하인지만 검사한다.따라서 size를 0으로 설정하여 검사를 우회
32.[포너블] Logical Bug: Command Injection
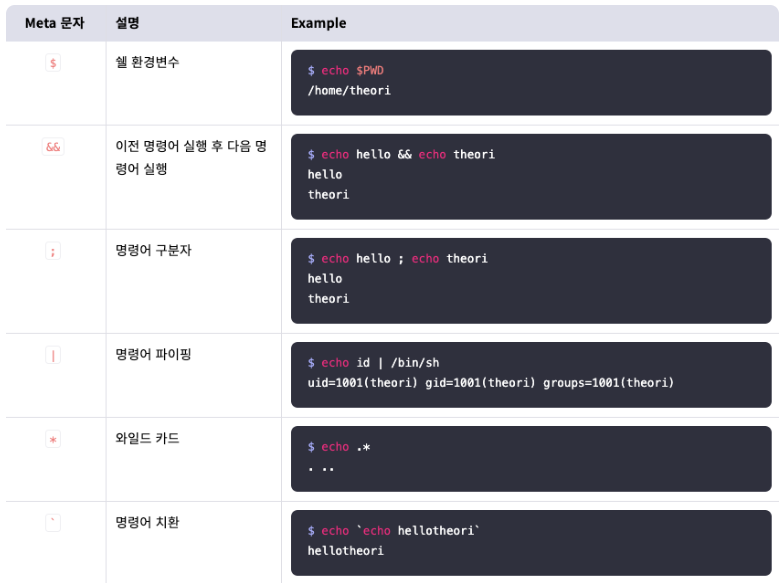
출처 드림핵(https://learn.dreamhack.io/108>system 함수가 명령어를 실행하는 과정system 함수는 라이브러리 내부에서 do_system 함수를 호출한다. do_system은 "sh-c"와 system 함수의 인자를 결합하여 exe
33.[포너블] Logical Bug: Path Traversal

출처: 드림핵 강의로컬 파일 시스템에 접근하는 시스템에서, 사용자가 허용되지 않은 경로에 접근할 수 있는 취약점을 Path Traversal이라고 한다.절대 경로는 루트 디렉토리부터 파일에 이를 떄까지 거쳐야 하는 디렉토리 명을 모두 연결하여 구성한다. 한 파일에 대응