구성도
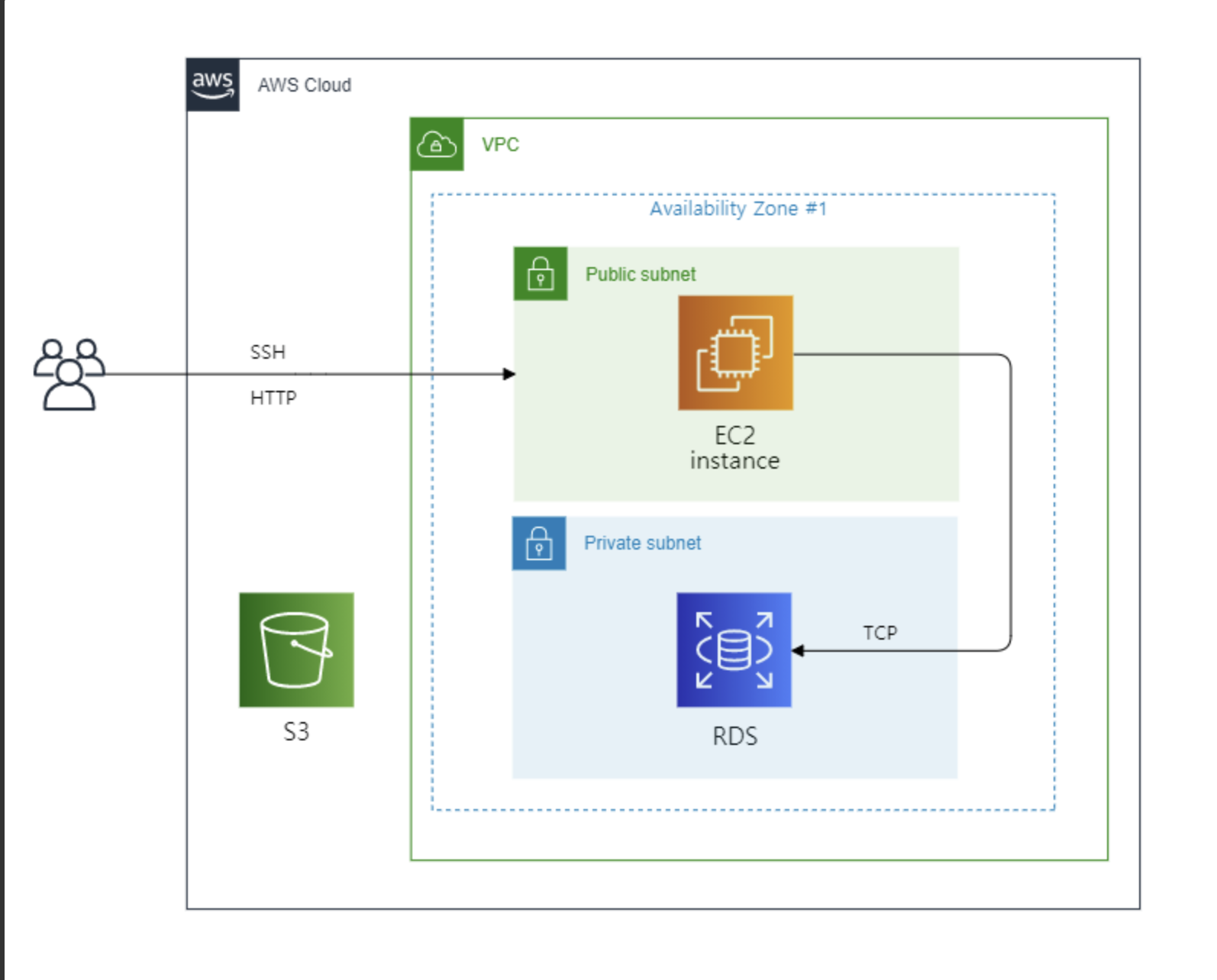
이런 형태로 구축하려고 한다.
서브넷 추가하기
#vpc.tf
#퍼블릭 서브넷
resource "aws_subnet" "realPublicSubnet" {
vpc_id = aws_vpc.realVPC.id
cidr_block = "10.0.0.0/24"
availability_zone = "ap-northeast-2c"
tags = {
Name = "real-public-subnet"
}
}
#프라이빗 서브넷
resource "aws_subnet" "realPrivateSubnet1" {
vpc_id = aws_vpc.realVPC.id
cidr_block = "10.0.1.0/24"
availability_zone = "ap-northeast-2c"
tags = {
Name ="real-private-subnet1"
}
}
resource "aws_subnet" "realPrivateSubnet2" {
vpc_id = aws_vpc.realVPC.id
cidr_block = "10.0.2.0/24"
availability_zone = "ap-northeast-2a"
tags = {
Name = "real-private-subnet2"
}
}- vpc_id 부분에 바로전에 만들었던 vpc의 id를 추가하면 쉽게 서브넷을 추가할 수 있다.
- 아까 만들었던 이름을 사용해서 id를 쉽게 얻을 수 있다. (aws_vpc.testVPC.id)
IGW (인터넷 게이트웨이 추가)
# vpc.tf
resource "aws_internet_gateway" "realIGW" {
vpc_id = aws_vpc.realVPC.id
tags = {
Name="real-IGW"
}
}- vpc에서 외부와 통신할 수 있게 public subnet과 통신한 인터넷 게이트웨이를 추가한다.
라우팅 테이블 작성
#vpc.tf
##라우팅 테이블 만들기
#퍼블릭 라우팅 테이블
resource "aws_route_table" "realPublicRoute" {
vpc_id = aws_vpc.realVPC.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.realIGW.id
#퍼블릭 서브넷에 인터넷 게이트웨이 연결.
}
tags = {
Name = "real-public-route"
}
}
#프라이빗 라우팅 테이블
resource "aws_route_table" "realPrivateRoute" {
vpc_id = aws_vpc.realVPC.id
tags = {
Name = "real-private-route"
}
}
#퍼블릭 라우팅 테이블 연결
resource "aws_route_table_association" "realPublicRTAssociation"{
subnet_id = aws_subnet.realPublicSubnet.id
route_table_id = aws_route_table.realPublicRoute.id
}
#프라이빗 라우팅 테이블 연결
resource "aws_route_table_association" "realPrivateRTAssociation1"{
subnet_id = aws_subnet.realPrivateSubnet1.id
route_table_id = aws_route_table.realPrivateRoute.id
}
resource "aws_route_table_association" "realPrivateRTAssociation2"{
subnet_id = aws_subnet.realPrivateSubnet2.id
route_table_id = aws_route_table.realPrivateRoute.id
}- 다음으로는 라우팅 테이블을 만들어 서브넷과 연결시켜준다.
보안그룹 생성
#vpc.tf
#퍼블릭 보안 그룹
resource "aws_security_group" "realPublicSG" {
vpc_id = aws_vpc.realVPC.id
name = "real public SG"
description = "real public SG"
tags = {
Name = "real pulbic SG"
}
}
#퍼블릭 보안 그룹 규칙
resource "aws_security_group_rule" "realPublicSGRulesHTTPingress" {
type = "ingress"
from_port = 80
to_port=80
protocol = "TCP"
cidr_blocks = ["0.0.0.0/0"]
security_group_id = aws_security_group.realPublicSG.id
lifecycle{
create_before_destroy = true
}
}
resource "aws_security_group_rule" "realPublicSGRulesSSHingress" {
type = "ingress"
from_port = 22
to_port= 22
protocol = "TCP"
cidr_blocks=["0.0.0.0/0"]
security_group_id = aws_security_group.realPublicSG.id
lifecycle{
create_before_destroy = true
}
}
resource "aws_security_group_rule" "realPublicSGRulesALLegress" {
type = "egress"
from_port = 0
to_port= 0
protocol = "ALL"
cidr_blocks=["0.0.0.0/0"]
security_group_id = aws_security_group.realPublicSG.id
lifecycle{
create_before_destroy = true
}
}
#프라이빗 보안 그룹
resource "aws_security_group" "realPrivateSG" {
vpc_id = aws_vpc.realVPC.id
name = "real private SG"
description = "real private SG"
tags = {
Name = "real private SG"
}
}
#프라이빗 보안 그룹 규칙
resource "aws_security_group_rule" "realPrivateSGRulesRDSingress" {
type = "ingress"
from_port = 3306
to_port=3306
protocol = "TCP"
security_group_id = aws_security_group.realPrivateSG.id
source_security_group_id = aws_security_group.realPublicSG.id
lifecycle{
create_before_destroy = true
}
}
resource "aws_security_group_rule" "realPrivateSGRulesRDSegress" {
type = "egress"
from_port = 3306
to_port= 3306
protocol = "TCP"
security_group_id = aws_security_group.realPrivateSG.id
source_security_group_id = aws_security_group.realPublicSG.id
lifecycle{
create_before_destroy = true
}
}- public, private subnet의 보안그룹을 생성해준다.
- public의 경우 ssh접속을 위한 22번 포트와, http 통신을 위한 80를 ingress로, 열어주고 외부로 나가는 egress는 모든 트래픽을 열어준다.
- private의 경우 rds를 연결하기 위해 3306포트를 열어준다.
- 테라폼에서는 보안 그룹을 설정할 때 인라인으로 규칙을 추가해주거나 aws_security_group_rule
으로 추가할 수 있음. - 만약 인라인으로 지정하게 된다면 한 보안 그룹에서 인바운드로 허용하는 액세스원이 다른 보안 그룹인 경우 이를 지정 할 수 없다.
=> aws_security_group_rule를 사용해서 추가해주자.
- ingress는 외부에서 내부로 들어오는 트래픽, egress는 내부에서 외부로 나가는 트래픽을 의미.
계획 및 적용
$ terraform plan
.
.
.
Plan: 16 to add, 0 to change, 0 to destroy.$ terraform apply
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_security_group.testPrivateSG: Creating...
aws_route_table.testPrivateRoute2: Creating...
aws_route_table.testPrivateRoute1: Creating...
aws_route_table.testPublicRoute: Creating...
aws_security_group.testPublicSG: Creating...
aws_route_table.testPrivateRoute2: Creation complete after 1s [id=rtb-01a08a475c7aa3b6e]
aws_route_table_association.testPrivateRTAssociation2: Creating...
aws_route_table.testPrivateRoute1: Creation complete after 1s [id=rtb-0de978f9daf7138da]
aws_route_table_association.testPrivateRTAssociation1: Creating...
aws_route_table_association.testPrivateRTAssociation2: Creation complete after 0s [id=rtbassoc-04c687539b690b97e]
aws_route_table_association.testPrivateRTAssociation1: Creation complete after 0s [id=rtbassoc-00c81afb4d66a4afb]
aws_route_table.testPublicRoute: Creation complete after 1s [id=rtb-0b21780b54c48f288]
aws_route_table_association.testPublicRTAssociation: Creating...
aws_route_table_association.testPublicRTAssociation: Creation complete after 1s [id=rtbassoc-015a0b583a70d3d07]
aws_security_group.testPrivateSG: Creation complete after 2s [id=sg-0564ca6903f5d71ae]
aws_security_group.testPublicSG: Creation complete after 2s [id=sg-0d17e51c8f54212ee]
aws_security_group_rule.testPublicSGRulesHTTPegress: Creating...
aws_security_group_rule.testPrivateSGRulesRDSegress: Creating...
aws_security_group_rule.testPublicSGRulesHTTPSingress: Creating...
aws_security_group_rule.testPublicSGRulesHTTPSegress: Creating...
aws_security_group_rule.testPublicSGRulesHTTPingress: Creating...
aws_security_group_rule.testPublicSGRulesSSHegress: Creating...
aws_security_group_rule.testPrivateSGRulesRDSingress: Creating...
aws_security_group_rule.testPublicSGRulesSSHingress: Creating...
aws_security_group_rule.testPublicSGRulesSSHegress: Creation complete after 1s [id=sgrule-1099277773]
aws_security_group_rule.testPrivateSGRulesRDSegress: Creation complete after 1s [id=sgrule-640893485]
aws_security_group_rule.testPublicSGRulesHTTPSingress: Creation complete after 1s [id=sgrule-1338266698]
aws_security_group_rule.testPrivateSGRulesRDSingress: Creation complete after 1s [id=sgrule-3779608258]
aws_security_group_rule.testPublicSGRulesHTTPingress: Creation complete after 2s [id=sgrule-768399379]
aws_security_group_rule.testPublicSGRulesHTTPSegress: Creation complete after 2s [id=sgrule-292654581]
aws_security_group_rule.testPublicSGRulesSSHingress: Creation complete after 3s [id=sgrule-1743733607]
aws_security_group_rule.testPublicSGRulesHTTPegress: Creation complete after 3s [id=sgrule-3303017385]
Apply complete! Resources: 16 added, 0 changed, 0 destroyed.이런식으로 적용이 완료 되면 성공이다.