IAM User 생성
사용자 추가 클릭
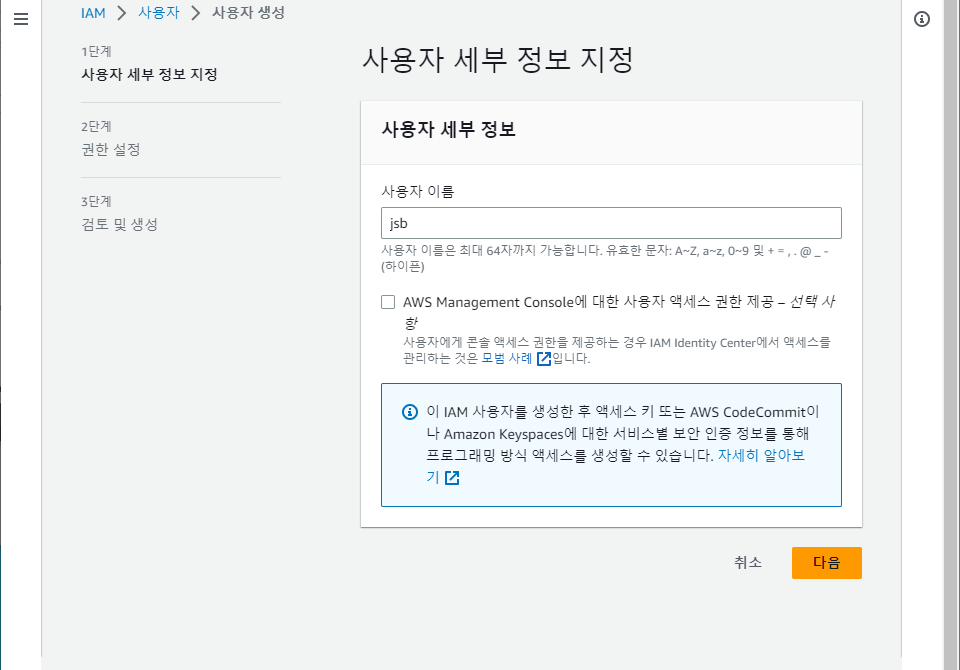
- 사용자 이름 지정
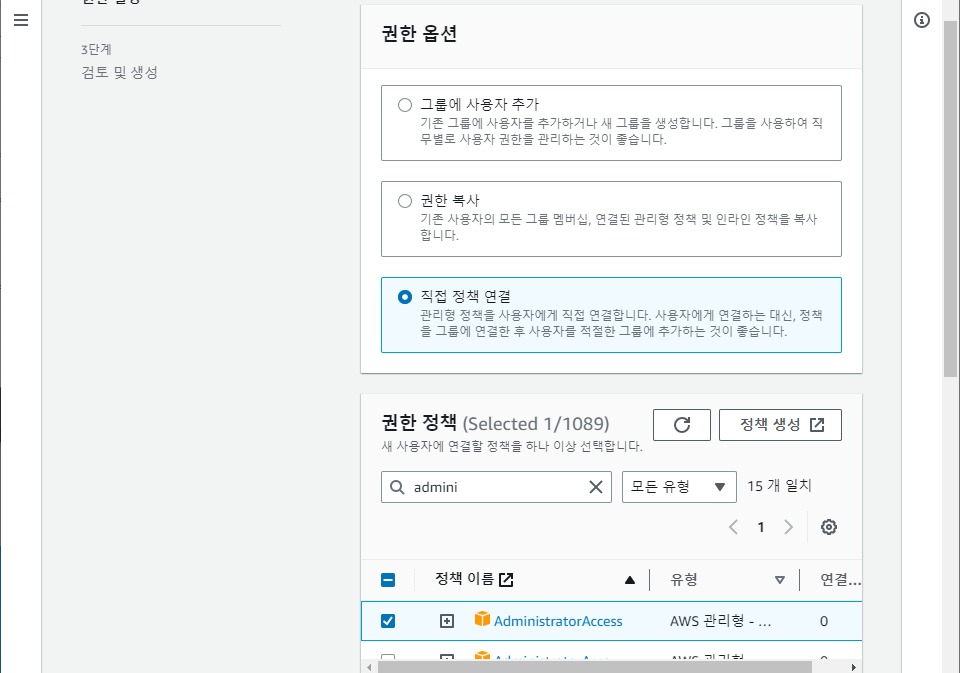
- 직접 정책 연결 - 권한 정책(AdministratorAccess) - 다음 - 사용자 생성
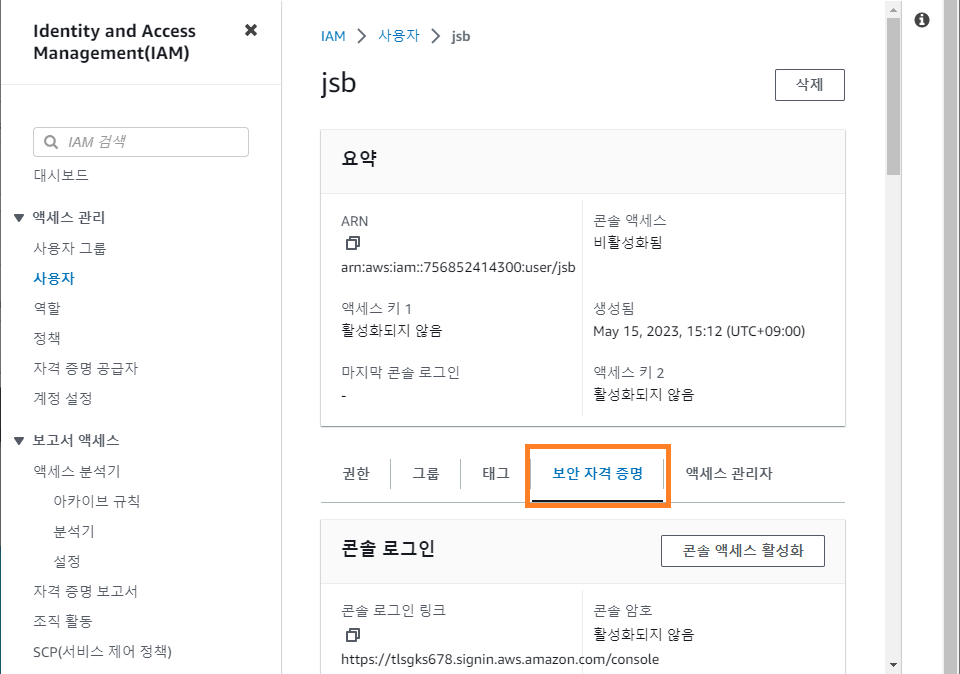
액세스 키 생성 및 다운로드
- 사용자 속성 - 보안자격 증명
- 액세스 키 만들기 클릭
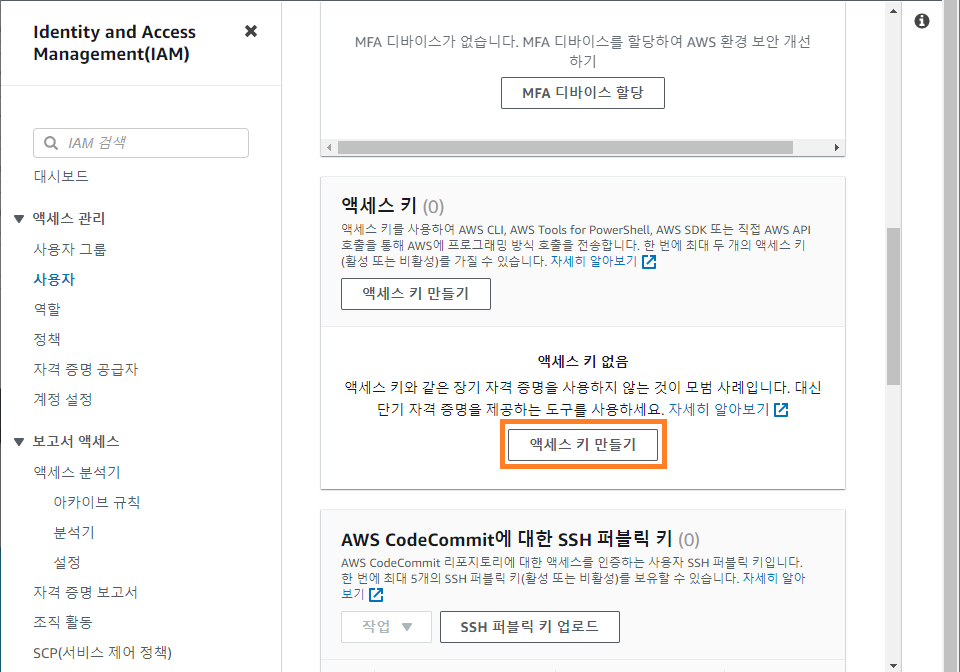
- Command Line Interface(CLI) 선택
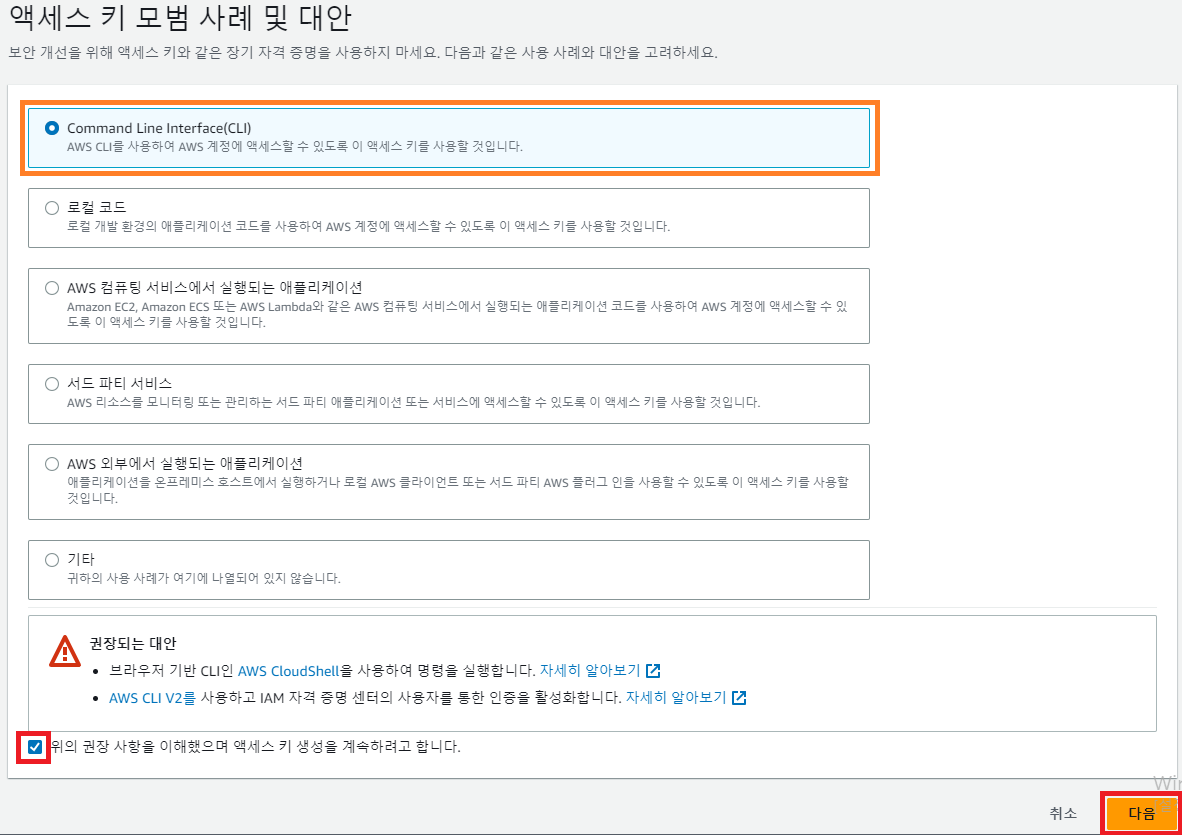
- 액세스 키 만들기 클릭
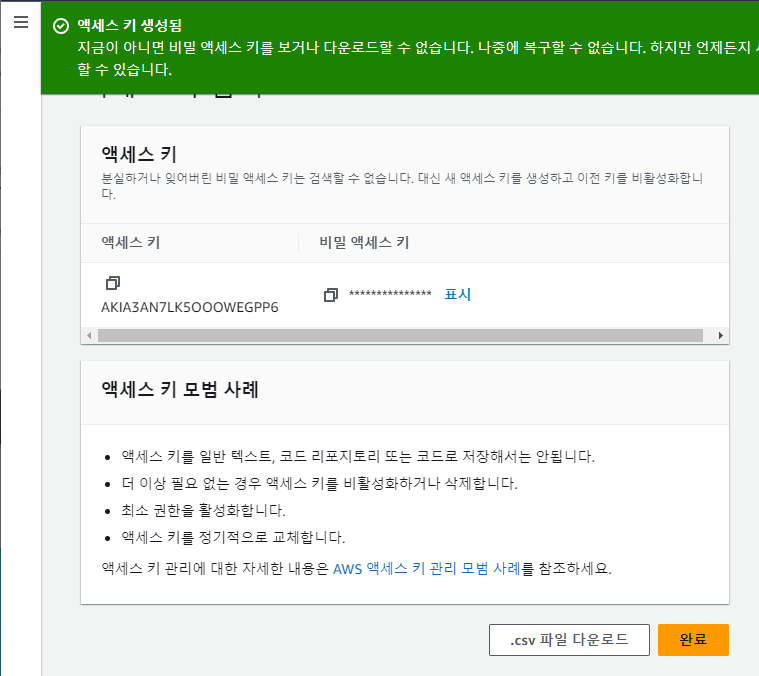
- 액세스 키 / 비밀 액세스 키 이용 (키를 저장하진 않음.)
AWS CLI 설치
\# curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
\# yum install -y unzip wget bash-completion mysql git
\# unzip awscliv2.zip
\# ./aws/install
\# echo "complete -C '/usr/local/bin/aws_completer' aws" >> .bash_profile
\# exit
\# aws --version
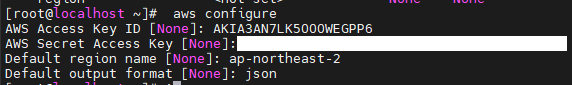
\# aws configure
\# aws s3 ls
\# vi /etc/selinux/config
----------------------------------------
SELINUX=disabled
----------------------------------------
\# setenforce 0
AWS CLI 스크립트
VPC와 서브넷 만들기
\# aws ec2 create-vpc --cidr-block 192.168.0.0/16 --tag-specification "ResourceType=vpc,Tags=[{Key=Name,Value=test-vpc}]" --output text
----------------------------------------
VPC 192.168.0.0/16 dopt-01e028e4248daab99 default False 756852414300 pending vpc-0a593c77a7c18705d
CIDRBLOCKASSOCIATIONSET vpc-cidr-assoc-0200bba8c47e4b58c 192.168.0.0/16
CIDRBLOCKSTATE associated
TAGS Name test=vpc
----------------------------------------
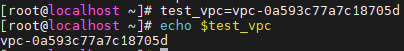
\# test_vpc=vpc-0a593c77a7c18705d
\# echo $test_vpc
- 변수 지정 결과
- 서브넷 생성
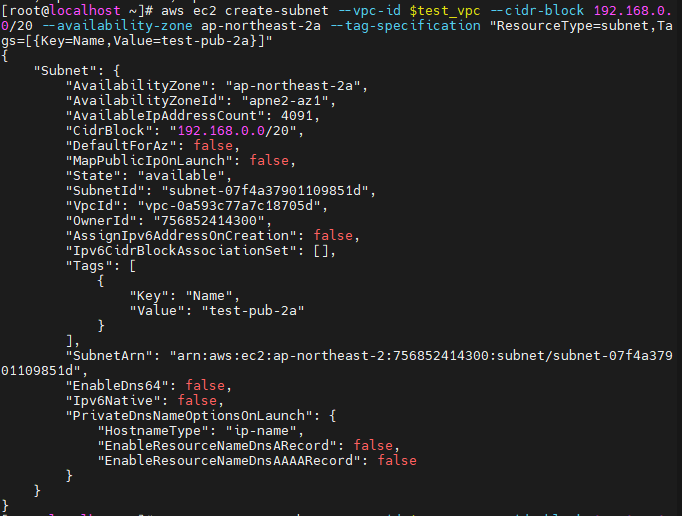
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.0.0/20 --availability-zone ap-northeast-2a --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pub-2a}]"
----------------------------------------
{
"Subnet": {
"AvailabilityZone": "ap-northeast-2a",
"AvailabilityZoneId": "apne2-az1",
"AvailableIpAddressCount": 4091,
"CidrBlock": "192.168.0.0/20",
"DefaultForAz": false,
"MapPublicIpOnLaunch": false,
"State": "available",
"SubnetId": "subnet-07f4a37901109851d",
"VpcId": "vpc-0a593c77a7c18705d",
"OwnerId": "756852414300",
"AssignIpv6AddressOnCreation": false,
"Ipv6CidrBlockAssociationSet": [],
"Tags": [
{
"Key": "Name",
"Value": "test-pub-2a"
}
],
"SubnetArn": "arn:aws:ec2:ap-northeast-2:756852414300:subnet/subnet-07f4a37901109851d",
"EnableDns64": false,
"Ipv6Native": false,
"PrivateDnsNameOptionsOnLaunch": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
}
}
}
----------------------------------------
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.16.0/20 --availability-zone ap-northeast-2b --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pub-2b}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.32.0/20 --availability-zone ap-northeast-2c --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pub-2c}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.48.0/20 --availability-zone ap-northeast-2d --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pub-2d}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.64.0/20 --availability-zone ap-northeast-2a --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pvt-2a}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.80.0/20 --availability-zone ap-northeast-2b --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pvt-2b}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.96.0/20 --availability-zone ap-northeast-2c --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pvt-2c}]"
\# aws ec2 create-subnet --vpc-id $test_vpc --cidr-block 192.168.112.0/20 --availability-zone ap-northeast-2d --tag-specification "ResourceType=subnet,Tags=[{Key=Name,Value=test-pvt-2d}]"
\# aws ec2 describe-subnets --filters "Name=vpc-id,Values=$test_vpc" --query 'Subnets[*].{AZ:AvailabilityZone,CIDR:CidrBlock,SUBNET:Tags[0].Value}'
퍼블릭 및 프라이빗 서브넷으로 만들기
\# aws ec2 create-internet-gateway --tag-specification "ResourceType=internet-gateway,Tags=[{Key=Name,Value=test-igw}]" --output text
----------------------------------------
INTERNETGATEWAY igw-0f9c8e2d78bb1739f 756852414300
TAGS Name test-igw
----------------------------------------
\# test_igw=igw-0f9c8e2d78bb1739f
\# aws ec2 attach-internet-gateway --vpc-id $test_vpc --internet-gateway-id $test_igw
\# aws ec2 describe-internet-gateways --filters "Name=internet-gateway-id,Values=$test_igw" --output table
----------------------------------------
---------------------------------------------
| DescribeInternetGateways |
+-------------------------------------------+
|| InternetGateways ||
|+------------------------+----------------+|
|| InternetGatewayId | OwnerId ||
|+------------------------+----------------+|
|| igw-0f9c8e2d78bb1739f | 756852414300 ||
|+------------------------+----------------+|
||| Attachments |||
||+------------+--------------------------+||
||| State | VpcId |||
||+------------+--------------------------+||
||| available | vpc-0a593c77a7c18705d |||
||+------------+--------------------------+||
||| Tags |||
||+--------------+------------------------+||
||| Key | Value |||
||+--------------+------------------------+||
||| Name | test-igw |||
||+--------------+------------------------+||
\# aws ec2 describe-route-tables --filter "Name=vpc-id,Values=$test_vpc"
----------------------------------------
{
"RouteTables": [
{
"Associations": [
{
"Main": true,
"RouteTableAssociationId": "rtbassoc-0f6247e439af295bd",
"RouteTableId": "rtb-0d80109586ce7af63",
"AssociationState": {
"State": "associated"
}
}
],
"PropagatingVgws": [],
"RouteTableId": "rtb-0d80109586ce7af63",
"Routes": [
{
"DestinationCidrBlock": "192.168.0.0/16",
"GatewayId": "local",
"Origin": "CreateRouteTable",
"State": "active"
}
],
"Tags": [],
"VpcId": "vpc-0a593c77a7c18705d",
"OwnerId": "756852414300"
}
]
}
----------------------------------------
\# test_pub_rtb=rtb-0d80109586ce7af63
\# aws ec2 create-route --route-table-id $test_pub_rtb --destination-cidr-block 0.0.0.0/0 --gateway-id $test_igw
\# aws ec2 create-tags --resources $test_pub_rtb --tags "Key=Name,Value=test-pub-rtb"
\# aws ec2 describe-route-tables --route-table-ids $test_pub_rtb --output table
----------------------------------------
-------------------------------------------------------------------------------------
| DescribeRouteTables |
+-----------------------------------------------------------------------------------+
|| RouteTables ||
|+------------------------------+--------------------------------------------------+|
|| OwnerId | 756852414300 ||
|| RouteTableId | rtb-0d80109586ce7af63 ||
|| VpcId | vpc-0a593c77a7c18705d ||
|+------------------------------+--------------------------------------------------+|
||| Associations |||
||+------------------------------------+------------------------------------------+||
||| Main | True |||
||| RouteTableAssociationId | rtbassoc-0f6247e439af295bd |||
||| RouteTableId | rtb-0d80109586ce7af63 |||
||+------------------------------------+------------------------------------------+||
|||| AssociationState ||||
|||+-----------------------------+-----------------------------------------------+|||
|||| State | associated ||||
|||+-----------------------------+-----------------------------------------------+|||
||| Routes |||
||+----------------------+-------------------------+--------------------+---------+||
||| DestinationCidrBlock | GatewayId | Origin | State |||
||+----------------------+-------------------------+--------------------+---------+||
||| 192.168.0.0/16 | local | CreateRouteTable | active |||
||| 0.0.0.0/0 | igw-0f9c8e2d78bb1739f | CreateRoute | active |||
||+----------------------+-------------------------+--------------------+---------+||
||| Tags |||
||+---------------------------+---------------------------------------------------+||
||| Key | Name |||
||| Value | test-pub-rtb |||
||+---------------------------+---------------------------------------------------+||
----------------------------------------
\# aws ec2 describe-subnets --filters "Name=vpc-id,Values=$test_vpc" --query 'Subnets[*].{ID:SubnetId,CIDR:CidrBlock,TAGS:Tags[0].Value}'
----------------------------------------
[
{
"ID": "subnet-07f4a37901109851d",
"CIDR": "192.168.0.0/20",
"TAGS": "test-pub-2a"
},
{
"ID": "subnet-02eb311c6fe50328e",
"CIDR": "192.168.80.0/20",
"TAGS": "test-pvt-2b"
},
{
"ID": "subnet-0f46a5b7a62922535",
"CIDR": "192.168.64.0/20",
"TAGS": "test-pvt-2a"
},
{
"ID": "subnet-0a3922448d2cd1f60",
"CIDR": "192.168.112.0/20",
"TAGS": "test-pvt-2d"
},
{
"ID": "subnet-09165b95a79cd598d",
"CIDR": "192.168.48.0/20",
"TAGS": "test-pub-2d"
},
{
"ID": "subnet-05553c8e8d598d500",
"CIDR": "192.168.16.0/20",
"TAGS": "test-pub-2b"
},
{
"ID": "subnet-03ba579adf9bbcc72",
"CIDR": "192.168.32.0/20",
"TAGS": "test-pub-2c"
},
{
"ID": "subnet-06c882d5a148970bc",
"CIDR": "192.168.96.0/20",
"TAGS": "test-pvt-2c"
}
]
----------------------------------------
\# test_pub_2a=subnet-07f4a37901109851d
\# test_pub_2b=subnet-05553c8e8d598d500
\# test_pub_2c=subnet-03ba579adf9bbcc72
\# test_pub_2d=subnet-09165b95a79cd598d
\# test_pvt_2a=subnet-0f46a5b7a62922535
\# test_pvt_2b=subnet-02eb311c6fe50328e
\# test_pvt_2c=subnet-06c882d5a148970bc
\# test_pvt_2d=subnet-0a3922448d2cd1f60
\# aws ec2 associate-route-table --subnet-id $test_pub_2a --route-table-id $test_pub_rtb
----------------------------------------
{
"AssociationId": "rtbassoc-022a09f7e951afc02",
"AssociationState": {
"State": "associated"
}
}
----------------------------------------
\# aws ec2 associate-route-table --subnet-id $test_pub_2b --route-table-id $test_pub_rtb
\# aws ec2 associate-route-table --subnet-id $test_pub_2c --route-table-id $test_pub_rtb
\# aws ec2 associate-route-table --subnet-id $test_pub_2d --route-table-id $test_pub_rtb
\# aws ec2 modify-subnet-attribute --subnet-id $test_pub_2a --map-public-ip-on-launch
\# aws ec2 modify-subnet-attribute --subnet-id $test_pub_2b --map-public-ip-on-launch
\# aws ec2 modify-subnet-attribute --subnet-id $test_pub_2c --map-public-ip-on-launch
\# aws ec2 modify-subnet-attribute --subnet-id $test_pub_2d --map-public-ip-on-launch
\# aws ec2 create-route-table --vpc-id $test_vpc
----------------------------------------
{
"RouteTable": {
"Associations": [],
"PropagatingVgws": [],
"RouteTableId": "rtb-0af42ec385b26d534",
"Routes": [
{
"DestinationCidrBlock": "192.168.0.0/16",
"GatewayId": "local",
"Origin": "CreateRouteTable",
"State": "active"
}
],
"Tags": [],
"VpcId": "vpc-0a593c77a7c18705d",
"OwnerId": "756852414300"
}
}
----------------------------------------
\# test_pvt_rtb=rtb-0af42ec385b26d534
\# aws ec2 create-tags --resources $test_pvt_rtb --tags "Key=Name,Value=test-pvt-rtb"
\# aws ec2 associate-route-table --subnet-id $test_pvt_2a --route-table-id $test_pvt_rtb
\# aws ec2 associate-route-table --subnet-id $test_pvt_2b --route-table-id $test_pvt_rtb
\# aws ec2 associate-route-table --subnet-id $test_pvt_2c --route-table-id $test_pvt_rtb
\# aws ec2 associate-route-table --subnet-id $test_pvt_2d --route-table-id $test_pvt_rtb
\# aws ec2 modify-vpc-attribute --vpc-id $test_vpc --enable-dns-hostnames
키페어, 보안 그룹 생성
\# aws ec2 create-key-pair --key-name test-key --query 'KeyMaterial' --output text > test-key.pem
\# chmod 400 test-key.pem
\# aws ec2 create-security-group --group-name test-sg-web --description "Security group for HTTP_SSH access" --vpc-id $test_vpc --tag-specification "ResourceType=security-group,Tags=[{Key=Name,Value=test-sg-web}]"
----------------------------------------
{
"GroupId": "sg-0546357b17d315a02",
"Tags": [
{
"Key": "Name",
"Value": "test-sg-web"
}
]
}
----------------------------------------
\# test_web_sg=sg-0546357b17d315a02
\# aws ec2 authorize-security-group-ingress --group-id $test_web_sg --protocol tcp --port 80 --cidr 106.253.56.124/32
----------------------------------------
{
"Return": true,
"SecurityGroupRules": [
{
"SecurityGroupRuleId": "sgr-0e370e9237d7e3176",
"GroupId": "sg-0546357b17d315a02",
"GroupOwnerId": "756852414300",
"IsEgress": false,
"IpProtocol": "tcp",
"FromPort": 80,
"ToPort": 80,
"CidrIpv4": "106.253.56.124/32"
}
]
}
----------------------------------------
\# aws ec2 authorize-security-group-ingress --group-id $test_web_sg --protocol tcp --port 80 --cidr 0.0.0.0/0
\# aws ec2 authorize-security-group-ingress --group-id $test_web_sg --protocol icmp --port -1 --cidr 0.0.0.0/0
\# aws ec2 describe-security-groups --group-id $test_web_sg --output table
---------------------------------------------------------
| DescribeSecurityGroups |
+-------------------------------------------------------+
|| SecurityGroups ||
|+--------------+--------------------------------------+|
|| Description | Security group for HTTP_SSH access ||
|| GroupId | sg-0546357b17d315a02 ||
|| GroupName | test-sg-web ||
|| OwnerId | 756852414300 ||
|| VpcId | vpc-0a593c77a7c18705d ||
|+--------------+--------------------------------------+|
||| IpPermissions |||
||+---------------------------------+-----------------+||
||| FromPort | 80 |||
||| IpProtocol | tcp |||
||| ToPort | 80 |||
||+---------------------------------+-----------------+||
|||| IpRanges ||||
|||+-------------------------------------------------+|||
|||| CidrIp ||||
|||+-------------------------------------------------+|||
|||| 106.253.56.124/32 ||||
|||| 0.0.0.0/0 ||||
|||+-------------------------------------------------+|||
||| IpPermissions |||
||+---------------------------------+-----------------+||
||| FromPort | 22 |||
||| IpProtocol | tcp |||
||| ToPort | 22 |||
||+---------------------------------+-----------------+||
|||| IpRanges ||||
|||+-------------------------------------------------+|||
|||| CidrIp ||||
|||+-------------------------------------------------+|||
|||| 0.0.0.0/0 ||||
|||| 106.253.56.124/32 ||||
|||+-------------------------------------------------+|||
||| IpPermissions |||
||+--------------------------------+------------------+||
||| FromPort | -1 |||
||| IpProtocol | icmp |||
||| ToPort | -1 |||
||+--------------------------------+------------------+||
|||| IpRanges ||||
|||+--------------------+----------------------------+|||
|||| CidrIp | 0.0.0.0/0 ||||
|||+--------------------+----------------------------+|||
||| IpPermissionsEgress |||
||+-----------------------------------+---------------+||
||| IpProtocol | -1 |||
||+-----------------------------------+---------------+||
|||| IpRanges ||||
|||+--------------------+----------------------------+|||
|||| CidrIp | 0.0.0.0/0 ||||
|||+--------------------+----------------------------+|||
||| Tags |||
||+------------------+--------------------------------+||
||| Key | Name |||
||| Value | test-sg-web |||
||+------------------+--------------------------------+||
볼륨 및 인스턴스 만들기
- 정의할 파일 생성
/dev/xvda : 루트 볼륨/dev/xvdb : 추가 볼륨 (선택)- 단위 : GB
\# vi mapping.json
----------------------------------------
[
{
"DeviceName": "/dev/xvda",
"Ebs": {
"VolumeSize": 8
}
},
{
"DeviceName": "/dev/xvdb",
"Ebs": {
"VolumeSize": 8
}
}
]
----------------------------------------
\# vi my_script.txt
----------------------------------------
yum install -y httpd
systemctl enable --now httpd
echo "<h1>Hello AWS CLI</h1>" > /var/www/html/index.html
----------------------------------------
인스턴스 생성
- AMI 카탈로그 정도에 있는 AMI-id 복사
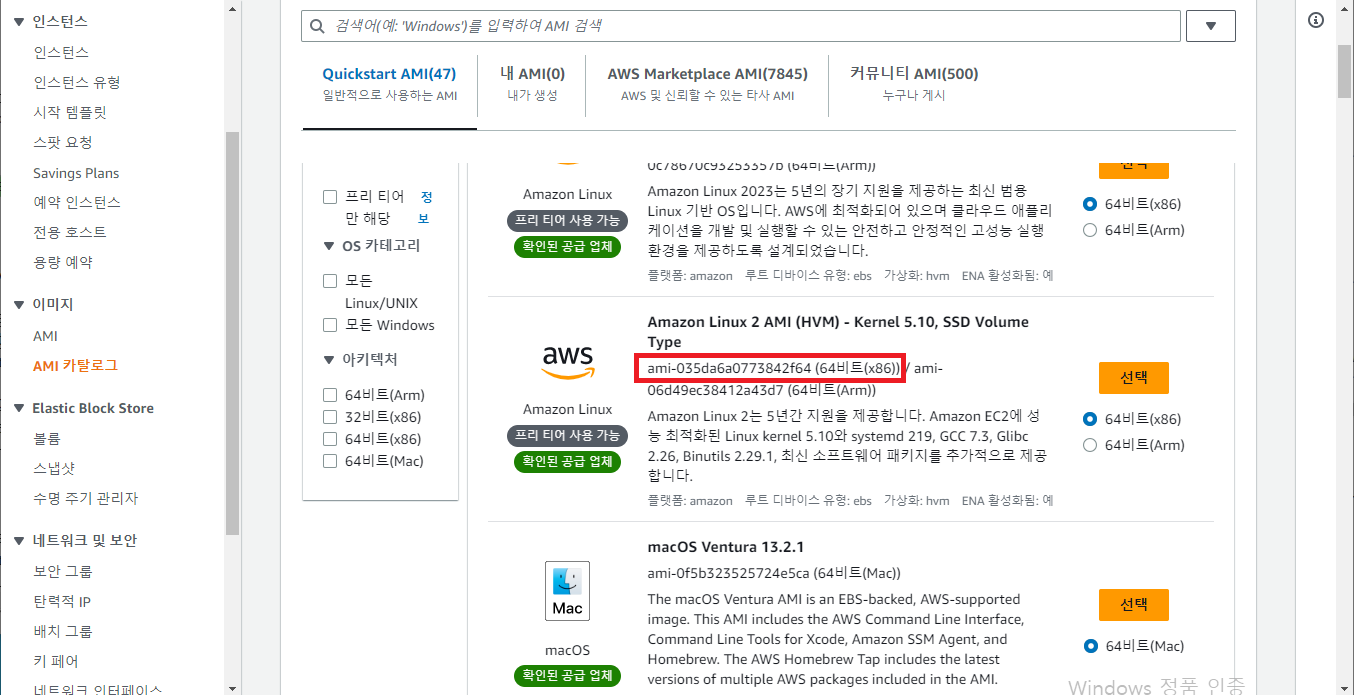
- 생성할 EC2 갯수, ami 이미지 등등 셋팅
--tag-specifications : s인 이유, EC2와 볼륨에 각각 태그를 달기 때문
\# aws ec2 run-instances \
--image-id ami-035da6a0773842f64 \
--count 1 \
--instance-type t2.micro \
--key-name test-key \
--security-group-ids $test_web_sg \
--subnet-id $test_pub_2a \
--block-device-mappings file://mapping.json \
--user-data file://my_script.txt \
--tag-specifications 'ResourceType=instance,Tags=[{Key=Name,Value=test-web}]' 'ResourceType=volume,Tags=[{Key=Name,Value=test-root}]'
----------------------------------------
{
"Groups": [],
"Instances": [
{
"AmiLaunchIndex": 0,
"ImageId": "ami-03db74b70e1da9c56",
"InstanceId": "i-03005e4701436c3cf",
"InstanceType": "t2.micro",
"KeyName": "test-key",
"LaunchTime": "2023-05-15T08:18:39+00:00",
"Monitoring": {
"State": "disabled"
},
"Placement": {
"AvailabilityZone": "ap-northeast-2a",
"GroupName": "",
"Tenancy": "default"
},
"PrivateDnsName": "ip-192-168-5-20.ap-northeast-2.compute.internal",
"PrivateIpAddress": "192.168.5.20",
"ProductCodes": [],
"PublicDnsName": "",
"State": {
"Code": 0,
"Name": "pending"
},
"StateTransitionReason": "",
"SubnetId": "subnet-07f4a37901109851d",
"VpcId": "vpc-0a593c77a7c18705d",
"Architecture": "x86_64",
"BlockDeviceMappings": [],
"ClientToken": "aabdfc26-9c61-4625-975a-995efe12b4d4",
"EbsOptimized": false,
"EnaSupport": true,
"Hypervisor": "xen",
"NetworkInterfaces": [
{
"Attachment": {
"AttachTime": "2023-05-15T08:18:39+00:00",
"AttachmentId": "eni-attach-08dd5616e017b2d26",
"DeleteOnTermination": true,
"DeviceIndex": 0,
"Status": "attaching",
"NetworkCardIndex": 0
},
"Description": "",
"Groups": [
{
"GroupName": "test-sg-web",
"GroupId": "sg-0546357b17d315a02"
}
],
"Ipv6Addresses": [],
"MacAddress": "02:0d:3d:82:82:ea",
"NetworkInterfaceId": "eni-01587ad2879903852",
"OwnerId": "756852414300",
"PrivateDnsName": "ip-192-168-5-20.ap-northeast-2.compute.internal",
"PrivateIpAddress": "192.168.5.20",
"PrivateIpAddresses": [
{
"Primary": true,
"PrivateDnsName": "ip-192-168-5-20.ap-northeast-2.compute.internal",
"PrivateIpAddress": "192.168.5.20"
}
],
"SourceDestCheck": true,
"Status": "in-use",
"SubnetId": "subnet-07f4a37901109851d",
"VpcId": "vpc-0a593c77a7c18705d",
"InterfaceType": "interface"
}
],
"RootDeviceName": "/dev/xvda",
"RootDeviceType": "ebs",
"SecurityGroups": [
{
"GroupName": "test-sg-web",
"GroupId": "sg-0546357b17d315a02"
}
],
"SourceDestCheck": true,
"StateReason": {
"Code": "pending",
"Message": "pending"
},
"Tags": [
{
"Key": "Name",
"Value": "test-web"
}
],
"VirtualizationType": "hvm",
"CpuOptions": {
"CoreCount": 1,
"ThreadsPerCore": 1
},
"CapacityReservationSpecification": {
"CapacityReservationPreference": "open"
},
"MetadataOptions": {
"State": "pending",
"HttpTokens": "optional",
"HttpPutResponseHopLimit": 1,
"HttpEndpoint": "enabled",
"HttpProtocolIpv6": "disabled",
"InstanceMetadataTags": "disabled"
},
"EnclaveOptions": {
"Enabled": false
},
"PrivateDnsNameOptions": {
"HostnameType": "ip-name",
"EnableResourceNameDnsARecord": false,
"EnableResourceNameDnsAAAARecord": false
},
"MaintenanceOptions": {
"AutoRecovery": "default"
},
"CurrentInstanceBootMode": "legacy-bios"
}
],
"OwnerId": "756852414300",
"ReservationId": "r-08819bc619ee076d0"
}
----------------------------------------
\# test_iid=i-03005e4701436c3cf
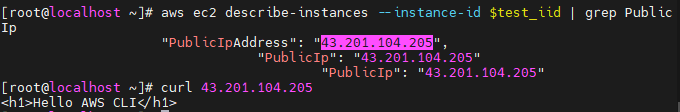
\# aws ec2 describe-instances --instance-id $test_iid | grep PublicIp
curl 43.201.104.205
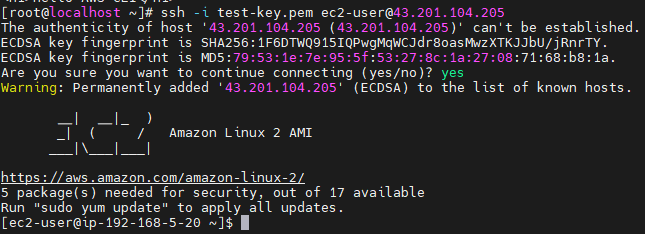
\# ssh -i test-key.pem ec2-user@43.201.104.205
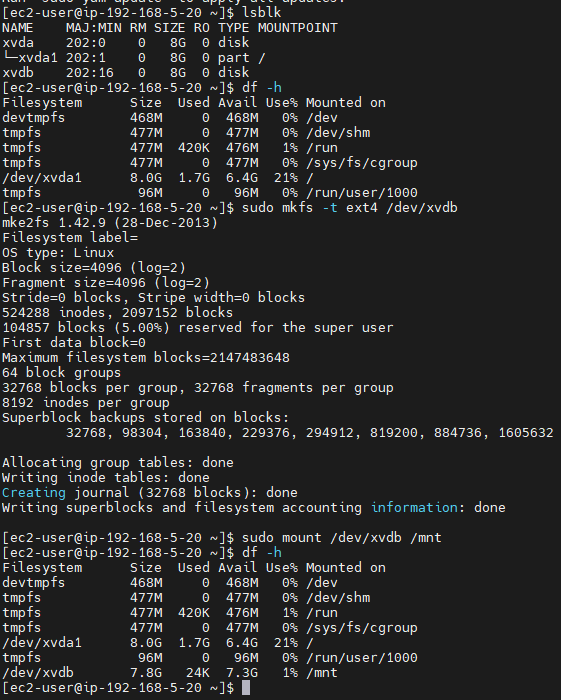
\# lsblk
\# df -h
\# sudo mkfs -t ext4 /dev/xvdb
\# sudo mount /dev/xvdb /mnt
\# df -h
리소스 정리
\# aws ec2 terminate-instances --instance-id $test_iid
----------------------------------------
{
"TerminatingInstances": [
{
"CurrentState": {
"Code": 32,
"Name": "shutting-down"
},
"InstanceId": "i-03005e4701436c3cf",
"PreviousState": {
"Code": 16,
"Name": "running"
}
}
]
}
----------------------------------------
\# aws ec2 delete-security-group --group-id $test_web_sg
\# aws ec2 delete-subnet --subnet-id $test_pub_2a
\# aws ec2 delete-subnet --subnet-id $test_pub_2b
\# aws ec2 delete-subnet --subnet-id $test_pub_2c
\# aws ec2 delete-subnet --subnet-id $test_pub_2d
\# aws ec2 delete-subnet --subnet-id $test_pvt_2a
\# aws ec2 delete-subnet --subnet-id $test_pvt_2b
\# aws ec2 delete-subnet --subnet-id $test_pvt_2c
\# aws ec2 delete-subnet --subnet-id $test_pvt_2d
\# aws ec2 detach-internet-gateway --internet-gateway-id $test_igw --vpc-id $test_vpc
\# aws ec2 delete-internet-gateway --internet-gateway-id $test_igw
\# aws ec2 delete-route-table --route-table-id $test_pvt_rtb
\# aws ec2 delete-route --route-table-id $test_pub_rtb --destination-cidr-block 0.0.0.0/0
\# aws ec2 delete-vpc --vpc-id $test_vpc















