- Azure Resource Manager, GCP Deployment Manager
주요 섹션 설명
1. Resources(생성)
2. Parameters(입력)
- Parameters
- 명령줄 도구에 입력하는 매개변수와 동일하게 스택을 만들거나 업데이트할 때 정의하는 입력값
- 파라미터는 템플릿의 변경 없이도 스택을 커스터마이즈할 수 있게 해줍니다.
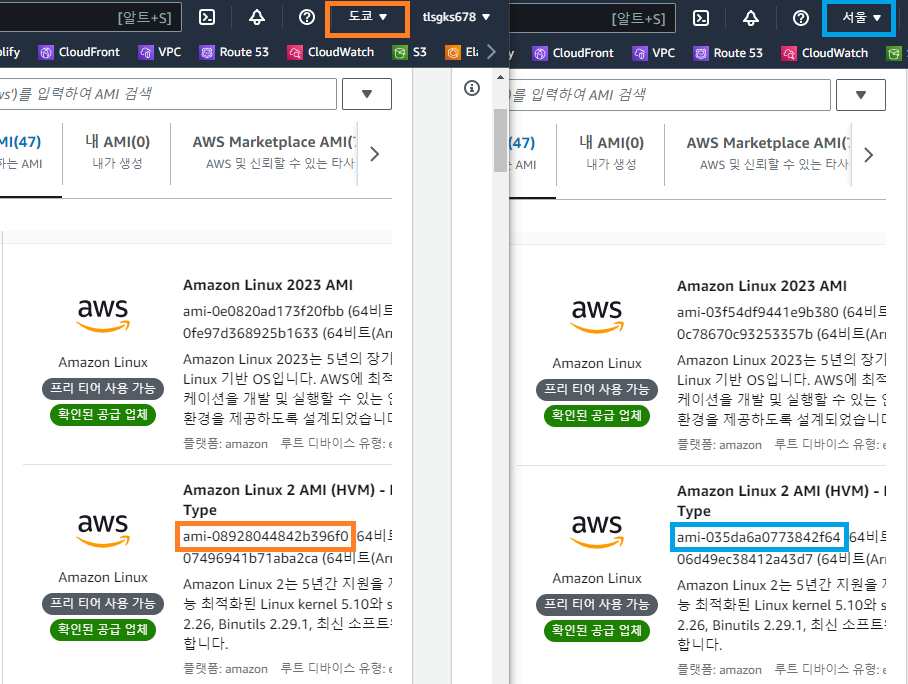
- AMI ID, VPC ID, Subnet ID등과 같은 매개변수를 사용가능하다.
- 도쿄의 AMI ID와 서울의 AMI ID는 다르다.
3. Output(출력)
- Output
- 스택이 완료된 후에 결과물을 출력하려고 할때 유용
- 예를 들어 ELB의 퍼블릭 URL이나 EC2의 퍼블릭 IP를 출력한다.
4. Mapping(지정)
- Mappings
- 리전의 특화된 템플릿에서 어떠한 요소를 참조할 때 필요
- 예를 들어 템플릿에 EC2 AMI ID에 대한 매핑을 지정하는 것으로 💦 AMI ID가 리전에 특화된 리소스이기 때문에 유효한 AMI ID를 리전별로 지정하려고 할때 사용한다.
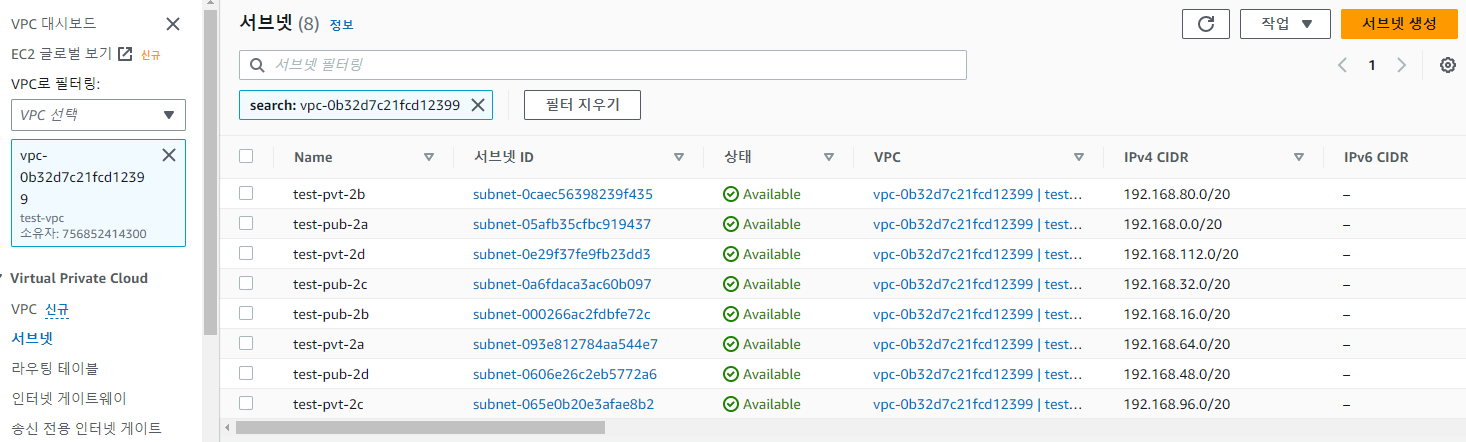
VPC 생성 실습
vi test-vpc.yaml
----------------------------------------
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: test-vpc
PUB2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2a
PUB2B:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.16.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2b
PUB2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2c
PUB2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-2d
PVT2A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2a
VpcId: !Ref VPC
CidrBlock: 192.168.64.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2a
PVT2B:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2b
VpcId: !Ref VPC
CidrBlock: 192.168.80.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2b
PVT2C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2c
VpcId: !Ref VPC
CidrBlock: 192.168.96.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2c
PVT2D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-2d
VpcId: !Ref VPC
CidrBlock: 192.168.112.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-2d
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: test-igw
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PUBRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pub-rtb
PVTRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pvt-rtb
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref PUBRTB
PUB2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2A
PUB2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2B
PUB2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2C
PUB2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB2D
PVT2ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2A
PVT2BRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2B
PVT2CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2C
PVT2DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT2D
----------------------------------------
- CloudFormation용 저장소 ❌
- 이미 가지고 있는 S3 또는 템플릿 파일 업로드를 이용(버킷이 생성된다.)
스택 생성 클릭
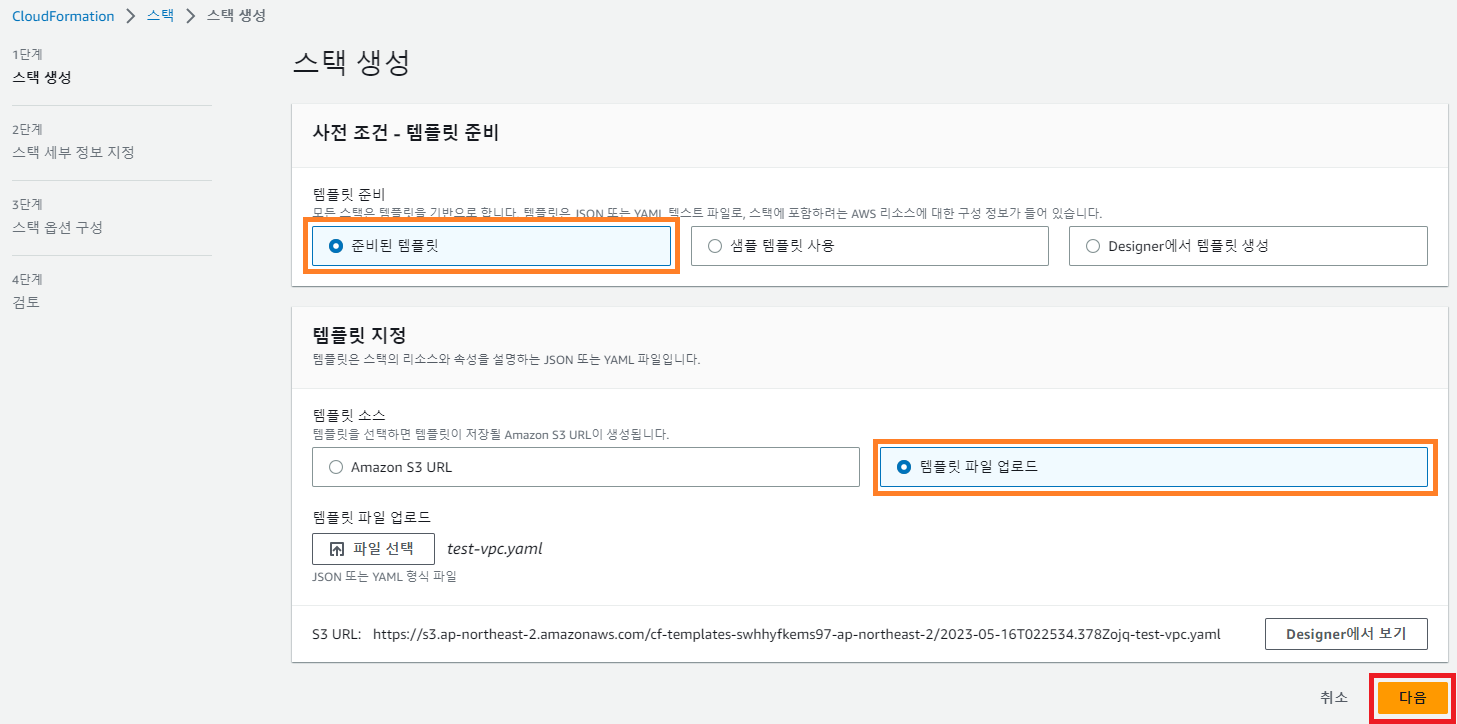
- 템플릿 지정 - 템플릿 파일 업로드
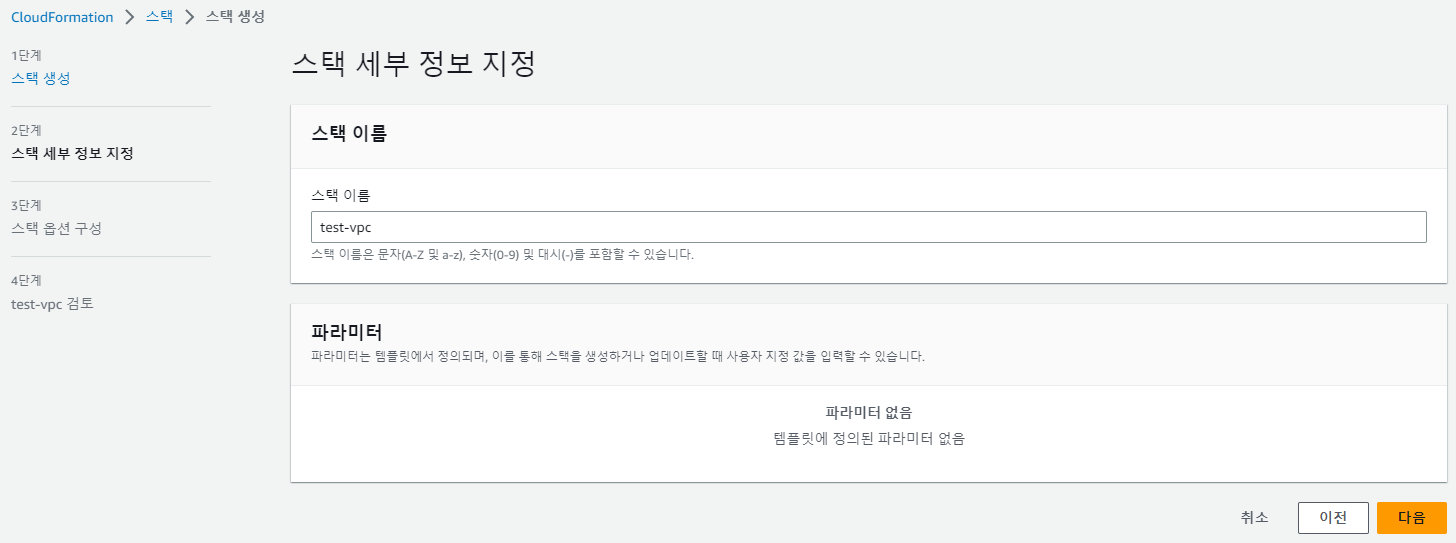
- 스택 세부 정보 지정 - 이름 지정
- 스택 옵션 구성 (기본값)
- 검토 - 전송 클릭
- 생성 결과
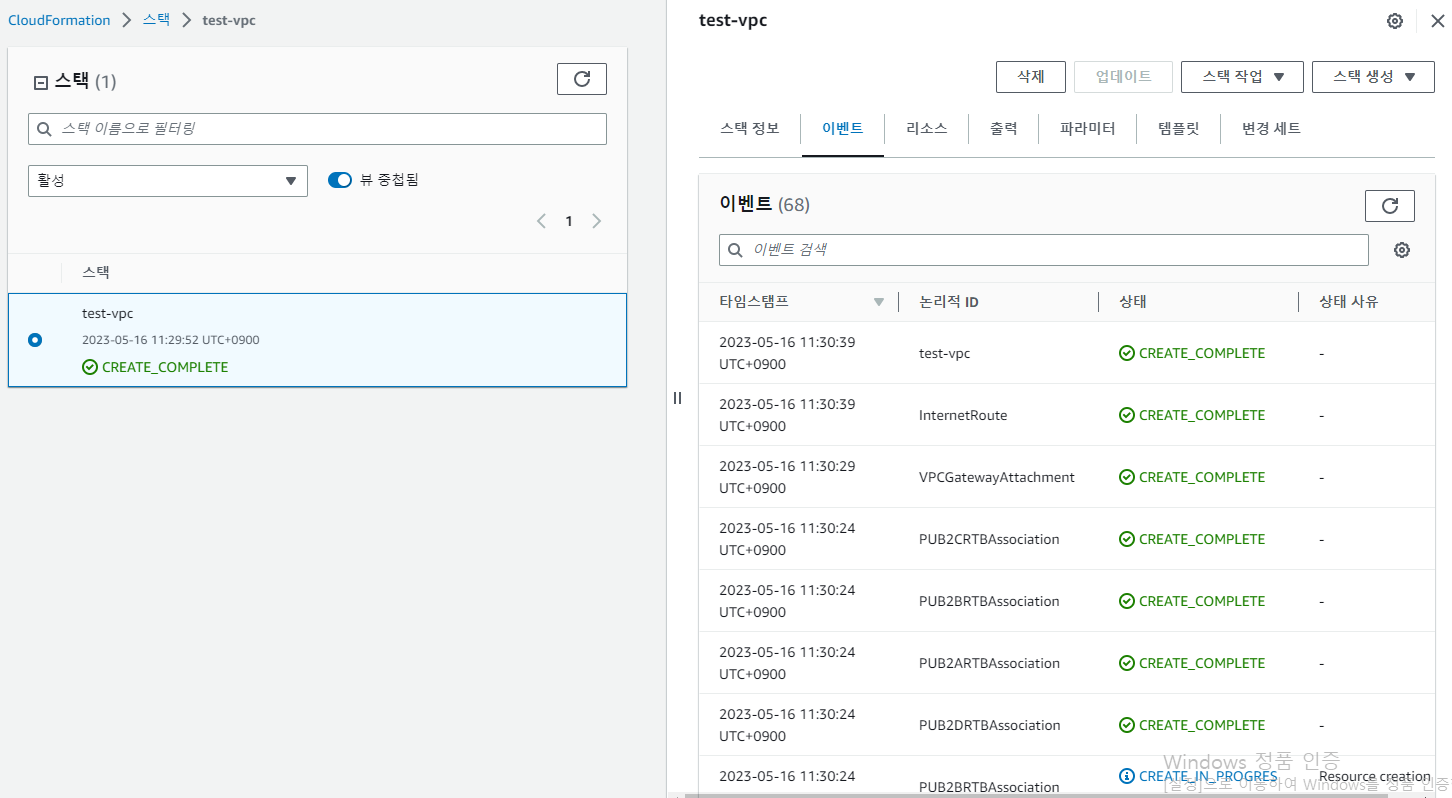
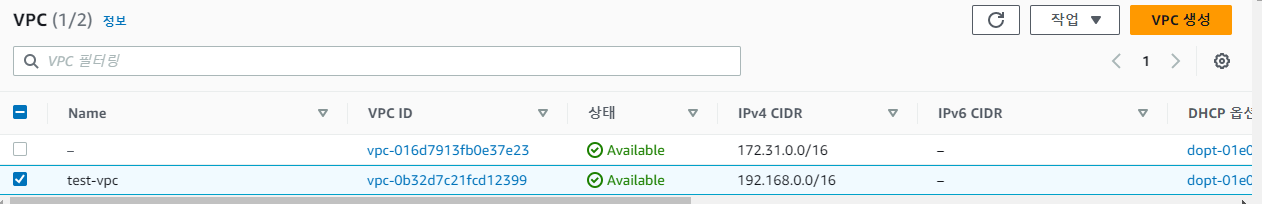
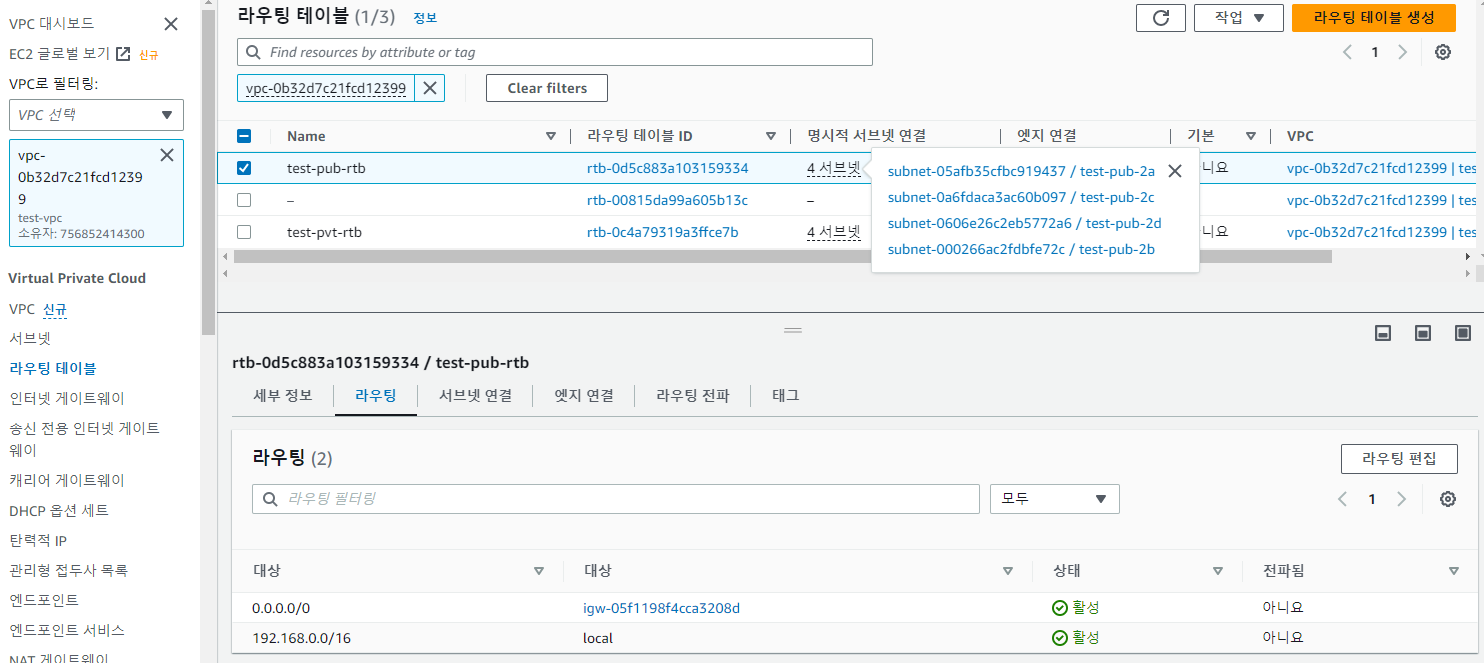
- VPC 가서 확인시 정상적으로 생성된 것 확인 가능
EC2 생성 실습
vi test-ec2.yaml
----------------------------------------
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-035da6a0773842f64
ap-northeast-1:
AMIID: ami-08928044842b396f0
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-0b32d7c21fcd12399
Description: VPC ID.
Subnet:
Type: String
Default: subnet-05afb35cfbc919437
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: test-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "test-sg-web"
GroupDescription: "test-sg-web"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 106.253.56.124/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Insteance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref Subnet
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: test-ec2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["EC2Insteance","PublicIp"]}
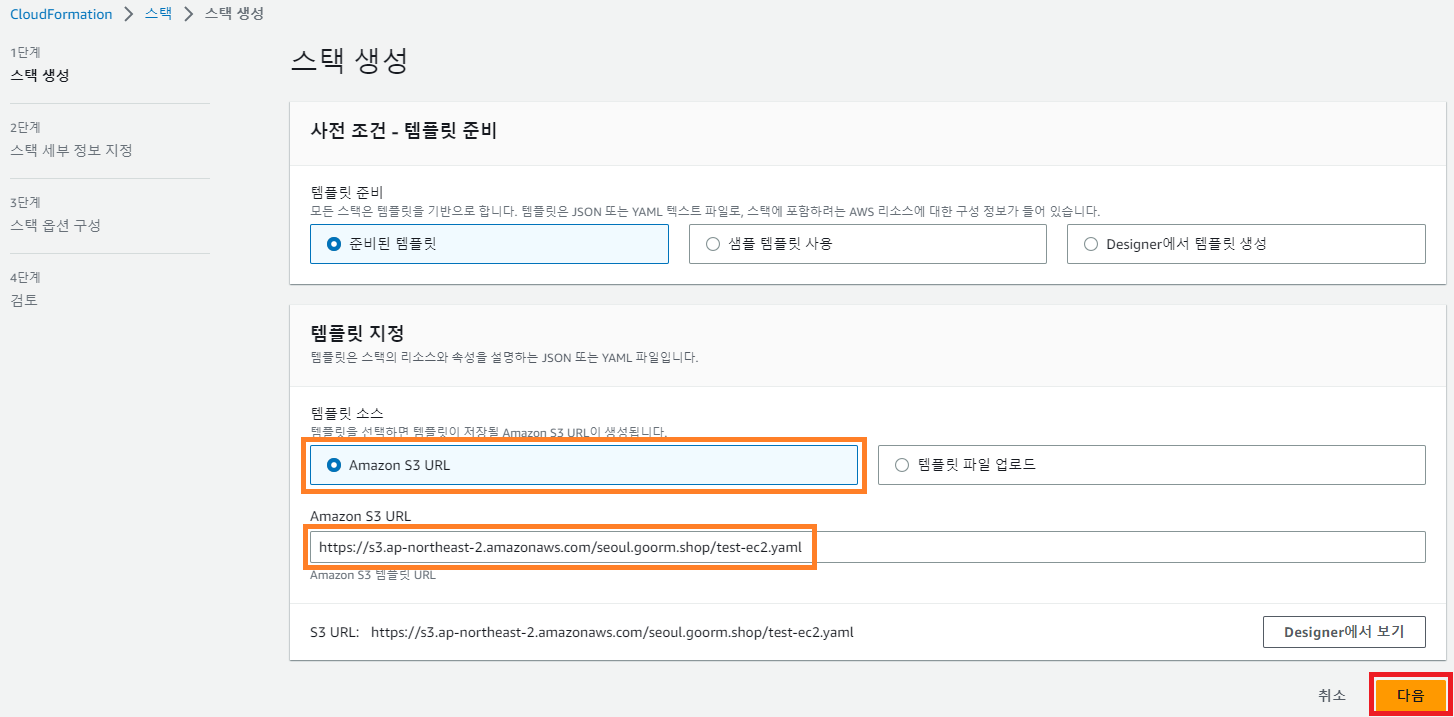
- S3 업로드
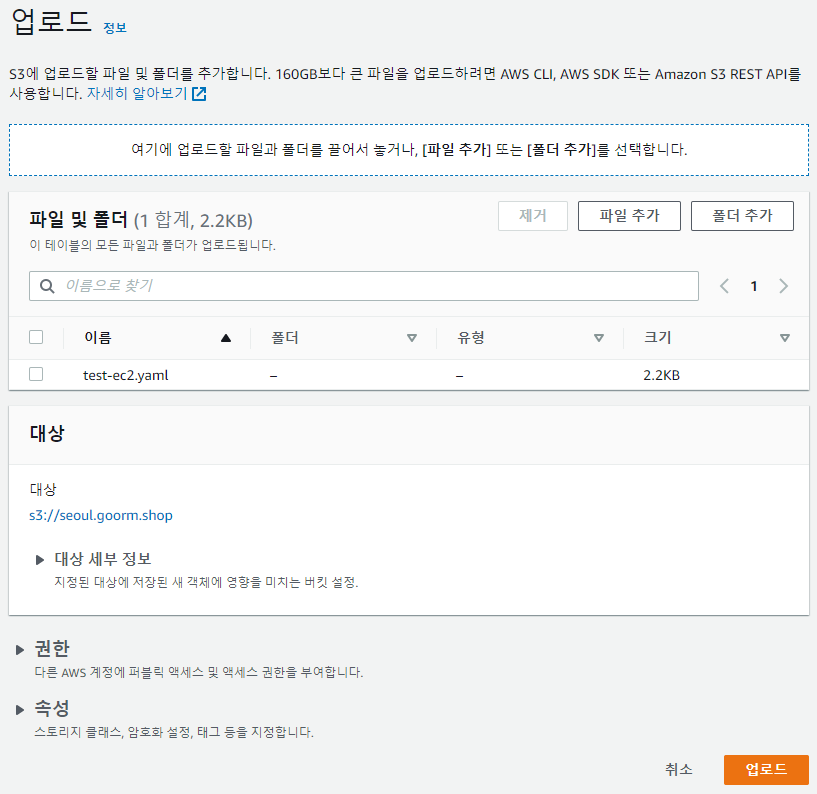
- S3 URL
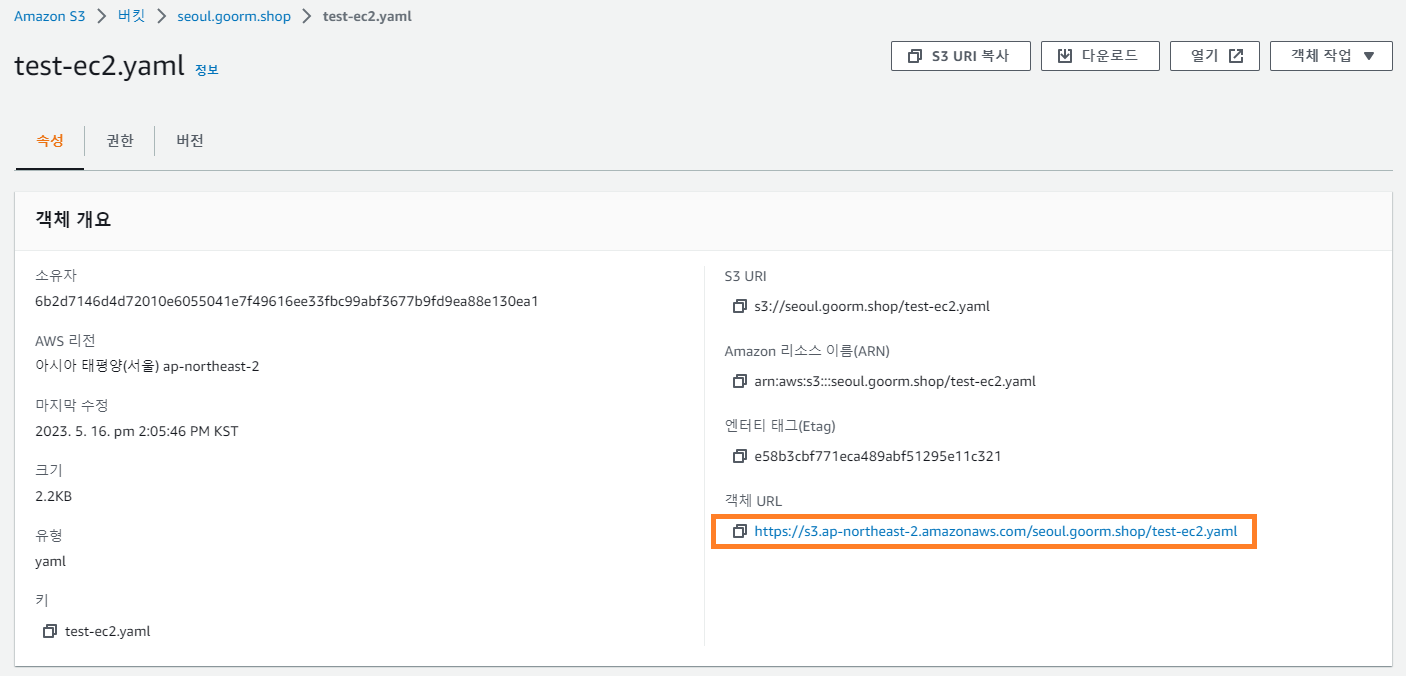
- 스택 생성
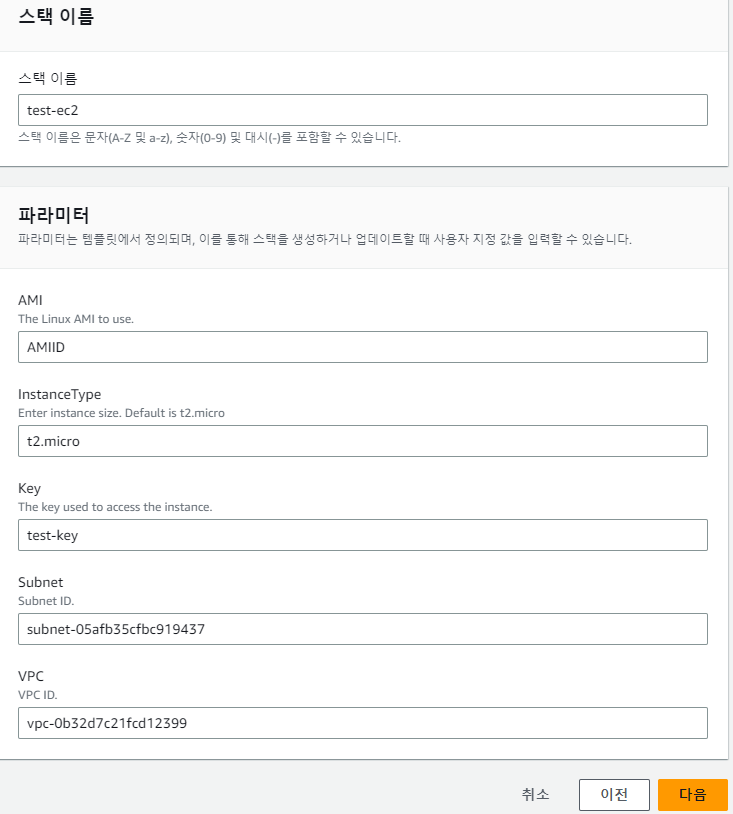
- 스택 세부 정보; yaml에 지정한 내용이 들어가 있다.
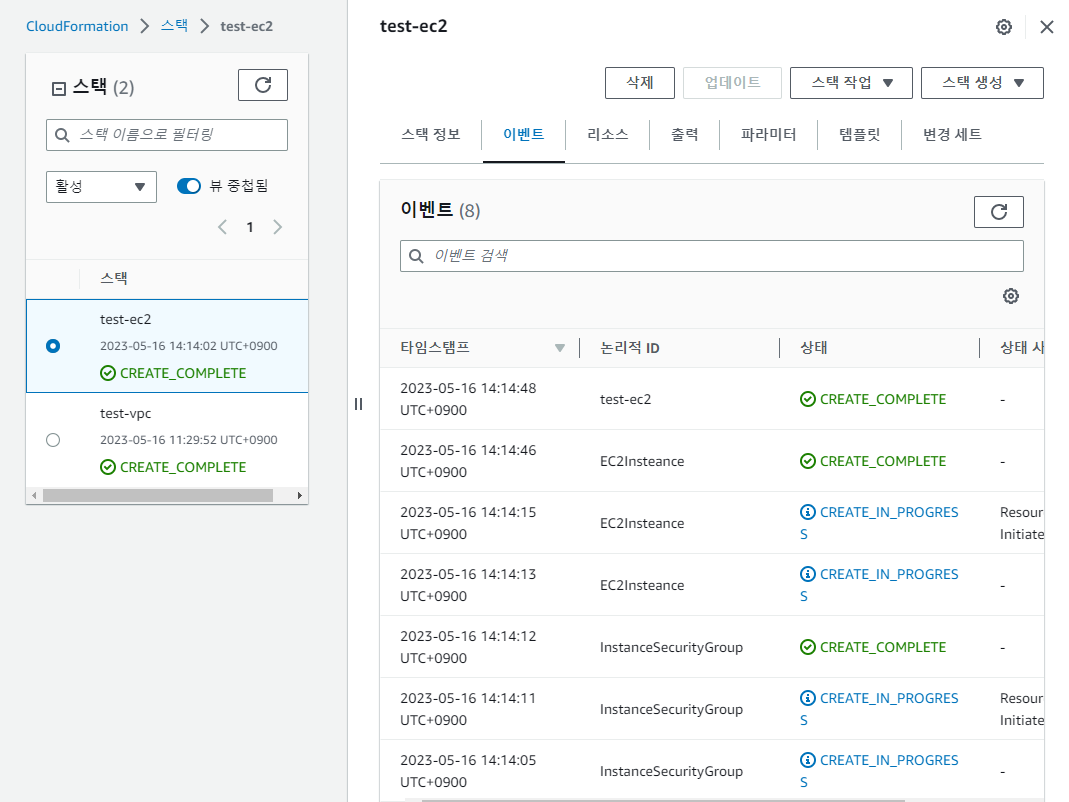
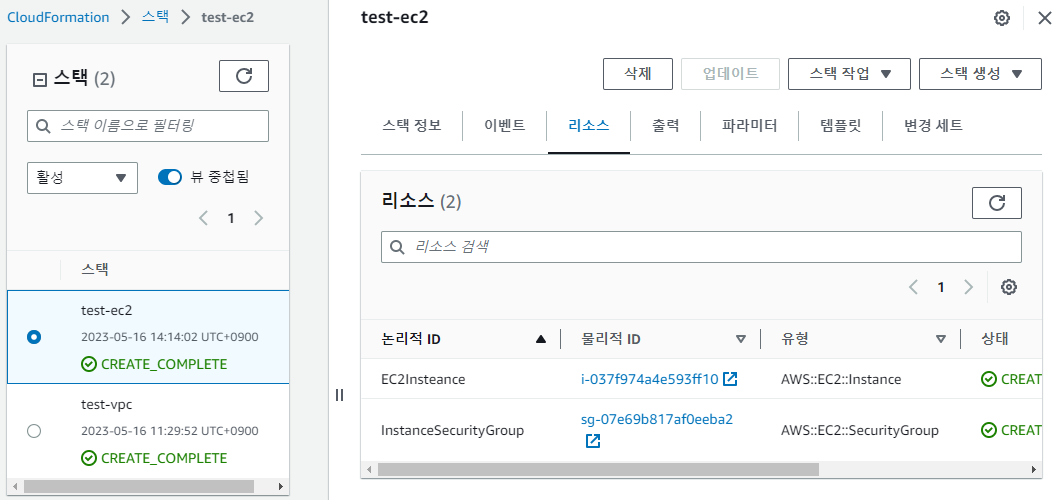
- 스택 결과
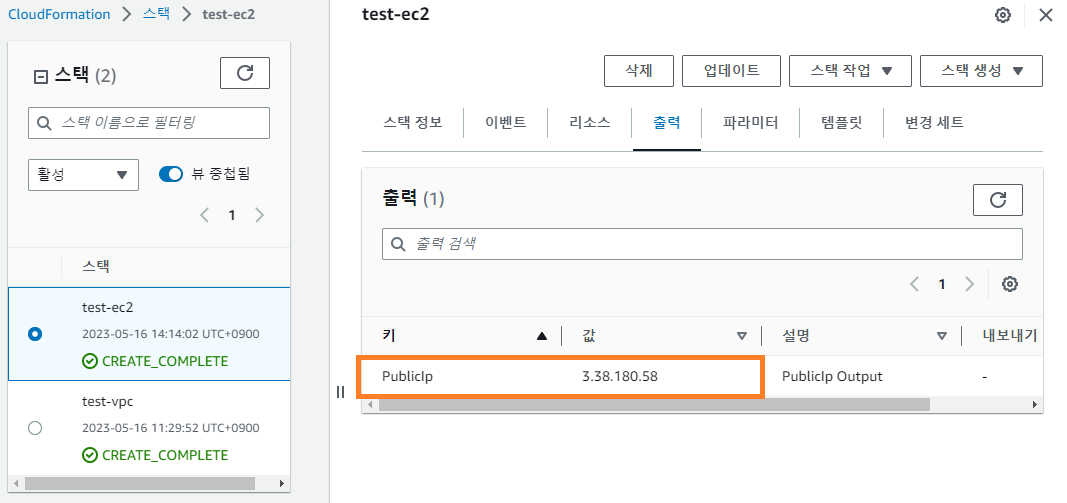
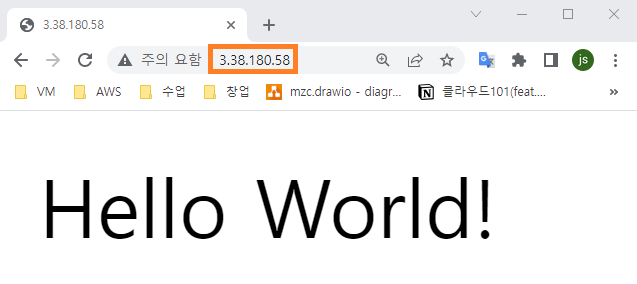
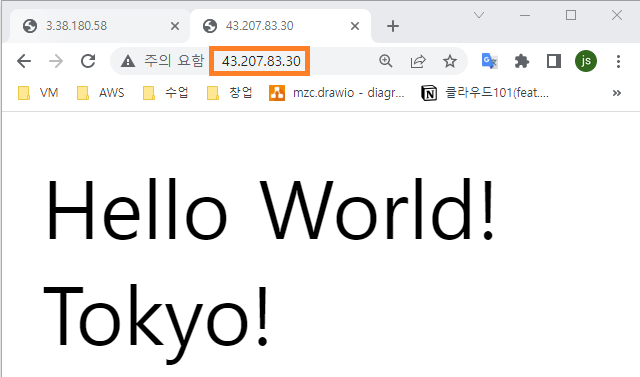
도쿄 리전에서 수행
- VPC 스택
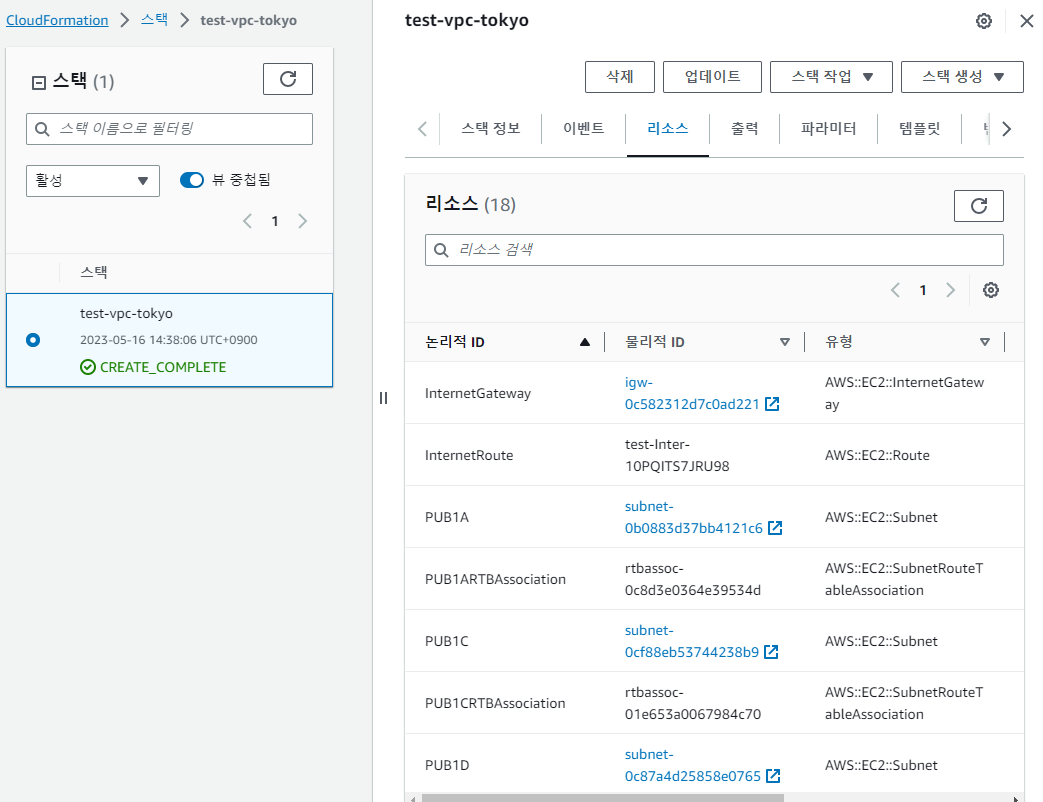
- VPC 리소스 생성 확인
- 도쿄리전 키페어 생성
aws ec2 create-key-pair --region ap-northeast-1 --key-name tokyo-key --query 'KeyMaterial' --output text > tokyo-key.pem
- EC2 스택; 파라미터 직접 입력 가능 (리소스 ID 복사후 입력)
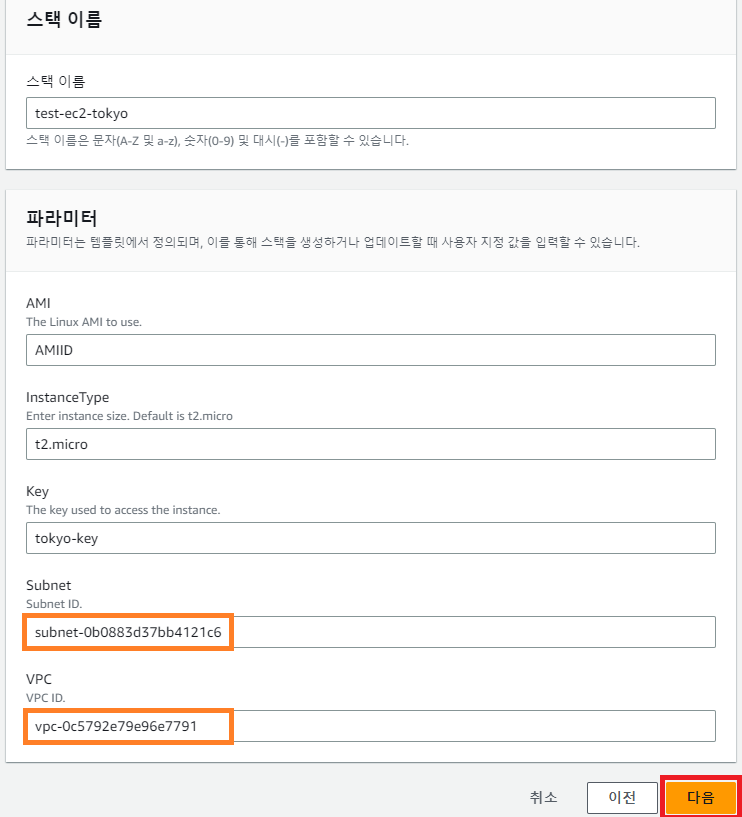
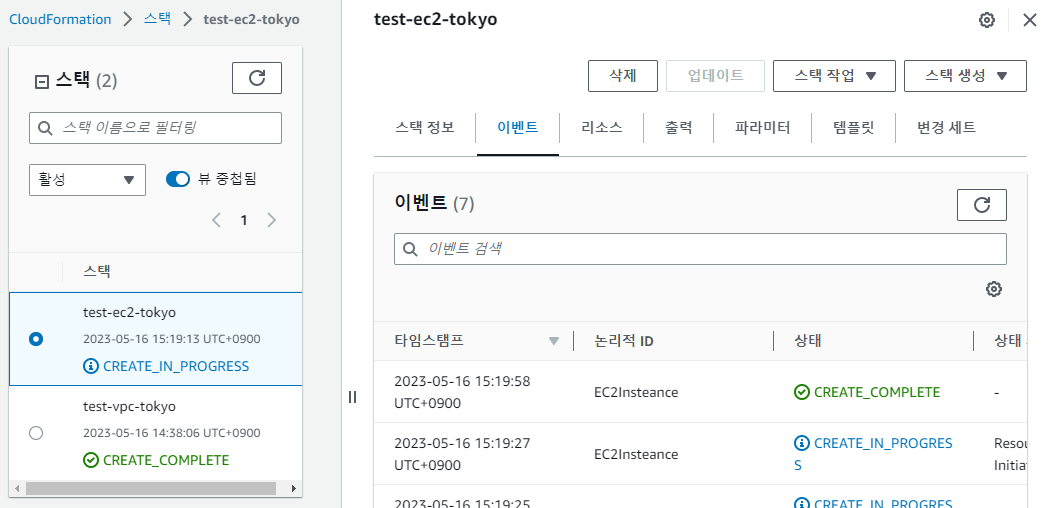
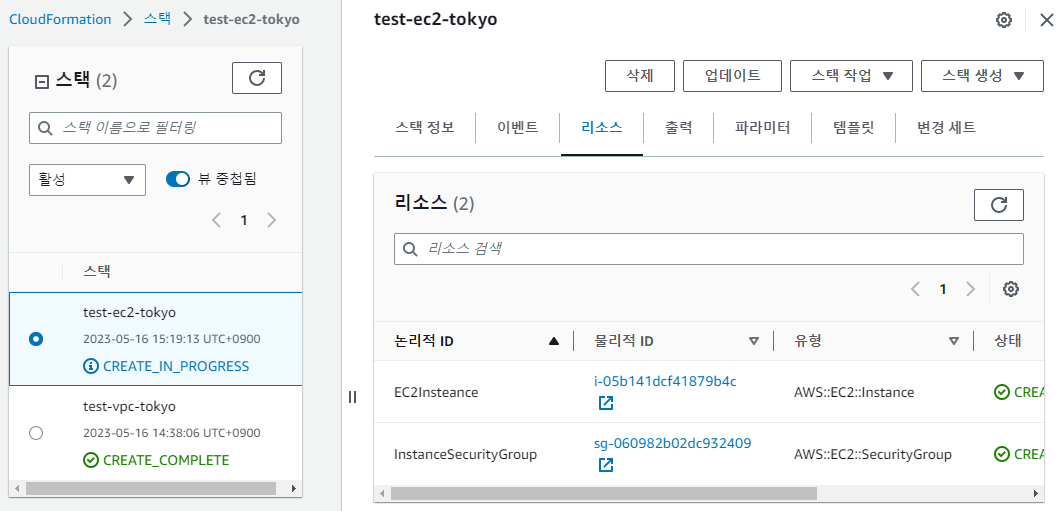
- EC2 리소스 생성 확인
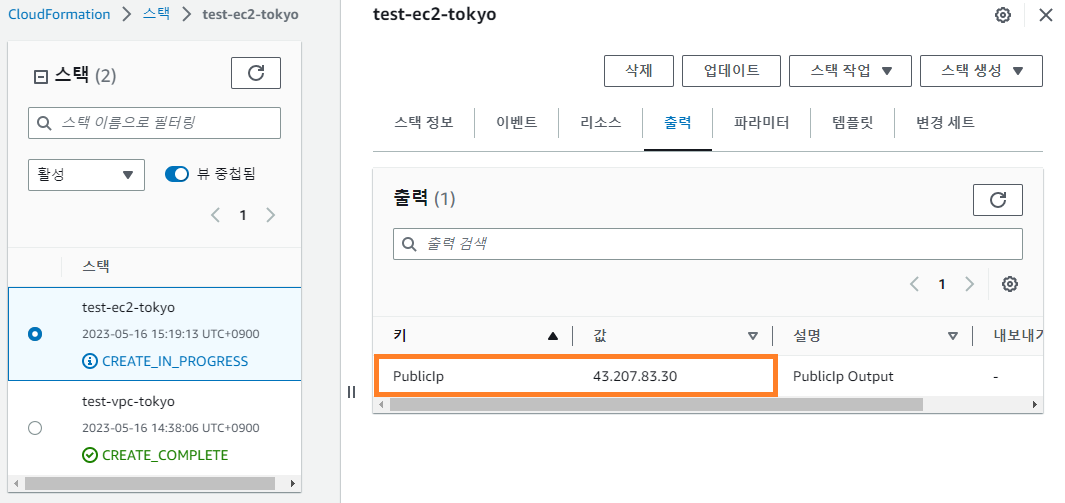
test-vpc-tokyo
AWSTemplateFormatVersion: 2010-09-09
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: 192.168.0.0/16
EnableDnsSupport: true
EnableDnsHostnames: true
InstanceTenancy: default
Tags:
- Key: Name
Value: test-vpc
PUB1A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.0.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1a
PUB1C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.16.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1c
PUB1D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.32.0/20
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: test-pub-1d
PVT1A:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1a
VpcId: !Ref VPC
CidrBlock: 192.168.48.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1a
PVT1C:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1c
VpcId: !Ref VPC
CidrBlock: 192.168.64.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1c
PVT1D:
Type: AWS::EC2::Subnet
Properties:
AvailabilityZone: ap-northeast-1d
VpcId: !Ref VPC
CidrBlock: 192.168.80.0/20
MapPublicIpOnLaunch: false
Tags:
- Key: Name
Value: test-pvt-1d
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: test-igw
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
VpcId: !Ref VPC
InternetGatewayId: !Ref InternetGateway
PUBRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pub-rtb
PVTRTB:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref VPC
Tags:
- Key: Name
Value: test-pvt-rtb
InternetRoute:
Type: AWS::EC2::Route
DependsOn: InternetGateway
Properties:
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
RouteTableId: !Ref PUBRTB
PUB1ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1A
PUB1CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1C
PUB1DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PUBRTB
SubnetId: !Ref PUB1D
PVT1ARTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1A
PVT1CRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1C
PVT1DRTBAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
RouteTableId: !Ref PVTRTB
SubnetId: !Ref PVT1D
AWSTemplateFormatVersion: 2010-09-09
Mappings:
RegionMap:
ap-northeast-2:
AMIID: ami-035da6a0773842f64
ap-northeast-1:
AMIID: ami-08928044842b396f0
Parameters:
InstanceType:
Type: String
Default: t2.micro
Description: Enter instance size. Default is t2.micro
VPC:
Type: String
Default: vpc-0b32d7c21fcd12399
Description: VPC ID.
Subnet:
Type: String
Default: subnet-05afb35cfbc919437
Description: Subnet ID.
AMI:
Type: String
Default: AMIID
Description: The Linux AMI to use.
Key:
Type: String
Default: tokyo-key
Description: The key used to access the instance.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: "test-sg-web"
GroupDescription: "test-sg-web"
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: '80'
ToPort: '80'
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: '22'
ToPort: '22'
CidrIp: 106.253.56.124/32
- IpProtocol: icmp
FromPort: '-1'
ToPort: '-1'
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: -1
CidrIp: 0.0.0.0/0
EC2Insteance:
Type: AWS::EC2::Instance
Properties:
SubnetId: !Ref Subnet
ImageId: !FindInMap [ RegionMap, !Ref "AWS::Region", !Ref AMI ]
InstanceType:
Ref: InstanceType
KeyName: !Ref Key
SecurityGroupIds:
- Ref: InstanceSecurityGroup
BlockDeviceMappings:
- DeviceName: /dev/xvda
Ebs:
VolumeSize: 8
- DeviceName: /dev/xvdb
Ebs:
VolumeSize: 8
Tags:
- Key: Name
Value: test-ec2
UserData:
Fn::Base64: |
#cloud-boothook
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello World! Tokyo!" > /var/www/html/index.html
Outputs:
PublicIp:
Description: PublicIp Output
Value: {"Fn::GetAtt": ["EC2Insteance","PublicIp"]}
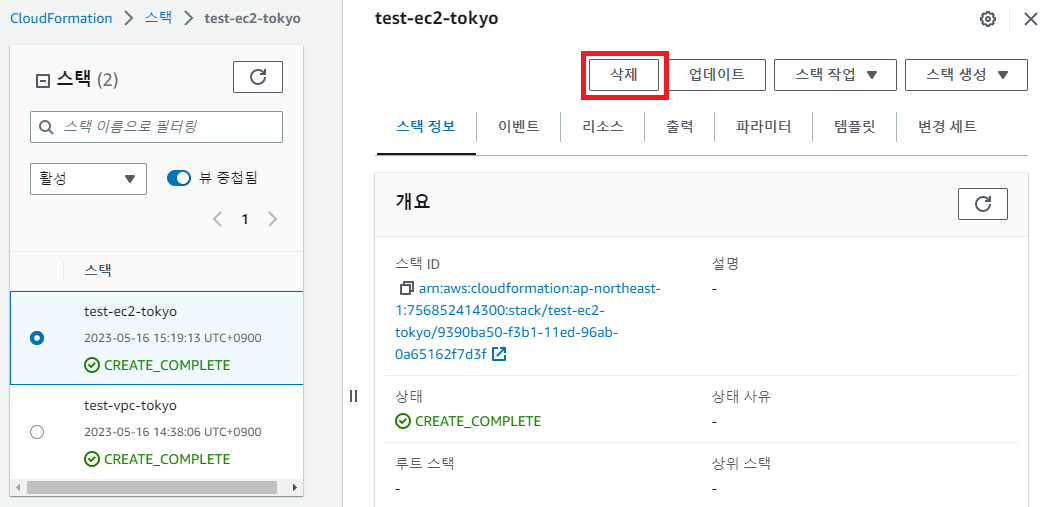
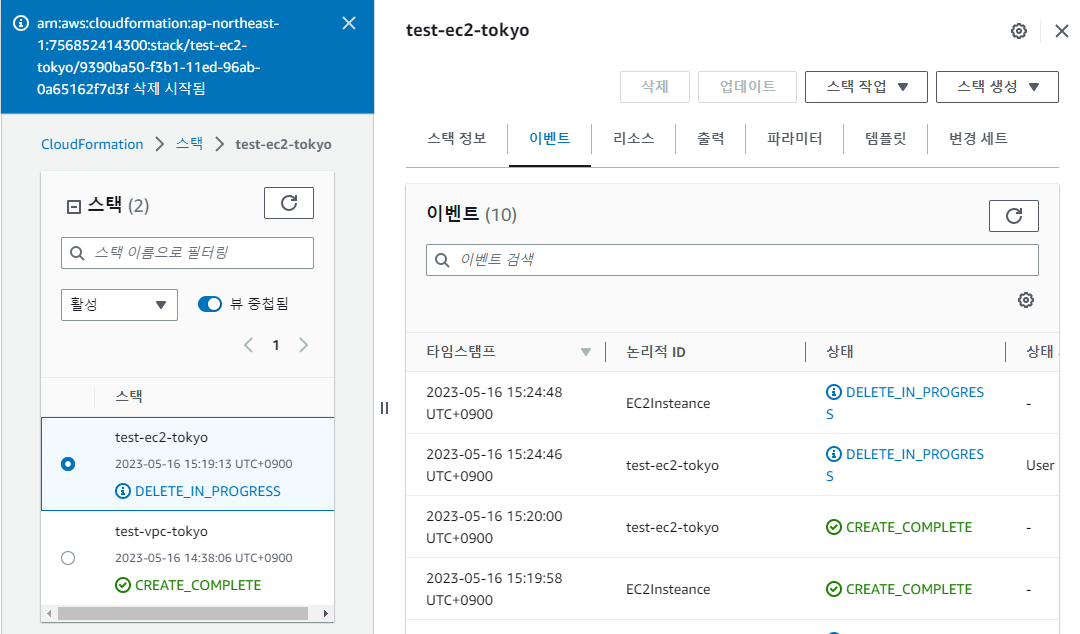
리소스 제거
- 사용된 스택 제거
기타
- CLI 환경에서 내가 있는 곳의 IP 확인
curl ipconfig.io
- 💥 최종 프로젝트에서는
CloudFormation을 이용하지 않음



























