26번
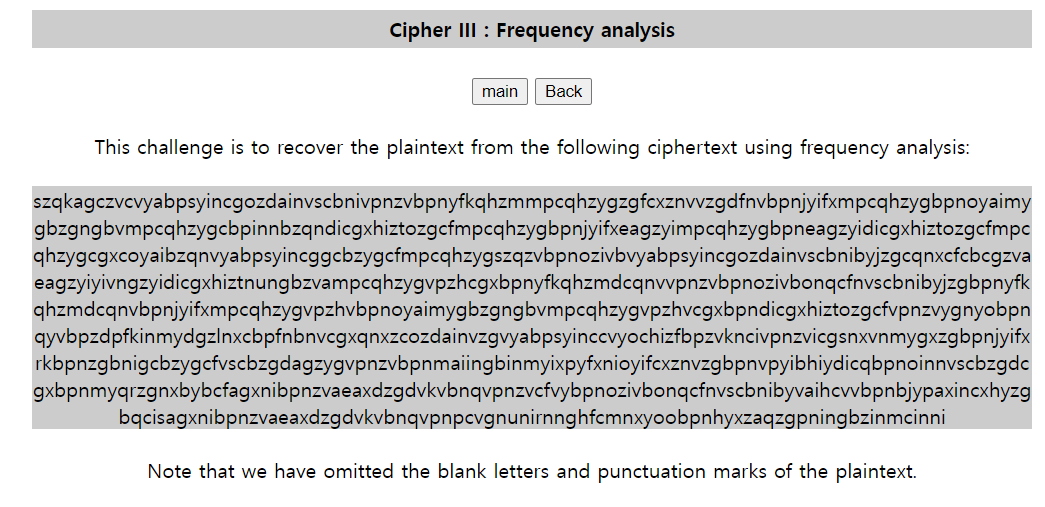
문제에 따라서, 빈도 분석을 해봤다.
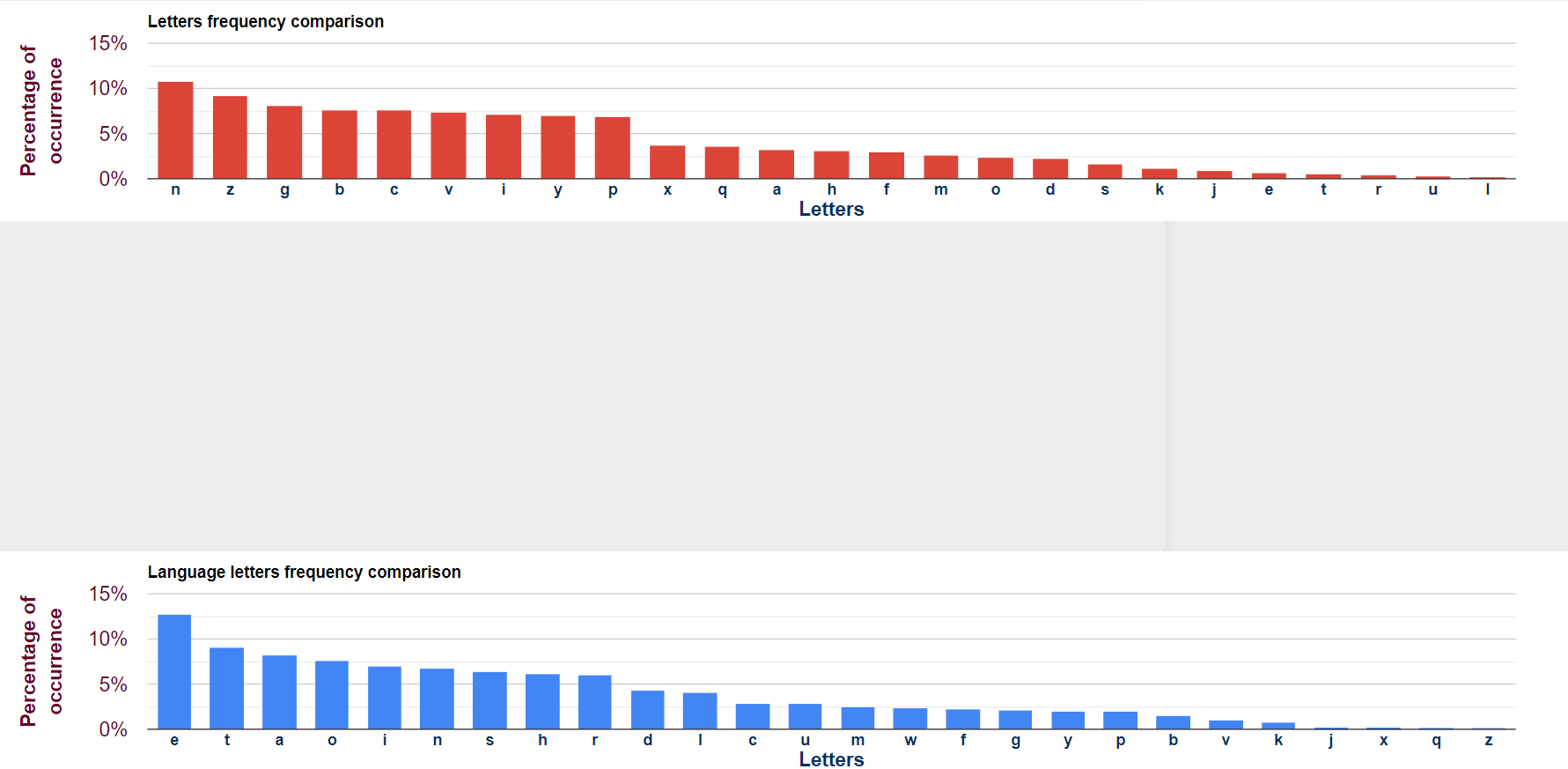
N -> E / Z -> T / G -> A / ... 이런식으로 치환을 해서 평문을 복구하는 거다. 근데 아무래도 반드시 가 적용될 수 없기에 다 확률이다.
- Online Decoder에 들어가서,
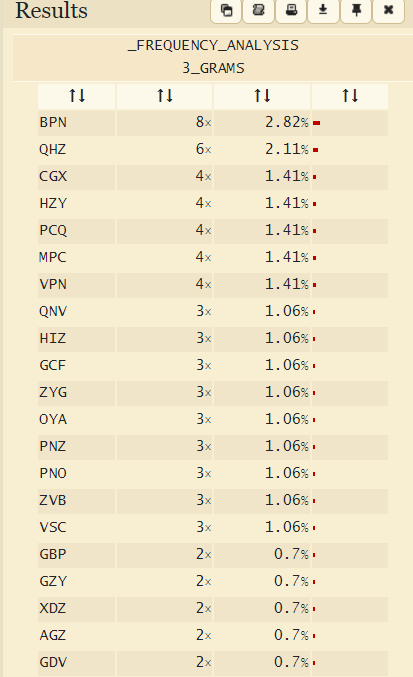
TriGram까지 분석을 해봤다. BPN이 가장 많다. 영어에서 3글자 가장 많은 단어, the를 생각해봤다. 이런식으로 계속 추측하면서 그냥 "떄려 맞추는 거다". brute force같다고 느꼈다. 다만, https://quipqiup.com/ 에서 그냥 자동으로 해준다.
28번
이 문제는 처음보는 유형이었다. 압축 파일을 제시해주는데, "암호를 풀어야 뭘 볼수 있지! 암호가 있기나 한건가!" 라는 문장과 함께 준다. 처음에는 Bruteforce를 생각해서, 파일의 제목들이나, 이것 저것 passwd가 될 법한 것들을 넣어봤다. 그러다가 암호가 있기나 한건가? 에 대해 집중을 해봤고, 결론은 다음과 같다.
Zip 파일 구조에 대해서 이해를 해야한다.
시그니처 : 50 4B 03 04
Local file Header + Data + Data Descriptor가 1개의 덩어리로, 반복되는 구조를 가진다.
Local File Header
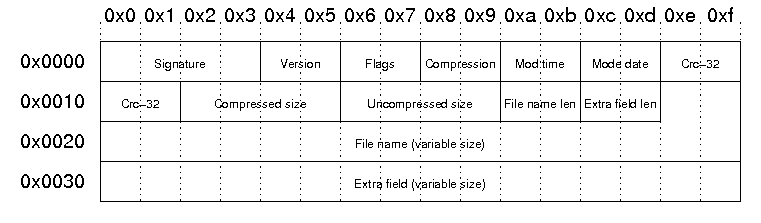
| Offset | Byte | Description |
|---|---|---|
| 0 | 4 | Local file header signature |
| 4 | 2 | Version needed to extract (minimum) |
| 6 | 2 | General purpose bit flag |
| 8 | 2 | Compression |
| 10 | 2 | File last modification time |
| 12 | 2 | File last modification date |
| 14 | 4 | CRC-32 of uncompressed data |
| 18 | 4 | Compressed size (or 0xffffffff for ZIP64) |
| 22 | 4 | Uncompressed size (or 0xffffffff for ZIP64) |
| 26 | 2 | File name length (n) |
| 28 | 2 | Extra field length (m) |
| 30 | n | File name |
| 30+n | m | Extra field |
- Flags General purpose bit flag:
Bit 00: encrypted file
Bit 01: compression option
Bit 02: compression option
Bit 03: data descriptor
Bit 04: enhanced deflation
Bit 05: compressed patched data
Bit 06: strong encryption
Bit 07-10: unused
Bit 11: language encoding
Bit 12: reserved
Bit 13: mask header values
Bit 14-15: reserved
(09 08) => (08 09로 변환, Little Endian) => 0000 1000 0000 1001 (bit 15 < - > bit 0)
- Compression method
00: no compression
01: shrunk
02: reduced with compression factor 1
03: reduced with compression factor 2
04: reduced with compression factor 3
05: reduced with compression factor 4
06: imploded
07: reserved
08: deflated => 이게 보통 압축 방식.
09: enhanced deflated
10: PKWare DCL imploded
11: reserved
12: compressed using BZIP2
13: reserved
14: LZMA
15-17: reserved
18: compressed using IBM TERSE
19: IBM LZ77 z
98: PPMd version I, Rev 1
Data Descriptor
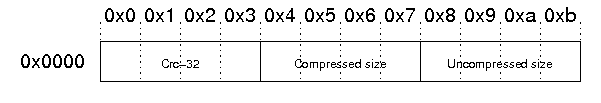
| Offset | Byte | Description |
|---|---|---|
| 0 | 4 | Data Descriptor 시그니처(0x08074b50 고정) |
| 4 | 4 | CRC-32 |
| 8 | 4 | Compressed Size |
| 12 | 4 | Uncompressed Size |
Central Directory File Header
- 이건 Local File Header의 확장으로, 1:1로 연결된다. Disk에서 Local file header까지의 offset을 담고 있어, 이를 통해 해당 Local file set와 연결된다.
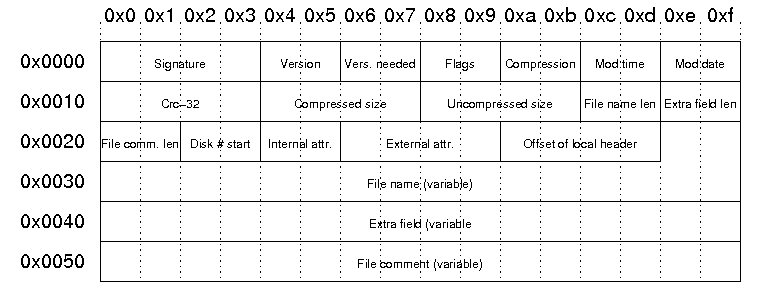
Signature The signature of the file header. This is always '\x50\x4b\x01\x02'.
Version Version made by:
upper byte:
0 - MS-DOS and OS/2 (FAT / VFAT / FAT32 file systems)
1 - Amiga
2 - OpenVMS
3 - UNIX
4 - VM/CMS
5 - Atari ST
6 - OS/2 H.P.F.S.
7 - Macintosh
8 - Z-System
9 - CP/M
10 - Windows NTFS
11 - MVS (OS/390 - Z/OS)
12 - VSE
13 - Acorn Risc
14 - VFAT
15 - alternate MVS
16 - BeOS
17 - Tandem
18 - OS/400
19 - OS/X (Darwin)
20 - 255: unused
lower byte:
zip specification version
Vers. needed
PKZip version needed to extract
Flags General purpose bit flag:
Bit 00: encrypted file
Bit 01: compression option
Bit 02: compression option
Bit 03: data descriptor
Bit 04: enhanced deflation
Bit 05: compressed patched data
Bit 06: strong encryption
Bit 07-10: unused
Bit 11: language encoding
Bit 12: reserved
Bit 13: mask header values
Bit 14-15: reserved
Compression method 00: no compression
01: shrunk
02: reduced with compression factor 1
03: reduced with compression factor 2
04: reduced with compression factor 3
05: reduced with compression factor 4
06: imploded
07: reserved
08: deflated
09: enhanced deflated
10: PKWare DCL imploded
11: reserved
12: compressed using BZIP2
13: reserved
14: LZMA
15-17: reserved
18: compressed using IBM TERSE
19: IBM LZ77 z
98: PPMd version I, Rev 1
File modification time stored in standard MS-DOS format:
Bits 00-04: seconds divided by 2
Bits 05-10: minute
Bits 11-15: hour
File modification date stored in standard MS-DOS format:
Bits 00-04: day
Bits 05-08: month
Bits 09-15: years from 1980
Crc-32 checksum value computed over file data by CRC-32 algorithm with 'magic number' 0xdebb20e3 (little endian)
Compressed size if archive is in ZIP64 format, this filed is 0xffffffff and the length is stored in the extra field
Uncompressed size if archive is in ZIP64 format, this filed is 0xffffffff and the length is stored in the extra field
File name length the length of the file name field below
Extra field length the length of the extra field below
File comm. len the length of the file comment
Disk # start the number of the disk on which this file exists
Internal attr.
Internal file attributes:
Bit 0: apparent ASCII/text file
Bit 1: reserved
Bit 2: control field records precede logical records
Bits 3-16: unused
External attr. External file attributes:
host-system dependent
Offset of local header Relative offset of local header. This is the offset of where to find the corresponding local file header from the start of the first disk.
File name the name of the file including an optional relative path. All slashes in the path should be forward slashes '/'.
Extra field Used to store additional information. The field consistes of a sequence of header and data pairs, where the header has a 2 byte identifier and a 2 byte data size field.
File comment An optional comment for the file.
End of Central Directory Record
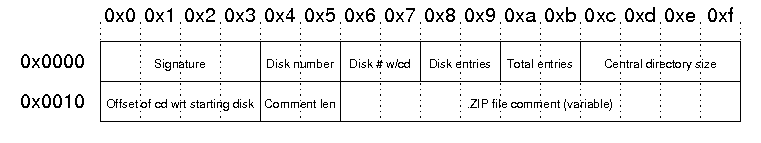
Signature : The signature of end of central directory record. This is always '\x50\x4b\x05\x06'.
Disk Number : The number of this disk (containing the end of central directory record)
Disk # w/cd : Number of the disk on which the central directory starts
Disk entries : The number of central directory entries on this disk
Total entries : Total number of entries in the central directory.
Central directory size : Size of the central directory in bytes
Offset of cd wrt to starting disk : Offset of the start of the central directory on the disk on which the central directory starts
Comment len : The length of the following comment field
ZIP file comment : Optional comment for the Zip file
구조를 알았다. 그럼, 압축에 비밀 번호가 있을 때와 없을 때의 헤더를 비교해보자.
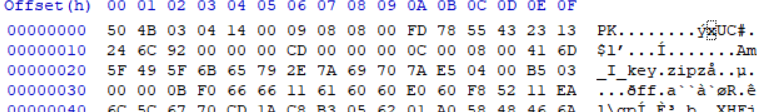
- 비밀번호 있는 경우
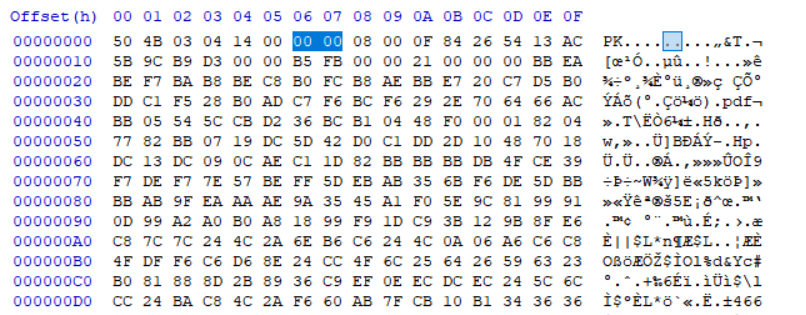
- 비밀번호 없는 경우
그럼 없는 경우와 동일하게 0x 09 08을 변경해준다면, 파일이 열리고 Key를 알 수 있다.
출처
https://en.wikipedia.org/wiki/ZIP_(file_format)
https://users.cs.jmu.edu/buchhofp/forensics/formats/pkzip.html
