⬇️ Main Note
https://docs.google.com/document/d/1xdJ0VVUDoXyaPY7ESq9DKnIpd8KiC2qjgZYxuffCaUU/edit
🐋 Google cloud SQL
4 vCPU, 265GB, 100GB => Recommended default settings
High Availability : 고가용성
➤ Two computers are operating. If one caught error, turn on the other computer so that the server doesn't stop
🔹 Create Instance
Instance ID: my-database02
Password: root
Database version: MySQL 8.0
영역 가용성: 단일 영역 (실제 production에서는 여러 영역으로 하기)
→ 여러 영역이은 다른 두 지역으로 설정해야함 (한 지역에 지진나면 다른 지역컴퓨터를 돌려야함)
Machine method: Standard 1 vCPU or 1 shared core
→ (하나의 컴퓨터로 메모리를 조금씩 여러명이 나눠 갖는 것)
저장용량 : 20GB
저장용량 자동 증가 사용 설정 (나중에 줄일 수 없음) 디스크를 늘린다는건 하나씩 더 연결시킨다는거임
→ (작은것들을 늘려나가는 형식)🐋 Serverless Architecture
- Serverless architecture is constructed with Cloud Function.
- Frontend server is running without backend server, and API is operated with Cloud Function.
➤ Relatively APIs that aren't really important are no need to open up a new server. So request is sent to Cloud Function and the source code inside the cloud function is being executed.
➤ Backend can access to database, but the cloud function can also access to the database
🔹 microservice
Let's suppose that our service became a microservice.
➤ Every single APIs are set to single services, and what kind of error occurs, the other APIs work normally and what we only have to do is fix that problometic API function and re-deploy.
Advantage
When user accesses to the server and requests an API, the computer turns on and inside that computer, the function is executed.
➤ Conservation of money (GCP 비용 절약)
➤ The computer isn't on 24/7, but it's only on when the user requests for an API. After the API is used, computer is automatically shut down.
Disadvantage
There exists a delay time for the computer to turn on and execute the function.
➤ So when the user requests for the first time after the computer is off, it takes a long time for that person.
Cold start : The computer starts with off state.
For 4 to 5 seconds, the computer is live after it starts operating.
When the user sends during that time, that's warm start to that person.
➤ Cold Start to Wram Start
: Request once a 4 sec
- Disadvantage: There's no big difference of cost as operating the computer for 24/7.
- Advantage: Can have precisely distributed microservice
🐋 Database Connection
-------- New database should be made --------
Database access address: IP Address(from SQL)
1. SQL → database → create database → name: myserver02
2. SQL Connection 들어가서 0.0.0.0/0 network 추가하기
3. Go to DBeaver
새로 MySQL 연결해서 server주소를 입력해주는데 이때 주소는
SQL Overview → connection test → IP Address
→ If private IP Address, 외부에 접속 불가능 (내부만 접속 가능)
→ If Public IP Address, 외부에 접속 가능
// docker.compose.prod.yaml --> prod doesn't need my-database docker anymore.
// ➤ app.module --> host and database should be changed🔹 Public IP vs. Private IP
If the IP is set as public, it has high possibility of being hacked.
➤ So the database should be in private mode.
SQL Connection → Private IP , Network: default(VPC)
VPC : Virtual Private Cloud (내부 아이피 사용)
➤ VPC 안에 여러 컴퓨터들이 있는데 그 컴퓨터들이 사용하는 IP는 내부IP임
➤ 이 컴퓨터들은 각각의 방화벽을 가지고 있음
근데 내부에서 내부로 접속하는건 일반적으로 풀어져있음 (그래서 모두가 쉽게 통신 가능)
외부에서 들어오는 접속은 막고 있는거임 (안전을 위해)
그래서 더이상 외부에서 이 내부 아이피로 접속을 할 수 없게 됨
기본적으로 만들어지는 VPC : default VPC (이 같은 default VPC를 설정이 되어있는 컴퓨터에 한에서는 서로서로 방화벽 없이 접근이 가능함) 이때 사용되는 IP가 내부 아이피
밖에서 들어올때 쓰는 IP가 외부 아이피 (공개IP)
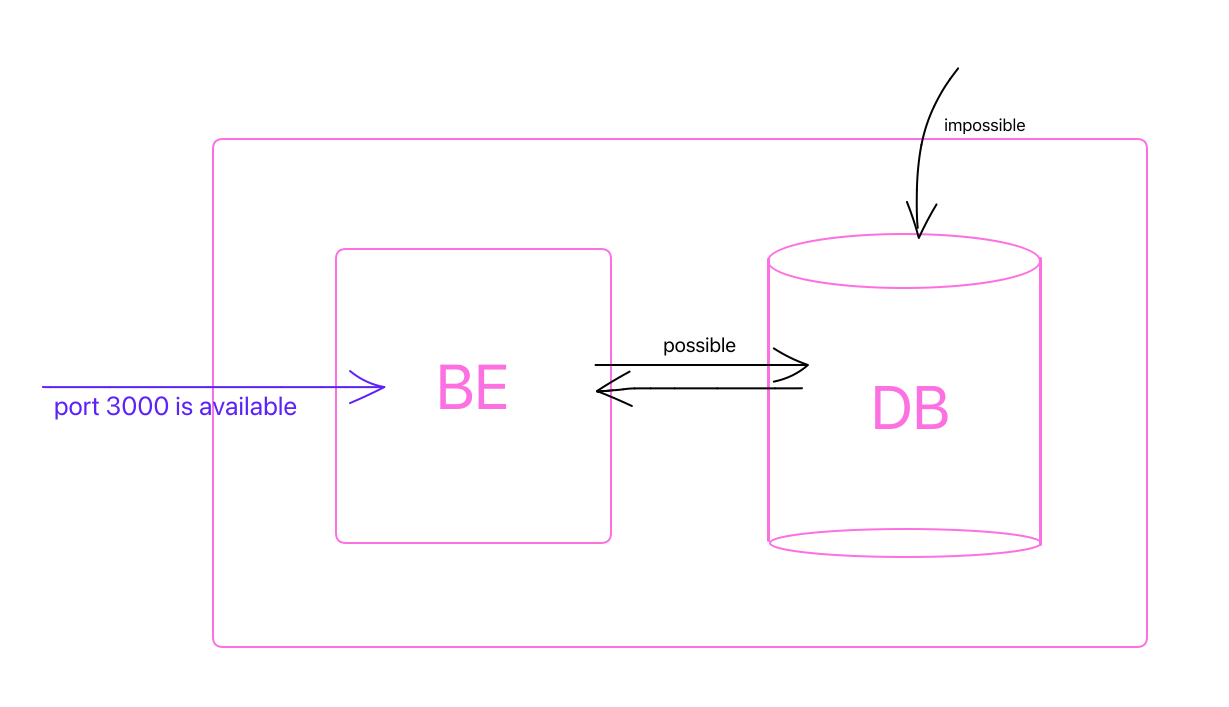
그래서 이젠 VPC안에 있는 컴퓨터밖에 DB에 접속을 못함 (같은 VPC 속 백엔드가 접속 할 수 있다는것)
근데 이젠 우리가 DBeaver로 접속을 못함 (VPC해서 등록한 같은 백엔드 컴퓨터는 DB에 접속 가능)
Compute Engine - VM Instance 들어가서 Network 보면 default VPC로 되어있음
(default라는 이름의 VPC임)
그래서 정리를 하자면 우리 backend는 default VPC, 그리고 SQL로 만든 database는 다른 VPC에 속해 있음
서로 VPC가 다르면 내부아이피로 연결이 안됨! 그래서 두개를 하나로 합쳐야함
➤ VPC-peering
Default VPC안으로 이 database가 들어오게 됨
그래서 backend와 database가 연결됨 (이건 자동으로 클릭 한방에 진행되는 과정임)
➤ so now on, able to connect with inner IP. (그리고 다른 포트는 막혀있고 3000번 포트만 접속 가능)
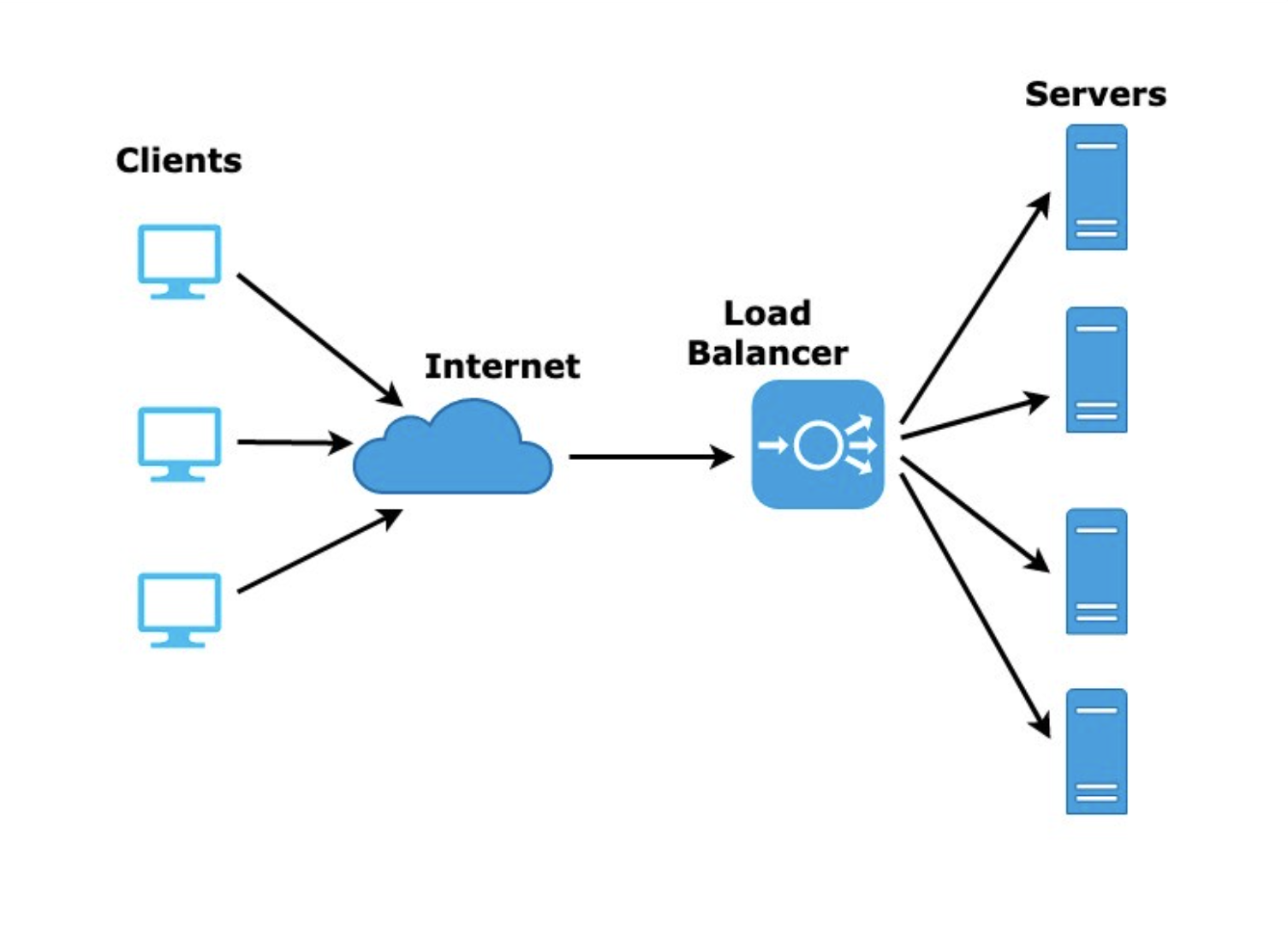
🐋 Load Balancer
https: secured server
To secure the server, there should be an authentication about the server.
And that authentication is set inside load balancer.
Main purpose of load balancer is literally load balancing the request that is sent to itself. (요청 분배)
➤ There exists diverse kinds of algorithms for load balancing: round-robin, least connection, etc...
Round-Robin : 1 goes to A, 2 goes to B, 3 goes to C, 4 goes to A, 5 goes to B, 6 goes to C, 7 goes to A...
Least Connection : Users are sent to the least-traffic server.
According to load balancer,
➤ Frontend : Incoming request
➤ Backend : outgoing respond
reverse-proxy = load balancer receiving the request instead
Http, https can be manipulated in the middle of the process
So instance group should be created on the base of instance template.
🐋 Health Checker
Health checker is attached to load balancer.
➤ Health checker literally checks the status of computers inside the instance group. So if there is an unhealth computer or a dead computer, the health checker tells the load balancer not to load balance to that computer.
How health checking works
When the health checker sends requests to the computers, those computers who responded are normal.
If the request is sent multiple times but there aren't any responses, then that computer is considered dead.
