Digital Signatures
Digital signatures are cryptographic mechanisms used to verify the authenticity and integrity of digital messages or documents. One popular digital signature scheme is the Schnorr signature scheme. Below is an overview of how it works:
Schnorr Signature Scheme
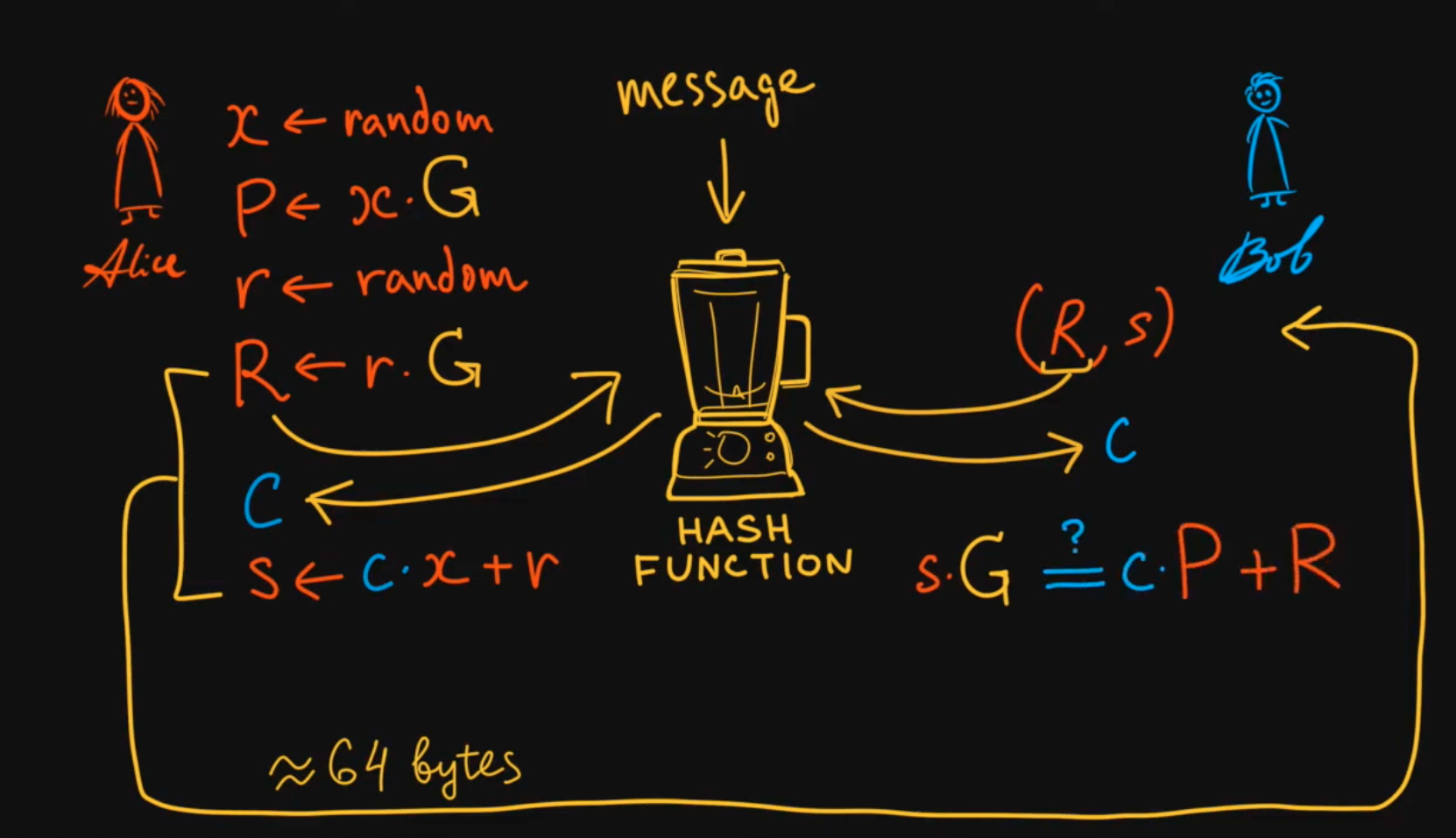
1. Key Generation:
- Generate Private Key : Select a random private key from the range , where is a large prime number.
- Compute Public Key : Calculate the public key , where is a generator of a cyclic group of order in a finite field .
2. Signing:
To sign a message :
-
Generate a Random Nonce : Select a random integer from the range .
-
Compute the Commitment: Calculate .
-
Compute the Hash: Calculate , where is a cryptographic hash function and denotes concatenation.
-
Compute the Response: Calculate .
The signature on the message is the pair .
3. Verification:
To verify a signature on a message :
-
Compute the Hash: Calculate .
-
Compute the Expected Commitment: Calculate .
-
Verify the Commitment: Check if . If they are equal, the signature is valid.
Security Properties
-
Unforgeability: The security of Schnorr signatures relies on the hardness of the discrete logarithm problem. Given and , it is computationally infeasible to find .
-
Non-repudiation: Only the holder of the private key can generate a valid signature for a given message .
-
Integrity: If a signature on a message verifies correctly, it ensures that the message has not been altered.
Benefits
-
Efficiency: Schnorr signatures are computationally efficient for both signature generation and verification.
-
Compactness: Schnorr signatures are relatively short, making them suitable for systems with bandwidth or storage constraints.
Applications
-
Cryptocurrencies: Schnorr signatures are used in some cryptocurrency protocols to improve efficiency and security.
-
Authentication: They are employed in various authentication protocols, including secure communications and access control.
Conclusion
Schnorr signatures provide a robust and efficient method for ensuring the authenticity and integrity of digital data, making them a valuable tool in modern cryptography.
