Cryptographic Commitments
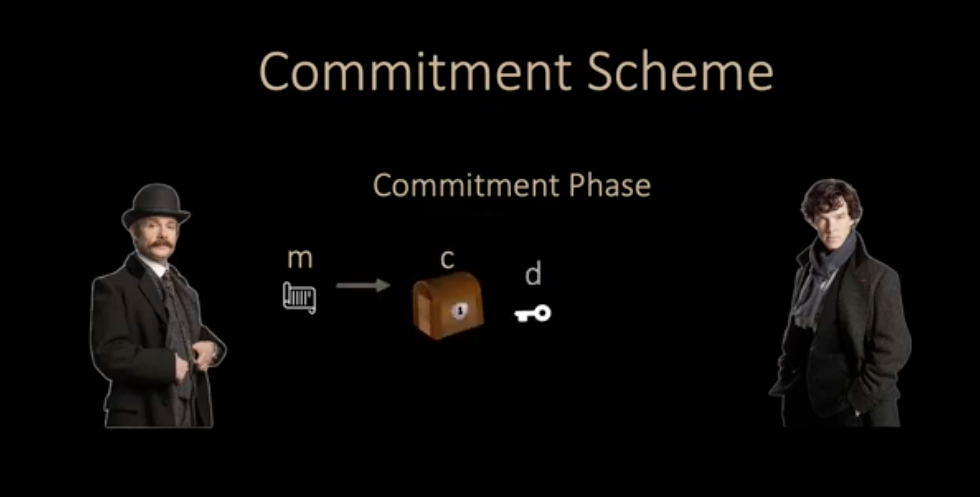
Cryptographic commitments are fundamental cryptographic primitives used to commit to a value while keeping it hidden, with the ability to reveal the committed value later. This concept is akin to putting a value in a locked box, giving the box to someone, and later providing the key to reveal the value inside. Commitments are widely used in protocols such as secure multiparty computation, zero-knowledge proofs, and blockchain technologies.
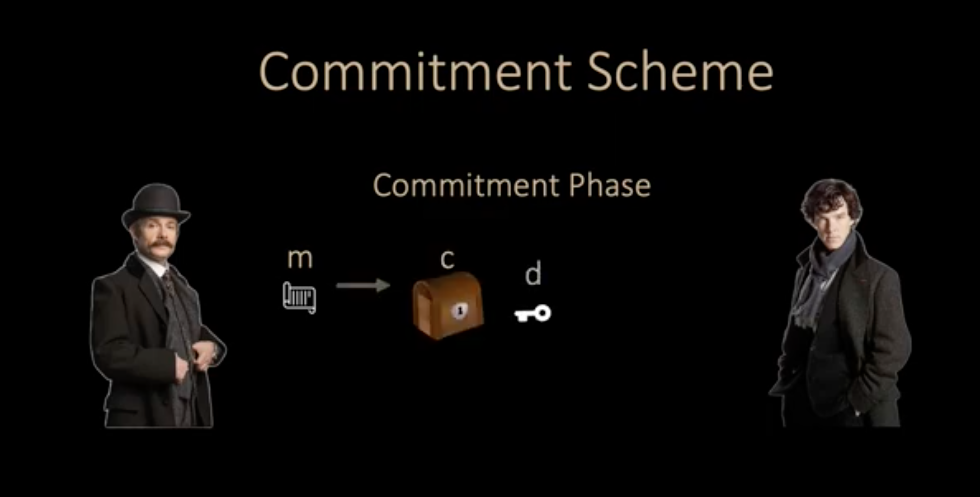
Commitment Scheme link with hand math eq
Properties of Cryptographic Commitments
Cryptographic commitments have two primary properties:
- Hiding: The commitment should not reveal any information about the committed value until it is opened.
- Binding: Once a value is committed, it cannot be changed. The committer cannot open the commitment to a different value than the one they initially committed to.
Types of Cryptographic Commitments
There are different ways to achieve cryptographic commitments, including:
- Hash-based commitments: Use cryptographic hash functions.
- Number-theoretic commitments: Use properties of number theory, such as those based on the discrete logarithm problem.
- Lattice-based commitments: Use lattice problems, relevant in post-quantum cryptography.
Example: Hash-based Commitments
Commit Phase:
- Choose a secret value .
- Choose a random nonce (also known as a blinding factor).
- Compute the commitment , where is a cryptographic hash function and denotes concatenation.
Reveal Phase:
- Reveal both and .
- Verify the commitment by checking if equals .
Example: Pedersen Commitment (Number-theoretic)
Pedersen commitments leverage the hardness of the discrete logarithm problem.
Setup:
- Choose a large prime and a generator of a cyclic group of order .
- Choose another generator such that the discrete logarithm of with respect to is unknown.
Commit Phase:
- Choose a secret value and a random nonce .
- Compute the commitment .
Reveal Phase:
- Reveal and .
- Verify the commitment by checking if equals the provided .
Applications of Cryptographic Commitments
- Zero-Knowledge Proofs: Commitments are used to enable a prover to convince a verifier that they know a value without revealing the value itself.
- Secure Multiparty Computation (SMPC): Commitments allow parties to commit to their inputs while keeping them hidden until all parties are ready to proceed.
- Blockchain and Cryptocurrencies: Commitments are used in protocols like confidential transactions, ensuring transaction amounts are hidden while preserving the integrity and correctness of the blockchain.
- Voting Systems: Commitments ensure that votes are cast in a concealed manner and can be revealed and verified later.
Security Considerations
- Hiding property: Ensures that the commitment does not leak any information about the committed value. It relies on the properties of the hash function (for hash-based commitments) or the difficulty of the discrete logarithm problem (for Pedersen commitments).
- Binding property: Ensures that once committed, the value cannot be changed. It relies on the collision resistance of the hash function or the binding nature of the number-theoretic construction.
Conclusion
Cryptographic commitments are essential tools in modern cryptography, providing a foundation for numerous secure protocols and applications. By ensuring both the hiding and binding properties, commitments enable secure, verifiable, and private interactions in various cryptographic systems.
Details
Once is published, the committer cannot change without changing . Given , it is infeasible to find a pair such that:
This binding property relies on the discrete logarithm problem's hardness.
Homomorphic Property
Pedersen commitments are homomorphic, meaning commitments can be combined in a meaningful way. Specifically, given commitments to two values and
- Commit to with nonce
- Commit to with nonce
The product of these commitments is a commitment to the sum with nonce
This property is particularly useful in cryptographic protocols where combining commitments needs to be efficient and secure.
Security Proofs
Hiding Proof: To prove the hiding property, consider an adversary who sees the commitment . Since is chosen uniformly at random from , the distribution of is uniformly random over for different values. Therefore, the adversary cannot distinguish between different values of .
Binding Proof: To prove the binding property, assume that an adversary can find two pairs such that:
Then:
Since and are generators and their discrete logarithm relationship is unknown, finding such a pair implies solving the discrete logarithm problem, which is assumed to be computationally infeasible.