BLS (Boneh-Lynn-Shacham) signatures are a type of digital signature scheme that utilizes pairings on elliptic curves to provide efficient and secure authentication. Developed by Dan Boneh, Ben Lynn, and Hovav Shacham in 2001, BLS signatures have gained popularity due to their efficient verification process, compactness, and support for signature aggregation.
Key Points:
-
Multisig Challenges: Traditional multisignature schemes require several communication rounds, which can be cumbersome, especially with cold storage setups. BLS signatures simplify this by enabling a more straightforward aggregation process.
-
Random Number Generation: In BLS signatures, the reliance on random number generators can be a concern since deterministic signing methods (like in ECDSA) are not applicable.
-
Complexity in m-of-n Multisig: Implementing an m-of-n multisignature scheme with BLS requires creating a Merkle tree of public keys, which can become unwieldy as and increase.
-
Signature Aggregation: While BLS allows for the aggregation of signatures, not all signatures within a block can be combined into a single signature, which can be a limitation in some contexts.
BLS Signature Scheme Overview:
-
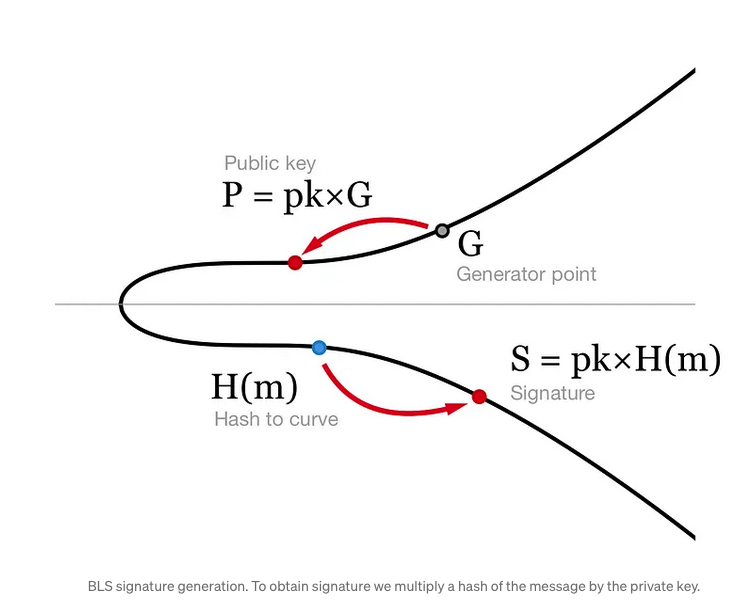
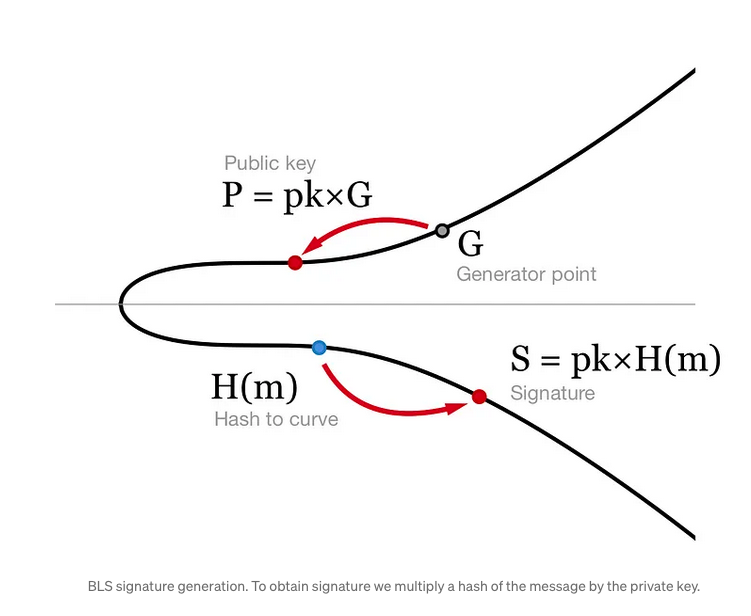
Key Generation:
- A user generates a private key and computes the corresponding public key by multiplying with a generator point on the elliptic curve.
-
Signing:
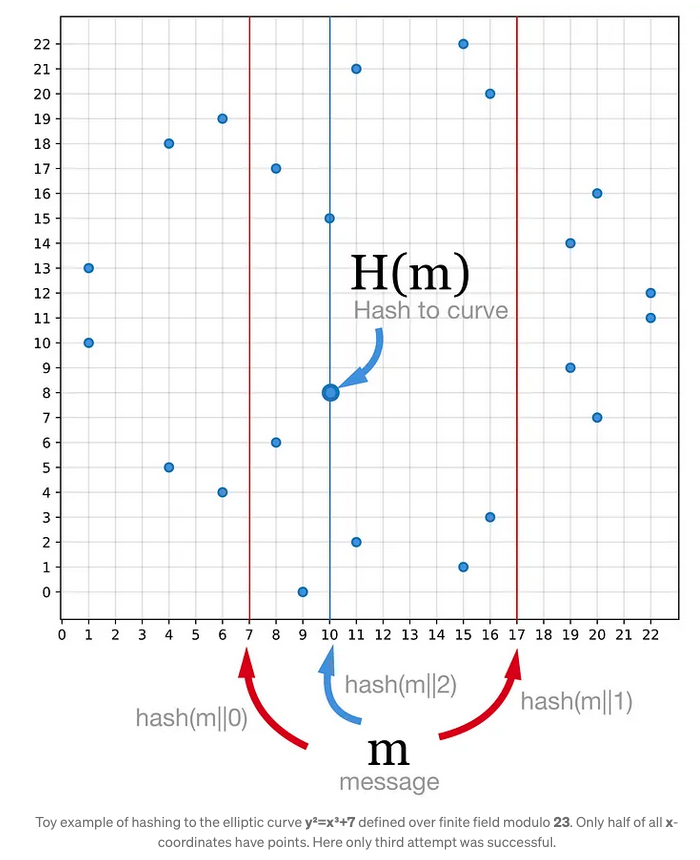
- To sign a message , the user hashes to a point on the elliptic curve using a cryptographic hash function .
- The signature is computed as .
-
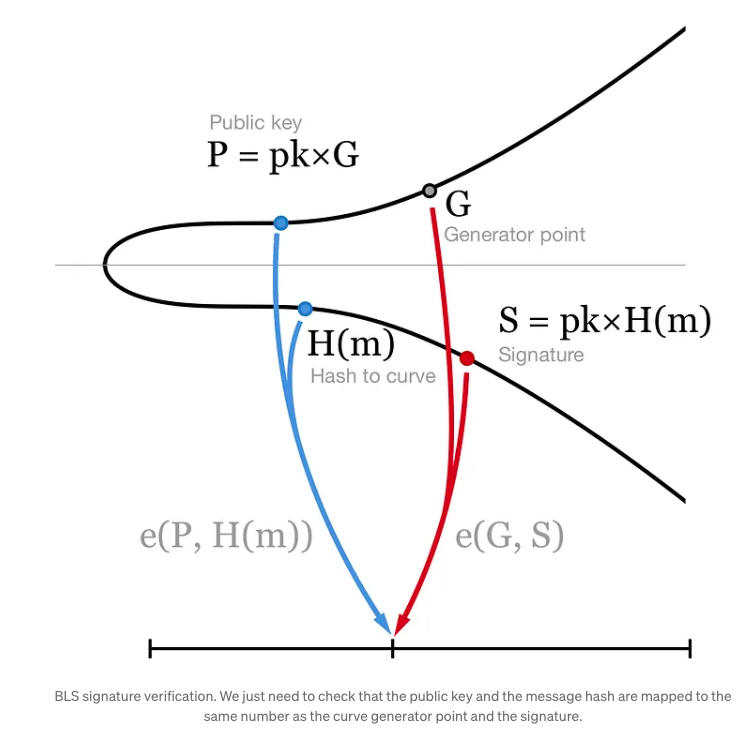
Verification:
- The verifier checks the validity of the signature by verifying the pairing equation:
- Here, is a bilinear pairing function, and is the generator point on the elliptic curve.
- The verifier checks the validity of the signature by verifying the pairing equation:
Advantages of BLS Signatures:
-
Fast Verification: The verification process in BLS is faster than in many other signature schemes, such as ECDSA, due to the efficient use of bilinear pairings.
-
Compactness: BLS signatures are compact, requiring minimal storage, making them ideal for resource-constrained environments.
-
Multisignature Support: BLS signatures enable efficient multisignature schemes, where multiple signatures can be aggregated into a single, compact signature.
Limitations:
-
Message Uniqueness: BLS signatures do not inherently enforce message uniqueness. If two different messages hash to the same point on the curve (a rare event), the same signature could be used for both.
-
Quantum Vulnerability: While BLS signatures are secure against classical attacks, they may be vulnerable to quantum attacks due to the reliance on bilinear pairings.
Applications:
-
Cryptocurrencies: BLS signatures are used in various cryptocurrencies, such as Ethereum 2.0 and Algorand, for secure transaction validation and key management.
-
Blockchain Consensus: In blockchain consensus protocols like PBFT and HotStuff, BLS signatures play a critical role in ensuring the correctness and efficiency of block propagation.
Introduction to BLS12-381
BLS12-381 is a popular elliptic curve used in modern cryptographic protocols, especially those requiring pairing-based operations. It is particularly favored for applications like zk-SNARKs, BLS signatures, and decentralized systems, including Ethereum 2.0.
Key Properties of BLS12-381:
-
Elliptic Curve Equation:
- BLS12-381 is defined by the equation over a prime field .
-
Prime Field :
- The prime field is defined by a large prime number , specifically , chosen for both security and efficiency.
-
Embedding Degree:
- The curve has an embedding degree of 12, which is crucial for efficient pairing operations used in cryptographic applications.
-
Twist Curve:
- BLS12-381 includes a twist curve, which aids in efficient pairing calculations by mapping the curve over an extension field.
-
Security Level:
- The curve offers 128-bit security, sufficient for most modern cryptographic applications.
BLS Signatures with BLS12-381
BLS12-381 is often used in implementing BLS signatures, which are valued for their efficiency and unique aggregation properties.
BLS Signature Scheme Overview:
-
Key Generation:
- Generate a private key and compute the public key , where is a generator on the curve.
-
Signing:
- Hash the message to a curve point .
- Compute the signature .
https://medium.com/cryptoadvance/bls-signatures-better-than-schnorr-5a7fe30ea716
-
Verification:
- Verify the signature by checking .
Signature Aggregation
BLS signatures can be aggregated, allowing multiple signatures to be combined into one. For example, if multiple users sign different messages:
The aggregate signature is:
This can be verified against an aggregated public key:
Background of this:
BLS12-381 for Rest of us
Pairings in BLS12-381
Pairing operations are central to the BLS signature verification process. In BLS12-381, a pairing function is computed between points on different groups, which enables efficient and secure signature verification.
Example with Concrete Values:
- Private Key: .
- Public Key: .
- Message: .
- Hash: (a specific point on the curve).
- Signature: .
- Verification: Check .
Summary
BLS12-381 is a robust elliptic curve used extensively in cryptographic applications, particularly for BLS signatures. The curve's design balances security, efficiency, and compatibility with pairing-based operations, making it suitable for secure communications and decentralized systems.
This version should be well-suited for your Velog blog with LaTeX support.