HTTP(Hypertext Transfer Protocols) are used on top of Transmission Control Protocol(TCP) to transfer webpages and other content from websites.
here are other Protocols commonly used on the internet.
Dynamic Host Configuration Protocol (DHCP)
When your computer connects to a networkd, DHCP is used to assign your computer an IP address.
Your computer communicates over User Datagram Protocol(UDP) using the protocol with a type of server called a DHCP server. The server keeps track of computers on the network and their IP address. It will assign your computer an IP address and respond over the protocol to let it know which IP address to use.
Once your computer has an IP address, it can communicate with other computers on the network.
Domain Name System (DNS)
Your computer checks with the DNS server associated with the domain name and then returns the correct IP address.
Internet Message Access Protocol (IMAP)
IMAP makes your device download emails and manage your mailbox on the server storing your emails.
Simple Mail Transfer Protocol (SMTP)
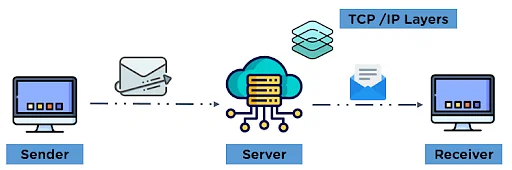
Now that your emails are on your device, you need a way to send emails. SMTP is used. It allows email clients to submit emails for sending via an SMTP server. You can also use it to receive emails from an email client, but IMAP is more commonly used.
Post Office Protocol (POP)
POP is an older protocol used to download emails to an email client.
POP will delete the emails on the server once they have been downloaded to your local device. (this is the difference between POP and IMAP)
Although no longer commonly used in email clients, developers often use it to implement email automation as it is a more straightforward protocol than IMAP.
File Transfer Protocol (FTP)
to transfer the files from your local computer to the server.
FTP allows you to list, send, receive and delete files on a server. Your server must run an FTP server and you will need an FTP Client on your local machine.
Secure Shell Protocol (SSH)
Using an SSH client allows you to connect to an SSH server running on a server to perform commands on the remote computer.
All data sent over SSH is encrypted. so third parties cannot understand the data transmitted. Only the sending and receiving computers can understand the data.
SSH File Transfer Protocol (SFTP)
The data is transmitted insecurely when using the File Transfer Protocol. So third parties may understand the data that you are sending. To solve this, the SSH File Transfer Protocol (is also called the Secure File Transfer Protocol) can be used to transfer files over the SSH protocol. This ensures that the data is transmitted securely.
