S3 object
- key, value, version ID, metaData 형태
- 파일단위
- 0바이트~5테라바이트
S3 Bucket
- 폴더나 디렉토리 공유
- 이름 unique 해야함
S3
- Standard : 99.99 availability, 빠름, 최소 3개 AZs
- Intelligent Tiering : Cost-effective access tier,(ML 기반으로 비용 측정)
- Standard Infrequently Accessed(IA) : Still Fast, Cheaper, 한달에 한번 미만 접근, 50% 더 싸다 Standard 보다
- One Zone IA : Still Fast, one AZ 존재 가능, IA보다 20% 더 쌈 - Glacier : 롱텀 cold storage, 굉장히 쌈
- Glacier Deep Archive : 가장 쌈, 12시간만 존재
S3 Encryption
- SSE-AES : S3 handles the key, uses algorithm
- SSE-KMS : manage the keys
- SSE-C : Customer provided key (you manage the keys)
S3 Cross Region Replication(CRR)
- 자동으로 object 복제 다른 region 으로
- higher durability, potential disaster recovery
- versioning 중요
S3 Transfer Acceleration
- over long distances : cloudFront distributed Edge Location
- bucket 업로드하는것 대신에, 다른 url 사용 (edge location)
- data가 edge location에 도착하면, 자동적으로
S3 presigned Urls
- private objects 에 접근하기 위해 링크로 제공 가능
- 링크 생성은 AWS CLI or AWS SDK
S3 MFA Delete
- 다른 유저가 object 삭제 못 하도록 MFA 코드 제공, AWS CLI 에서 MFA 접근 가능
AWS Snowball
- snowball can import and export from s3
- 겁나 싸고 빠름
Snowball Edge
- similar to snowball but with more storage and with local processing
- lcd display
- cluster in groups (5~10 devices)
Snowmobile
- 45-foot long shipping container, pulled by a truck
- gps tracking, alarm, escort security
VPC(virtual Private Cloud)
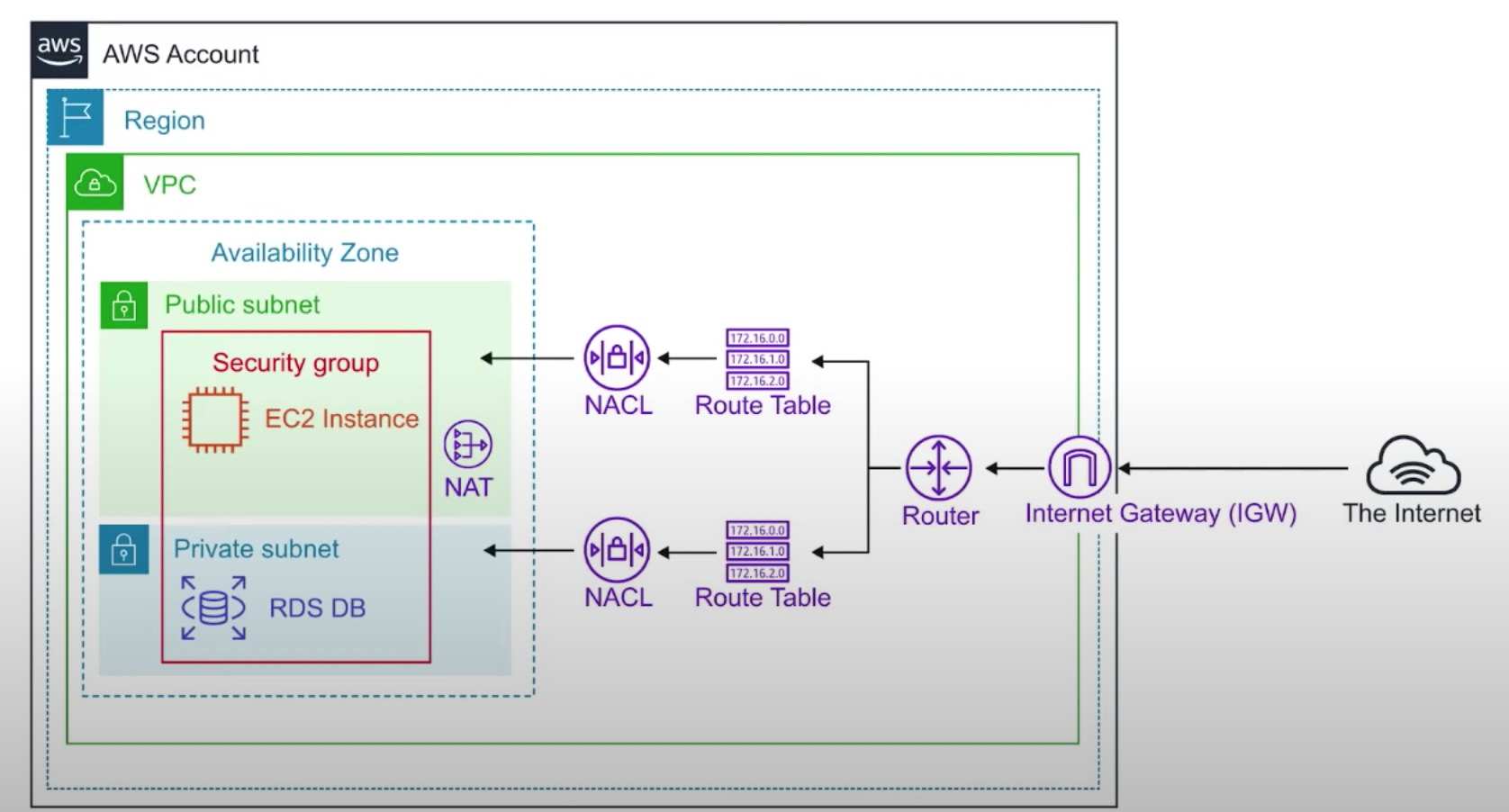
- VPC are Region Specific, don't span regions
- uses IPv4 Cidr Block and IPv6 Cidr blocks
- cost nothing: VPC, Route Tables, NACLs, Internet Gateways, Security Groups and Subnets, VPC Peering
- cost money : NAT Gateway, VPC Endpoints, VPN Gateway
- DNS hostnames
- when you create a VPC, it automatically has a main route table
VPC peering
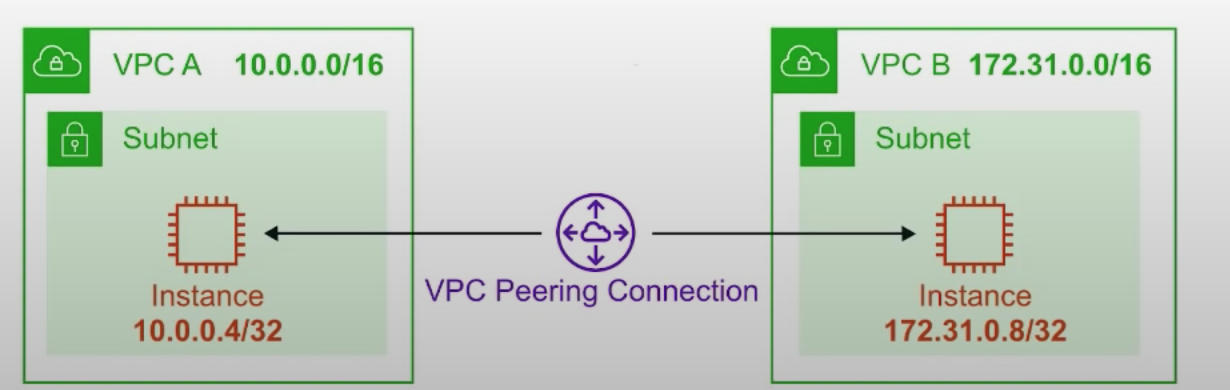
- peered VPCs behave just like they are on the same network
- different AWS accounts and regions available
- 1 Central VPC - 4 other VPCs
- No transitive peering (one to one connection)
- No overlapping CIDR Blocks
Route Tables
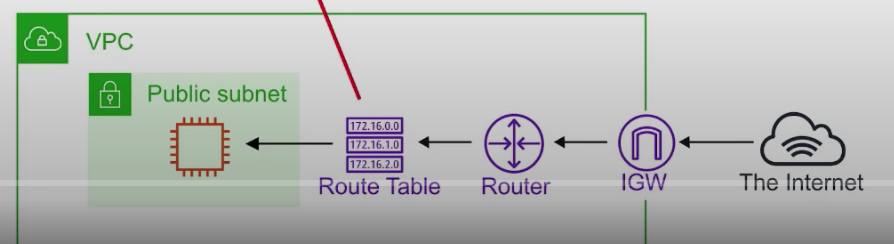
- network traffic is directed
- each subnet in your VPC must be associated with a route table
- A subnet can only be associated with one route table at a time, but you can associate multible subnets with the same route table
Internet Gateway(IGW)
- allows your VPC access to the Internet
- Perform network address translation(NAT) for instances that have been assigned public IPv4 addresses.
- To route out to the internet, you need to add in your route tables you need to add a route to the IGW and set the Destination to be 0.0.0.0/0
Bastion/Jumpbox
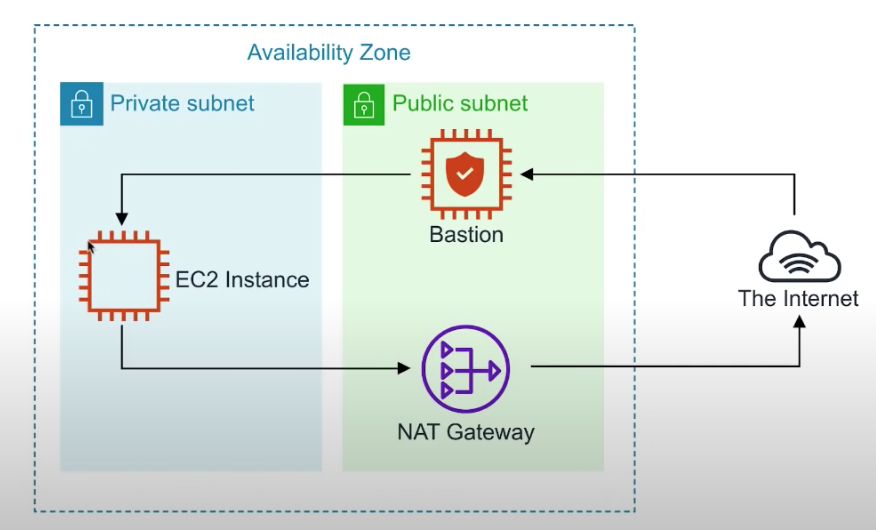
- Bastons are designed to help you gain access to your EC2 Instances via SSH or RCP(That are in a private subnet)
NAT Gateways/Instances
- EC2 instances to gain outbound access to the internet for things such as security updates.
- NATs can't be used as Bastrions
Direct Connect
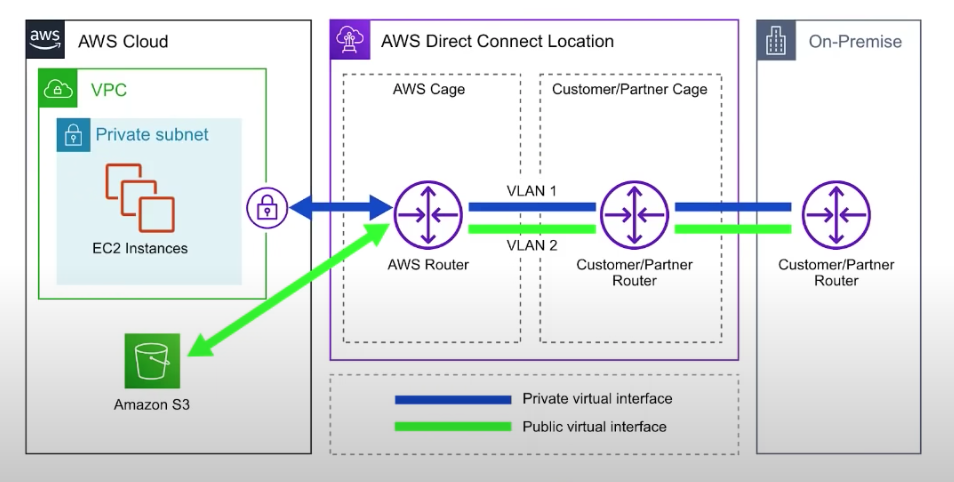
- dedicated network connections from on-premises locations to AWS
- very fast
- helps reduce network costs and increase bandwidth throughput
- provides a more consistent network experience than a typical internet-based connection
VPC Endpoints
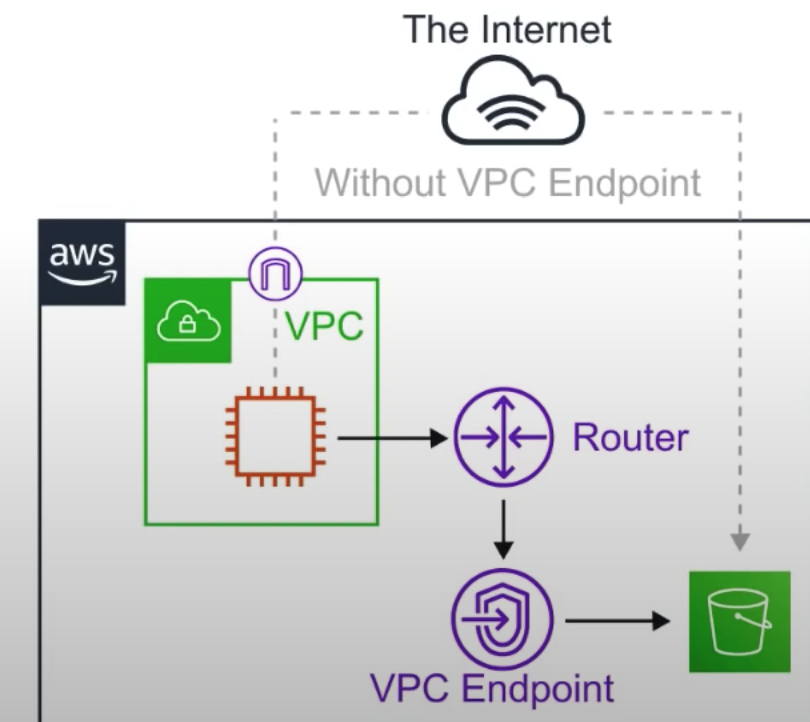
- VPC endpoints allow you to privately connect your VPC to other AWS services, and VPC endpoint services.
- IGW, NAT, VPC Connection, Direct Connect 없어도 외부로 연결 가능
- Instances in the VPC don't require a public IP Address to communicate with service resources
Interface Endpoints
- ENI(Elastic Network Interfaces) with a private IP address
- are powered by AWS PrivateLink (cost money)
VPC gateway Endpoints
- for a specific route in your route table, used for traffic destined for a supported AWS service (free)
- To Create Gateway Endpoint, you must specify the VPC in which you want to create the endpoint, and the service to which you want to establish the connection
- AWS Gateway Endpoint supports 2 services(S3, DynamoDB)
VPC flow logs
- allow you to monitor IP traffic information in-and-out of network interfaces within your VPC
- All log data is stored using Amazon CloudWatch Logs
- can be created for VPC, Subnets, Network Interface
Network Access Control List(NACL)
- in-and-out of subnets firewall (allow or deny)
- SUbnets can only belong to a single NACL
- could block a single IP address (can't do this with SG)
- follows a numbered list of rules in order from lowest to highest
Security Groups
-
inbound and outbound firewall for EC2 instances
-
there are no 'deny' rules(Use NACL). all traffic is blocked by default unless a rule specifically allows it.
-
all inbound traffic is blocked by default
-
multible instances across multible subnets can belong to a Security Group.
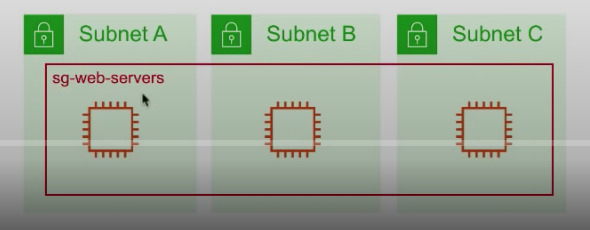
-
An EC2 inatance can belong to multiple Security Groups, and rules are permissive
-
specific IP range
-
if traffic is allowed inbound, it is also allowed outbound
Network Address Translation(NAT)
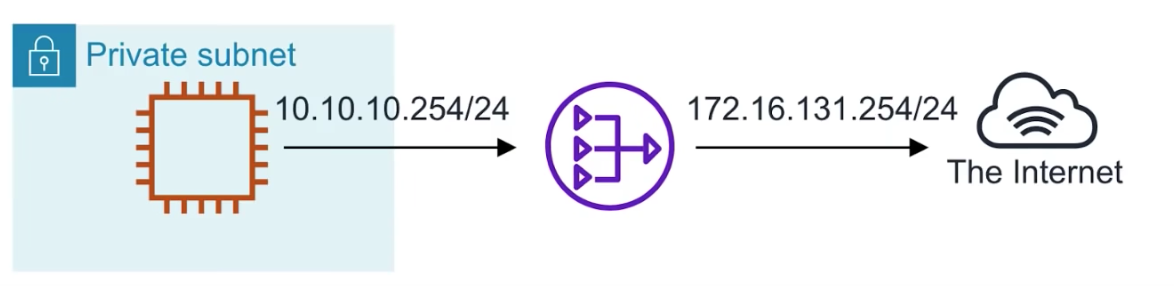
- method of re-mapping one IP address space into another
- private network outbound access to the internet
- if you have conflicting two network addresses, then NAT can make the addresses agreeable
NAT Instances vs NAT Gateways
- NATs have to run within a public subnet
- NAT Instances are individual EC2 instances.(Community AMIs)
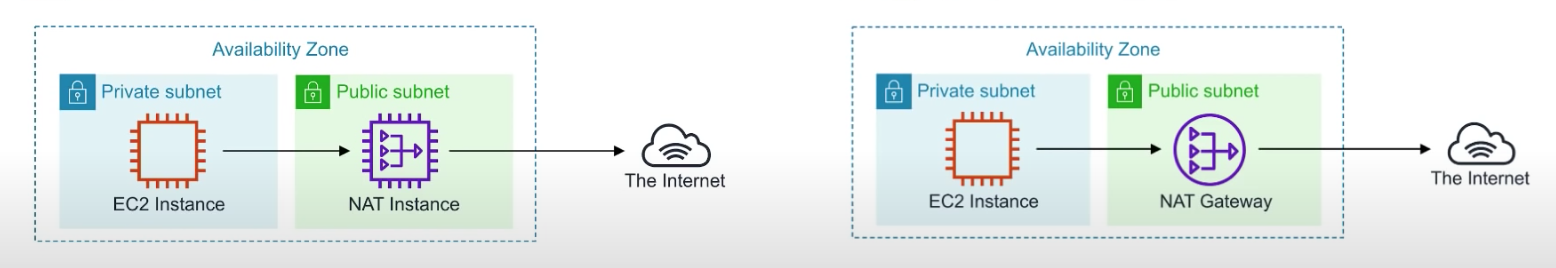
- NAT Gateways : managed, more recent, and launches redundant instances within the selected AZ.
- 1 NAT Gateway inside 1 AZ
- preferred setup for enterprice systems.
- no need to patch, check, and assign a public IP address.(자동으로 됨)
- Route table MUST be updated.
- NAT instance : Mush have route out of the private subnet to the NAT instance.
- The size of NAT instance determines how much traffic can be handled.
- High availability can be achieved using Autoscaling Groups, multiple subnets in different AZs.
