AWS Cloud practitioner lecture
IaaS – Infrastructure as a Service (EC2
PaaS – Platform as a Service (lambda
SaaS – Software as a Service (gmail
six advantages of AWS cloud computing
-Trade capital expense for variable expense
-Benefit from massive economies of scale
-Stop guessing about capacity
-Increase speed and agility
-Stop spending money running and maintaining DCs
-Go global in minutes
Regions, Availability Zone, Edge Location
1.one AZ = one Data Center
2.Region = consitsts of multiple AZ
3.Regions are isolated one from each other,
AZs are isolated one from each other, BUT ...
the AZs in the same Region are connected through low-latency links (2 or more)!
4.Amazon CloudFront uses a global network of 166 Points of Presence (155 Edge Locations and 11 Regional Edge Caches) in 65 cities across 29 countries
5.Edge Locations are AWS endpoints that cache content locally
6.Regional Edge Caches store even more cache locally
AWS Management Interfaces
1.AWS Management Console
-gui, aws사이트 들어가서 하는 거
2.AWS Command Line Interface (CLI)
-unified tool to manage your AWS services
-control multiple AWS services from the command line and automate them through scripts
-After AWS CLI tool installation, you can begin making calls to your AWS services from the command line.
3.AWS Software Development Kits (SDKs)
-SDK, is really nothing more than a set of tools that allow developers to create software or apps for a specific platform, operating system, computer system or device
-can access and manage AWS services with your preferred development language or platform
billing alarm
-프로필 클릭->my billing dashboard->Budgets(왼쪽 바)->create a budget
IAM
-The key in understanding IAM is represented by these two concepts: authentication and authorization
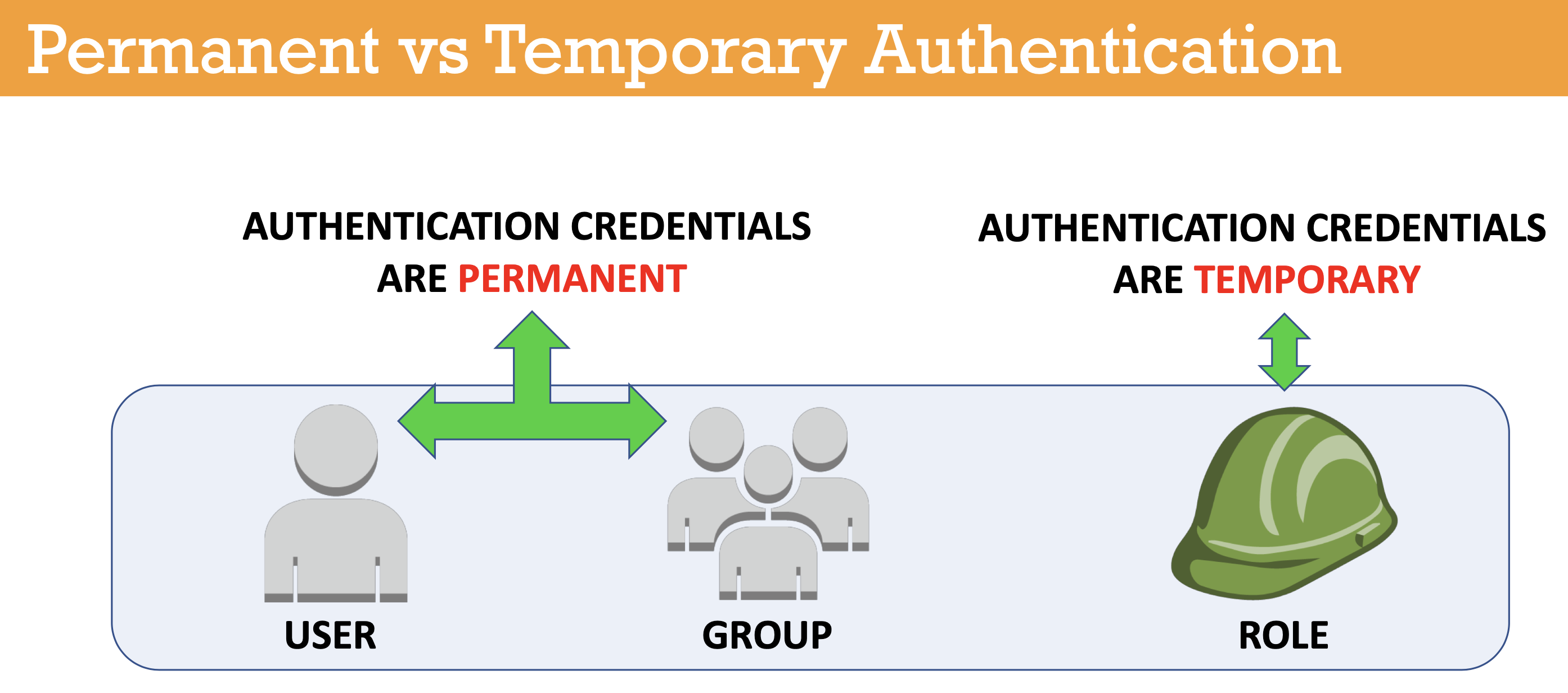
-Once a user/role is authenticated by AWS, it will be given permissions (authorized) based on policy document(s) that are attached to it
-Policy documents (JSON format) can be attached to a user, group or role; if policy is attached to group, once a user joins the group, it will inherit the attached policies
순서
1.A principal (or operator), human or AWS service, makes a request for an action on an AWS resource (API call)
2.First, the user is authenticated, based on username/password pair or access key ID / secret access key (programmatic access – CLI, API, SDK)
3.The user’s action will be permitted (authorized) based on attached policies
4.Every API call will be recorded in AWS by CloudTrail
Access key ID, Secret access key, password
IAM 유저 만들면 위 세개가 생성된다.
-Access key ID, Secret access key는 CLI, SDK로 접근할 때 필요
-Password is for console
IAM user만드는 과정
- IAM 창 들어간다
- MFA 설정
- user생성
- 그룹생성->user를 그룹에 넣어줌
VPC
vpc개념 잘 이해가 안된다ㅜㅜ
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
pricing models for EC2
1.On-Demand Instance
2.Reserved Instance
3.Spot Instance
4.Dedicated Host
do not use root user accont
-Never share your AWS account root user password or access keys with anyone
-Create individual users for anyone who needs access to your AWS account
-Use Groups to Assign Permissions to IAM Users
-Grant least privilege
Policy documents can be attached to a user, group or role. If the policy is attached to group, once a user joins the group, it will inherit the attached policie-Policy documents can be attached to a user, group or role. If the policy is attached to group, once a user joins the group, it will inherit the attached policies.
EC2
yum update -y : ec2접속 후, 소프트웨어 패키지 같은 것들 최신화 하는 명령어
쳐보면 아래처럼 권한문제가 나온다.
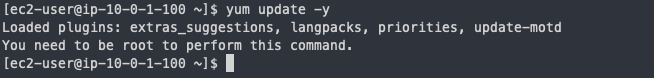
이를 해결하기 위해 sudo su명령어로 루트 권한을 확보한다.
그 후에 다시 yum update -y명령어 입력하면 작동한다.
yum install httpd -y
service httpd status
service httpd start
cd /var/www/html/
이 경로에서 index.html파일 만든다.
Security Groups(SG) Basics
-AWS security gorups act as a virtual firewall to control inbound&outbound traffic
-inbound: 외부에서 ec2로 들어오는 것(예.인터넷)
-outbound: ec2에서 밖으로 나가는 것.(예. 인터넷)
-SG는 instance level에서 적용됨. subnet차원에서 적용되는 것 아니다.
-그러므로 서로 다른 ec2끼리 다른 SG가 적용될 수 있따.
-Inbound, outbound룰을 각각 지정한다.
-when you first create a SG, it has no inbound rules ->no traffic is permitted to EC2
-When defining rules, you can only specify allow rules, and no deny rules
-by default, all outbound traffic is permitted
EBS(Elastic Block Store)
:proviced block level storage volumes for user with EC2 instances
:highly available and reliable storage volumes that can be attached to any running instance that is in the same AZ
:are exposed as storage volumes that persist independently from the life of the instance
-S3와는 다르다. S3는 object저장소다(파일, 이미지, 동영상 등에 적합)
-EBS는 storage for voulme이다. 하드드라이브 같은 것.
-2종류가 있다. 각각 성능, 가격 다름
1. SSD volumes-high IOPS(성능 중요하면 이거 써)
2. HDD volumes-throughput over IOPS(용량 중요하면 이거 써)
S3
-Every object in S3 is contained in a bucket
-Objects are the fundamental entities stored in S3
-Objects consist of object data and metadata;
object data is the actual data, while metadata is just data about data
-When creating an object, you specify the key name, which uniquely identifies the object in the bucket
-Every object in a bucket has exactly one key = name
-cost depends on number and size of objects and plan
-data tranfer in to S3=free
-data transfer out of s3 = charged by region
-s3, IAM does not require region selection
-static website hosting을 원할경우, pulbic으로 바꿔주고, Static website hosting설정을 바꿔줘야 한다.
Bucket policies
provide centralized access control to buckets and objects based on a variety of conditions. whit bucket policies, you can add or deny permissions across all of objects within a bucket
-bucket name should be unique globally
Route 53
Amazon Route 53 is a highly available and scalable DNS web service
-s3와 연동시키기 원할 경우, bucket이름=domain name이어야 한다.
-따라서 domain name만들기 전에, 해당 이름으로 s3버킷 만들 수 있는지 먼저 확인하자!
-port number 53
-With Route53 you can also register new domains within AWS or migrate existing ones to AWS.
CloudFront
: is a web service that speeds up distribution of your static and dynamic web content, to your users
:delivers your content through a worldwide network of data centers called edge locations
*When a user requests content that you're serving with CloudFront, the user is routed to the dege location that provides the lowest latency, so that content is delivered with the best possible performance
Edge Locations are AWS endpoints that cache content locally
Edge location과 Regional Edge Caches는 다른 개념이다.
CloudFront Regional Edge Caches really help when the content is not popular enough to stay at a CloudFront Edge Location and improve delivery performance for that content
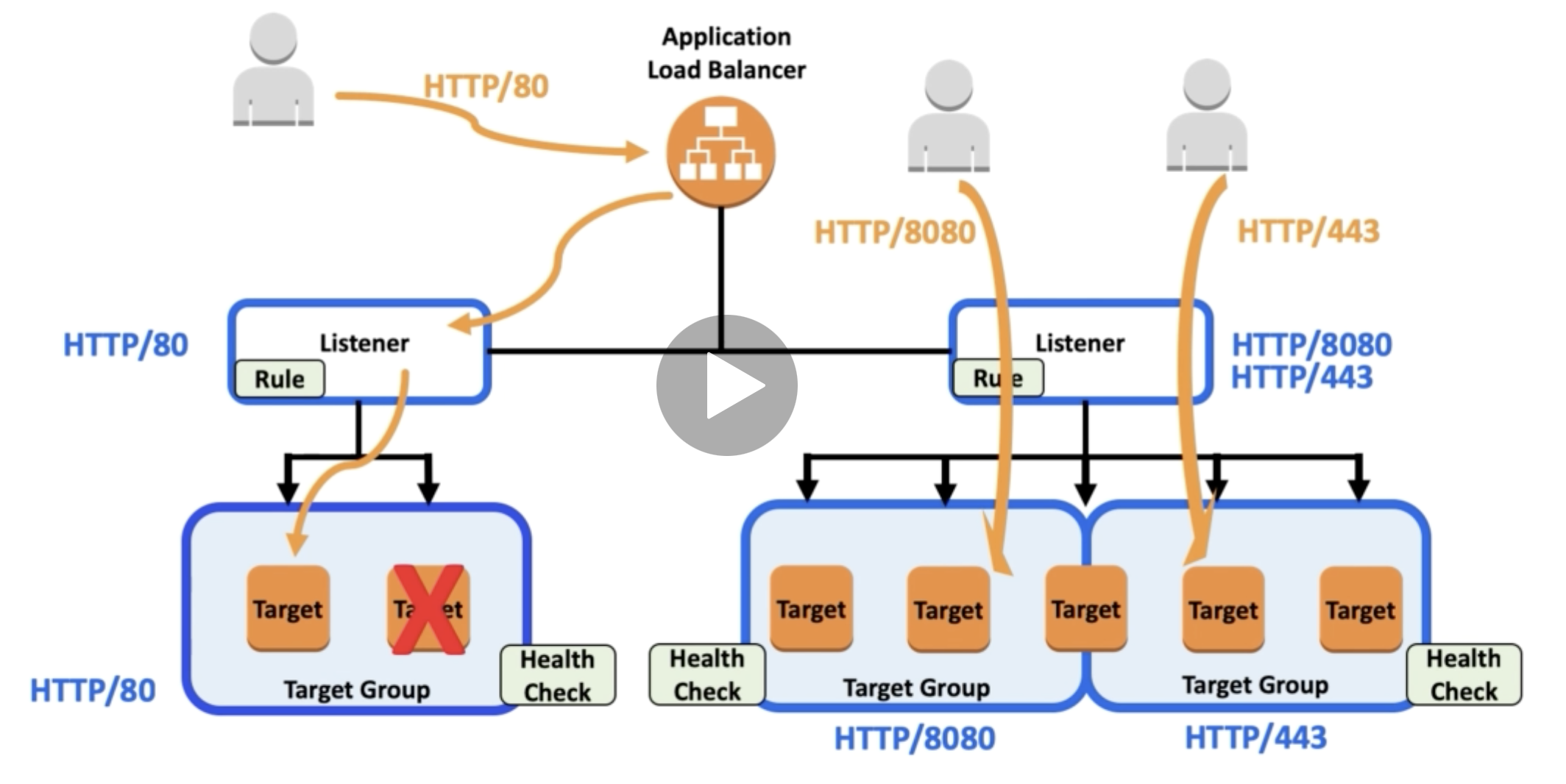
Application Load Balancer
There are three types of LB
1.Network Load Balancer
2.Classic Load Balancer
3. Application Load Balancer
-Application Load Balancers operate at layer 7, but Network Load Balancers operate at layer 4.
-LB is the single point of contact for clients
-serves EC2 instances in multiple AZs, which results in increased availability of your applications
-you will define Rules for traffic forwarding, including Target Groups, condition and priority
-the Target Group(TG) routes requests to one or more registerd targets, such as EC2 instances, using protocol/port number that you configured
Auto Scaling
EC2 instances are grouped in Auto Scaling Groups:
-Min number of EC2 instances
-Desired number of EC2 instances
-Max number of EC2 instances
-A launch configurations is an instance configuration template that an Auto Scaling Group(ASG) users to launch EC2 instances
-What's included in a launch configurations:
1.AMI ID
2.Instance type
3.Key pair
4.Security group
5.Blcok(Volume)
Auto scaling과정
1. 앞으로 사용될 instance를 하나 만들고, AMI화한다.
2. Launch Configuration 설정.(desired)
3. ASG만든다.(min, max)
4. scaling policies설정.
RDS
-RDS security is implemented through security groups;
you can allow access to the DB by specifying IP address rages or EC2 instances
Three types of security groups can be used;
1.DB security group, controls access to a DB instance that is not in a VPC
2.VPC security group controls access to a DB instance inside a VPC
3.EC2 security group controls access of an EC2 instance to the DB
How to interact?
1.Console
2.Command Line Interface(CLI)
3.AWS Software Development Kits(SDKs)
Monitoring
-You can use the free Amazon Cloudwatch service to monitor the performance and health of a DB instance
-Performance chars are shown in teh RDS console
AWS Lambda
Elastic Beanstalk
CloudFormation
Simple Notification Service(SNS)
CloudWatch

기타
sudo su
service install httpd
sevice httpd start
cd /var/www/html
vi index.htmlWAF
web application firewall
-with WAF you can monitor HTTP and HTTPS traffic
-WAF is a web application firewall that monitors connections forwarded to your web application
-WAF 방어목록: cross-site forgery, cross-site-scripting(XSS), file inclusion, SQL injection
-WAF provides several options that you can configure:
1.Allow all traffic except specific requests
2.Block all traffic except requests that you permit
3.Monitor and count requests with properties defined
AWS Shield
:hples you protect against DDoS attacks
AWS Firewall Manager
AWS Inspector
:tests your EC2 instances from the network accessibility perspective and the security state of your applications that run on these instances
:With AWS Inspector you can install a small software package, called an agent, in the operating system of the EC2 instances that you want to assess
-the agent monitors the behavior of the EC2 instances, including network, file system and process activity
ECR
Amazon Elastic Container Registry (ECR) is a fully-mngd Docker container registry that makes it easy for developers to store, manage and deploy Docker container images
Amazon ECR hosts your images in a highly available and scalable architecture, allowing you to reliably deploy containers for your applications
ECS
Amazon Elastic Container Service (ECS) is a highly scalable, high-performance container orchestration service that supports Docker containers and allows you to easily run and scale containerized applications on AWS
ECS is the AWS service that helps running and scaling applications in Docker containers
Amazon ElastiCache
:upports tow open-source in-memory caching engines: Redis, Memcached
