AWS Solutions Architect lectures
Region, AZ
Region은 국가개념이라 보면 맞을 듯하다.
한 Region안에 여러 AZ가 있다. 각각의 AZ는 물리적으로 독립적이지만, 네트워크적으로는 매우 붙어있다.
특정 Region에서는 특정 service가 불가능한 경우가 있으니, Region정할 때 AWS에서 제공하는 Region정보를 확인하자.
IAM
:Identity and Access Management
1.Users(Usually a physical person)
2.Groups(Functions(admins, devops), Teams(engineering, design..)) =>Contains users
3.Roles(Internal usage within AWS resources)
이것들을 명시하는 policies는 JSON형태다.
It's best to give users the minimal amount of permissions they need to perform thier job(least privilege principles)
IAM 중요사항
• One IAM User per PHYSICAL PERSON
• One IAM Role per Application
• IAM credentials should NEVER BE SHARED
• Never, ever, ever, ever, write IAM credentials in code. EVER.
• And even less, NEVER EVER EVER COMMIT YOUR IAM credentials
• Never use the ROOT account except for initial setup.
• Never use ROOT IAM Credentials
SSH
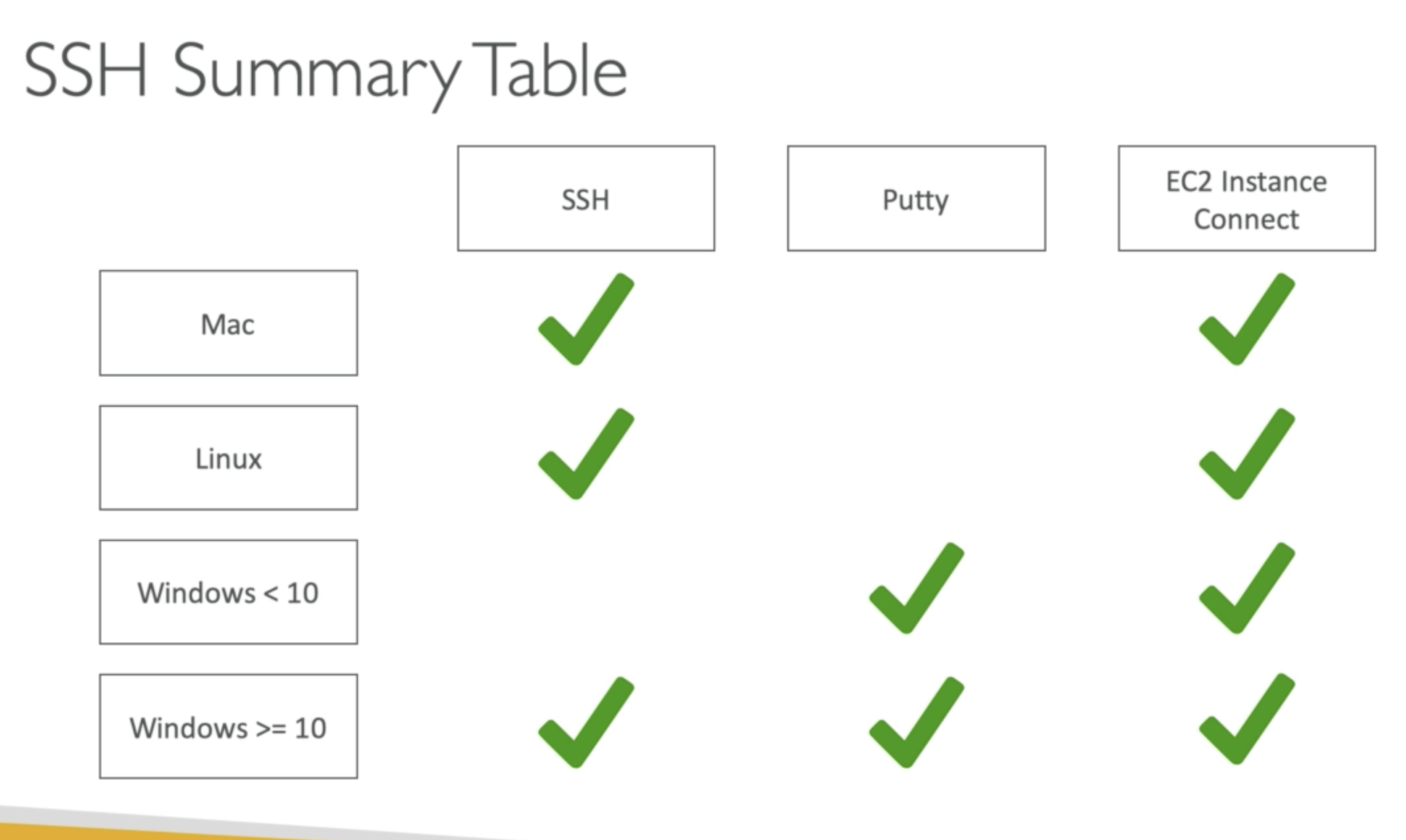
-SSH is one of the most important function. It allows you to control a remote machine, all using the comand line.
ssh접근 시 겪는 문제 1. password pem파일 명령어에 포함 안하는 경우.
ssh ec2-user@ip주소로 접근하면, permission denied뜬다. 비밀번호 없기 떄문
해결책: ssh -i example.pem ec2-user@id주소
ssh접근 시 겪는 문제 1. .pem파일 권한설정
비밀번호 파일은 쓰기가 되어선 안되므로, 읽기전용 파일로 바꿔주자. 안그러면 접근 불허가 뜬다.
chod 0400 example.pem
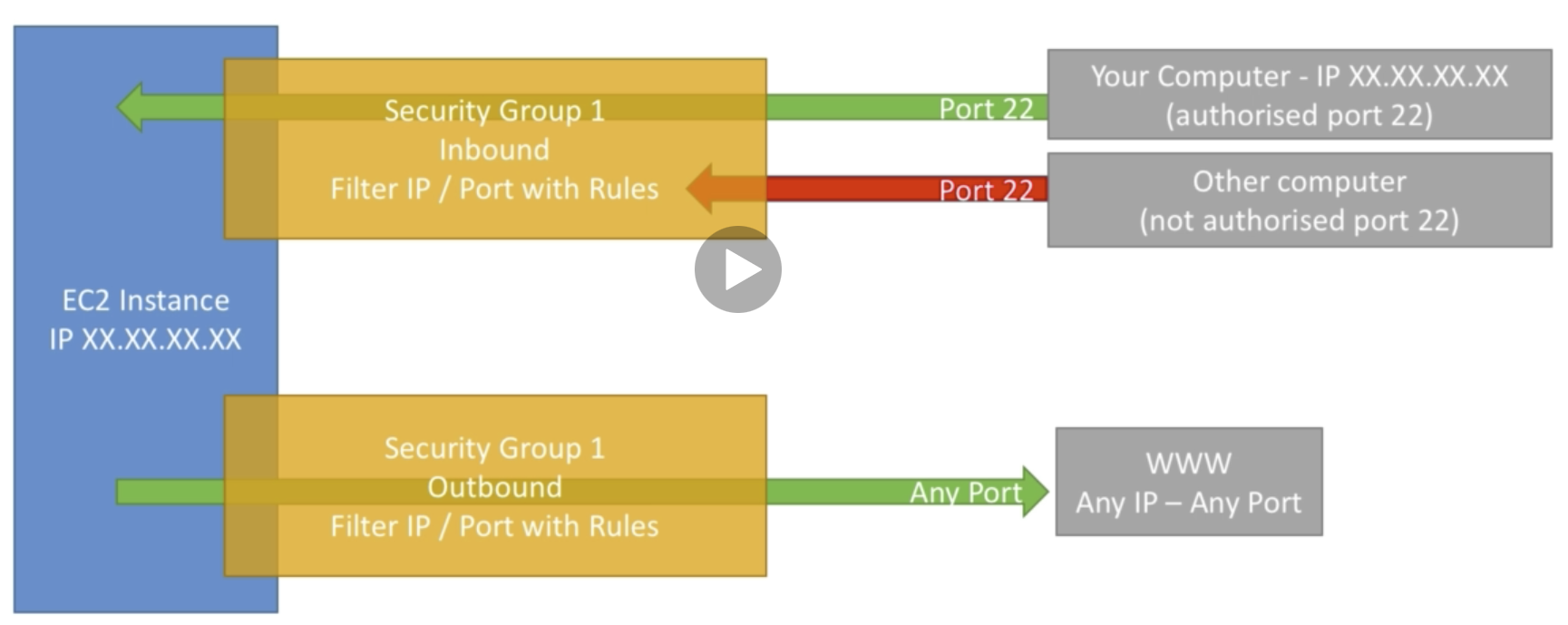
Security Groups
-inbound, outbound
-"firewall" of EC2 instances
They regulates
• Access to Ports
• Authorised IP ranges – IPv4 and IPv6
• Control of inbound network (from other to the instance)
• Control of outbound network (from the instance to other)
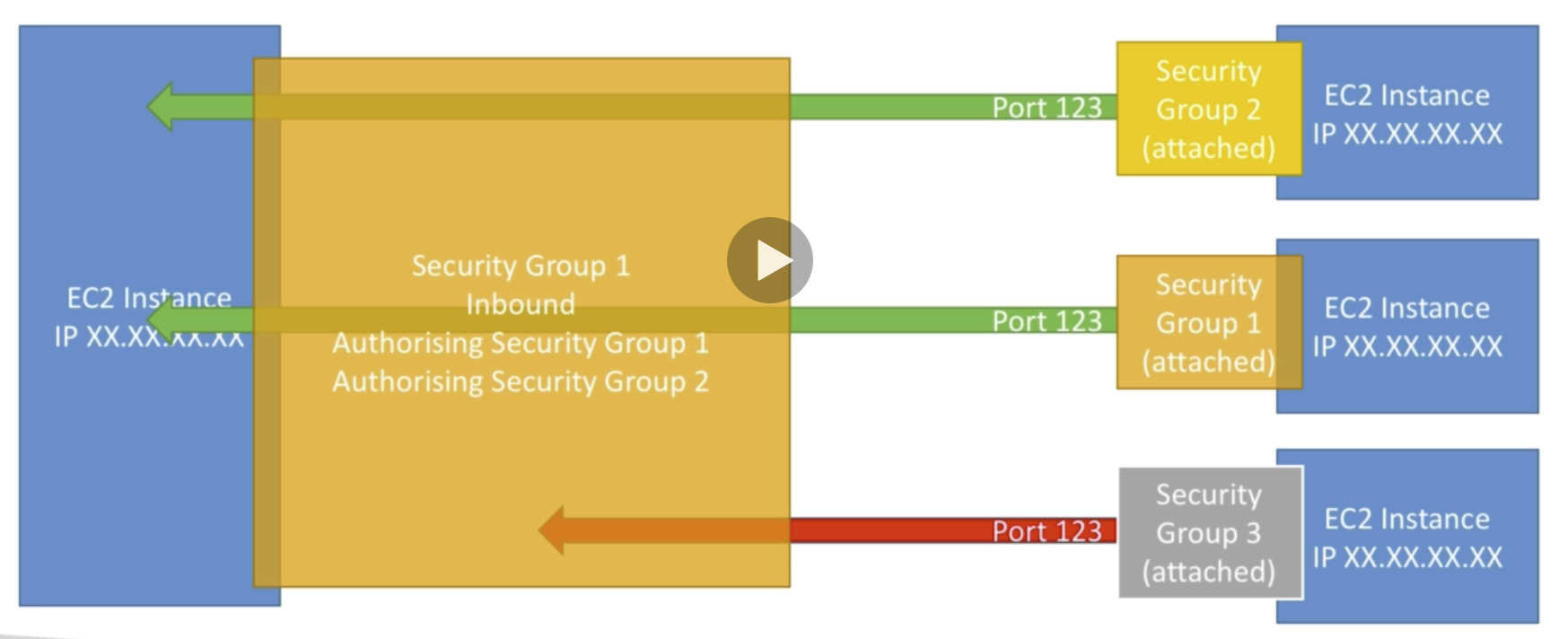
import knowledge about SG
•Can be attached to multiple instances
• Locked down to a region / VPC combination
• Does live “outside” the EC2 – if traffic is blocked the EC2 instance won’t see it
• It’s good to maintain one separate security group for SSH access
• If your application is not accessible (time out), then it’s a security group issue
• If your application gives a “connection refused“ error, then it’s an application error or it’s not launched
• All inbound traffic is blocked by default
• All outbound traffic is authorised by default
IP: private vs public vs elastic
IPv4: [0-255].[0-255].[0-255].[0-255].
Public IP:
• Public IP means the machine can be identified on the internet (WWW)
• Must be unique across the whole web (not two machines can have the same public IP). • Can be geo-located easily
Private IP:
• Private IP means the machine can only be identified on a private network only
• The IP must be unique across the private network
• BUT two different private networks (two companies) can have the same IPs.
• Machines connect to WWW using a NAT + internet gateway (a proxy)
• Only a specified range of IPs can be used as private IP
elastic Ip
If you need to have a fixed public IP for your instance, you need an Elastic IP
try to avoid using Elastic IP:
• They often reflect poor architectural decisions
• Instead, use a random public IP and register a DNS name to it
• Or, as we’ll see later, use a Load Balancer and don’t use a public IP
강의정리
private ip는 고정되있다.인스턴스를 stop했다가 run으로 바꿔도 안바뀜.
private ip는 같은 네트워크를 공유해야 한다 ->우리는 aws내부네트워크를 공유하지 않기에->private ip로는 접근 불가능하다.
echo "Hello World" from $(hostname -f)" > /var/www/html/index.html
EC2 User Data
It is possible to bootstrap our instances using an EC2 User data script. • bootstrapping means launching commands when a machine starts
• That script is only run once at the instance first start
• EC2 user data is used to automate boot tasks such as: • Installing updates
• Installing software
• Downloading common files from the internet
• Anything you can think of
• The EC2 User Data Script runs with the root user
-it automatically runs with the sudo command
-instance실행할 때 자동실행할 명령어.
S3
-버킷은 region level, S3는 global level
-Buckets are defined at the region level
-Naming convention
• No uppercase
• No underscore
• 3-63 characters long
• Not an IP
• Must start with lowercase letter or number
Objects (files) have a Key
• The key is the FULL path:
• s3://my-bucket/my_file.txt
• s3://my-bucket/my_folder1/another_folder/my_file.txt
• The key is composed of prefix + object name
• s3://my-bucket/my_folder1/another_folder/my_file.txt
• There’s no concept of “directories” within buckets (although the UI will trick you to think otherwise)
• Just keys with very long names that contain slashes (“/”)
SSL/TSL
-SSL refers to Secure Sockets Layer, userd to encrypt connections
-TLS refers to Transport Layer Security, which is a newer version
-Nowadays, TLS certificates are mainly used, but people still refer as SSL
ASG
-it's possible to scale an ASG based on CloudWatch alarms
-An Alarm moitors a metric(such as Average CPU)
- send custom metric from application on EC2 to CloudWatch(PutMetric API)
- Create CloudWatch alarm to react to low / high values
- User the CloudWatch alarm as the scaling policy for ASG
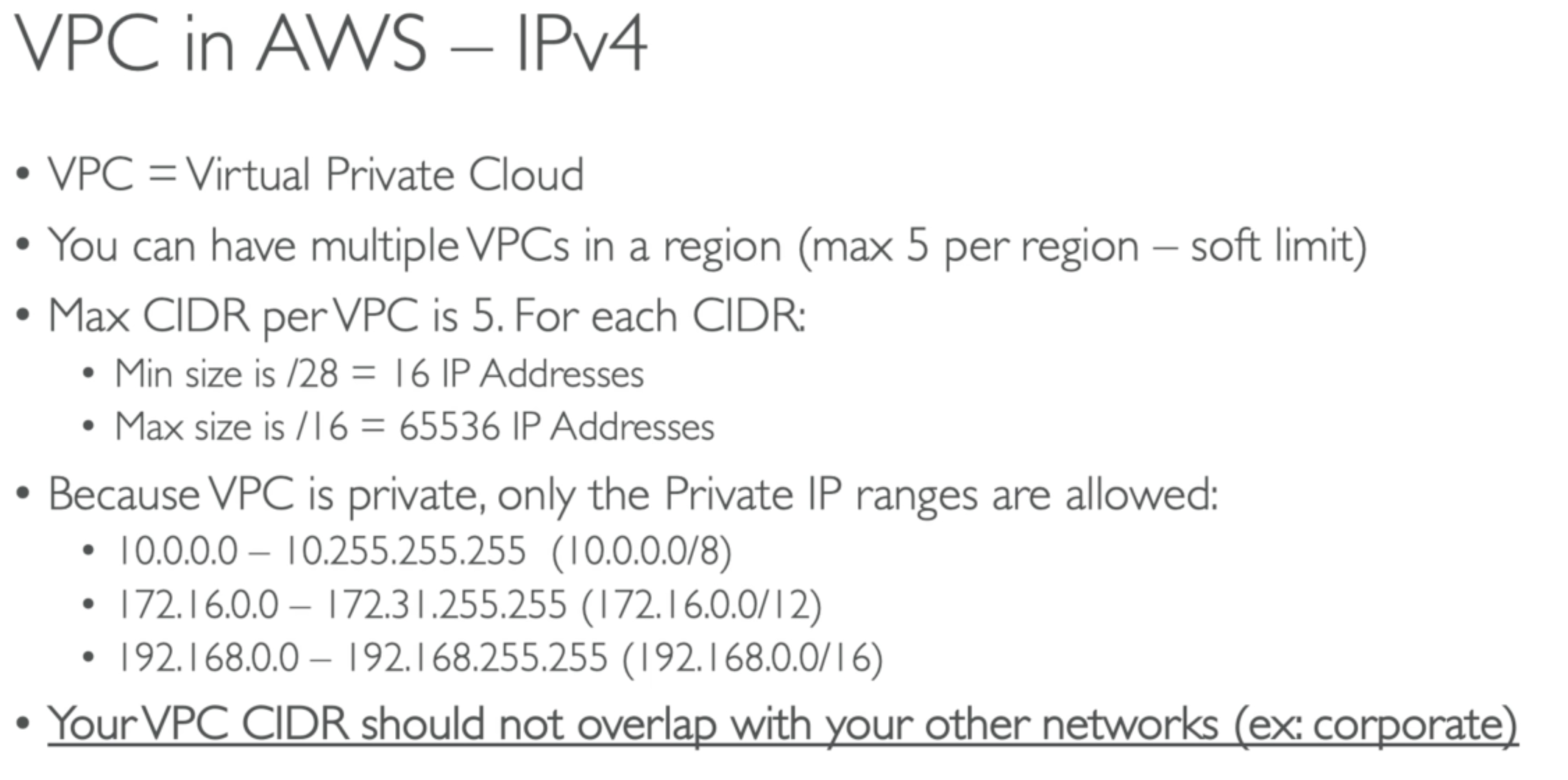
CIDR
CLI
EC2 에는 aws personal account정보 절대 기입하지 말자!!!!보안상 위험(aws configure)
-IAM role을 사용하자 무조건!!!!!!!!!!
-aws configure에서 Default region name만 현재 region적어주기.
aws s3 ls: s3버킷 목록 확인
aws s3 ls s3://bucket_name: 특정 버킷 내의 파일들 확인
aws s3 mb s3://new_bucket_name :버킷 새로 만들기
aws s3 cp s3://bucket_name/file_name [내 컴퓨터에 저장할 때 사용할 파일 이름]: 파일 복사,저장
Policies
https://policysim.aws.amazon.com/
Cloudwatch
note: EC2 Memory usage is by default not pushed(must be pushed from inside the instance as a custom metric)