You’ve taken the plunge, navigated the exchanges, and successfully purchased your first (or next) batch of cryptocurrency. Congratulations! But the journey doesn’t end there. In the dynamic world of digital assets, knowing how to store cryptocurrency securely is just as crucial as knowing how to buy it. Protecting your investments from theft, loss, or unauthorized access is paramount to safeguarding your digital wealth.
This guide will walk you through the essential steps and best practices for storing your cryptocurrency safely after you’ve acquired it. We’ll explore different wallet options, delve into robust security measures, and provide practical tips to ensure your holdings remain secure for the long term.
Understanding Why Secure Storage is Critical
Holding cryptocurrency gives you direct control over your assets, unlike traditional finance where intermediaries manage funds. This control comes with significant responsibility. If your private keys are compromised or lost, your cryptocurrency can be stolen or become permanently inaccessible. Exchanges, while convenient for trading, can be targets for hackers, and keeping large amounts of crypto on them long-term carries inherent risks. Implementing secure storage practices is your best defense against these threats.
Choosing the Right Cryptocurrency Wallet
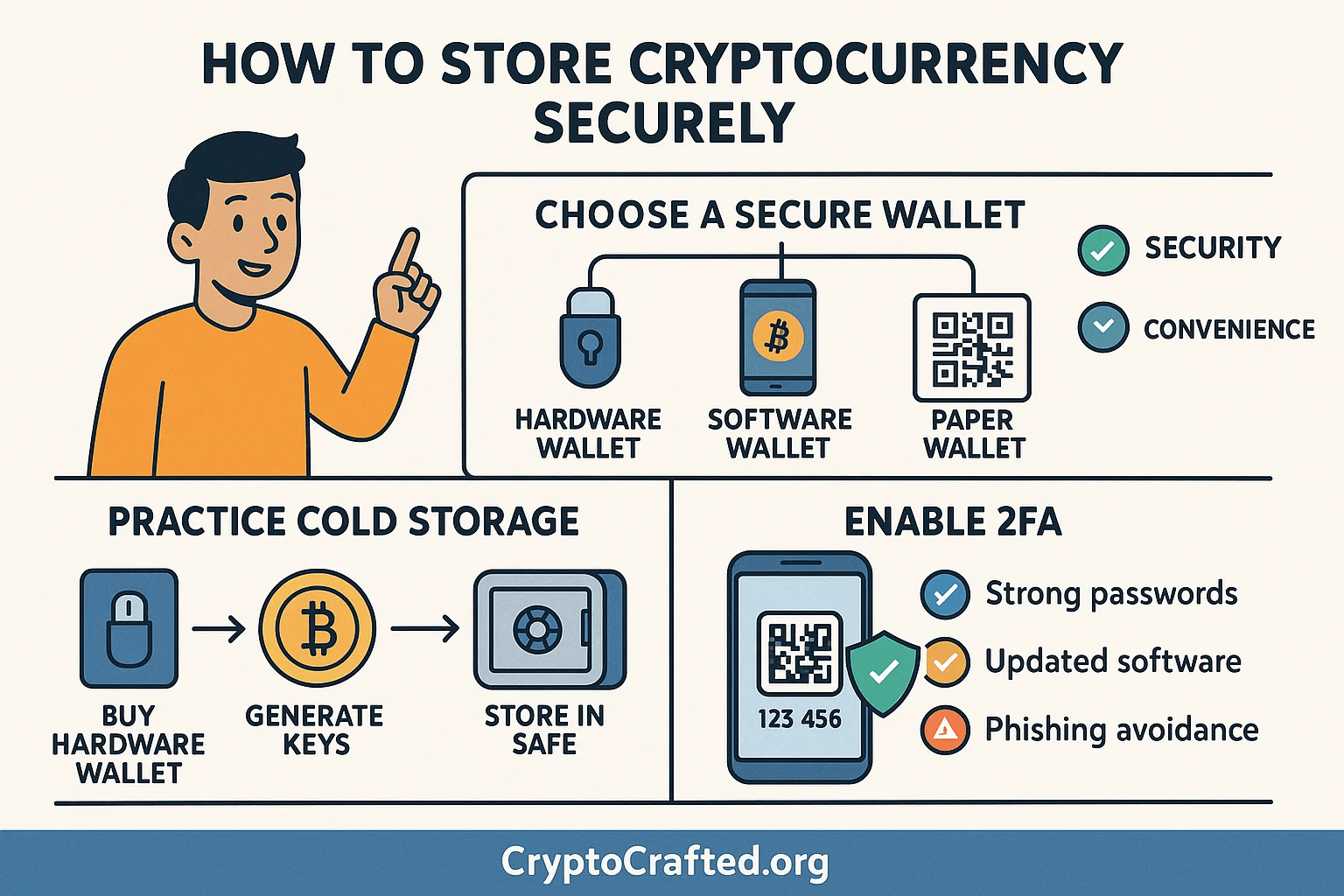
After purchasing cryptocurrency on an exchange, the next critical step is often to transfer it to a secure personal wallet. A cryptocurrency wallet is essentially a digital tool that manages your private keys – the cryptographic codes that prove ownership and allow you to spend your cryptocurrency. Wallets don't technically "store" the crypto itself (which lives on the blockchain), but they provide the necessary access. Choosing the right wallet depends on your needs regarding security, accessibility, and the amount of cryptocurrency you hold.
Types of Cryptocurrency Wallets
Wallets come in various forms, each offering different levels of security and convenience:
- Hardware Wallets: These are physical devices designed specifically to store your private keys offline.
- Security: Offer the highest level of security by keeping keys isolated from internet-connected devices (cold storage). They are highly resistant to online hacking and malware.
- Examples: Popular brands include Ledger, Trezor, and KeepKey.
- Usage: You connect the device to your computer or mobile via USB or Bluetooth to authorize transactions, requiring physical confirmation on the device itself.
- Software Wallets: These are applications or programs installed on your computer, smartphone, or accessed via a web browser.
- Convenience: Offer easy access for frequent transactions.
- Security: Security depends heavily on the security of the device they are on and the user's practices. They are more vulnerable to online threats than hardware wallets.
- Sub-types:
- Desktop Wallets: Installed on your computer (e.g., Electrum, Exodus, Atomic Wallet).
- Mobile Wallets: Smartphone apps for on-the-go access (e.g., Trust Wallet, MyEtherWallet, Coinomi).
- Web Wallets: Accessed through a web browser (e.g., exchange wallets, some standalone web services). Require caution due to phishing and server breach risks.
- Paper Wallets: A physical document with your cryptocurrency keys (public and private) printed on it, often as QR codes.
- Security: Provide offline storage, making them immune to online hacking.
- Security Risks: Susceptible to physical damage (fire, water) or loss. Need secure physical storage. Generated securely using offline tools like Bitaddress.org or WalletGenerator.net.
- Brain Wallets: Generating keys from a memorized passphrase.
- Security: Ultimate offline storage.
- Security Risks: Highly risky if the passphrase is weak, forgotten, or compromised. Not generally recommended due to the difficulty of creating truly random passphrases.
- Multi-Signature Wallets (Multisig): Require multiple private keys (held by different individuals or devices) to authorize a transaction.
- Security: Adds an extra layer of security, preventing a single point of failure. Often used for joint accounts or organizational funds.
Key Considerations When Choosing Your Wallet
Selecting the best wallet for your needs involves balancing security, accessibility, and ease of use.
- Security Features: Prioritize wallets known for strong security measures like encryption and 2FA (two-factor authentication). Look for wallets with a proven track record and avoid those with past security breaches. Hierarchical Deterministic (HD) key generation is also a plus, allowing easy backup from a single seed phrase.
- Compatibility: Ensure the wallet supports the specific cryptocurrencies you own or plan to hold. Some wallets are currency-specific (like official Bitcoin or Ethereum wallets), while others are multi-currency.
- Ease of Use: Choose a wallet with an intuitive interface that makes sending, receiving, and managing your holdings straightforward. Consider the user experience, especially if you are new to crypto.
- Backup and Recovery: Your wallet must provide a reliable way to back up your private keys or seed phrase (a list of words that can regenerate your wallet). Store this backup securely offline in multiple locations. Losing your seed phrase means losing access to your crypto, regardless of how secure the wallet itself is.
- Community Support: A strong community or dedicated support channels can be invaluable if you encounter issues or have questions about using the wallet securely.
For significant long-term holdings, hardware wallets are generally considered the gold standard due to their offline storage ("cold storage"). Software wallets are useful for smaller amounts or for frequent transactions.
Implementing Robust Security Measures
Selecting a secure wallet is just the beginning. Proactive security practices are essential to protect your cryptocurrency holdings.
- Enable Two-Factor Authentication (2FA): Always enable 2FA on your exchange accounts and any wallet services that offer it. This adds an extra layer of security requiring a second form of verification (like a code from an authenticator app or SMS) in addition to your password.
- Use Strong, Unique Passwords: Create complex, unique passwords for each crypto-related account. Avoid using easily guessable information. Consider using a reputable password manager to generate and store them securely.
- Keep Software Updated: Regularly update your wallet software, operating system, and antivirus programs. Updates often include critical security patches that protect against newly discovered vulnerabilities, malware, and exploits. Enable automatic updates whenever possible.
- Beware of Phishing Scams: Be extremely vigilant against phishing attempts. Scammers use fake websites, emails, or social media messages designed to steal your private keys or login credentials. Always double-check URLs, verify the authenticity of communications, and never click suspicious links or download attachments from unknown sources.
- Secure Your Private Keys and Seed Phrase: Your private keys and seed phrase are the ultimate access to your crypto. Store them offline in secure locations – this is where hardware wallets excel. If using paper or digital backups (on an encrypted USB drive, for example), ensure they are stored safely away from potential threats and never share them or store them unencrypted on cloud services.
- Implement Cold Storage: For large amounts of cryptocurrency, actively practice cold storage by moving funds off exchanges and into hardware or paper wallets that remain offline. This minimizes the attack surface.
- Exercise Caution with Third-Party Services: If using lending platforms, staking services, or other third-party platforms, conduct thorough research and understand the risks involved. Entrusting your funds means relying on their security measures, which may not be as robust as personal cold storage.
- Prepare for Emergencies: Have a contingency plan. Know how to access your wallet if your primary device is lost or damaged. Understand the recovery process using your seed phrase. Consider multi-signature wallets for added redundancy in accessing funds.
Monitoring Your Investments Safely
While storing securely is key, staying informed about your investments and the market is also important. Use reliable portfolio tracking apps or websites (be mindful of security when connecting APIs) and monitor the market through reputable news sources. Setting realistic goals and understanding market trends will help you make informed decisions, but always prioritize the security of your holdings above all else.
Conclusion
Storing your cryptocurrency securely after purchase is a fundamental step in managing your digital assets responsibly. By understanding the different types of wallets available, choosing options that prioritize robust security features, and diligently following best practices like enabling 2FA, securing your private keys offline, and staying vigilant against scams, you significantly reduce the risk of loss. Taking these steps ensures you maintain full control over your investments and can confidently navigate the exciting yet challenging world of cryptocurrency.
Ready to take the next step in your crypto journey? If you haven't yet purchased cryptocurrency, learn how to buy cryptocurrency safely and efficiently.
Learn How to Buy Cryptocurrency Safely Here →
