👩💻0705[terraform,ansible]
📌 terraform - azure[git]
[root@localhost ~]# git clone https://github.com/hali-linux/azure_set.git
[root@localhost azure_set]# terraform output -raw tls_private_key > azure-key.pem
[root@localhost azure_set]# terraform output public_ip_address
"20.214.236.120"
[root@localhost azure_set]# ssh -i azure-key.pem azureuser@20.214.236.120
📌 GCP
📙 CLI
[root@localhost ~]# mkdir gcp_cli && cd $_
[root@localhost gcp_cli]# tee -a /etc/yum.repos.d/google-cloud-sdk.repo << EOM
[google-cloud-cli]
name=Google Cloud CLI
baseurl=https://packages.cloud.google.com/yum/repos/cloud-sdk-el8-x86_64
enabled=1
gpgcheck=1
repo_gpgcheck=0
gpgkey=https://packages.cloud.google.com/yum/doc/yum-key.gpg
https://packages.cloud.google.com/yum/doc/rpm-package-key.gpg
EOM
[root@localhost gcp_cli]# yum install -y google-cloud-cli
[root@localhost gcp_cli]# gcloud --version
[root@localhost gcp_cli]# gcloud init --console-only
✔️아래 링크 진입
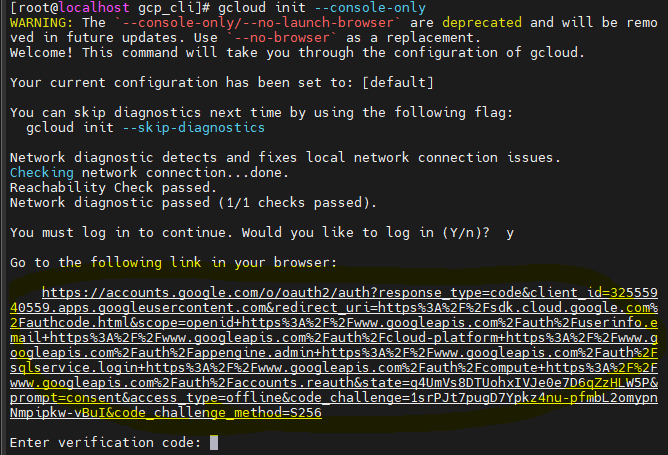
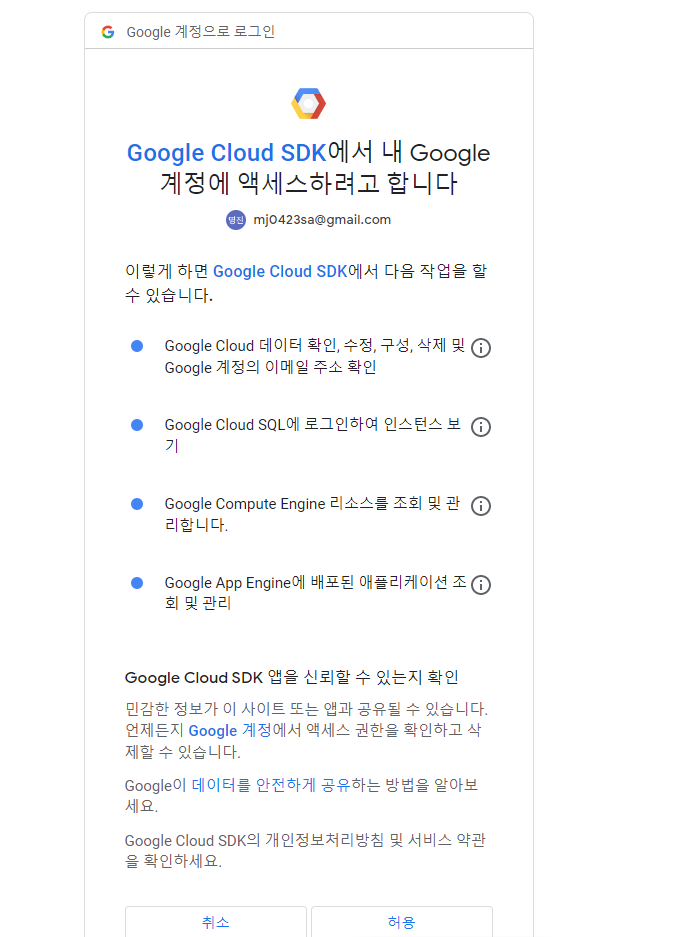
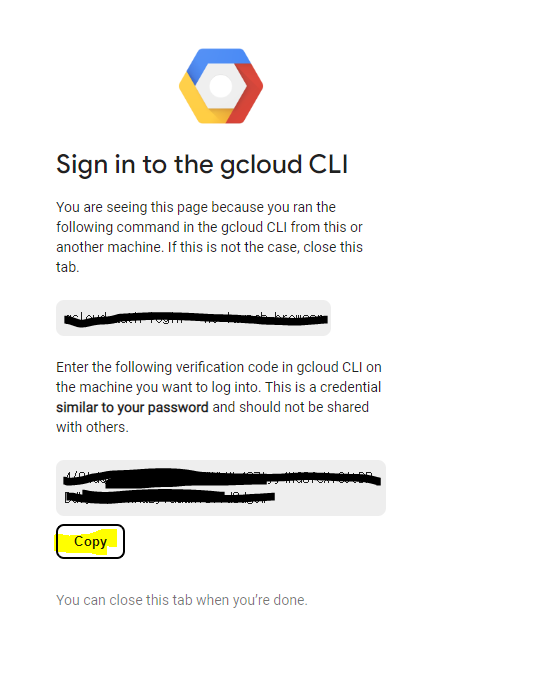
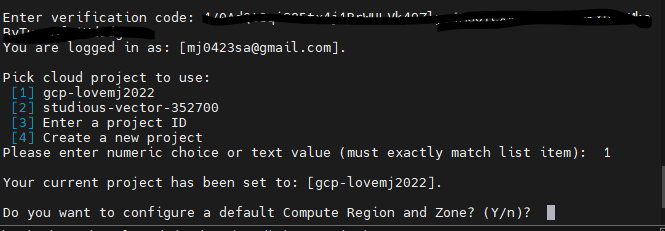
Do you want to configure a default Compute Region and Zone? (Y/n)? y
Which Google Compute Engine zone would you like to use as project default?
If you do not specify a zone via a command line flag while working with Compute
Engine resources, the default is assumed.
...
[47] asia-northeast2-a
[48] asia-northeast2-b
[49] asia-northeast2-c
[50] asia-northeast3-a
Did not print [54] options.
Too many options [104]. Enter "list" at prompt to print choices fully.
Please enter numeric choice or text value (must exactly match list item): 50
-> 완료
# gcloud compute networks create new-vpc --subnet-mode=custom
# gcloud compute networks subnets create new-subnet --network=new-vpc --range=192.168.0.0/16 --region=asia-northeast3
# gcloud compute networks subnets list
# gcloud compute firewall-rules list
# gcloud compute firewall-rules create new-vpc-allow-ssh --allow=tcp:22 --description="Allow incoming traffic on TCP port 22" --direction=INGRESS --network=new-vpc --source-ranges 0.0.0.0/0
# gcloud compute firewall-rules create new-vpc-allow-http --allow=tcp:80 --description="Allow incoming traffic on TCP port 80" --direction=INGRESS --network=new-vpc --source-ranges 0.0.0.0/0
# gcloud compute images list | grep centos-cloud
# gcloud compute images describe centos-7-v20220621 \
--project=centos-cloud
# gcloud compute machine-types list --filter="zone:( asia-northeast3-a )"
# vi httpd-gcp.txt
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello GCP CLI" > /var/www/html/index.html
# gcloud compute instances create web01 \
--image=centos-7-v20220621 \
--image-project=centos-cloud \
--machine-type=e2-micro \
--network=new-vpc \
--subnet=new-subnet \
--tags http-server,https-server \
--zone=asia-northeast3-a \
--metadata-from-file=startup-script=httpd-gcp.txt
✔️GCP 브라우저에서 로그인 - 프로젝트 ID 확인
!-- 사용자 이름 임의(lovemj)로 내가 넣기 --!
[root@localhost gcp_cli]# ssh-keygen -t rsa -f /root/.ssh/lovemj -C lovemj -b 2048
# vi /root/.ssh/lovemj.pub
lovemj:ssh-rsa ~~ blahblah
# gcloud compute os-login ssh-keys add \
--key-file=/root/.ssh/lovemj.pub \
--project=gcp-lovemj2022 \
--ttl=365d
# gcloud compute instances add-metadata web01 --metadata-from-file ssh-keys=/root/.ssh/lovemj.pub
# gcloud compute instances describe web01
# curl 34.64.48.211
# ssh -i /root/.ssh/lovemj lovemj@34.64.48.211
# gcloud compute instances delete web01
# gcloud compute firewall-rules list
# gcloud compute firewall-rules delete new-vpc-allow-http
# gcloud compute firewall-rules delete new-vpc-allow-ssh
# gcloud compute networks subnets delete new-subnet
# gcloud compute networks delete new-vpc📙 terraform - GCP
# git clone https://github.com/hali-linux/gcp_set.git
# vi provider.tf
provider "google" {
credentials = file("credentials.json")
project = "gcp-lovemj2022"
region = "asia-northeast3"
zone = "asia-northeast3-a"
}
# vi main.tf
resource "google_compute_network" "custom-test" {
name = "new-vpc"
auto_create_subnetworks = false
}
resource "google_compute_subnetwork" "network-with-private-ip-ranges" {
name = "new-subnet"
ip_cidr_range = "192.168.0.0/16"
region = "asia-northeast3"
network = google_compute_network.custom-test.id
}
resource "google_compute_instance" "default" {
name = "vm-from-terraform"
machine_type = "e2-micro"
zone = "asia-northeast3-a"
boot_disk {
initialize_params {
image = "debian-cloud/debian-9"
}
}
network_interface {
network = "new-vpc"
subnetwork = "new-subnet"
access_config {
// Include this section to give the VM an external ip address
}
}
metadata_startup_script = file("/root/gcp_set/script.txt")
// Apply the firewall rule to allow external IPs to access this instance
tags = ["http-server","ssh-server"]
}
resource "google_compute_firewall" "http-server" {
name = "default-allow-http-terraform"
network = "new-vpc"
allow {
protocol = "tcp"
ports = ["80"]
}
// Allow traffic from everywhere to instances with an http-server tag
source_ranges = ["0.0.0.0/0"]
target_tags = ["http-server"]
}
resource "google_compute_firewall" "ssh-server" {
name = "default-allow-ssh-terraform"
network = "new-vpc"
allow {
protocol = "tcp"
ports = ["22"]
}
// Allow traffic from everywhere to instances with an http-server tag
source_ranges = ["0.0.0.0/0"]
target_tags = ["ssh-server"]
}
# vi output.tf
output "ip" {
value = "${google_compute_instance.default.network_interface.0.access_config.0.nat_ip}"
}
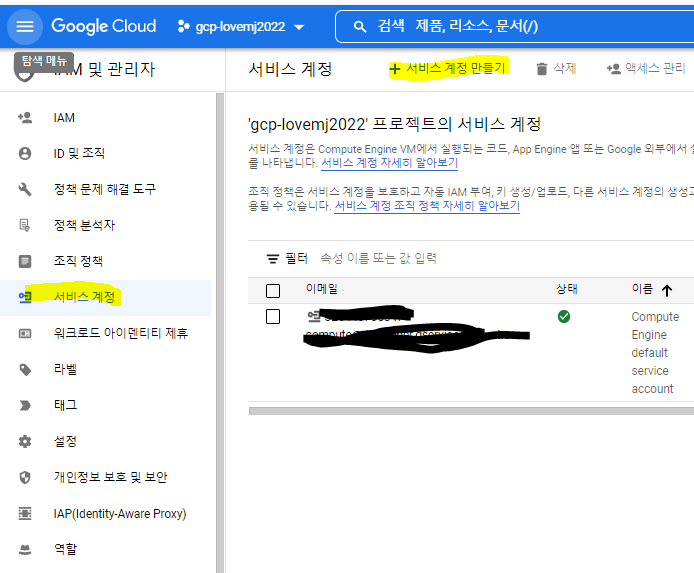
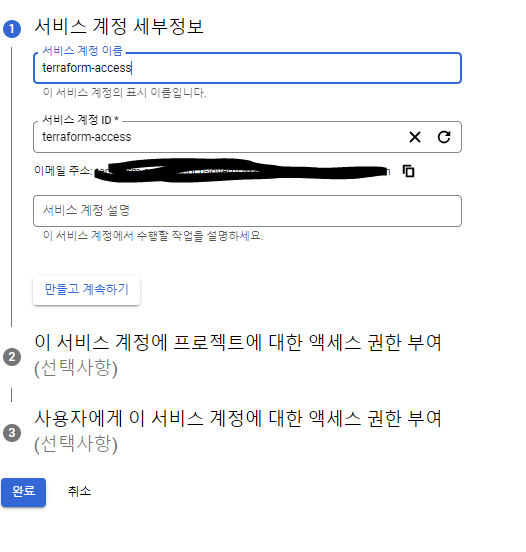
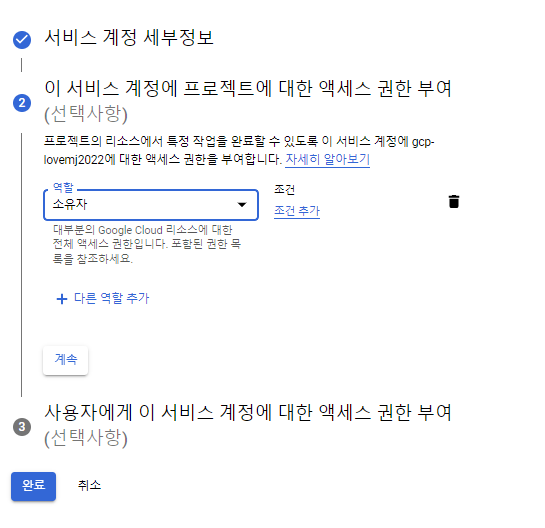
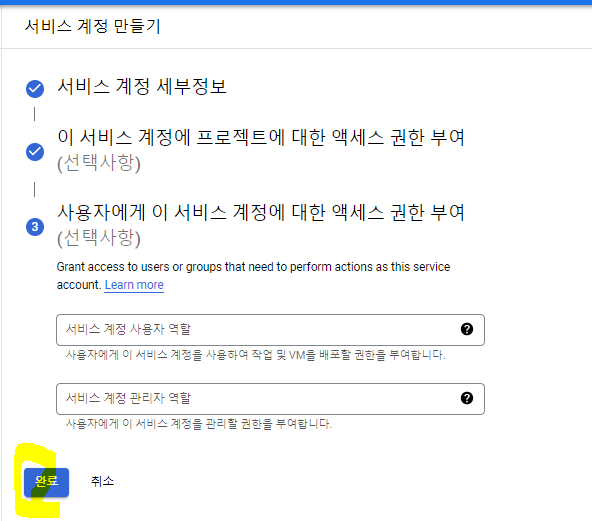
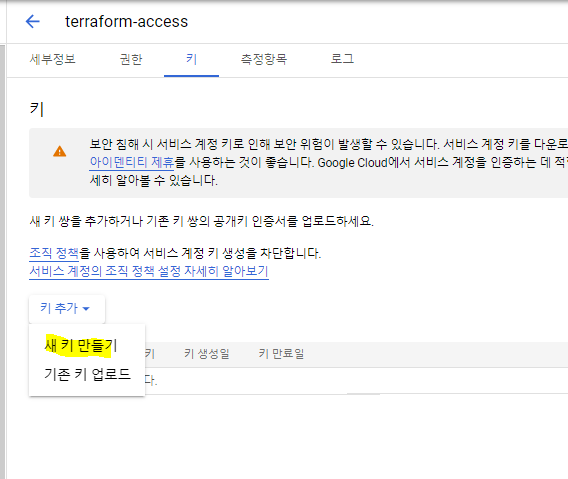
JSON - 만들기 - 파일이름 : credentials.JSON
# terraform init
# terraform plan
# terraform apply
# terraform output ip
# gcloud compute instances add-metadata vm-from-terraform --metadata-from-file ssh-keys=/root/.ssh/lovemj.pub
# ssh -i /root/.ssh/lovemj lovemj@34.64.48.211
# terraform destroy📌 ansible
📙 이론
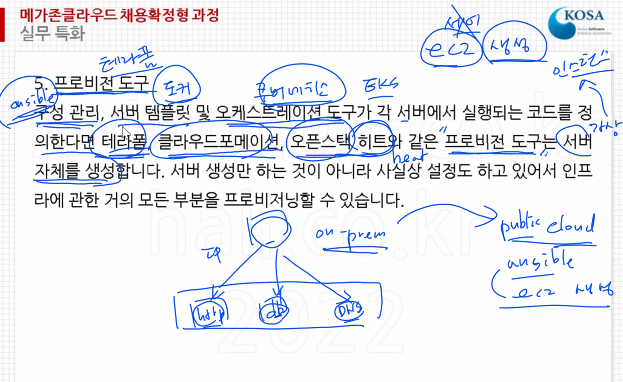
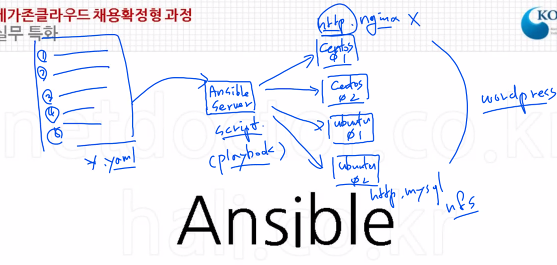
SSH 접속이 가능한 상태여야함.(우리가 원격을 접속해서 설치하는거랑 같은 원리)
- 파이썬이 있어야함.
📙 ansible-server
centos-node01
centos-node02
ununtu-node01
ununtu-node02
📙 ubuntu서버 생성
(centos는 이미 있음)
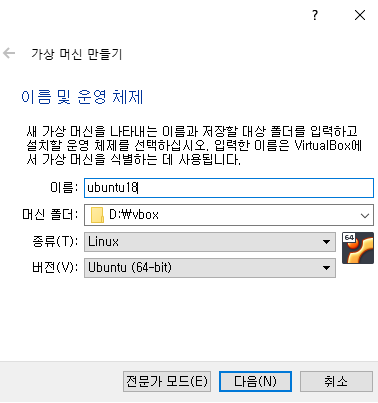
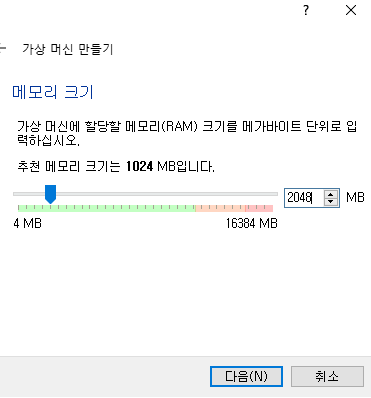
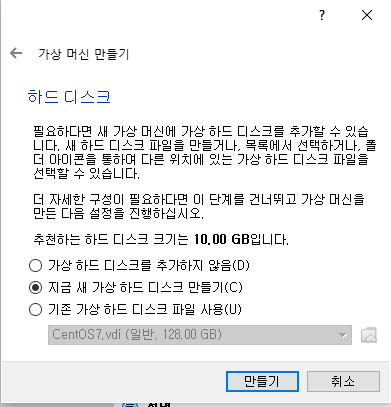
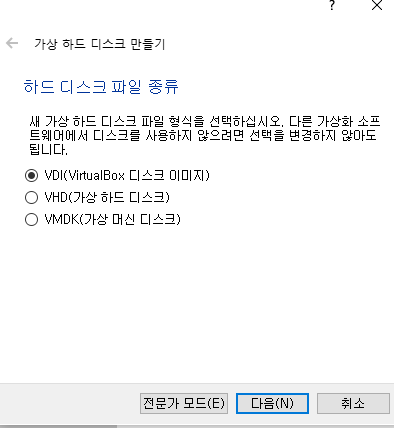
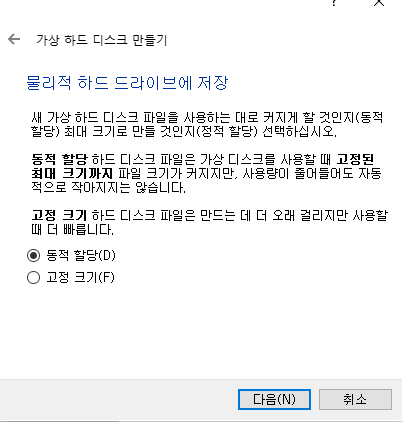
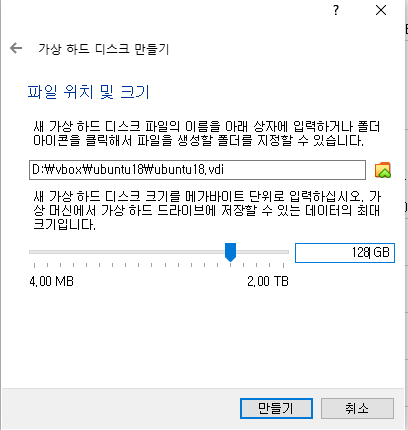
✔️만들기 클릭
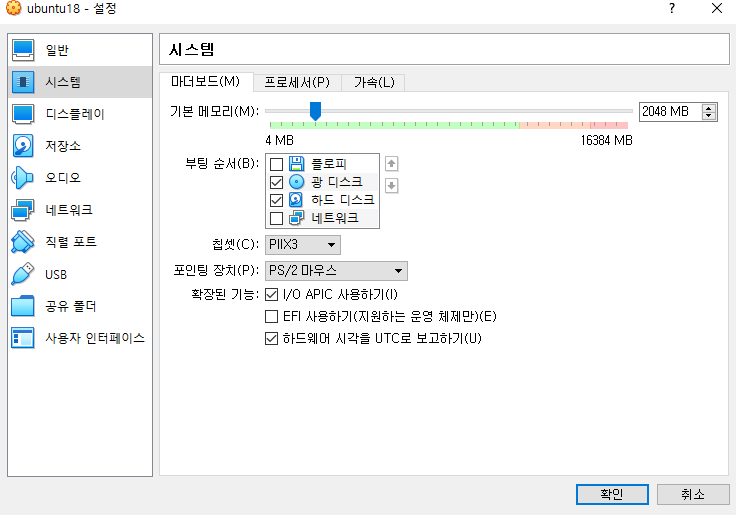
✔️상단 메뉴에서 설정 클릭 - 디스플레이 : 비디오메모리 : 9MB(초록색에서 최대한 작게) - 저장소 : 비어있음에 ubuntu18.04.4 셋팅 - 오디오 : 사용하기 해제 - 네트워크 : 어댑터에 브릿지 - USB : 컨트롤러 사용안함
✔️ 언어 english 로케이션 asia korea, 키보드 korea 101/104 - 사이에 뭐 나오는데 no - host name: ubuntu 그대로 - 사용자계정 원하는 ID ; mj - account ID ;mj - password 두번입력 - timezone 확인 후 yes or no - partitioning method : use entire disk - 디스크 확인 후 yes - http proxy? blank ( 그냥 엔터 ) - no automaitc update - openSSH server 스페이스 엔터- boot record: yes - continue
✔️ 서버진입해서 ip확인 후 mobaxterm으로 진입
mj@ubuntu:~$ sudo vi /etc/ssh/sshd_config
[sudo] password for mj:
#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
mj@ubuntu:~$ sudo su -
root@ubuntu:~# passwd root
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
mj@ubuntu:~$ sudo systemctl restart sshd
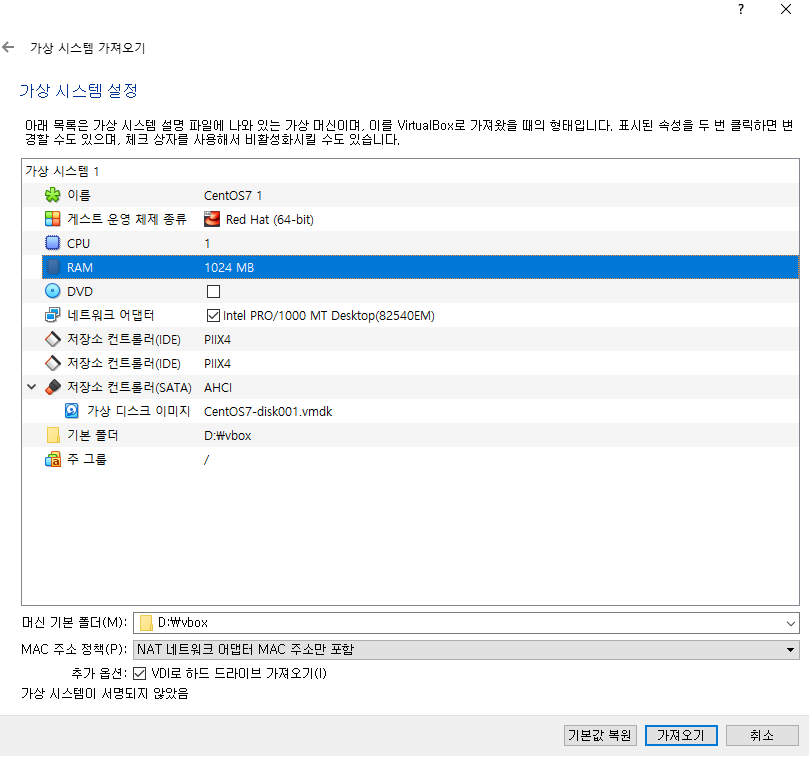
📙 centos ova로 가져오기
📙✔️✏️📢⭐️📌
📌 기타
⭐️ ssh 진입 오류 트러블 슈팅
[root@localhost gcp_set]# ssh -i /root/.ssh/lovemj lovemj@34.64.48.211
key_load_public: invalid format
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
SHA256:Jrzlnn4WHpyzdHsEtoi740IoZWtJe2tbygx0zRNh3JM.
Please contact your system administrator.
Add correct host key in /root/.ssh/known_hosts to get rid of this message.
Offending ECDSA key in /root/.ssh/known_hosts:4
ECDSA host key for 34.64.48.211 has changed and you have requested strict checking.
Host key verification failed.
-> know_hosts파일이 꼬여서 문제 발생 지워서 해결하자.
->재진입해서 yes하면 문제없음.
[root@localhost gcp_set]# rm /root/.ssh/known_hosts
