👩💻0704[terraform]
📌 terraform - asg
✔️ 변수 설명
variable "instance_security_group_name" {
description = "The name of the security group for the EC2 Instances"
type = string
default = "terraform-example-instance"
}
variable " " ; 변수 명
default ; 변수 내용
✔️ 변수 파일 만들기
[root@localhost ~]# mkdir asg
[root@localhost ~]# cd asg
[root@localhost asg]# vi variables.tf
variable "instance_security_group_name" {
description = "The name of the security group for the EC2 Instances"
type = string
default = "terraform-example-instance"
}
variable "http_port" {
description = "The port the server will use for HTTP requests"
type = number
default = 80
}
variable "ssh_port" {
description = "The port the server will use for SSH requests"
type = number
default = 22
}
variable "alb_name" {
description = "The name of the ALB"
type = string
default = "terraform-asg-example"
}
variable "alb_security_group_name" {
description = "The name of the security group for the ALB"
type = string
default = "terraform-example-alb"
}📙 main 파일 만들기
✔️ 구성데이터 생성
[root@localhost asg]# vi user-data.sh
#!/bin/bash
yum install -y httpd
systemctl enable --now httpd
echo "Hello AWS Terraform" > /var/www/html/index.html
timedatectl set-timezone Asia/Seoul
rdate -s time.bora.net
echo $(date +"%H:%M:%S") >> /var/www/html/index.html
sleep 600
yes > /dev/null &
✔️ 메인 파일 생성
[root@localhost asg]# vi main.tf
provider "aws" {
region = "ap-northeast-2"
}
### new-vpc ###
resource "aws_vpc" "new_vpc" {
cidr_block = "192.168.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
tags = {
Name = "NEW-VPC"
}
}
data "aws_availability_zones" "available" {
state = "available"
}
resource "aws_subnet" "new_public_subnet_2a" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.0.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[0]
tags = {
Name = "NEW-PUBLIC-SUBNET-2A"
}
}
resource "aws_subnet" "new_public_subnet_2b" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.16.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[1]
tags = {
Name = "NEW-PUBLIC-SUBNET-2B"
}
}
resource "aws_subnet" "new_public_subnet_2c" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.32.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[2]
tags = {
Name = "NEW-PUBLIC-SUBNET-2C"
}
}
resource "aws_subnet" "new_public_subnet_2d" {
vpc_id = aws_vpc.new_vpc.id
cidr_block = "192.168.48.0/20"
map_public_ip_on_launch = true
availability_zone = data.aws_availability_zones.available.names[3]
tags = {
Name = "NEW-PUBLIC-SUBNET-2D"
}
}
resource "aws_internet_gateway" "new_igw" {
vpc_id = aws_vpc.new_vpc.id ## attach
tags = {
Name = "NEW-IGW"
}
}
resource "aws_route_table" "new_public_rtb" {
vpc_id = aws_vpc.new_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.new_igw.id
}
tags = {
Name = "NEW-PUBLIC-RTB"
}
}
resource "aws_route_table_association" "new_public_subnet_2a_association" {
subnet_id = aws_subnet.new_public_subnet_2a.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2b_association" {
subnet_id = aws_subnet.new_public_subnet_2b.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2c_association" {
subnet_id = aws_subnet.new_public_subnet_2c.id
route_table_id = aws_route_table.new_public_rtb.id
}
resource "aws_route_table_association" "new_public_subnet_2d_association" {
subnet_id = aws_subnet.new_public_subnet_2d.id
route_table_id = aws_route_table.new_public_rtb.id
}
### asg ###
resource "aws_security_group" "instance" {
name = var.instance_security_group_name
vpc_id = aws_vpc.new_vpc.id
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["112.221.225.165/32"]
}
ingress {
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_launch_configuration" "example" {
image_id = "ami-0fd0765afb77bcca7"
instance_type = "t2.micro"
security_groups = [aws_security_group.instance.id]
key_name = "new-key"
user_data = file("user-data.sh")
# Required when using a launch configuration with an auto scaling group.
lifecycle {
create_before_destroy = true
}
}
resource "aws_autoscaling_group" "example" {
launch_configuration = aws_launch_configuration.example.name
vpc_zone_identifier = [
aws_subnet.new_public_subnet_2a.id,
aws_subnet.new_public_subnet_2b.id,
aws_subnet.new_public_subnet_2c.id,
aws_subnet.new_public_subnet_2d.id
]
target_group_arns = [aws_lb_target_group.asg.arn]
health_check_type = "ELB"
min_size = 2
desired_capacity = 2
max_size = 4
tag {
key = "Name"
value = "terraform-asg-example"
propagate_at_launch = true
}
}
resource "aws_lb" "example" {
name = var.alb_name
load_balancer_type = "application"
subnets = [
aws_subnet.new_public_subnet_2a.id,
aws_subnet.new_public_subnet_2b.id,
aws_subnet.new_public_subnet_2c.id,
aws_subnet.new_public_subnet_2d.id
]
security_groups = [aws_security_group.alb.id]
}
resource "aws_lb_listener" "http" {
load_balancer_arn = aws_lb.example.arn
port = var.http_port
protocol = "HTTP"
# By default, return a simple 404 page
default_action {
type = "fixed-response"
fixed_response {
content_type = "text/plain"
message_body = "404: page not found"
status_code = 404
}
}
}
resource "aws_lb_target_group" "asg" {
name = var.alb_name
port = var.http_port
protocol = "HTTP"
vpc_id = aws_vpc.new_vpc.id
health_check {
path = "/"
protocol = "HTTP"
matcher = "200"
interval = 15
timeout = 3
healthy_threshold = 2
unhealthy_threshold = 2
}
}
resource "aws_lb_listener_rule" "asg" {
listener_arn = aws_lb_listener.http.arn
priority = 100
condition {
path_pattern {
values = ["*"]
}
}
action {
type = "forward"
target_group_arn = aws_lb_target_group.asg.arn
}
}
resource "aws_security_group" "alb" {
vpc_id = aws_vpc.new_vpc.id
name = var.alb_security_group_name
# Allow inbound HTTP requests
ingress {
from_port = var.http_port
to_port = var.http_port
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
# Allow all outbound requests
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_autoscaling_policy" "scale_in" {
name = "ScaleInPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = -1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_in" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_in.arn]
alarm_name = "ScaleInAlarm"
comparison_operator = "LessThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "30"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}
resource "aws_autoscaling_policy" "scale_out" {
name = "ScaleOutPolicy"
autoscaling_group_name = aws_autoscaling_group.example.name
adjustment_type = "ChangeInCapacity"
scaling_adjustment = 1
cooldown = 300
}
resource "aws_cloudwatch_metric_alarm" "scale_out" {
alarm_description = "Monitors CPU utilization for Terramino ASG"
alarm_actions = [aws_autoscaling_policy.scale_out.arn]
alarm_name = "ScaleOutAlarm"
comparison_operator = "GreaterThanOrEqualToThreshold"
namespace = "AWS/EC2"
metric_name = "CPUUtilization"
threshold = "70"
evaluation_periods = "1"
period = "300"
statistic = "Average"
dimensions = {
AutoScalingGroupName = aws_autoscaling_group.example.name
}
}✔️output 설정
# vi outputs.tf
output "alb_dns_name" {
value = aws_lb.example.dns_name
description = "The domain name of the load balancer"
}📌 git - aws_set
[root@localhost ~]# yum install -y git
[root@localhost ~]# git clone https://github.com/hali-linux/aws_set.git
[root@localhost aws_set]# mv user_data.sh user-data.sh
📌 Azure CLI
✔️ 초기설정
[root@localhost ~]# mkdir azure_cli && cd $_
[root@localhost azure_cli]# echo -e "[azure-cli]
> name=Azure CLI
> baseurl=https://packages.microsoft.com/yumrepos/azure-cli
> enabled=1
> gpgcheck=1
> gpgkey=https://packages.microsoft.com/keys/microsoft.asc" | sudo tee /etc/yum.repos.d/azure-cli.repo
[azure-cli]
name=Azure CLI
baseurl=https://packages.microsoft.com/yumrepos/azure-cli
enabled=1
gpgcheck=1
gpgkey=https://packages.microsoft.com/keys/microsoft.asc
[root@localhost azure_cli]# yum install -y azure-cli
[root@localhost azure_cli]# az upgrade
[root@localhost azure_cli]# az --version
✔️ CLI로그인
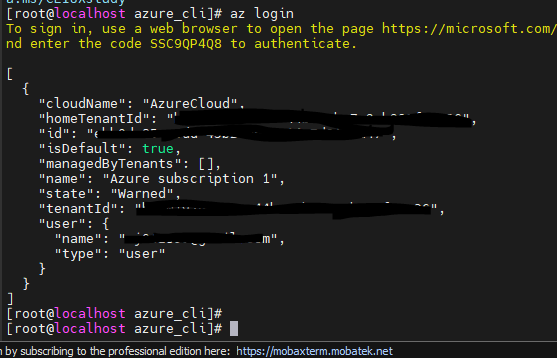
[root@localhost azure_cli]# az login
계정선택- 이미 애저에 로그인 해 둔 아이디 클릭 -
✔️
# resourceGroup=VMTutorialResources
# location=koreacentral
# az group create --name $resourceGroup --location $location
# vnetName=TutorialVNet1
# subnetName=TutorialSubnet1
# vnetAddressPrefix=10.114.0.0/16
# subnetAddressPrefix=10.114.0.0/24
# az network vnet create \
--name $vnetName \
--resource-group $resourceGroup \
--address-prefixes $vnetAddressPrefix \
--subnet-name $subnetName \
--subnet-prefixes $subnetAddressPrefix
# az network vnet list
# az vm image list
# vmName=TutorialVM1
# vi httpd.txt
#!/bin/bash
apt update
apt install -y apache2
echo "<h1>Hello Azure CLI</h1>" > /var/www/html/index.html
# az vm create \
--resource-group $resourceGroup \
--name $vmName \
--image UbuntuLTS \
--vnet-name $vnetName \
--subnet $subnetName \
--size Standard_B1s \
--custom-data httpd.txt \
--admin-username azureuser \
--generate-ssh-keys \
--output json \
--verbose
# az network nsg rule create \
--resource-group $resourceGroup \
--nsg-name TutorialVM1NSG \
--name myNetworkSecurityGroupRule \
--protocol tcp \
--priority 900 \
--destination-port-range 80
!--간략하게 포트번호 열기 / 우선순위 고려해서 추가해야함 --!
# az vm open-port -n $vmName -g $resourceGroup --port 443 --priority 999
# az vm list-ip-addresses
# ssh -i /root/.ssh/id_rsa azureuser@20.249.82.60
# az vm delete --resource-group $resourceGroup --name $vmName --yes
# az group delete -n $resourceGroup
# az group delete -n NetworkWatcherRG
📙 git - azure set
# git clone https://github.com/hali-linux/azure_set.git
# vi variables.tf
variable "resource_group_name_prefix" {
default = "rg"
description = "Prefix of the resource group name that's combined with a random ID so name is unique in your Azure subscription."
}
variable "resource_group_location" {
default = "koreacentral"
description = "Location of the resource group."
}
# vi main.tf
provider "azurerm" {
features {}
}
resource "random_pet" "rg-name" {
prefix = var.resource_group_name_prefix
}
resource "azurerm_resource_group" "rg" {
name = random_pet.rg-name.id
location = var.resource_group_location
}
# Create virtual network
resource "azurerm_virtual_network" "myterraformnetwork" {
name = "myVnet"
address_space = ["10.214.0.0/16"]
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
}
# Create subnet
resource "azurerm_subnet" "myterraformsubnet" {
name = "mySubnet"
resource_group_name = azurerm_resource_group.rg.name
virtual_network_name = azurerm_virtual_network.myterraformnetwork.name
address_prefixes = ["10.214.0.0/24"]
}
# Create public IPs
resource "azurerm_public_ip" "myterraformpublicip" {
name = "myPublicIP"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
allocation_method = "Dynamic"
}
# Create Network Security Group and rule
resource "azurerm_network_security_group" "myterraformnsg" {
name = "myNetworkSecurityGroup"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
security_rule {
name = "SSH"
priority = 1001
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "22"
source_address_prefix = "112.221.225.165/32"
destination_address_prefix = "*"
}
security_rule {
name = "HTTP"
priority = 1002
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "80"
source_address_prefix = "*"
destination_address_prefix = "*"
}
}
# Create network interface
resource "azurerm_network_interface" "myterraformnic" {
name = "myNIC"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
ip_configuration {
name = "myNicConfiguration"
subnet_id = azurerm_subnet.myterraformsubnet.id
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.myterraformpublicip.id
}
}
# Connect the security group to the network interface
resource "azurerm_network_interface_security_group_association" "example" {
network_interface_id = azurerm_network_interface.myterraformnic.id
network_security_group_id = azurerm_network_security_group.myterraformnsg.id
}
# Create (and display) an SSH key
resource "tls_private_key" "example_ssh" {
algorithm = "RSA"
rsa_bits = 4096
}
# Create virtual machine
resource "azurerm_linux_virtual_machine" "myterraformvm" {
name = "myVM"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
network_interface_ids = [azurerm_network_interface.myterraformnic.id]
size = "Standard_B1s"
os_disk {
name = "myOsDisk"
caching = "ReadWrite"
storage_account_type = "Premium_LRS"
}
source_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "18.04-LTS"
version = "latest"
}
computer_name = "myvm"
admin_username = "azureuser"
custom_data = filebase64("httpd-azure.txt")
disable_password_authentication = true
admin_ssh_key {
username = "azureuser"
public_key = tls_private_key.example_ssh.public_key_openssh
}
}
# vi outputs.tf
output "resource_group_name" {
value = azurerm_resource_group.rg.name
}
output "public_ip_address" {
value = azurerm_linux_virtual_machine.myterraformvm.public_ip_address
}
output "tls_private_key" {
value = tls_private_key.example_ssh.private_key_pem
sensitive = true
}
# terraform init
# terraform plan
# terraform apply
# terraform output -raw tls_private_key > azure-key.pem
# terraform output public_ip_address
# ssh -i id_rsa azureuser@<public_ip_address>
📙✔️✏️📢⭐️📌
📌 기타
⭐️ VPC, 서브넷 셋팅
✔️ 16비트로 쪼개고 20 비트로 또 쪼개는거 이해 안간다..!
⭐️healthcheck

상윗단에서 elb에서 헬스체크 ( 잘 이해 못함 )
⭐️ 404page
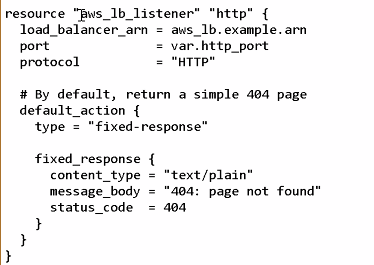
잘못된 접근 안내 페이지(fixed-response). 프론트에서 리스너.