정보보안
1.Cryptographic Hash Function

일반적인 Hash Function에 암호학적 성질을 추가한 Cryptographic Hash Function.
2021년 4월 9일
2.Birthday Attack
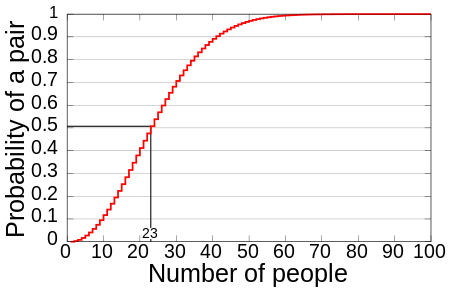
Birthday Attack H가지의 값을 가지는 암호학적 해시 함수 $f(x)$에 대해, $f(x1)=f(x2)$이고 $x1 \ne x2$인 두 입력값 x1, x2를 찾는 것이 해시 충돌의 목표이다.
2021년 4월 10일
3.SHAttered

SHA-1의 취약성에 대해 구글과 네덜란드 CWI연구소에서 SHA-1 해시함수의 충돌쌍을 생성하는 서비스를 공개하였다.
2021년 4월 10일
4.Attack Models in Cryptography

Attack models > 기본적으로 Attacker가 암호 알고리즘을 알고 있다는 것을 가정한다. plaintext: 평문 ciphertext: 암호문 Ciphertext Only Attack(COA) Attacker는 해독해야 할 ciphertext을 알고
2022년 10월 17일