
공격자(Attacker)
공격자가 하는 일
1. Target 선정 작업
2. Target 선정
3. 취약점 공격(파괴, 데이터 유출, 도청)
4. Log 삭제
5. 백도어 설치
Port Scan 이란?
공격 대상을 결정하거나 공격 방법을 결정할 때 네트워크 구조, 시스템이 제공하는 서비스 등의 정보를 얻기 위해 수행되는 방법
Port Scan으로 확인할 수 있는 것
- 공격 대상 보안장비 사용현황
- 우회 가능 네트워크
특정 컴퓨터의 1~65535개 중에서 어느 포트가 열려있는지 확인 하는 작업이다. 예를 들어 내가 도둑이라고 가정했을 때 문이 열려있는지 확인해보는 것과 동일하다.
1. ping 확인
✔ VMware에 설치한 Kali Linux에서 진행한다.
✔ Wireshark 실행
터미널
# 그룹 ping 확인 192.168.10.0 부터 10.24까지
$ fping -g 192.168.10.0/24Wireshark
ARP에서 Operation Code로 Alive한 IP찾기
Operation Code로 찾을 경우
arp.opcode == 1 (request)
arp.opcode == 2 (reply)프로토콜로 찾을 경우
ICMPAlive IP 확인
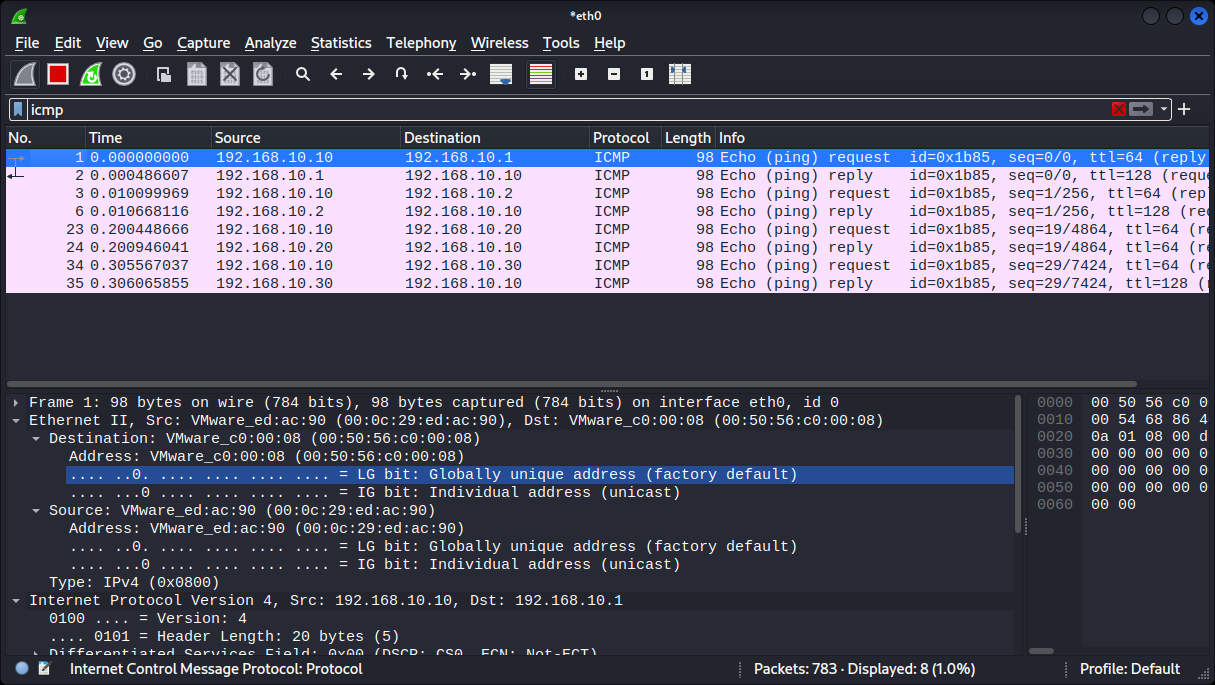
192.168.10.1
192.168.10.2
192.168.10.10
192.168.10.20
192.168.10.30nmap으로 Port 스캔
TCP Full Open Scan이란?
3-way handshaking 를 이용한 방법
# 형식
nmap -sT [대상 IP]단시간에 RST, ACK 발생되면 Port Scan이 들어왔다고 알 수 있다.
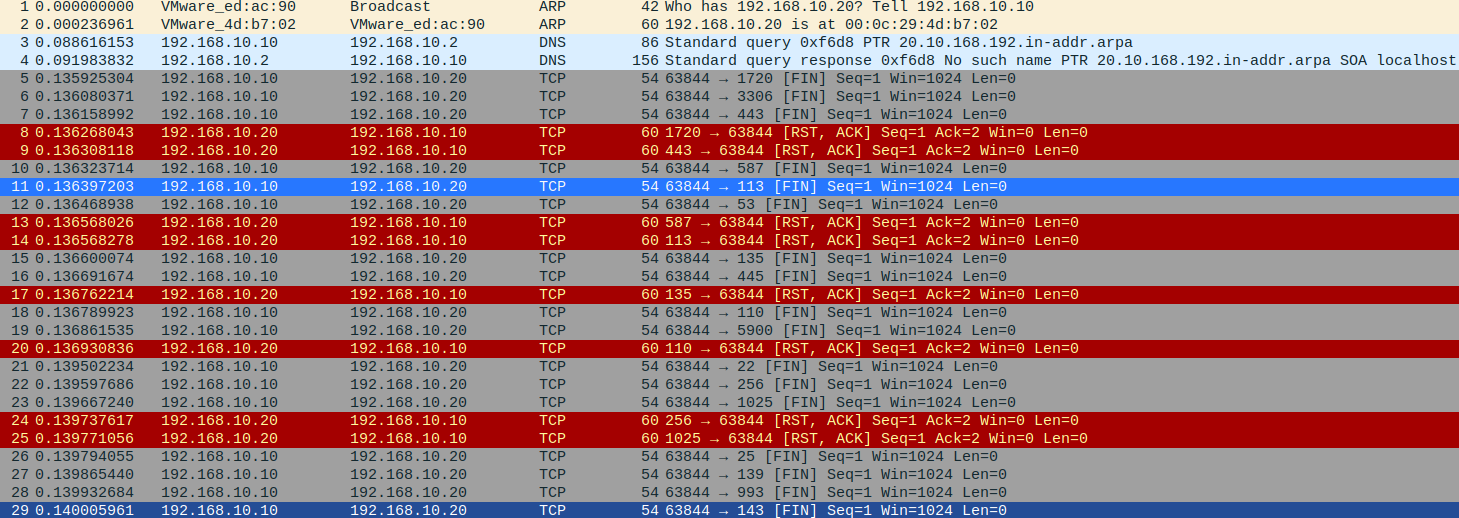
TCP Full Open Scan의 단점
정직하게 3whs를 이용하면 공격자가 노출된다. 왜? 3whs을 정직하게 하기 때문에 ⇒ 보통 사내망 보안관리자들이 포트 확인을 위해 사용한다.
192.168.10.20 스캔
nmap -sT 192.168.10.20Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-15 23:45 EST
Nmap scan report for 192.168.10.20
Host is up (0.0018s latency).
Not shown: 977 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.31 seconds192.168.10.30의 포트 스캔
nmap -sT 192.168.10.30Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-15 23:50 EST
Nmap scan report for 192.168.10.30
Host is up (0.00021s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5357/tcp open wsdapi
MAC Address: 00:0C:29:53:E1:EC (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.50 secondshidden으로 처리되어야 할 내용을 오픈한다.
# 형식
nmap -sT -O [대상 IP]nmap -sT -O 192.168.10.20Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:04 EST
Nmap scan report for 192.168.10.20
Host is up (0.00057s latency).
Not shown: 977 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
# OS / 커널 정보-----------------------
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop # 나와의 거리가 얼마나 떨어져 있는지
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.82 seconds192.168.10.30 스캔
nmap -sT -O 192.168.10.30Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:07 EST
Nmap scan report for 192.168.10.30
Host is up (0.00063s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5357/tcp open wsdapi
MAC Address: 00:0C:29:53:E1:EC (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=11/16%OT=135%CT=1%CU=35950%PV=Y%DS=1%DC=D%G=Y%M=000C29
OS:%TM=6555A3B2%P=x86_64-pc-linux-gnu)SEQ(SP=109%GCD=1%ISR=106%TI=I%CI=I%II
OS:=I%SS=S%TS=U)OPS(O1=M5B4NW8NNS%O2=M5B4NW8NNS%O3=M5B4NW8%O4=M5B4NW8NNS%O5
OS:=M5B4NW8NNS%O6=M5B4NNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF
OS:70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M5B4NW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=
OS:S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y
OS:%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD
OS:=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0
OS:%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1
OS:(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI
OS:=N%T=80%CD=Z)
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.69 seconds20과 30을 비교했을 때 30을 공격하는 것이 좋다.
445/tcp 가 open 상태라서
Wireshark로 확인
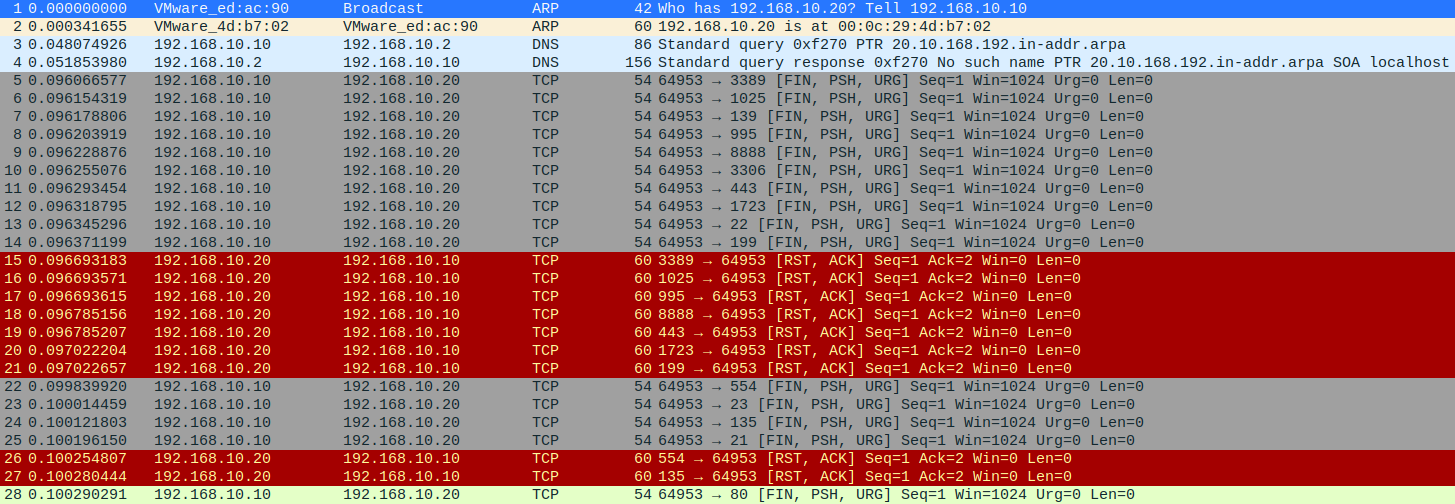
계속 포트번호를 바꿔서 SYN를 보내는 것을 확인할 수 있다.
TCP Half Open Scan이란?
TCP Full Open Scan 시 로그가 남는다. 그러므로 Half Open Scan을 한다.
nmap -sS 192.168.10.20 Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:30 EST
Nmap scan report for 192.168.10.20
Host is up (0.00062s latency).
Not shown: 977 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.33 seconds열린 포트
Attacker 10 --SYN--> Target 20
Attacker 10 <--RST/ARK-- Target 20
Attacker 10 --ACK--> Target 20
Stealth Scan
- 3-Way Handshaking 연결 기법을 이용한 것이 아님
⇒ 로그에 내용이 남지 않는다. - TCP 헤더를 조작해서 특수한 패킷을 생성 -> 스캔 대상의 시스템에 보내어 그 응답으로 포트 활성화 여부를 알아내는 기법
FIN scan
$ nmap -sF [대상 IP]FINflag를 설정해서 공격대상에 메세지 전송
Flags 에서FIN은 세션 종료할 때 사용
포트 활성화 여부 확인 방법
- 열린 포트 or 차단정책으로 차단된 경우
Attacker 가FIN보내면 Target은 응답 X - 닫힌 포트의 경우
Attacker 가FIN보내면 Target은RSKACK응답
$ nmap -sF 192.168.10.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:38 EST
Nmap scan report for 192.168.10.20
Host is up (0.00061s latency).
Not shown: 977 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.44 secondsXmas Scan
$ nmap -sX [대상 IP]스캔 시 flag가 UGR PSH FIN 로
UGR PSH는 함께 있을 수 있지만 FIN 은 종료 flag기 때문에 앞선 flag와 함께 있을 수가 없다. 말이 안된다는 얘기.
포트 활성화 여부 확인 방법
- 열린 포트 or 차단정책으로 차단된 경우
Attacker 가UGRPSHFIN보내면 Target은 응답 X - 닫힌 포트의 경우
Attacker 가UGRPSHFIN보내면 Target은RSKACK응답
$ nmap -sX 192.168.10.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:45 EST
Nmap scan report for 192.168.10.20
Host is up (0.00019s latency).
Not shown: 977 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.43 secondsNull Scan
$ nmap -sN [대상 IP]$ nmap -sN 192.168.10.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 00:57 EST
Nmap scan report for 192.168.10.20
Host is up (0.0011s latency).
Not shown: 977 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open|filtered ftp
22/tcp open|filtered ssh
23/tcp open|filtered telnet
25/tcp open|filtered smtp
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
139/tcp open|filtered netbios-ssn
445/tcp open|filtered microsoft-ds
512/tcp open|filtered exec
513/tcp open|filtered login
514/tcp open|filtered shell
1099/tcp open|filtered rmiregistry
1524/tcp open|filtered ingreslock
2049/tcp open|filtered nfs
2121/tcp open|filtered ccproxy-ftp
3306/tcp open|filtered mysql
5432/tcp open|filtered postgresql
5900/tcp open|filtered vnc
6000/tcp open|filtered X11
6667/tcp open|filtered irc
8009/tcp open|filtered ajp13
8180/tcp open|filtered unknown
MAC Address: 00:0C:29:4D:B7:02 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.42 seconds- 패킷 1, 2번을 보면 처음에 ARP도 함께 보낸다. 왜? MAC주소를 알아내기 위해서
- flag가
<None>으로 온다면 포트 스캔을 의심할 수 있다.
UDP scan
$ nmap -sU [대상 IP]- 3-way handshake 같은 절차 X
- UDP 패킷 전송 시 열려있는 포트로부터 특정 UDP 응답값으로 수신
- 수신측 포트가 닫혀있는 경우
ICMP Port Unreachable에러 메세지를 통해 포트 활성화 유무 확인 가능
$ nmap -sU 192.168.10.20
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-16 01:29 EST