Docker Swarm
ubuntu 기본 이미지 + docker
-> new image 생성
-> glance에 등록
-> 2 volumes(manager, worker) 생성하여
manager에서 토큰 발행
worker는 토큰 이용하여 클러스터에 조인
- admin 접속
[root@localhost ~]# source keystonerc_admin
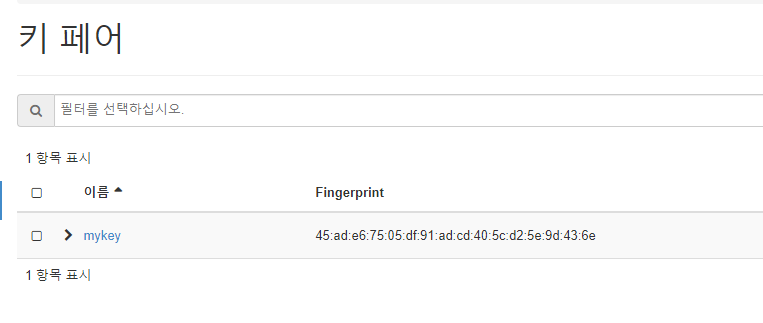
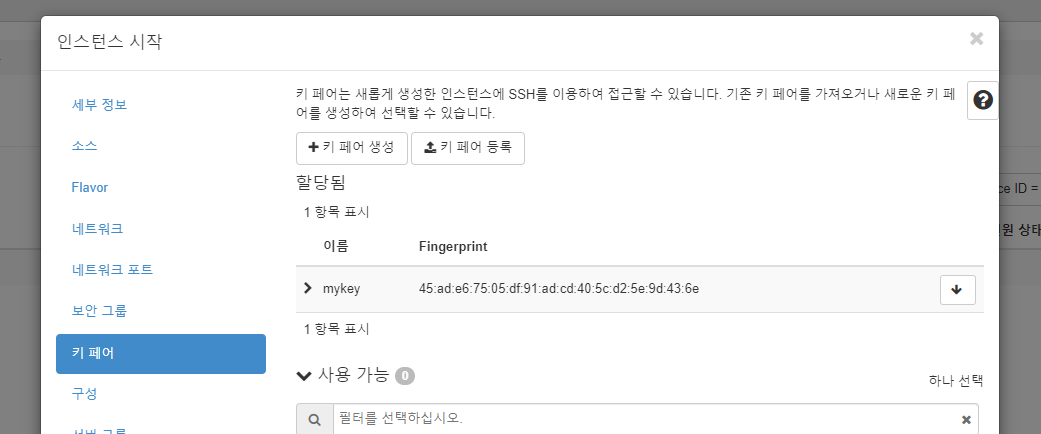
[root@localhost ~(keystone_admin)]# - 키페어 생성
[root@localhost ~(keystone_admin)]# ssh-keygen -q -f /root/.ssh/mykey.pem -N ""- 키페어 등록
[root@localhost ~(keystone_admin)]# openstack keypair create \
> --public-key /root/.ssh/mykey.pem.pub \
> mykey
+-------------+-------------------------------------------------+
| Field | Value |
+-------------+-------------------------------------------------+
| fingerprint | 45:ad:e6:75:05:df:91:ad:cd:40:5c:d2:5e:9d:43:6e |
| name | mykey |
| user_id | 4d4037b31688480e8ebce7c4619d8078 |
+-------------+-------------------------------------------------+
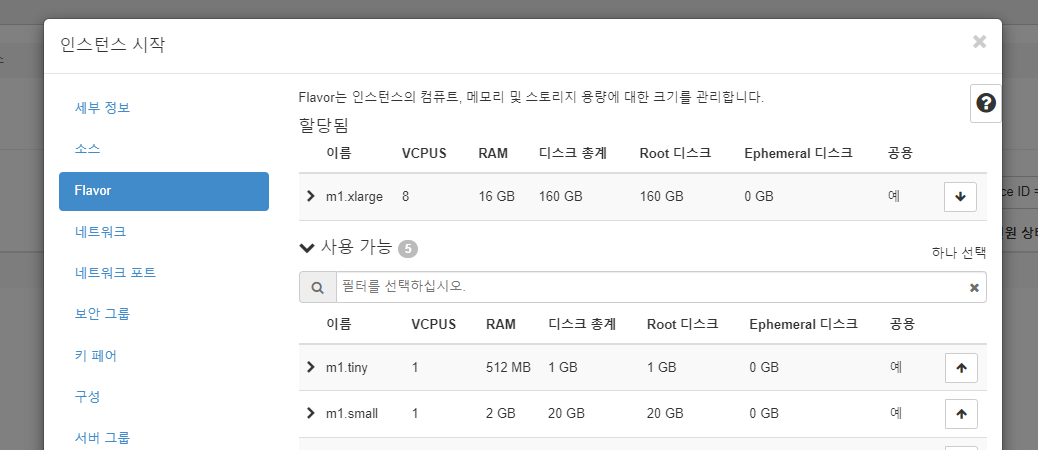
- flavor 생성
[root@localhost ~(keystone_admin)]# openstack flavor create \
> --id 6 \
> --vcpus 1 \
> --ram 1024 \
> --disk 20 \
> m1.xsmall
+----------------------------+-----------+
| Field | Value |
+----------------------------+-----------+
| OS-FLV-DISABLED:disabled | False |
| OS-FLV-EXT-DATA:ephemeral | 0 |
| disk | 20 |
| id | 6 |
| name | m1.xsmall |
| os-flavor-access:is_public | True |
| properties | |
| ram | 1024 |
| rxtx_factor | 1.0 |
| swap | |
| vcpus | 1 |
+----------------------------+-----------+- security group 생성
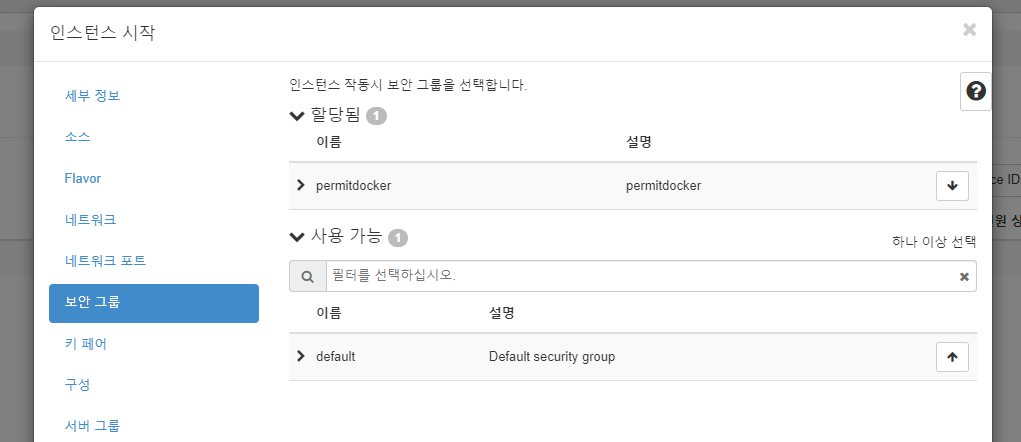
[root@localhost ~(keystone_admin)]# openstack security group create \
> permitdocker
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+
| created_at | 2022-09-19T01:30:43Z |
| description | permitdocker |
| id | dc95c109-f9e7-472a-b704-aaea85c7d9bd |
| name | permitdocker |
| project_id | 6633a1d2e5b5496ba6f210326bccc7f0 |
| revision_number | 2 |
| rules | created_at='2022-09-19T01:30:43Z', direction='egress', ethertype='IPv6', id='0b355c00-0581-4602-b1b8-89f9924e168e', updated_at='2022-09-19T01:30:43Z' |
| | created_at='2022-09-19T01:30:43Z', direction='egress', ethertype='IPv4', id='8d664868-460d-4234-ad72-17e7fef1ed65', updated_at='2022-09-19T01:30:43Z' |
| updated_at | 2022-09-19T01:30:43Z |
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+- rule 추가 (22 허용)
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 22 \
> permitdocker
+-------------------+--------------------------------------+
| Field | Value |
+-------------------+--------------------------------------+
| created_at | 2022-09-19T01:32:59Z |
| description | |
| direction | ingress |
| ether_type | IPv4 |
| id | 455f2808-f85d-4333-8f92-4b01cf6fbd4c |
| name | None |
| port_range_max | 22 |
| port_range_min | 22 |
| project_id | 6633a1d2e5b5496ba6f210326bccc7f0 |
| protocol | tcp |
| remote_group_id | None |
| remote_ip_prefix | 0.0.0.0/0 |
| revision_number | 0 |
| security_group_id | dc95c109-f9e7-472a-b704-aaea85c7d9bd |
| updated_at | 2022-09-19T01:32:59Z |
+-------------------+--------------------------------------+- rule 추가
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 80 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 443 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto icmp \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 2376 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 2377 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto tcp \
> --dst-port 7946 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto udp \
> --dst-port 7946 \
> permitdocker
[root@localhost ~(keystone_admin)]# openstack security group rule create \
> --proto udp \
> --dst-port 4789 \
> permitdocker
- 80/tcp
- 443/tcp
- icmp
- 2376/tcp
- 2377/tcp
- 7946/tcp
- 7946/udp
- 4789/udp
- 미리 만들어 놓은 도커 이미지 준비
-rw-r--r-- 1 root root 1172439040 Sep 19 10:46 ubuntu1804Docker.img- openstack 이미지 생성
[root@localhost ~(keystone_admin)]# openstack image create "docker" \
> --file ubuntu1804Docker.img \
> --disk-format qcow2 \
> --container-format bare \
> --public
+------------------+------------------------------------------------------+
| Field | Value |
+------------------+------------------------------------------------------+
| checksum | b7db1b205d7664fa1d3c22b37a145916 |
| container_format | bare |
| created_at | 2022-09-19T01:48:55Z |
| disk_format | qcow2 |
| file | /v2/images/ab42c709-212c-4464-9ba5-d40a66d91c20/file |
| id | ab42c709-212c-4464-9ba5-d40a66d91c20 |
| min_disk | 0 |
| min_ram | 0 |
| name | docker |
| owner | 6633a1d2e5b5496ba6f210326bccc7f0 |
| protected | False |
| schema | /v2/schemas/image |
| size | 1172439040 |
| status | active |
| tags | |
| updated_at | 2022-09-19T01:49:17Z |
| virtual_size | None |
| visibility | public |
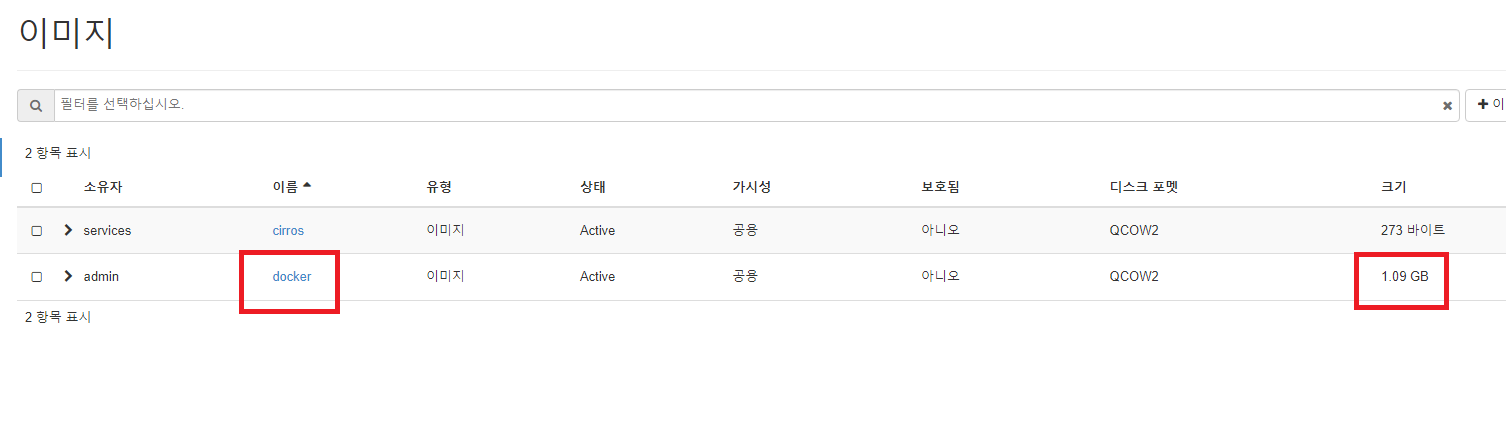
+------------------+------------------------------------------------------+- 이미지 확인
[root@localhost ~(keystone_admin)]# openstack image list
+--------------------------------------+--------+--------+
| ID | Name | Status |
+--------------------------------------+--------+--------+
| 6c5224fc-130b-49e6-a10f-a1c6d04c1e9b | cirros | active |
| ab42c709-212c-4464-9ba5-d40a66d91c20 | docker | active |
+--------------------------------------+--------+--------+docker active
manager, worker 볼륨 생성
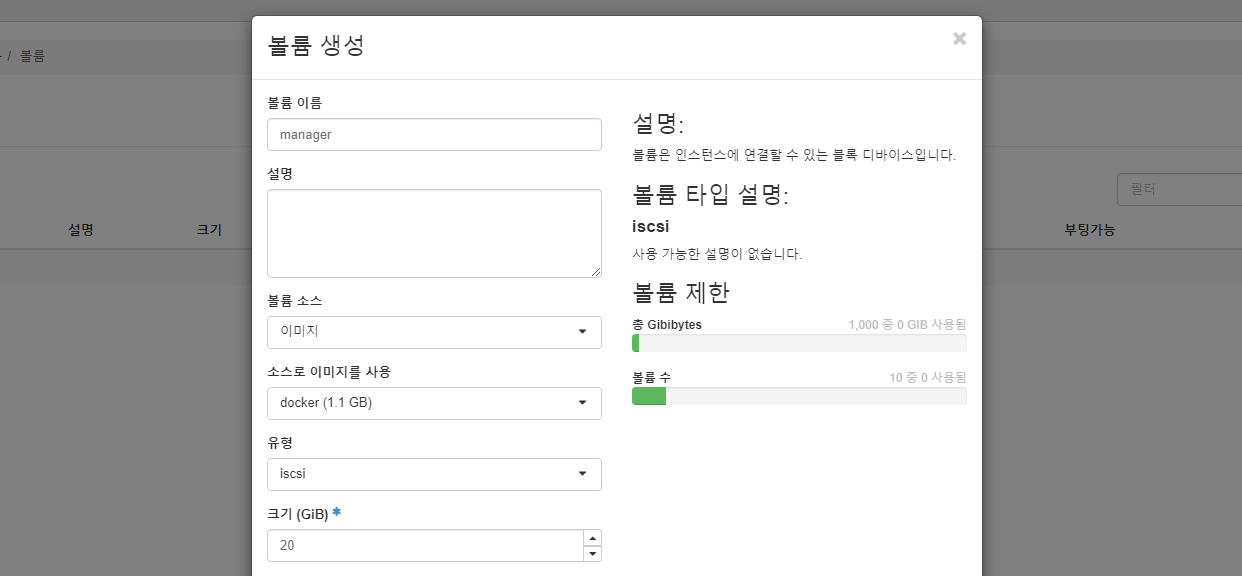
manager
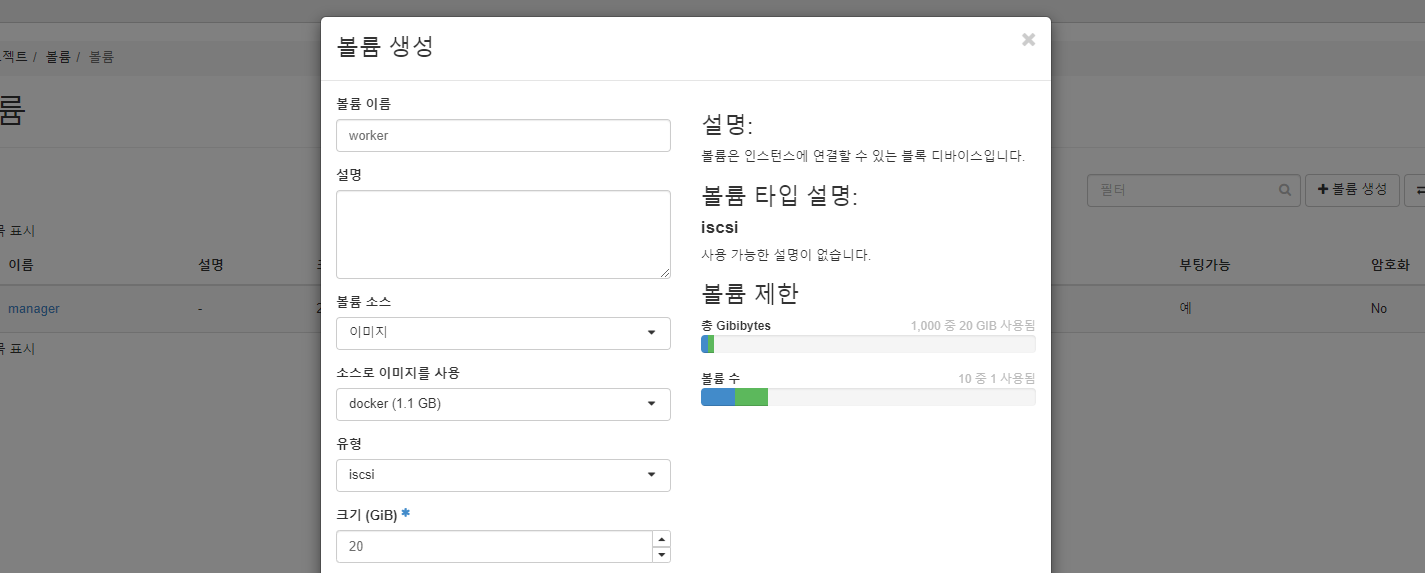
worker
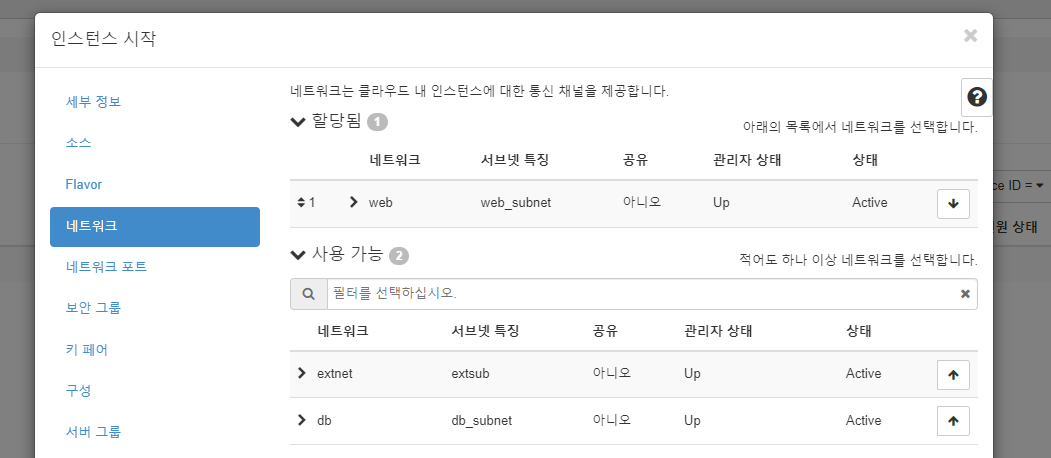
manager 인스턴스 생성
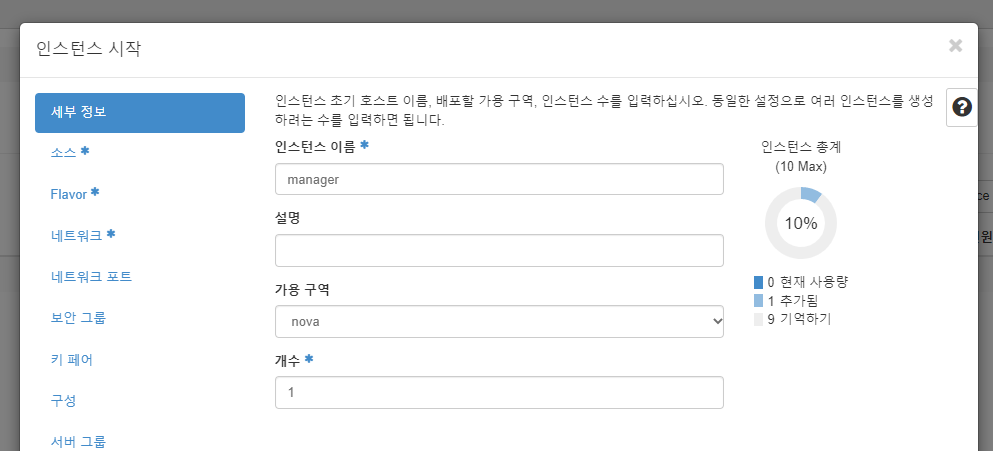
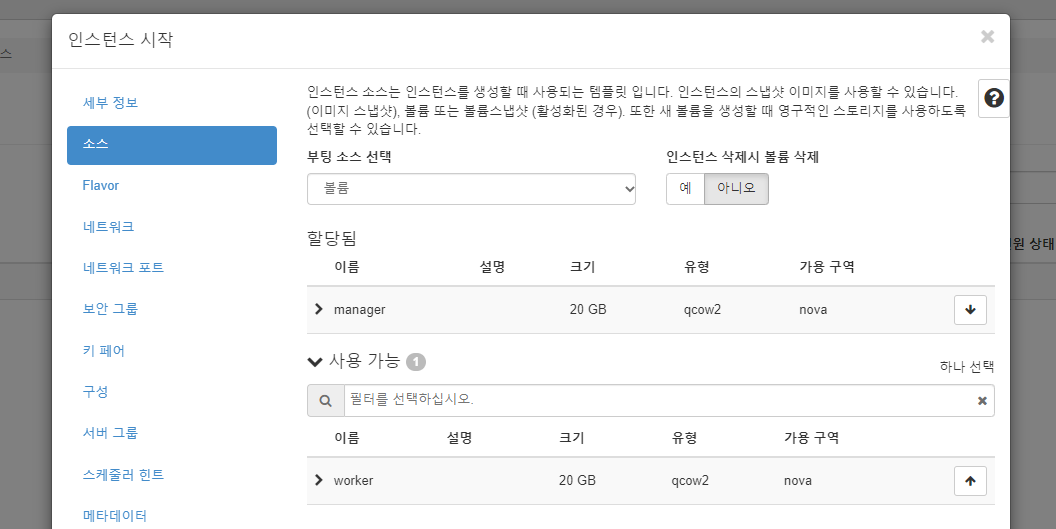
- 유동 ip 연결
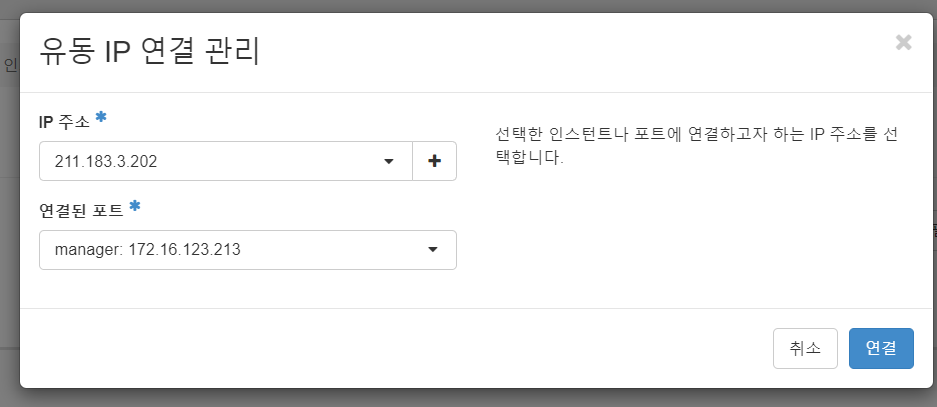
211.183.3.202
- ssh 연결 확인
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.202 'hostname'
The authenticity of host '211.183.3.202 (211.183.3.202)' can't be established.
ECDSA key fingerprint is SHA256:W9S7p5P9HR7KOe9snBrockQ2c72X2SoRdwY6nOvQWok.
ECDSA key fingerprint is MD5:cb:2f:cf:12:e1:00:07:aa:b0:fc:a1:e5:42:47:8c:b7.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '211.183.3.202' (ECDSA) to the list of known hosts.
managerworker 인스턴스 생성
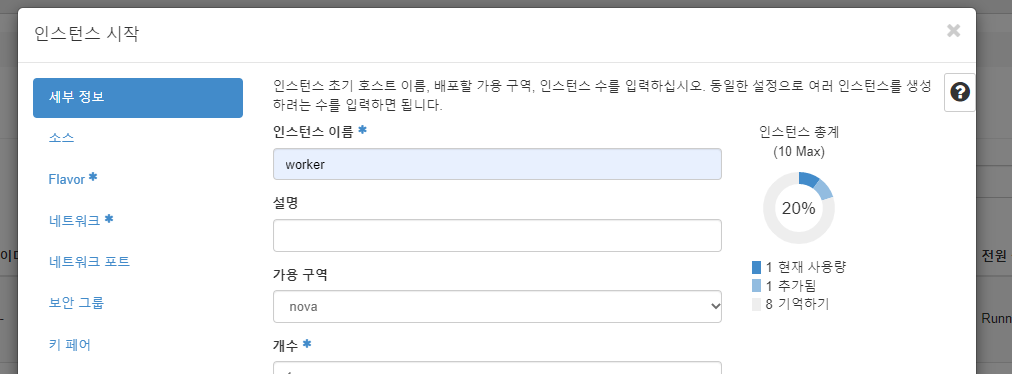
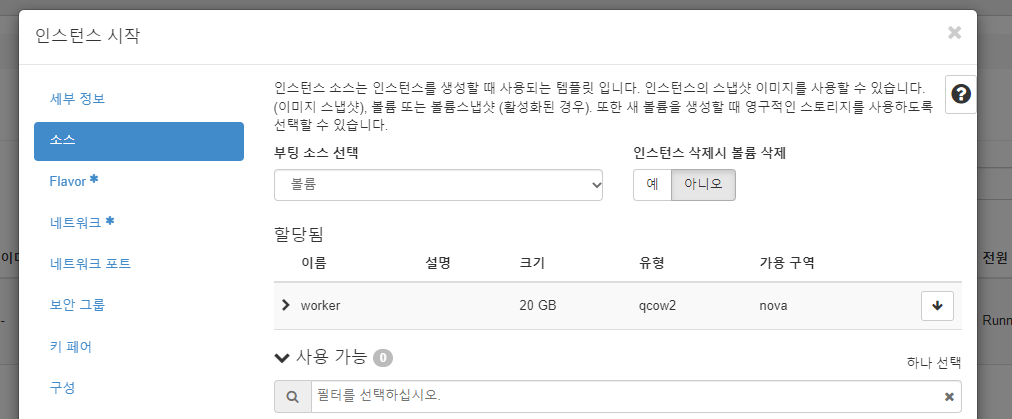
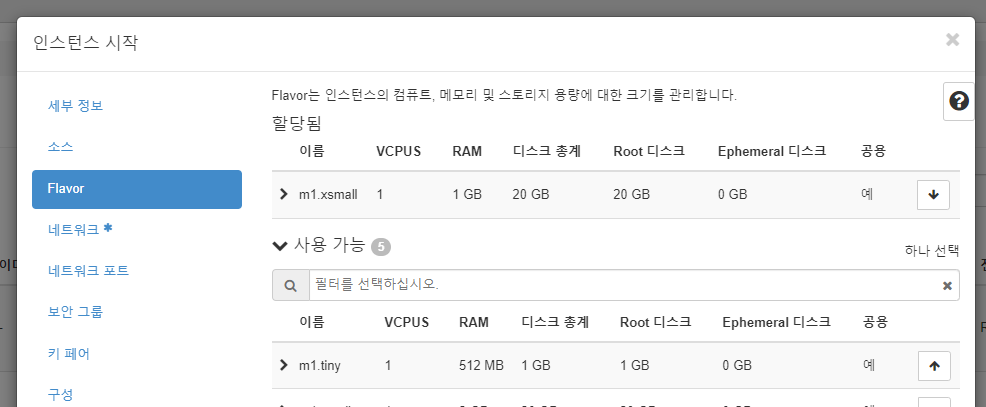
- 유동 ip 연결
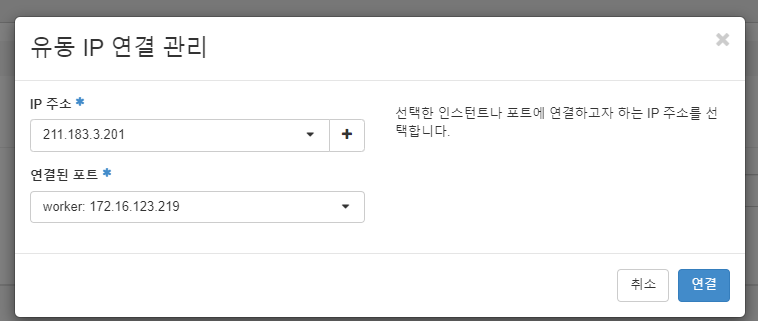
211.183.3.201
- known_hosts 등록
[root@localhost ~(keystone_admin)]# ssh-keyscan 211.183.3.201 >> /root/.ssh/known_hosts
# 211.183.3.201:22 SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.7
# 211.183.3.201:22 SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.7
# 211.183.3.201:22 SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.7- ssh 연결 확인
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.201 'hostname'
workerDocker Swarm 구성
- manager의 인터페이스 확인
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.202 'ip a | grep ens'
2: ens3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1450 qdisc fq_codel state UP group default qlen 1000
inet 172.16.123.213/24 brd 172.16.123.255 scope global dynamic ens3ens3
- advertise (manager 인스턴스, 211.183.3.202)
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.202 'sudo docker swarm init --advertise-addr ens3'
Swarm initialized: current node (esjkgeqr2ogqbwqpk4cdnsfwi) is now a manager.
To add a worker to this swarm, run the following command:
docker swarm join --token SWMTKN-1-25zwrqe4n7n7nl0huvzoxdorx3qzvffmcxwcpmzjnpa6xblsuv-6z0abx87b3fptcqijwjl6ie05 172.16.123.213:2377
To add a manager to this swarm, run 'docker swarm join-token manager' and follow the instructions.- join (worker 인스턴스, 211.183.3.201)
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.202 'sudo docker swarm init --advertise-addr ens3'
Swarm initialized: current node (esjkgeqr2ogqbwqpk4cdnsfwi) is now a manager.
To add a worker to this swarm, run the following command:
docker swarm join --token SWMTKN-1-25zwrqe4n7n7nl0huvzoxdorx3qzvffmcxwcpmzjnpa6xblsuv-6z0abx87b3fptcqijwjl6ie05 172.16.123.213:2377
To add a manager to this swarm, run 'docker swarm join-token manager' and follow the instructions.
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.201 'sudo docker swarm join --token SWMTKN-1-25zwrqe4n7n7nl0huvzoxdorx3qzvffmcxwcpmzjnpa6xblsuv-6z0abx87b3fptcqijwjl6ie05 172.16.123.213:2377'
This node joined a swarm as a worker.- swarm 클러스터 node 확인
[root@localhost ~(keystone_admin)]# ssh -i /root/.ssh/mykey.pem -l ubuntu 211.183.3.202 'sudo docker node ls'
ID HOSTNAME STATUS AVAILABILITY MANAGER STATUS ENGINE VERSION
esjkgeqr2ogqbwqpk4cdnsfwi * manager Ready Active Leader 20.10.18
kpwut4kq3v9yyjcjlsilsait0 worker Ready Active 20.10.18Object Storage
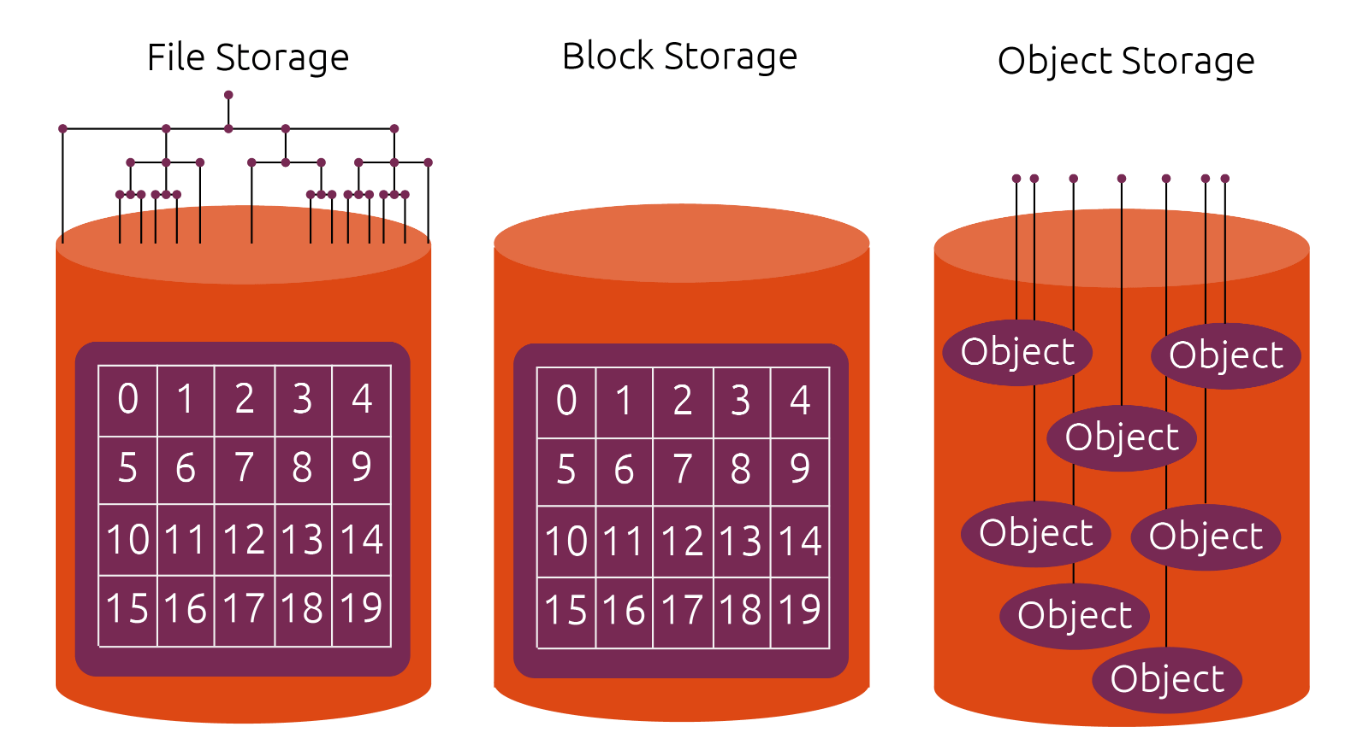
object storage는 서버의 위치와 상관 없이, 일종의 계정 별로 일정 저장 공간을 제공할 수 있다.
특정 서버에 연결을 위한 목적의 스토리지가 아니다.
openstack에서는 swift라고 부르며, aws에서는 s3라고 부른다.
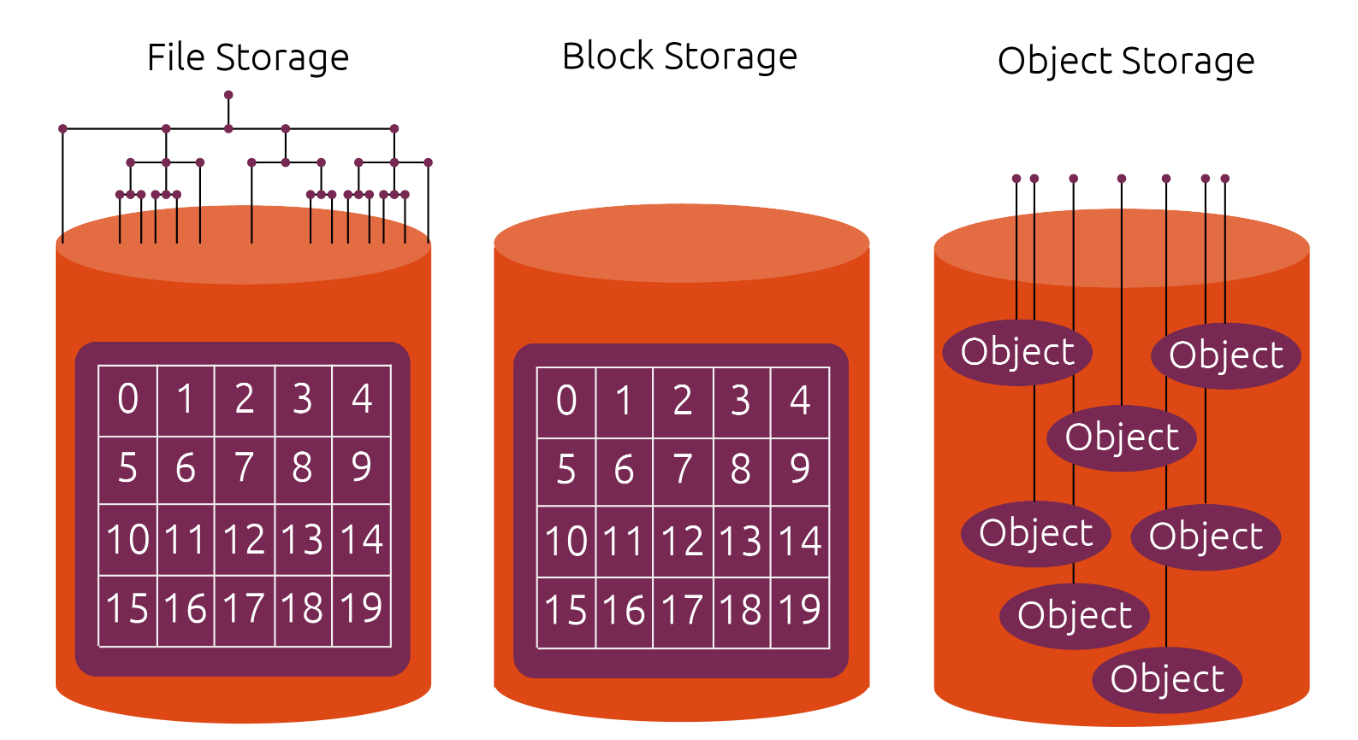
이미지 출처: https://ubuntu.com/blog/what-are-the-different-types-of-storage-block-object-and-file
file storage: tree
block storage: 번호로 공간을 관리
object storage: key value로 관리
container에 파일 및 폴더 업로드 (GUI)
- 컨테이너 생성
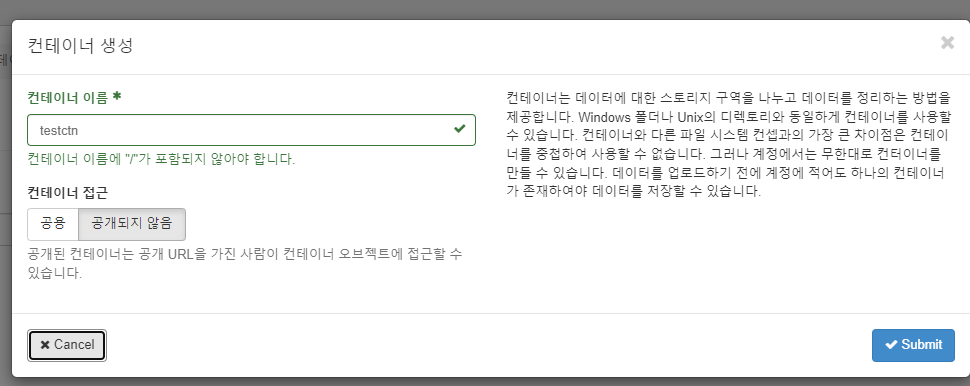
testctn
- 폴더 생성
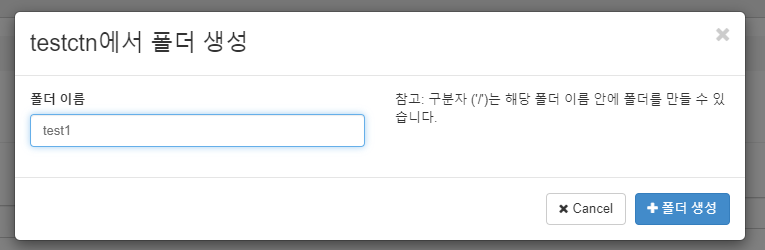
- 파일 업로드
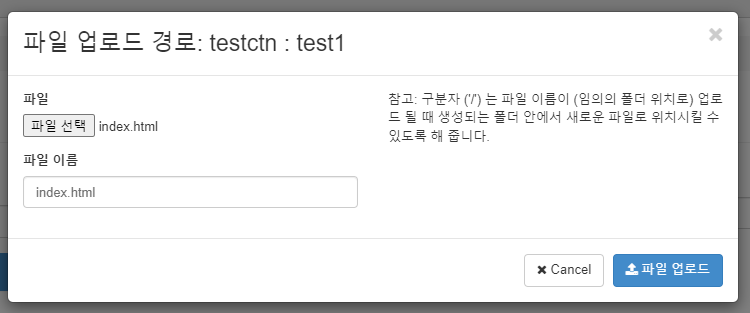
- 컨테이너 public으로 전환하기
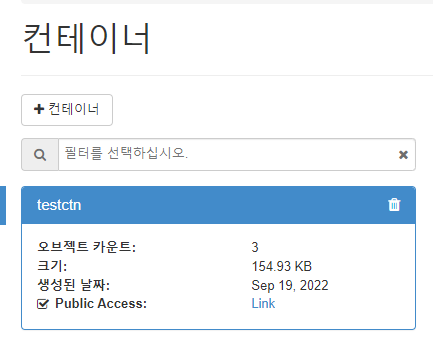
- public link 확인
<container name="testctn">
<object>
<name>test1/</name>
<hash>d41d8cd98f00b204e9800998ecf8427e</hash>
<bytes>0</bytes>
<content_type>application/octet-stream</content_type>
<last_modified>2022-09-19T03:20:49.291190</last_modified>
</object>
<object>
<name>test1/index.html</name>
<hash>6a537d292f7f17e053b6fb42947a8a2c</hash>
<bytes>116</bytes>
<content_type>text/html</content_type>
<last_modified>2022-09-19T03:23:37.902240</last_modified>
</object>
<object>
<name>test1/tabby-cat-with-wine-and-cheese.jpg</name>
<hash>8d8a369b2d7e563e546bb9e980ab8288</hash>
<bytes>158530</bytes>
<content_type>image/jpeg</content_type>
<last_modified>2022-09-19T03:21:39.941190</last_modified>
</object>
</container>- 파일 링크 접속
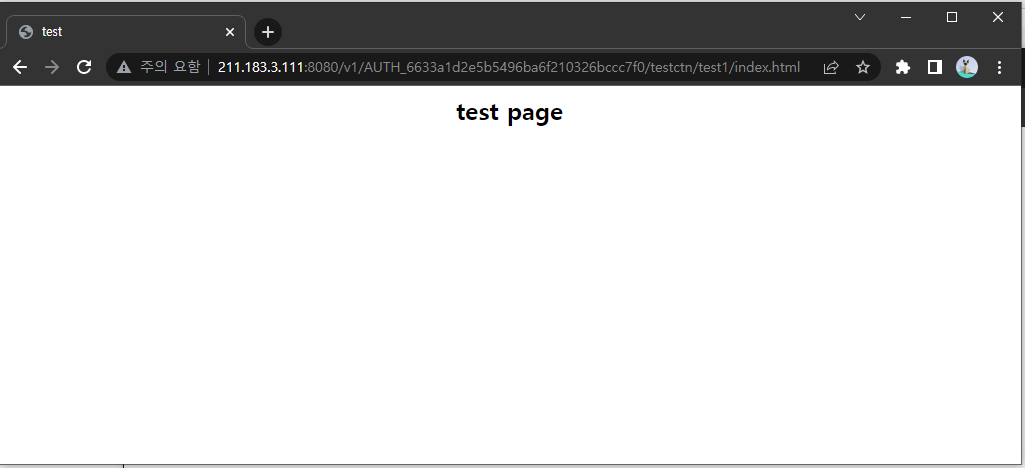
container에 파일 및 폴더 업로드 (CLI)
- 컨테이너 확인
[root@localhost ~(keystone_admin)]# openstack container list
+---------+
| Name |
+---------+
| testctn |
+---------+- www 컨테이너 생성
[root@localhost ~(keystone_admin)]# openstack container create www
+---------------------------------------+-----------+------------------------------------+
| account | container | x-trans-id |
+---------------------------------------+-----------+------------------------------------+
| AUTH_6633a1d2e5b5496ba6f210326bccc7f0 | www | tx723b821f57e74a47b6efc-006327e184 |
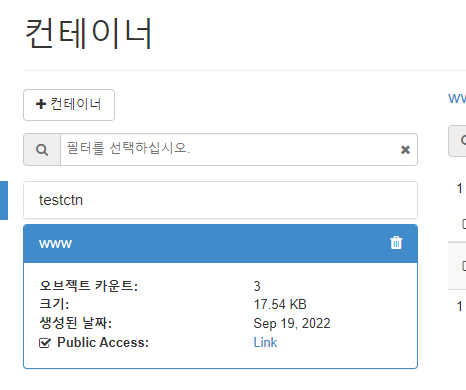
+---------------------------------------+-----------+------------------------------------+- www 컨테이너 확인
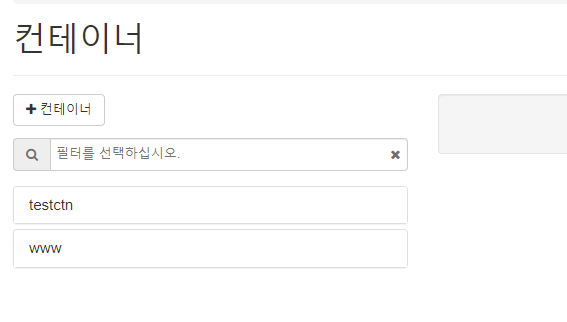
- bootstrap 다운로드
[root@localhost ~(keystone_admin)]# wget https://github.com/twbs/bootstrap/releases/download/v5.2.1/bootstrap-5.2.1-examples.zip
--2022-09-19 12:28:54-- https://github.com/twbs/bootstrap/releases/download/v5.2.1/bootstrap-5.2.1-examples.zip
Resolving github.com (github.com)... 20.200.245.247
Connecting to github.com (github.com)|20.200.245.247|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/2126244/5cf56db8-79cf-4313-b73f-501648d9923e?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220919%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220919T032825Z&X-Amz-Expires=300&X-Amz-Signature=57b043f46cb0381fb0567444989d5ad7cb4b56d86a575cafd2541183404ec02f&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=2126244&response-content-disposition=attachment%3B%20filename%3Dbootstrap-5.2.1-examples.zip&response-content-type=application%2Foctet-stream [following]
--2022-09-19 12:28:54-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/2126244/5cf56db8-79cf-4313-b73f-501648d9923e?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220919%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220919T032825Z&X-Amz-Expires=300&X-Amz-Signature=57b043f46cb0381fb0567444989d5ad7cb4b56d86a575cafd2541183404ec02f&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=2126244&response-content-disposition=attachment%3B%20filename%3Dbootstrap-5.2.1-examples.zip&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1321678 (1.3M) [application/octet-stream]
Saving to: ‘bootstrap-5.2.1-examples.zip’
100%[=====================================================================================================================================================================>] 1,321,678 --.-K/s in 0.02s
2022-09-19 12:28:54 (59.9 MB/s) - ‘bootstrap-5.2.1-examples.zip’ saved [1321678/1321678]- 압축 해제
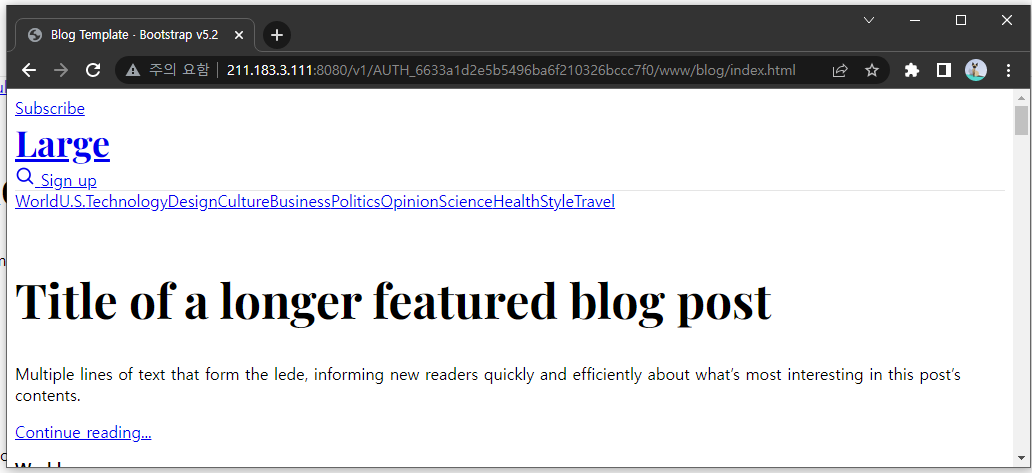
[root@localhost ~(keystone_admin)]# unzip bootstrap-5.2.1-examples.zip - www 컨테이너에 blog 폴더 업로드하기
[root@localhost bootstrap-5.2.1-examples(keystone_admin)]# swift upload www blog
blog/blog.css
blog/blog.rtl.css
blog/index.htmlswift upload www blog
- public 전환
- blog/index.html 접속