- X509 Client Certs
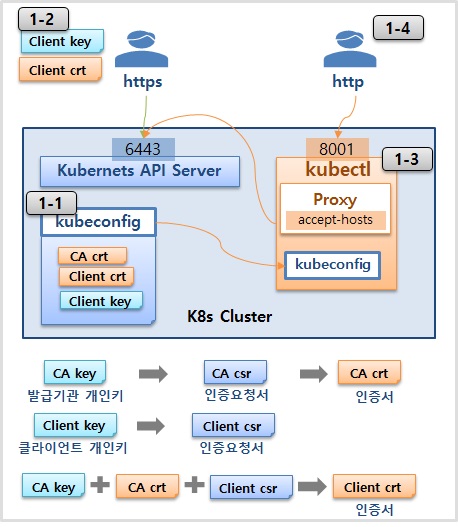
1-1) kubeconfig 인증서 확인
Path : /etc/kubernetes/admin.conf
cluster.certificate-authority-data : CA.crt (Base64)
user.client-certificate-data: Client.crt (Base64)
user.client-key-data: Client.key (Base64)
grep 'client-certificate-data'
/etc/kubernetes/admin.conf | head -n 1 | awk '{print $2}' | base64 -d
grep 'client-key-data' /etc/kubernetes/admin.conf | head -n 1 | awk '{print $2}' | base64
- kubectl
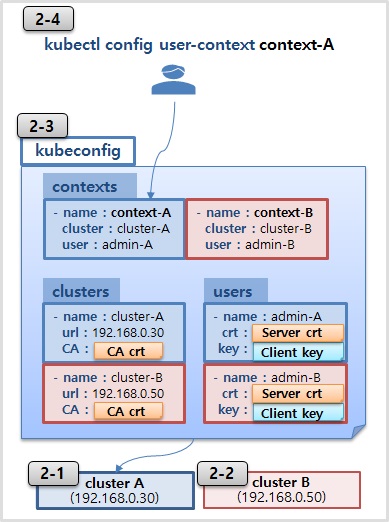
2-1) Cluster A kubeconfig
path : /etc/kubernetes/admin.conf
2-2) Cluster B kubeconfig
path : /etc/kubernetes/admin.conf
2-3) kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1KVEUtLS0tLQo=
server: https://192.168.0.30:6443
name: cluster-a
- cluster:
certificate-authority-data: LS0tLS1KVEUtLS0tLQo=
server: https://192.168.0.50:6443
name: cluster-b
contexts:
- context:
cluster: cluster-a
user: admin-a
name: context-a
- context:
cluster: cluster-b
user: admin-b
name: context-b
current-context: context-a
kind: Config
preferences: {}
users:
- name: admin-a
user:
client-certificate-data: LS0tLS1KVEUtLS0tLQo=
client-key-data: LS0tLS1KVEUtLS0tLQo=
- name: admin-b
user:
client-certificate-data: LS0tLS1KVEUtLS0tLQo=
client-key-data: LS0tLS1KVEUtLS0tLQo=- Service Account
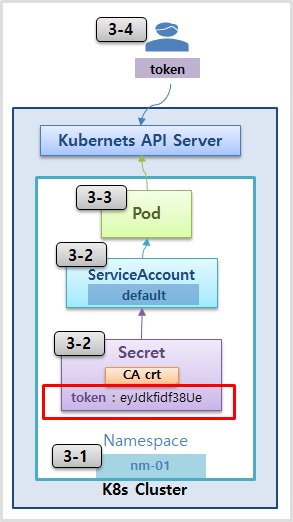
3-1) Namespace
kubectl create ns nm-01
3-2) ServiceAccount & Secret 확인
kubectl describe -n nm-01 serviceaccounts
kubectl describe -n nm-01 secrets
3-3) Pod
cat <<EOF | kubectl create -f -
apiVersion: v1
kind: Pod
metadata:
name: pod-1
namespace: nm-01
labels:
app: pod
spec:
containers:
- name: container
image: kubetm/app
EOF