https://tryhackme.com/room/burpsuiterepeater
Burp Suite: Intruder
Task 1 Room Outline
Intruder allows us to automate requests, which is very useful when fuzzing or brute forcing.
Task 2 what is Intruder?
It allows us to take a request and use it as a template to send many more requests with slightly altered values automatically. For example, by capturing a request containing a login attempt, we could then configure Intruder to swap out the username and password fields for values form a wordlist -> bruteforce the login form.
One problem: to access the full speed of Intruder, we need Burp Professional. This speed restriction means that many hackers choose to use other tools for brutefocing (like Wfuzz, Ffuf)
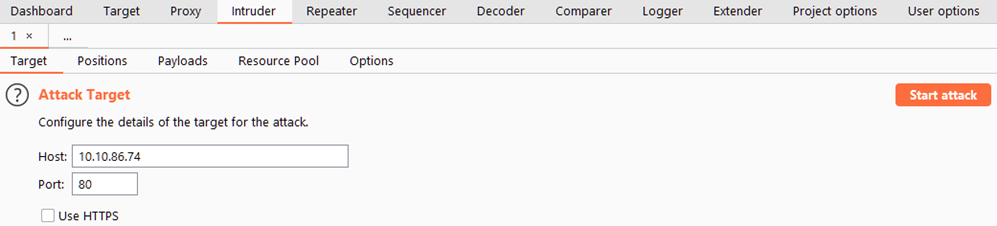
- Positions: allows us to select an Attack Type, as well as configure where in the request template we wish to insert our payloads.
- Payloads: allows us to select values to insert into each of the positions we defined in the previous sub-tab.
- Resource Pool: not particularly useful to us in Burp Community.
Task 3 Positions
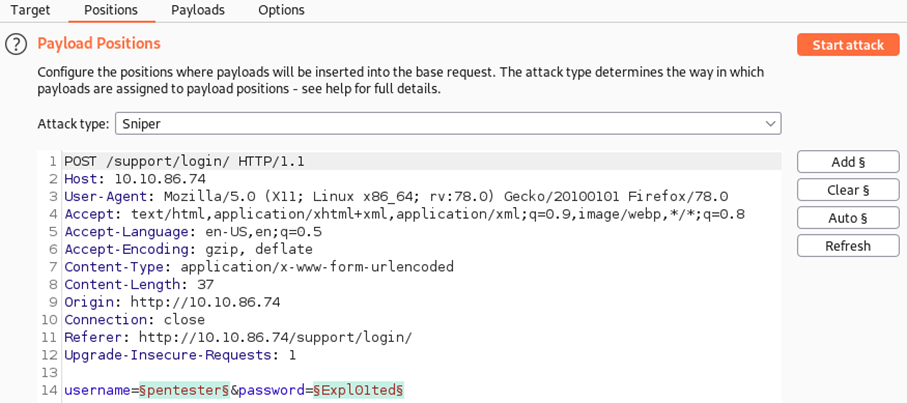
- Add: lets us define new positions by highlighting them in the editor and clicking the button
- Clear: removes all defined positions
- Auto: attempts to select the most likely positions automatically; useful if we cleared the default positions and want them back
Task 5 Sniper
It is the first and most common attack type.
When conducting a sniper attack, we provide one set of payloads. For example, this could be a single file containing a wordlist or a range of numbers.
Task 6 Battering Ram
Battering ram puts the same payload in every position rather than in each position in turn.
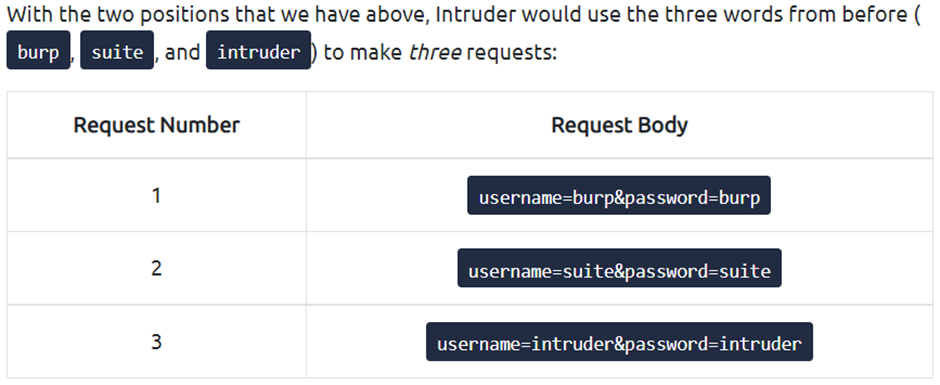
Task 7 Pitchfork
After Sniper, Pitchfork is the attack type you are most likely to use. It may help to think of Pitchfork as being like having numerous Snipers running simultaneously. It uses one payload set per position and iterates(반복하다) through them all at once.
Task 8 Cluster Bomb
Cluster bomb allows us to choose multiple payload sets: one per position, up to a maximum of 20; iterates through each payload set individually making sure that every possible combination of payloads is tested.
For example, we have three users and three passwords, but we don’t know how to match them up. In this case, we would use a cluster bomb attack.
Task 9 Payloads
“Payloads” sub-tab is split into four sections.
- Payload Sets: allows us to choose which position we want to configure a set for as well as type of payload we would like to use. The second dropdown in this section allows us to select a “payload type”.
- Payload Options: differ depending on the payload type we select for the current payload set.
- Payload Processing: allows us to define rules to applied to each payload in the set before being sent to the target.
- Payload Encoding: allows us to override the default URL encoding options that are applied automatically to allow for the safe transmission of our payload. ‘
Task 10 Example
This test portal login page has no protective measures in place: It means that we could very easily attack this form using a cluster bomb attack for a bruteforce.
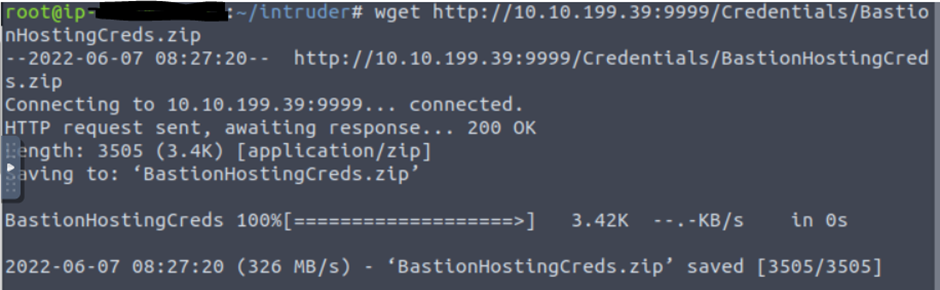
But they give us a list of leaked credentials for Bastion Hosting employees. We can avoid a straight bruteforce and instead use a credential stuffing attack.
Unzip the file.
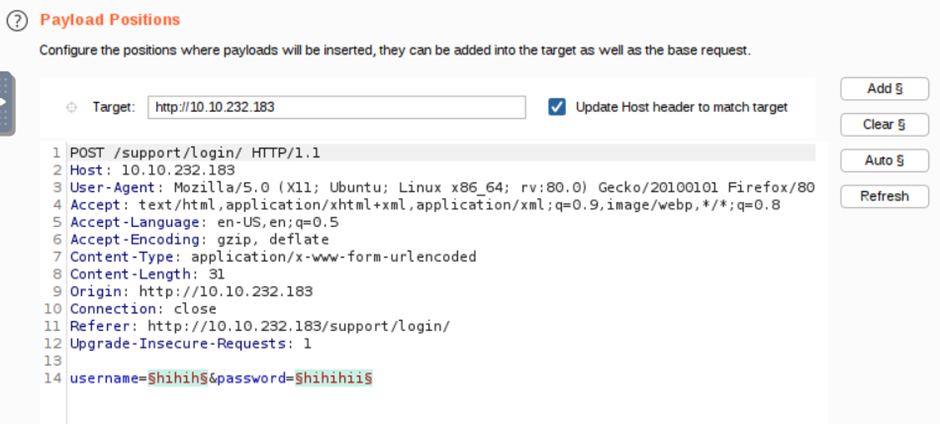
Activate the Burp Proxy and try to log in, catching the request in your proxy. Send to Intruder.
Then change the Attack type to be “Pitchfork”
In the first payload set, go to payload options and choose load then select usernames list. Do the same thing for the second payload set and the list of passwords. And then start to attack
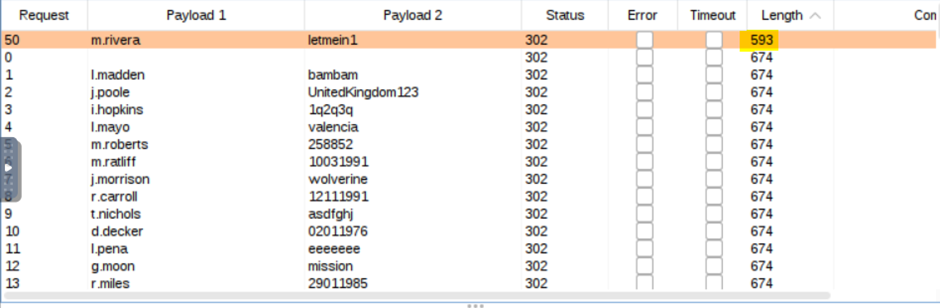
we can sort our results, one request should stand out as being different.
Task 11 Challenge
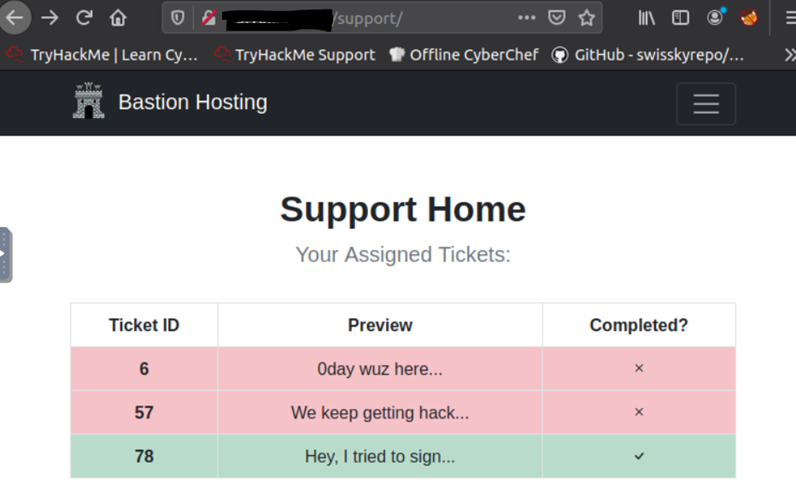
After login, we can see the support home page.
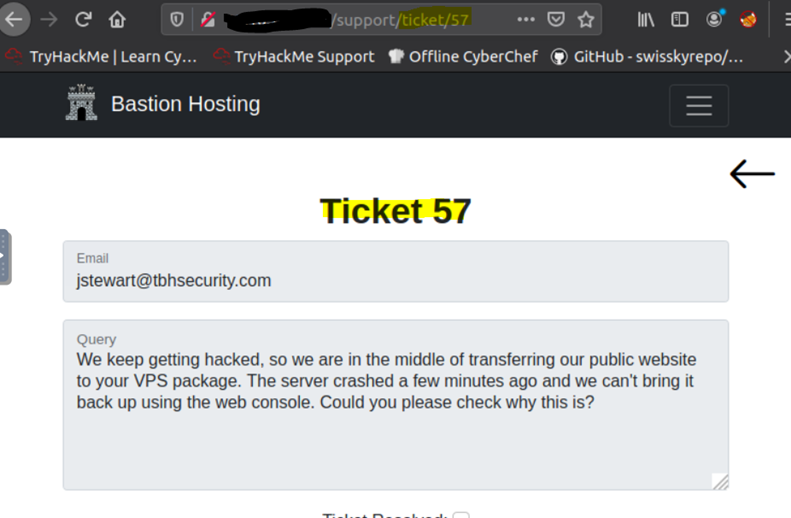
The home interface shows us a table of tickets. If we click on any of the rows in the table, we get redirected to a page. And these pages are numbered like ~support/ticket/NUMBER
The endpoint has not had the correct access set, which would allow us to read all of the tickets. This vulnerability called IDOR(Insecure Direct Object References)
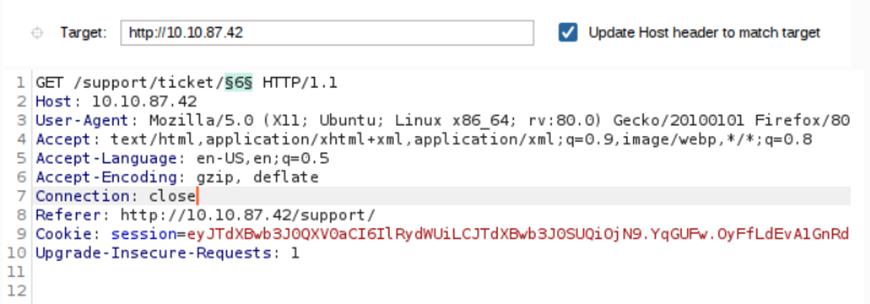
We will change the number value.
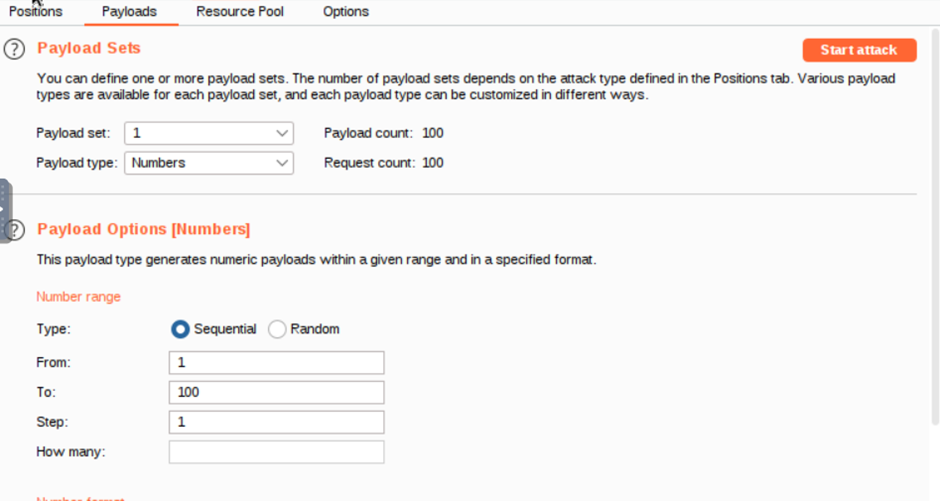
Payload type is numbers. The number range is from 1 to 100. And step is 1.
Setting like these and then start the attack.
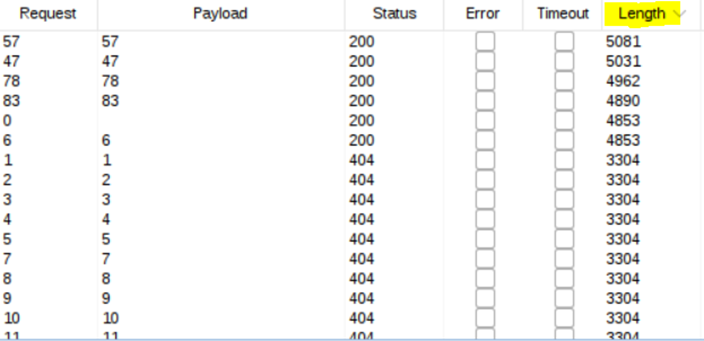
6, 57, 78 are tickets that we have.
So look for other numbers.
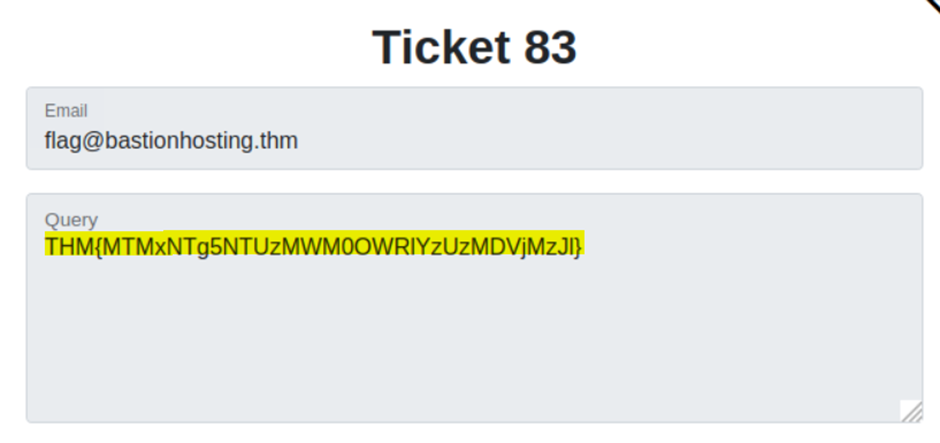
Find it~

