Burp Suite: Other Modules
https://tryhackme.com/room/burpsuiteom
Task 1 Outline
Decoder, Comparer, and Sequencer tools allow us to work with encoded text; compare sets of text’ and analyse the randomness of captured tokens.
Task 2 Decoder Overview
The Burp Decoder module allows us to manipulate data. We can decode information that we capture during an attack, but we can also encode data of our own, ready to be sent to the target. And also allows us to create hashsums of data as well as providing a Smart Decode feature which attempts to decode provided data recursively until it is back to being plaintext.
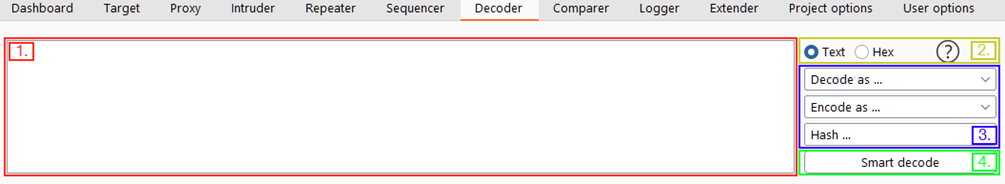
- Where we would paste or type text to be encoded or decoded. we can also send data by right-clicking and choosing Sent to Decoder.
- the option to select between treating the input as text or hexadecimal byte values.
- dropdown menus to Encode, Decode or Hash the input.
- decode the input automatically.
Task 3 Decoder Encoding/Decoding
Let’s take a closer look at manual encoding and decoding options.
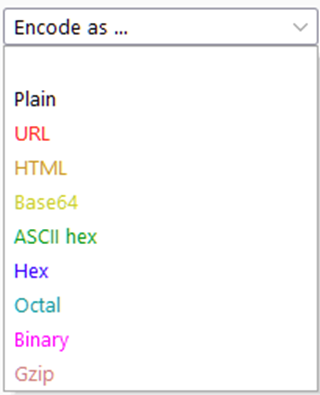
- Plain: what we have before performing any transformations
- URL: It is used to make data safe to transfer in the URL of a web request. It involves exchanging characters for their ASCII character code in hexadecimal format, proceeded by a percentage symbol. It is useful to know for any kind of web application testing.
- HTML: Encoding text as HTML Entities involves replacing special characters with an ampersand(&) followed by either a hexadecimal number or a reference to the character being escaped, then a semicolon.
- Base64: base64 is used to encode any data in an ASCII-compatible format.
- ASCII Hex: This option converts data between ASCII representation and hexadecimal representations
- Hex, Octal, and Binary: These methods all apply only to numeric inputs.
- Gzip: Gzip provides a way to compress data. It is widely used to reduce the size of tiles and pages before they are sent to your browser.
Task 4 Decoder Hashing
Decoder also gives us the option to generate hashsums for out entered data.
To be a hasing algorithm, the resulting output must be impossible to reserve. A good hashing algorithm will ensure that every piece of data entered will have a completely unique hash. For this reason, hashes are frequently used to verify the integrity of files and documents as even a very small change to the file will result in the hashsum changing significantly.
Hashed are also used to securely store passwords as the passwords will be secure even if the database is leaked.
하다보니 해싱과 인코딩의 차이가 헷갈려서 본 글: https://brunch.co.kr/@sangjinkang/32
암호화: 민감한 정보를 외부 노출로부터 보호
해싱: 무결성 확인. 내가 받은 정보가 걔가 보낸 그대로가 맞나?
Task 5 Comparer Overview
Comparer allows us to compare two pieces of data, either by ASCII words or by bytes.
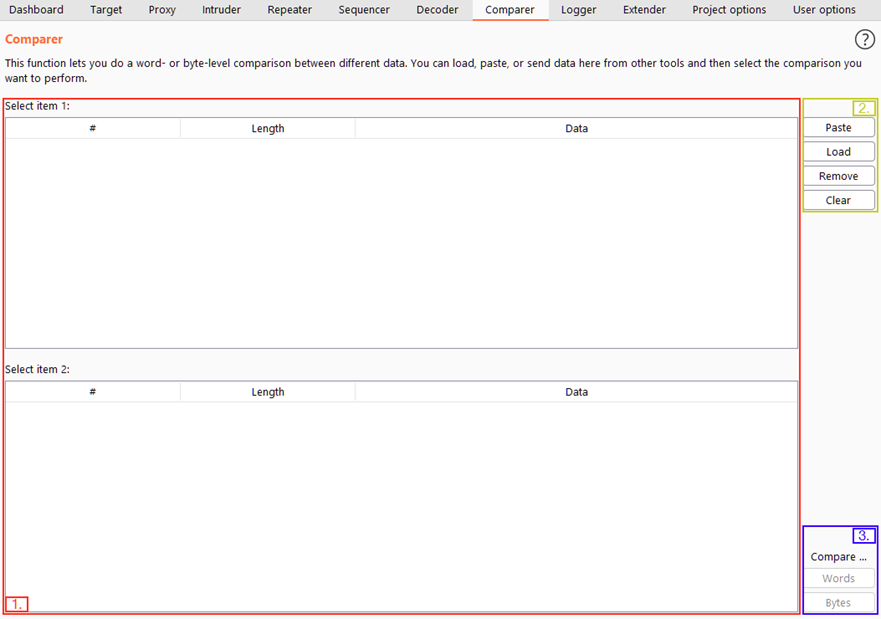
- The items being compared. When we load data into Comparer, it will appear as rows in these tables.
- options for Paste, Load, Remove, Clear all datasets.
- the option to compare our datasets by either words or bytes.
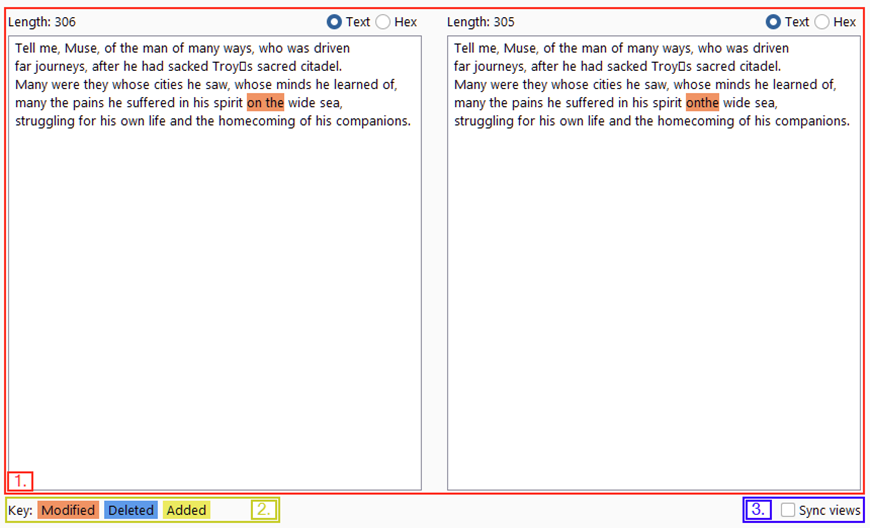
When we have loaded data in to compare, we get a pop-up window showing us he comparison.
- this can be viewed in either text or hex format.
- this shows which colours denote(나타내다) modified, deleted, and added data between the two datasets.
- When this checkbox is selected, this means that both sets of data will sync formats. i.e. if you change one of them into Hex view, the other will do the same to match.
Task 6 Comparer Example
There are many situations where being able to quickly compare two pieces of data can come in handy.
For example, when performing a login bruteforce or credential stuffing attack with Intruder, you may wish to compare two responses with different lengths to see where the differences lie and whether the differences indicate a successful login.
크리덴셜 스터핑&브루트포스
- 크리덴셜스터핑: 수집된 사용자 이름과 비밀번호를 자동으로 대입하며 사용자 계정에 부정하게 액세스 하려는 공격
- 일종의 브루트포스 공격이지만, 사전을 이용해 추측하는게 아닌 데이터 침해에서 입수한 유효 정보를 이용한다는 점이 차이점임!!!!!!!
- https://www.itworld.co.kr/howto/135422 : 헷갈려서

