IDOR
Task 1 What is an IDOR?
IDOR: Insecure Direct Object Reference. Type of access control vulnerability.
Task 2 An IDOR Example
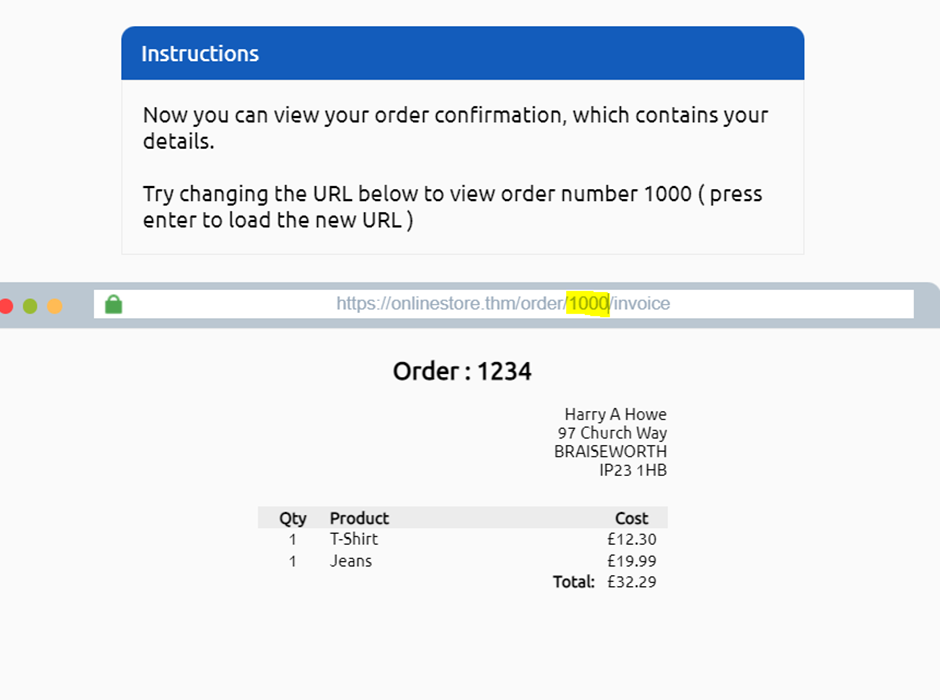
Change the number 1234 -> 1000
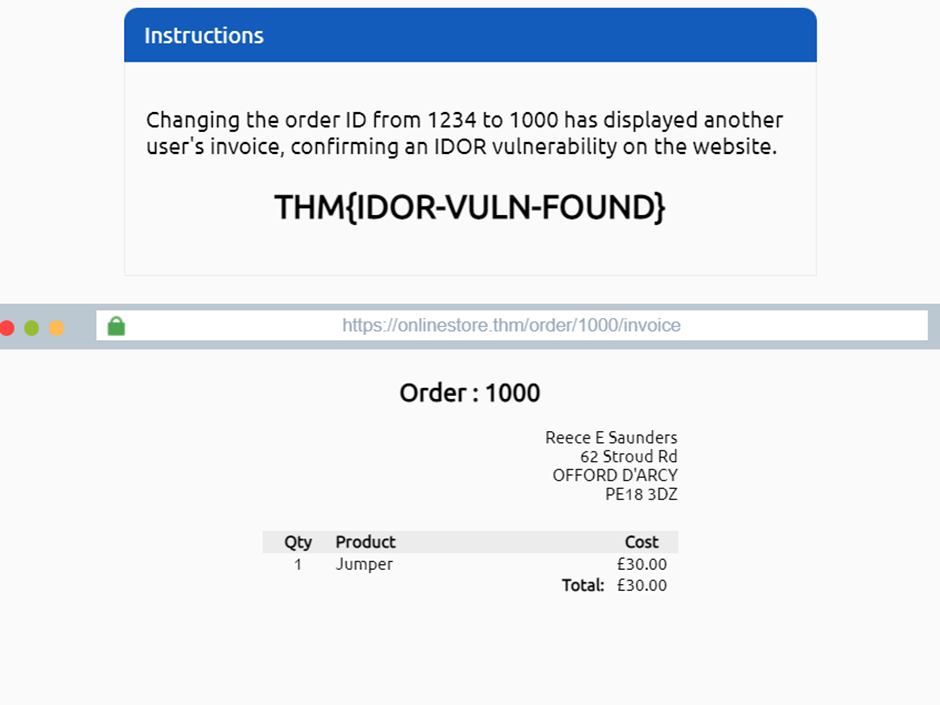
Then the page has displayed another user(1000)’s invoice. And also I can see the flag.’
Task 3 Finding IDORs in Encoded IDs
When passing data from page to page either by post data, query strings, or cookies, web developers will often first take the raw data and encode it. Encoding changes binary data into an ASCII string. The most common encoding technique on the web is base64 encoding.
https://www.base64encode.org/
Task4 Finding IDORs in Hashed IDs
Hashed IDs are a little bit more complicated to deal with than encoded ones.
https://crackstation.net/
Task 5 Finding IDORs in Unpredictable IDs
If the Id cannot be detected using the above methods, an excellent method of IDOR detection is to create two accounts and swap the Id numbers between them.
Task 6 Where are IDORs located
The vulnerable endpoint you’re targeting may not always be something you see is the address bar. It could be content your browser loads in via an AJAX request or something that you find referenced in a JavaScript file.
Task 7 A Practical IDOR Example
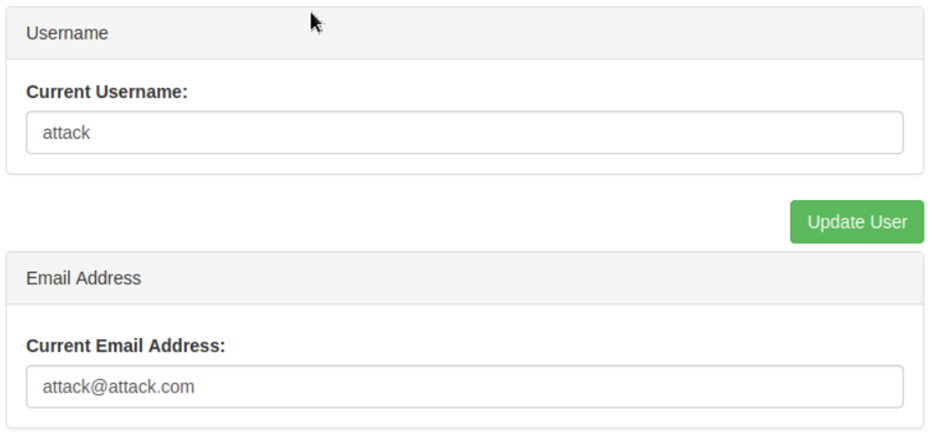
Firstly, create an account and click on the your Account tab. We can notice the username and email fields pre-filled in with my information.
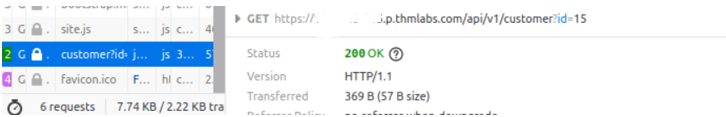
Open the browser developer tools, select the network tab and then refresh the page, we can see a call to an endpoint with the path /api/v1/customer?id={user_id}
This page returns in JSON format my user id, username and email address. We can see from the path that the user information shown is taken from the query string’s id parameter.
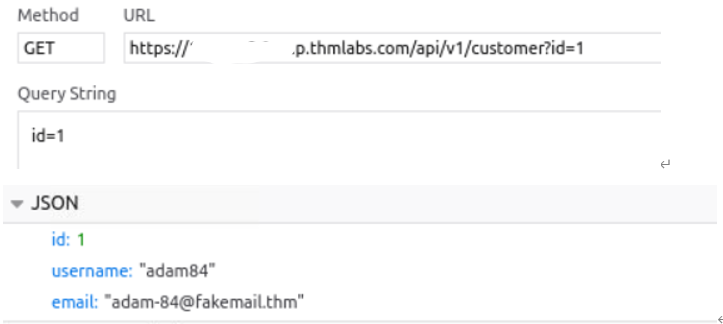
By changing the id to another user’s id, I test an IDOR vulnerability.

