VPC Peering
Connecting 2 VPC networks
- Cross region
- Cross account
- No overlapping CIDR ranges for connected VPCs AT ALL
Configuration
2 VPCs will have different fuctions, one as a requestor and one as an acceptor.
Establish the VPC peering connection from the acceptor VPC and add route table entries in both VPCs.
Cons
- VPC peering does not scale very well because it requires a mesh for connections
Configure with Console
- Create two separate VPCs as requestor and acceptor

- Click on Peering connections on the VPC console, left nav bar
- Create Peering Connection
- Select corresponding VPCs for requestor and acceptor (there's no cost for this connection, but the traffic could incur charges)
- Create connection and click Actions -> Accept Request
- Check on Peering Connection tab to check active connections
- Go to Route Tables
- Let's say we want to connect two private subnets
- Click on Routes for the private requestor subnet
- Add a route, in this case,
10.1.0.0/16, Target = Peering Connection, save changes - This allows traffic from one direction
- Follow the same steps for acceptor as well
Configure with CLI
Required commands
Note that all lines with $ is a single line command, spaced for legibility
$ aws ec2 create-vpc-peering-connection
--vpc-id VPC_ID_OF_YOUR_VPC_REQUESTOR
--peer-vpc-id VPC_ID_OF_YOUR_VPC_ACCEPTOR
--region YOUR_REGION
Naviagte to the VPC dashboard and
copy the peering connection ID for "Pending acceptance"
OR copy the peering connection ID from the response JSON
$ aws ec2 accept-vpc-peering-connection
--vpc-peering-connection-id COPIED_ID_FROM_ABOVE
--region YOUR_REGION
$ aws ec2 create-route
--route-table-id ROUTE_TABLE_ID_FOR_VPC_REQUESTOR_PRIVATE
--destination-cidr-block YOUR_CIDR (10.1.0.0/16 for this example)
--vpc-peering-connection-id PEERING_CONNECTION_ID_COPIED_ABOVE
$ aws ec2 create-route
--route-table-id ROUTE_TABLE_ID_FOR_VPC_ACCEPTOR_PRIVATE
--destination-cidr-block YOUR_CIDR (10.0.0.0/16 for this example)
--vpc-peering-connection-id PEERING_CONNECTION_ID_COPIED_ABOVE- The response of the 1st command will be a JSON object that describes the connection
- Response JSON will have
Statuschange.
Transit Gateway
Stand-alone region scoped resource that can be connected to other networks
- It can be connected to multiple VPCs or on-prem resources
- The connection must be specified in the route table
- It scales much better than VPC peering
Deploy a Transit Gateway
- Go to VPC dashboard left nav bar,
Transit Gateway - These incur charges
- Create Transit Gateway with default settings
- Create Transit Gateway Attachments for acceptor and requestor
- Select tgw, VPC, DNS
- It will create attachments for each subnet
- Go to private route tables for subnets for accptor and requestor to add the route destinations
Route 53
Global scoped TCP and UDP port that is dedicated to DNS
- It has all traditional DNS features
- Perfect fit for cloud-native applications
- Features consist, DNS registrar, creating DNS zones, health checks
- Resolver endpoints, firewalls, rules to restrict or forward DNS requests
Features
Contrary to traditional DNS, Route 53 offers
Weighted Routing: modify the amount of traffic reacing each endpoints, set weight to zero for maintainance
Latency-based Routing: depending on the region of request, DNS response is determined by lowest latency from client
Failover Routing: set primary and secondary DNS, and if there's an issue with primary, pass to secondary
Geolocation Routing: determined by physical location of client, more static than latency routing
Alias Records: Point a DNS name to an AWS service
Configure Resilience Features on Route 53 with Console
- Go to Route 53
- Create Health Check
- Input name and select
Endpointfor monitoring - Protocol: HTTPS, domain name: aws.amazon.com, Port: 443
- Under Advanced config, add
latency graphs - Create health check
Create DNS private hosted zone
- Go to Hosted zones
- Create hosted zone
- Type: private hosted zone
- Select the corresponding region and VPC
- Hosted zones are Cost Incurring
Create failover record
This requires endpoints
Connect to aws CLI and create a script file
create_eips.sh
REGION1=$1
REGION2=$2
aws ec2 allocate-address --domain vpc
--tag-specifications 'ResourceType=elastic-ip, Tags=[{Key=route53demo, Value=true}]'
--region $REGION1 --output text --query [PublicIp, NetworkBorderGroup]
aws ec2 allocate-address --domain vpc
--tag-specifications 'ResourceType=elastic-ip, Tags=[{Key=route53demo, Value=true}]'
--region $REGION2 --output text --query [PublicIp, NetworkBorderGroup]Run the script
$ bash ./create_eips.sh YOUR_REGION1 YOUR_REGION2
- Go to Hosted zones, click on create records
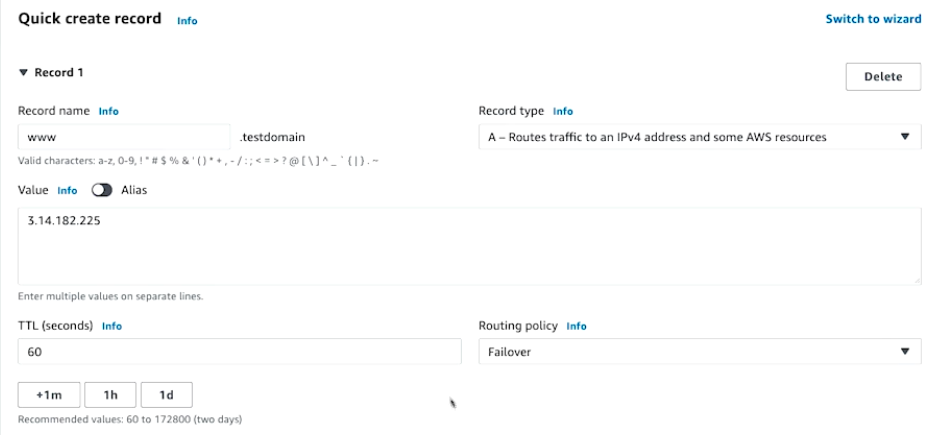
- The IP provided in
Valuewill become your primary IP - Failover record type: primary, and select healthcheck and Record ID (more like record name)
- Add the same for secondary IP
Disclaimer
This summary is made possible by Oreilly's AWS, 3rd Edition - Chad Smith.
If the above post violates any copyright permissions, please let me know!

