VPC (Virtual Private Cloud)
What is a VPC?
The VPC network itself is region scoped
VPC is used for almost everything that has a scope of AZ (Availabilty Zones)
First thing to setup is the CIDR address.
- An individual VPC also supports up to 5 CIDR ranges as long as they're within the same base range. So, if you create a new VPC network and assign
10.0.0.0/16to it, any other CIDR ranges that you apply also need to start with 10. You cannot apply a172.16.0.0or a192.168.0.0 - The largest CIDR range is 16 (65,536 IPs) and the smallest is 28 (16 IPs)
- By default, AWS reserves 5 IP addresses per subnet
Subnets
A contiguous range of addresses within a VPC
They are AZ scoped and usually much smaller than the VPC size. However, they have the ability to be scoped at the local zone layer, which makes it possible to target data centers that are geographically closer to you.
Each subnet can be associated with a Route Table and a network ACL (Access Control List).
Subnet Types
Since subnets are technically identical other than the CIDR range, we can differentiate their purpose by their accessibility.
Public
A public subnet has a route table attached that has bi-directional access to the internet through IGWs.
Private Subnet
A private subnet has outbound access but no direct inbound access, usually controlled by a NAT gateway.
Create Custom VPC and Subnets
Create a default VPC only option.
Give IPv4 CIDR.
Enable DNS hostnames.
Create VPC
Now create subnets.
To optimize for reduced latency, cost optimization and simplified networking, locate subnets in the same AZ
-
Reduced Latency: Keeping subnets within the same Availability Zone minimizes the network latency between resources within the subnets. This can be beneficial for applications that require low-latency communication between components, such as a database server and an application server.
-
Simplified Networking: Placing subnets in the same Availability Zone simplifies network configuration and management. You don't have to deal with cross-Availability Zone routing or worry about configuring and maintaining VPC peering or VPN connections between subnets in different Availability Zones.
-
Cost Optimization: AWS does not charge for data transfer between resources within the same Availability Zone.
Apply names and CIDR range.
Example,
public - 10.100.1.0/24
private - 10.100.2.0/24
database - 10.100.3.0/24Networks
Route Table
Associated with one or more subnets to sepcify a network that is not the local subnet to provide a gateway.
Basic approach is to attach one route table per subnet instead of route table for all, to avoid confusing route table.
Internet Gateway
Attach to a VPC to provide public internet access to the AWS services.
You still require a route table entry in the public subnet.
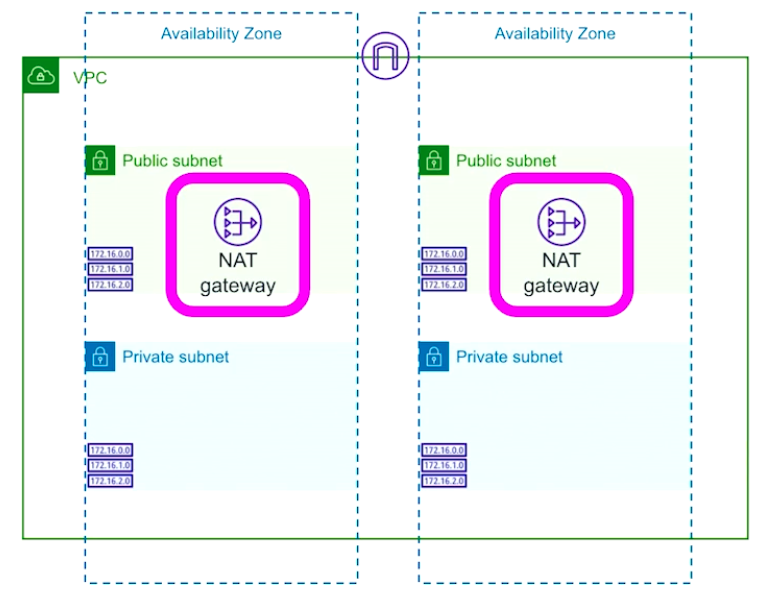
NAT Gateway
Allowing outbound resource for private gateways.
It is AZ scoped resource and is deployed into the subnet.
One NAT Gatewayper AZ is recommended for higher resilience.
Enable Internet Access through Console
- Create internet gateway
- Attach to desired VPC
- Go to Route Tables
- Create a Route Table
- Associate with VPC
- Create a route in the route table by scrolling down to routes in the Route Table
- Click
edit routes - Add a route with IP address of
0.0.0.0/0with a target to igw - Now the igw that's created from #1 is attached to the VPC and added to the route table
- Associate the public subnet to the route table
- From Route Tables, click on
edit subnet associationson explicit subnet - Select the public subnet to associate with the public route table
- Theoretically, resources that are launched in that public subnet will have access to and from the internet
Tip: Go to the public subnet and
edit subnet settings, enable auto assign public IPv4. Then any resource that is created in this subnet will automatically be given a dynamic public IP.
Setup NAT gateway
NAT gateway is a resource that costs.
- Create NAT gateway
- Select a public subnet for
subnetbeacuse that's the one that has access to and from the internet - Select public connectivity since we want grant access to the internet
- NAT gateway need to be granted a static, public IP address
- Click on allocate Elastic IP
- Now the NAT gateway ID can be used as a target in the route table
- Create another route table for a private subnet
- When setting the target, select NAT Gateway instead of igw
- Add private subnet associations
Traffic Control for VPC
NACL (Network Access Control List)
Associate with subnets along with the route table as a stateless firewall.
Characteristics
- It acts as a stateless firewall, which means you have to create rulse in both directions
- The rules are evaluated in specific orderSimilar to route tables, it's better to attach one per subnet but for organization purposes, it is common to see combined NACL.
Security Group
Rather than being associated with a subnet, it is associated with a network interface as a stateful firewall.
Security groups only require single rule in the direction of traffic and the return traffic is automatically allowed.
The default is to deny all inbound traffic, so with a brand-new security group, no inboud traffic is allowed.
Create one secruity group per application per tier.
Setting Up NACL
Scenario: We would like to assume that we are going to deny all inbound traffic from the public subnet.
- On VPC console, find the Network ACL tab under Security
- Create Network ACL (assuming this ACL is for a database, no inboud traffic should be allowed)
- Associate with the VPC
- Modify Inbound Rules
- Add a new rule with
Type: All traffic - Set
Sourceas your public IP address, eg.10.100.1.0/24and select deny - Add a second rule to allow traffic from the rest of the VPC, eg.
10.100.0.0/16 - Edit outbound rule to allow all traffic from the VPC, eg.
10.100.0.0/16 - Associate this NACL with a subnet, select the public subnet (not db subnet) and associate.
This implies that the public subnet will have the above restrictions applied
Setting up Security Groups
Scenario: We would like to deploy a load balancer into our public subnet that allows all inbound traffic on ports 80 and 443 from the entire world.
- Create security group
- Choose the correct VPC
- Set Inbound Rule,
1. Type: HTTP
Source: IPv4, 0.0.0.0/0
2. Type: HTTPS
Source:IPv4, 0.0.0.0/0- Then create a front-end facing resource to connect with this security group
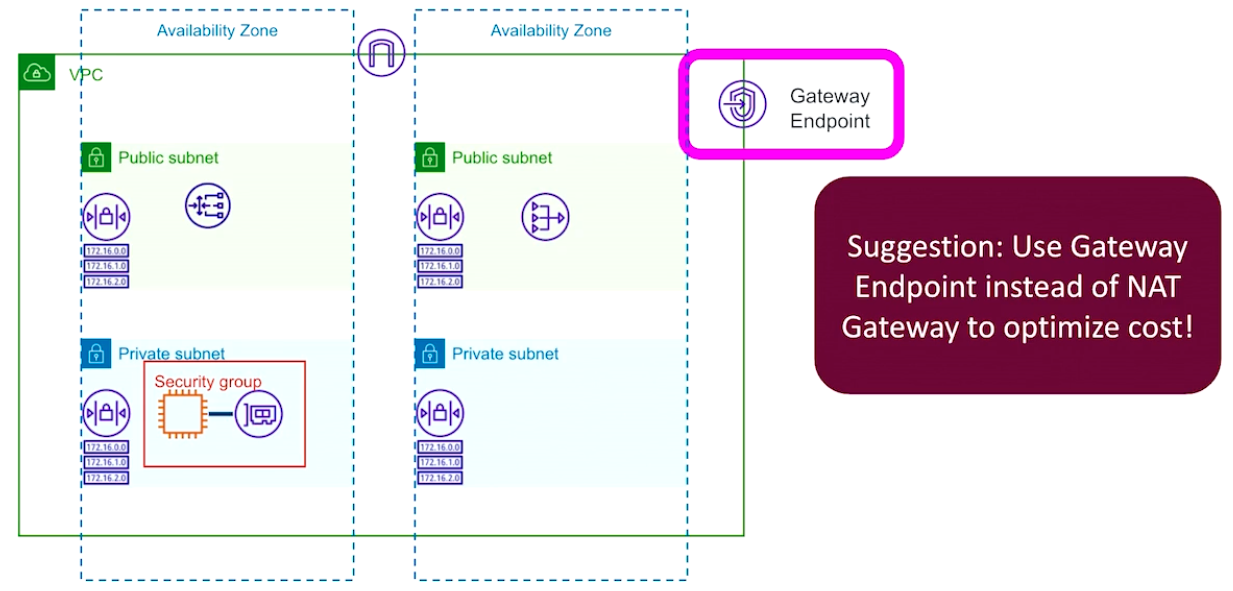
VPC Endpoints
Gateway Endpoints
Same-region resources only that's attached to the VPC for S3 and DynamoDB access
Gateway endpoints require a route table entry to be created in any subnet that you want to use this Gateway endpoint from.
Diagram
Advantages
FREE !! for S3 and DynamoDB
Interface Endpoints
Associate with one subnet, one security group, one AWS service
NOT FREE
It acts as a direct proxy to the AWS service.
Use to connect to private endpoints in VPCs in other accounts.
Also used with a service called Private Link where you can expose endpoints that are in other VPCs, behind a network load balancer.
Configuring VPC Endpoints
Senario 1. Push all S3 traffic from our VPC private subnet directly to the service, so that we are not utilizing the NAT Gateway and incurring the NAT Gateway throughput charges.
- Go to VPC console
- Select Endpoints
- Create Endpoint (this will be an endpoint for s3)
- Search for
S3in Services, Type: Gateway - Select desired VPC
- Select Route Table, private subnet
- Policy tab shows
resource based policies - Create Endpoint
Senario 2. Interface Endpoint that blocks all public access but allow access to CloudWatch for monitoring
- Same up to #3
- Search for
monitoringin Services - Select VPC and subnet
- Choose private subnet
- Select default security group and change access later on
Disclaimer
This summary is made possible by Oreilly's AWS, 3rd Edition - Chad Smith.
If the above post violates any copyright permissions, please let me know!

