Introduction
The Network Security Operation position I would be taking requires extensive experience in network contstruction.
When I was a university student, I practiced various network configurations using Cisco Packet Tracer while studying for the CCNA certification.
However my current role as an Infrastructure Security Engineer involves responding to security incidents in a business environment, rather than directly engaging in network construction.
Therefore, it is worthwhile to review the concepts related to network configuration.
packettracernetwork.com
Unlike the Cisco official website, which only covers basic usage of Packet Tracer, packettracernetwork.com offers guides for various network scenarios and configurations.
I will follow along with provided practice files on this site to familiarize myself with network configuration concepts.
Lab 1 : Basic switch setup
This lab will test your ability to configure basic settings such as hostname, motd banner, encrypted passwords, and terminal options on a Cisco Catalyst 2960 switch.
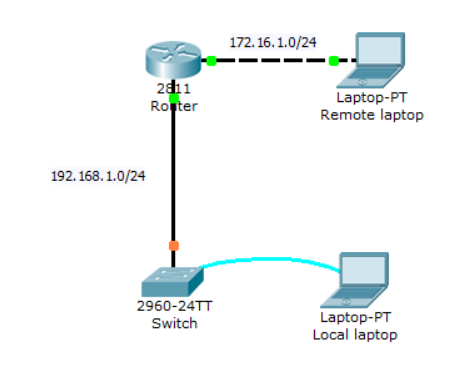
Network diagram
Prerequisites
Switch
There is no preconfigured item. (vlan, interface status, etc)
Router
FastEthernet0/0, FastEthernet0/1 have been assigned the ip addresses 192.168.1.1 and 172.6.1.1, respectively:
Router(config)#int fastEthernet 0/0
Router(config-if)#ip address 192.168.1.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#
%LINK-5-CHANGED: Interface FastEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
Router(config-if)#exit
Router(config)#int fastethernet 0/1
Router(config-if)#ip address 172.16.1.1 255.255.255.0
Router(config-if)#no shutdown
Router(config-if)#
%LINK-5-CHANGED: Interface FastEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
Router(config-if)#exitRemote laptop
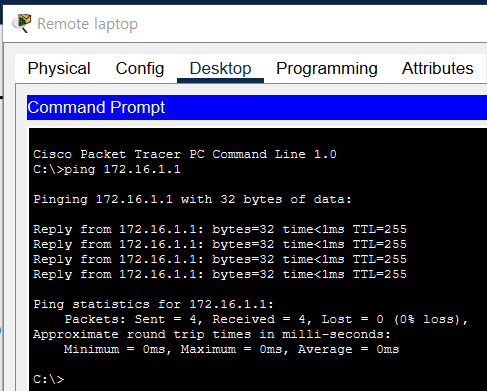
The Remote laptop has been assigned the ip address 172.16.1.2 to connect to the Router.
After setting the ip address of the Remote laptop, it could communicate with the Router via ICMP.
Questions
Q1. Configure Switch hostname as LOCAL-SWITCH
Switch#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#hostname LOCAL-SWITCH
LOCAL-SWITCH(config)#Q2. Configure the message of the day as "Unauthorized access is forbidden"
LOCAL-SWITCH(config)#banner motd #
Enter TEXT message. End with the character '#'.
Unauthorized access is forbidden#Let's check whether this message is displayed:
LOCAL-SWITCH#exit
LOCAL-SWITCH con0 is now available
Press RETURN to get started.
Unauthorized access is forbidden
LOCAL-SWITCH>Q3. Configure the password for privileged mode access as "cisco". The password must be md5 encrypted
Configure the password for privileged mode access as "cisco":
LOCAL-SWITCH(config)#enable secret cisco
LOCAL-SWITCH(config)#exit
LOCAL-SWITCH# show running-config
Building configuration...
...
...
...
!
hostname LOCAL-SWITCH
!
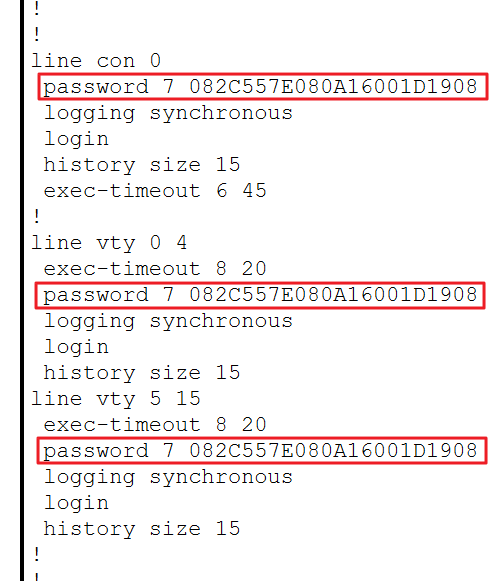
enable secret 5 $1$mERr$c3N7F.QsD6uEqs2Smq6Q..Configure the password for console/remote access as "myPassword":
LOCAL-SWITCH(config)#line con 0
LOCAL-SWITCH(config-line)#password myPassword
LOCAL-SWITCH(config-line)#logging synchronous
LOCAL-SWITCH(config-line)#login
LOCAL-SWITCH(config-line)#history size 15
LOCAL-SWITCH(config-line)#exec-timeout 6 45
LOCAL-SWITCH(config-line)#exit
LOCAL-SWITCH(config)#line vty 0 15
LOCAL-SWITCH(config-line)#password myPassword
LOCAL-SWITCH(config-line)#logging synchronous
LOCAL-SWITCH(config-line)#login
LOCAL-SWITCH(config-line)#history size 15
LOCAL-SWITCH(config-line)#exec-timeout 8 20
LOCAL-SWITCH(config-line)#exitAlso, the passowrd should be stored encrypted using MD5:
LOCAL-SWITCH(config)#service password-encryptionIf these steps so far have been completed, you won't be able to see any passwords in plain text:
Q4. Configure the IP address of the switch as 192.168.1.2/24 and it's default gateway IP (192.168.1.1)
LOCAL-SWITCH(config)#int vlan1
LOCAL-SWITCH(config-if)#ip address 192.168.1.2 255.255.255.0
LOCAL-SWITCH(config-if)#ip default-gateway 192.168.1.1
LOCAL-SWITCH(config-if)#no shutdownFinal Verification
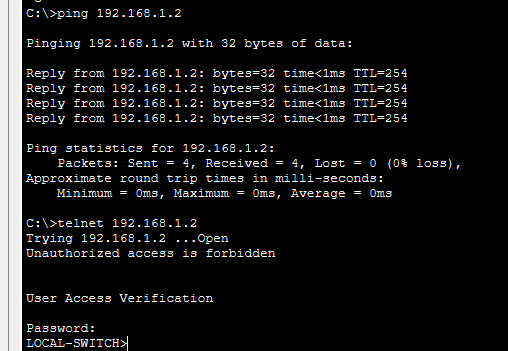
Connect from the Remote laptop to the Local-Switch via Telnet
References
https://www.packettracernetwork.com/labs/lab1-basicswitchsetup.html
