Scenario 1. Web site defacement
Summary
Today is Alice's first day at the Wayne Enterprises' Security Operations Center. Lucius sits Alice down and gives her first assignment: A memo from Gotham City Police Department (GCPD). Apparently GCPD has found evidence online (http://pastebin.com/Gw6dWjS9) that the website www.imreallynotbatman.com hosted on Wayne Enterprises' IP address space has been compromised. The group has multiple objectives... but a key aspect of their modus operandi is to deface websites in order to embarrass their victim. Lucius has asked Alice to determine if www.imreallynotbatman.com. (the personal blog of Wayne Corporations CEO) was really compromised.
The Splunk virtual server is provided, and we should resolve the questions related to the given scenario by analyzing the event logs stored in the Splunk server.
Q1. What is the likely IPv4 address of someone from the Po1s0n1vy group scanning imreallynotbatman.com for web application vulnerabilities?
First of all, I took a quick look at the types of the given event logs.
There seemed to consist of various log types, including Suricata JSON logs, Fortinet IDS logs, Stream data, and similar to that.
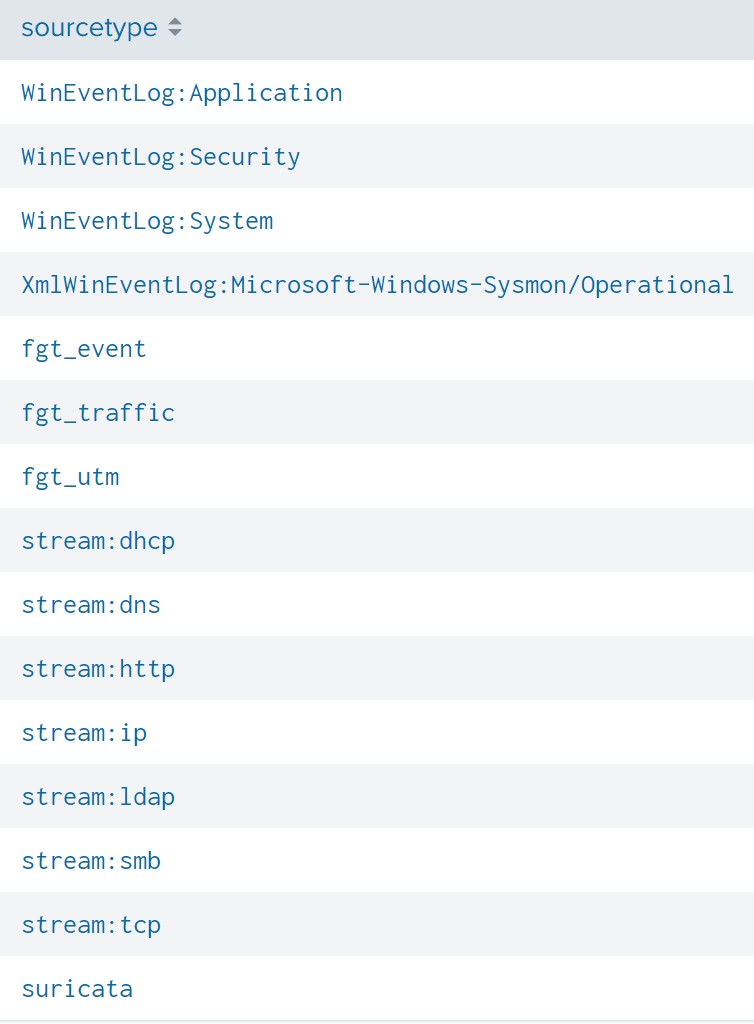
To find the Ipv4 address scanning "imreallynotbatman.com", I literally searched for the domain name in all event logs related to a web service.
Then I appended the conditions where the result would include URLs transmitted from a client to identify web scanning.
Its result clearly indicated only one IP address that appears to have been used by Po1s0n1vy group for web scanning:
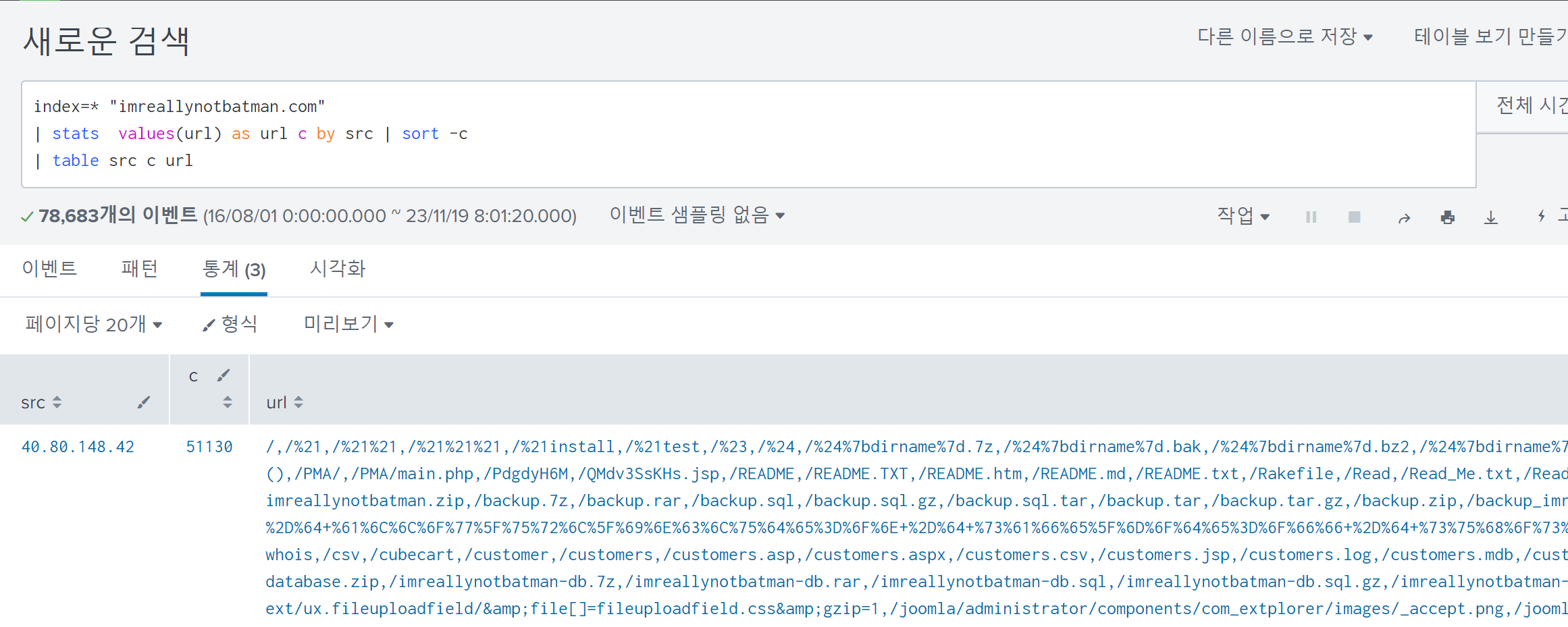
The answer is 40.80.148.42
Q2. What company created the web vulnerability scanner used by Po1s0n1vy?
The information about a used web scanner is typically included in the HTTP header User-Agent.
Therefore, I thought finding the vendor of the web scanner would be easy. However, upon sorting the results based on User-Agent and glancing at them, no evidence of a web scanner was found:
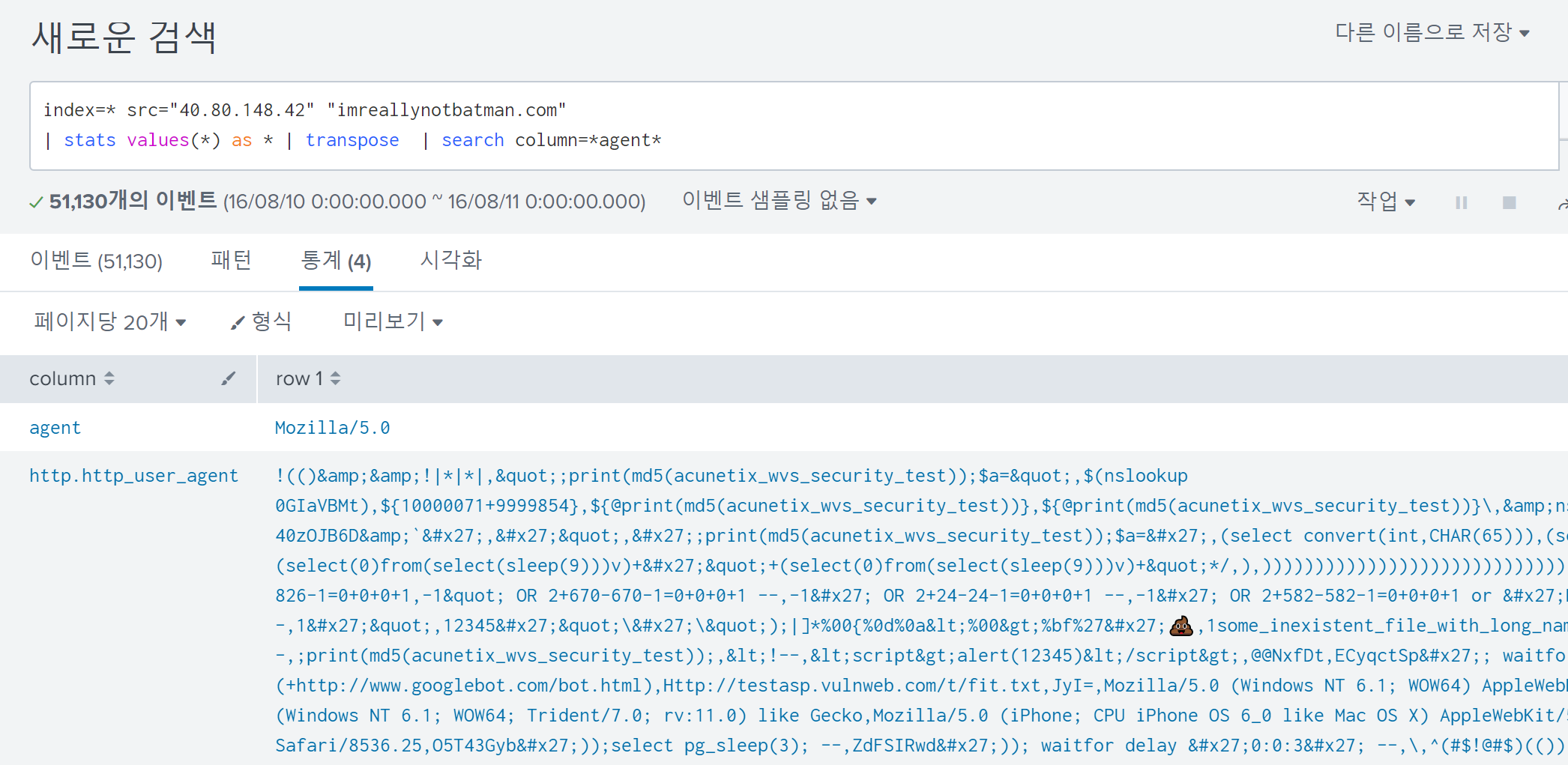
Instead I found the suspicious value as follows:
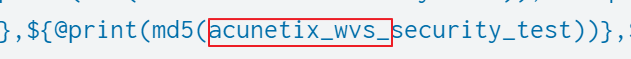
I believed it was likely the signature of a web scanner, and it was:
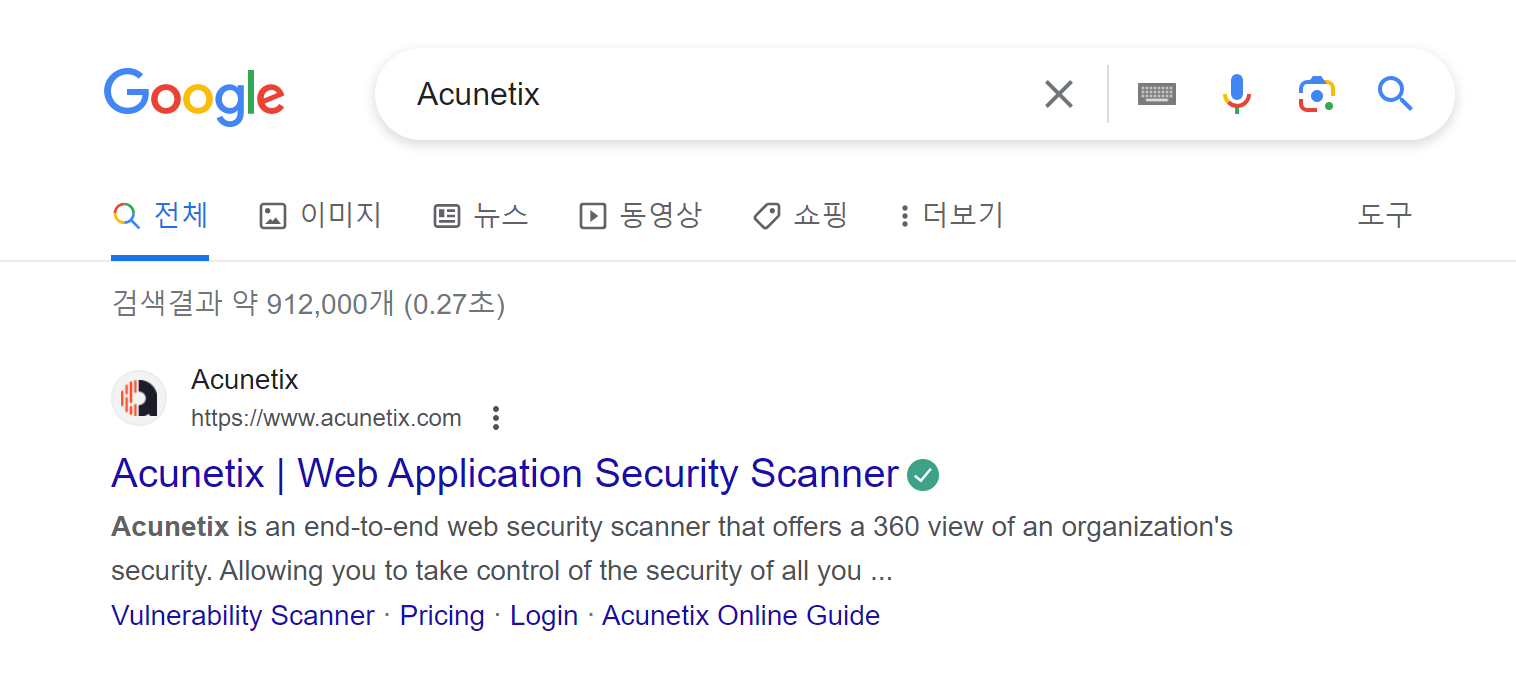
The answer is Acunetix.
Q3. What content management system is imreallynotbatman.com likely using?
The answer to this question could be found by simply verifying the URL path that returned a status code of 200 and was accessed most frequently by clients:
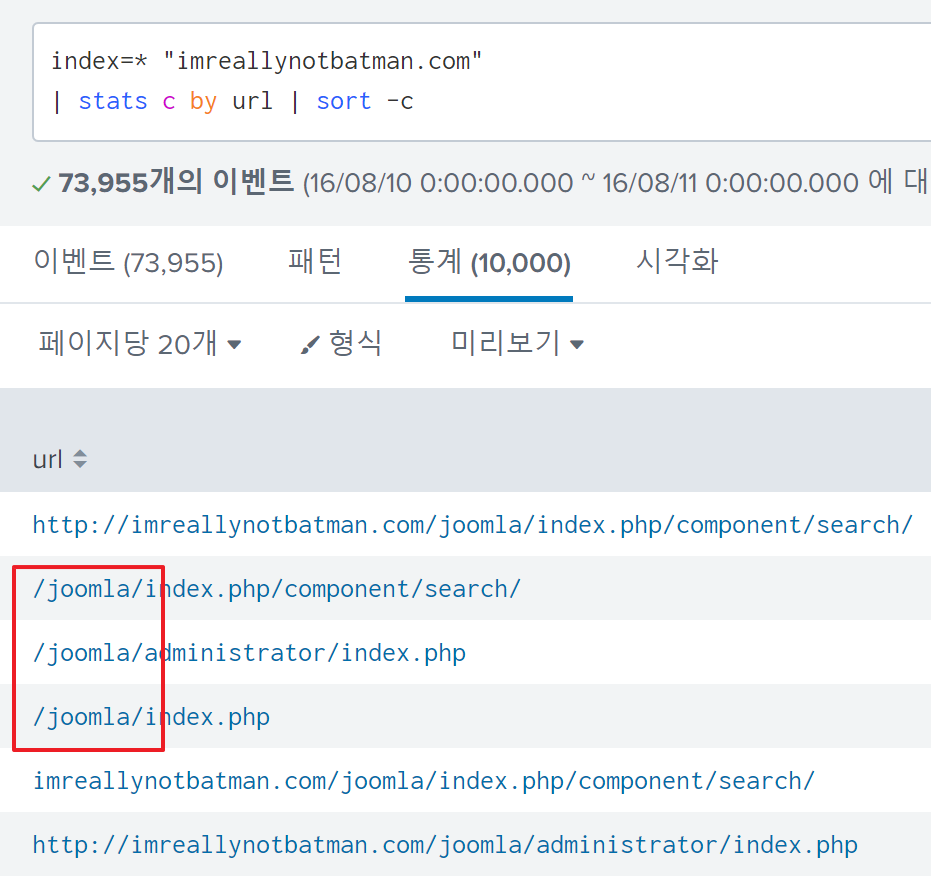
The answer is joomla.
Q4. What is the name of the file that defaced the imreallynotbatman.com website?
Actually, I had difficulty understanding the meaning of "defaced".
I couldn't determine whether a malicious file was uploaded to the web server or whether existing files were changed. The only centainty was that it indicates some activities by a attacker with negative effects occurred on the web server.
One of the web server's responses to the attack is connecting to external malicious sites as follows:
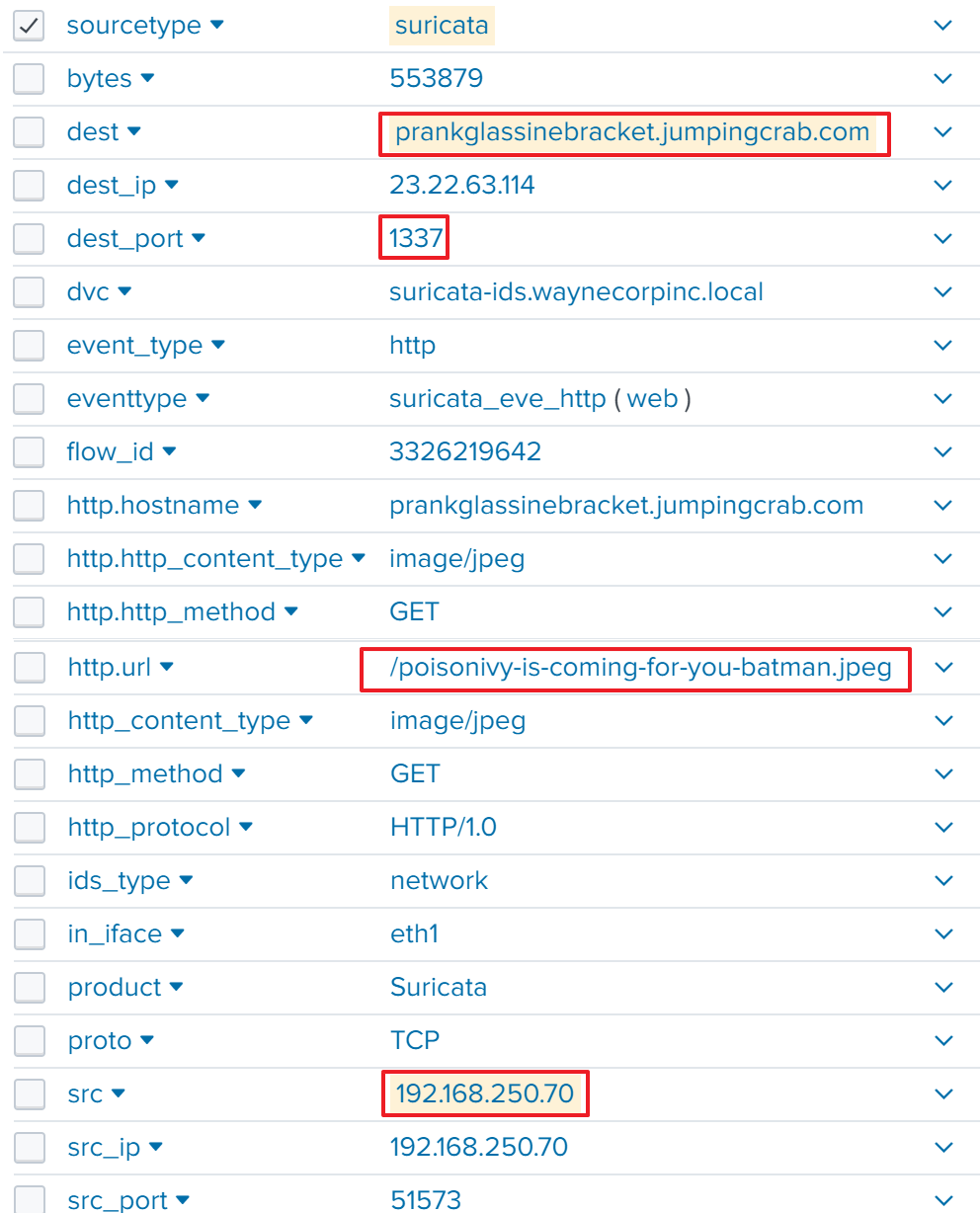
There were a few notable points.
destisprankglassinebracket.jumpingcrab.com. (typically a web server may not connect to this)dest_portis1337. (This is a registed port, and typically, a web server may not use this port when connecting to an external web server)
The file name in the URL is /poisonivy-is-coming-for-you-batman.jpeg and this is correct answer.
Q5. This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack?
We've already found the solution to this question in the previous Q4.
The answer is prankglassinebracket.jumpingcrab.com.
Q6. What IPv4 address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
This question is asking for the IPv4 address of the domain prankglassinebracket.jumpingcrab.com which was the solution forQ5
The answer is 23.22.63.114.
