Q8. What IPv4 address is likely attempting a brute force password attack against imreallynotbatman.com?
A brute force attack is typically carried out through HTTP URL parameters or HTTP Body parameters, with the aim of extorting a user's credentials.
First, I took a look at the HTTP URL parameters contained in uri field and HTTP Body parameters contained in src_content.
Shortly afterward, I identified the suspicious parameter passwd in the HTTP Body.
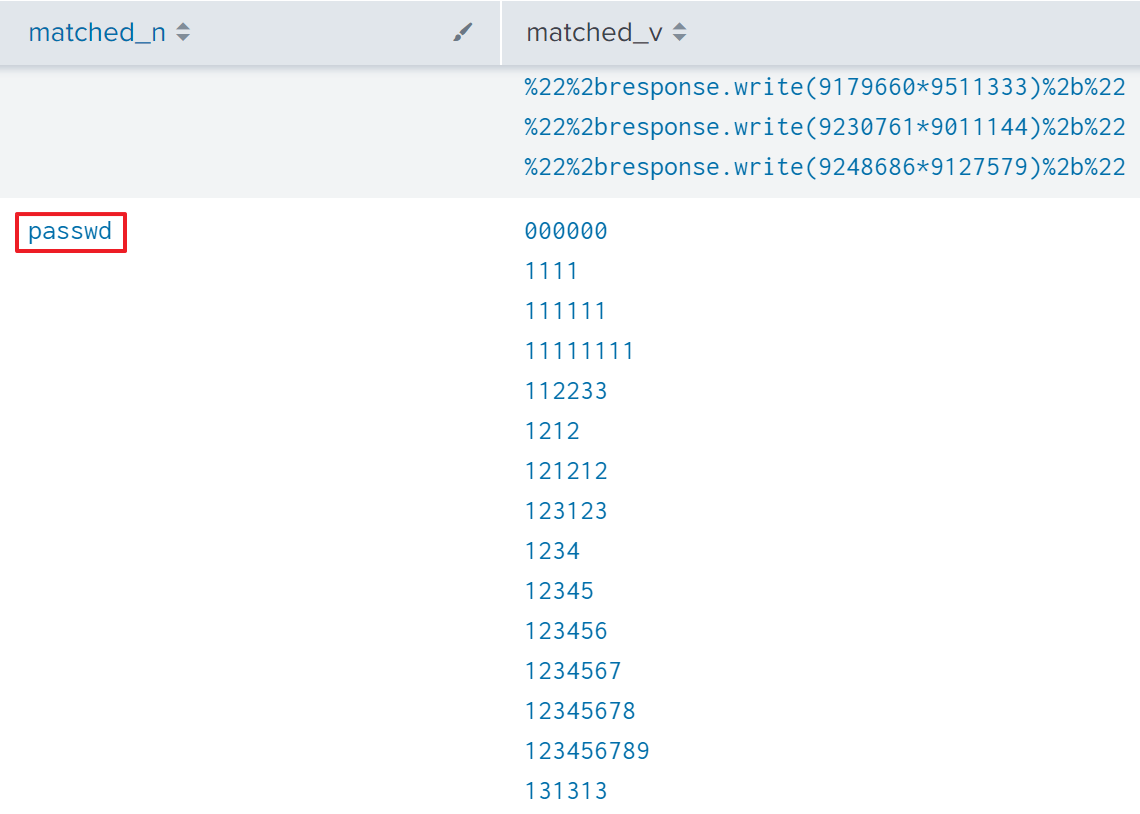
Sorting the IPv4 address based on the number of sending HTTP packet containing passwd field, I could verify which IPv4 address had performed brute force attack.
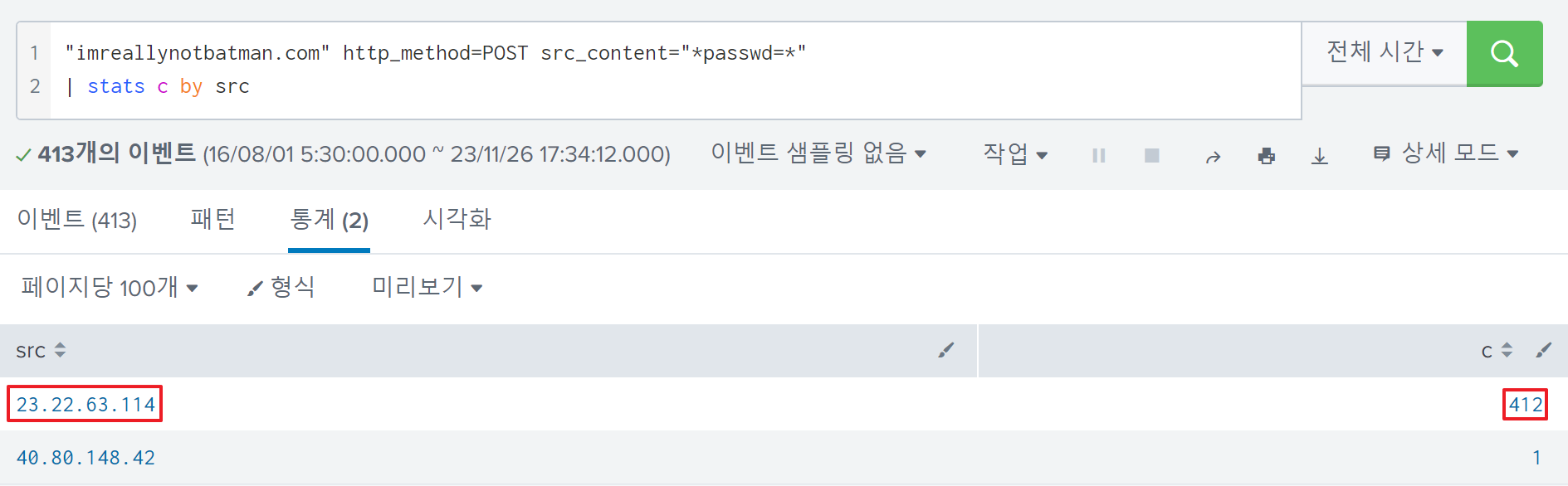
The answer is 23.22.63.114.
Q9. What is the name of the executable uploaded by Po1s0n1vy?
It was quite easy to find the executable uploaded by Po1s0n1vy.
I simply searched event logs with conditions, including such strings, 40.80.148.42(which would return activities related to Po1s0n1vy) and this program cannot be run in dos mode(this is a PE signature contained in the PE Header - Dos Stub)
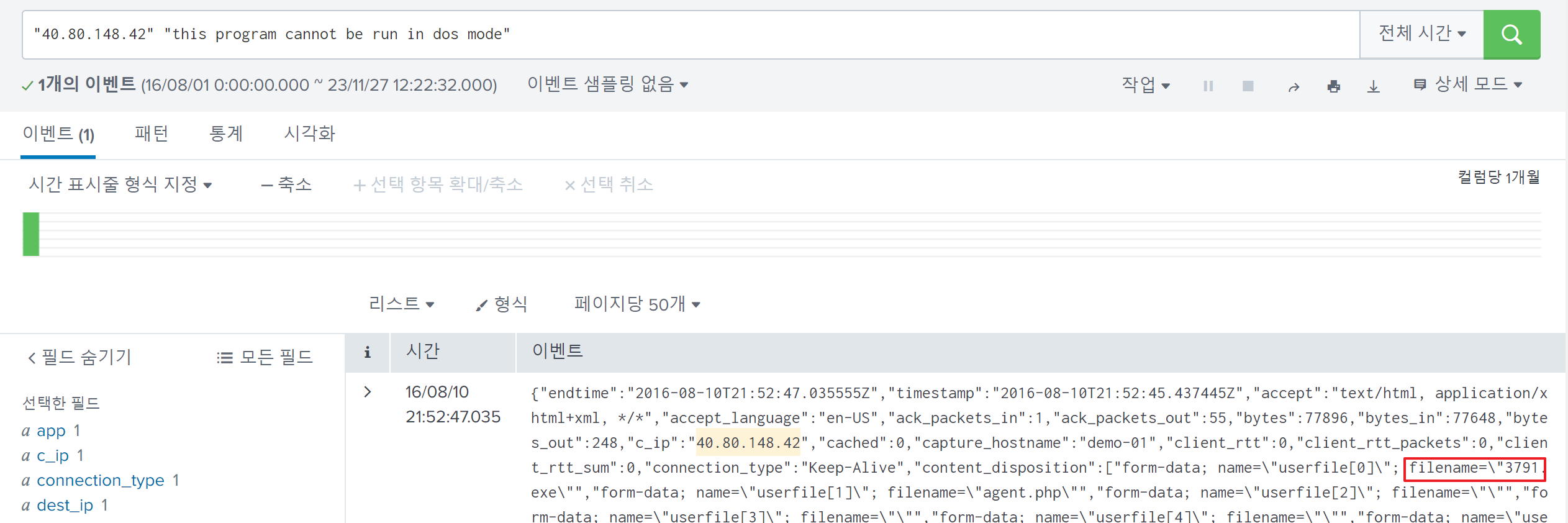
Only one event log of typestream:http was returned, indicating that the attacker accessed imreallynotbatman.com/joomla/administrator/index.php?option=com_extplorer&tmpl=component and uploaded 3791.exe and agent.php to the web server with aContent-Type of multipart/form-data;
The answer is 3791.exe.
Q10. What is the MD5 hash of the executable uploaded?
The MD5 hash has a feature of producing an output with a length of 16 bytes.
I searched for event logs which have a field with a length of 32 and include the file name of executable uploaded by Po1s0n1vy, 3791.exe:
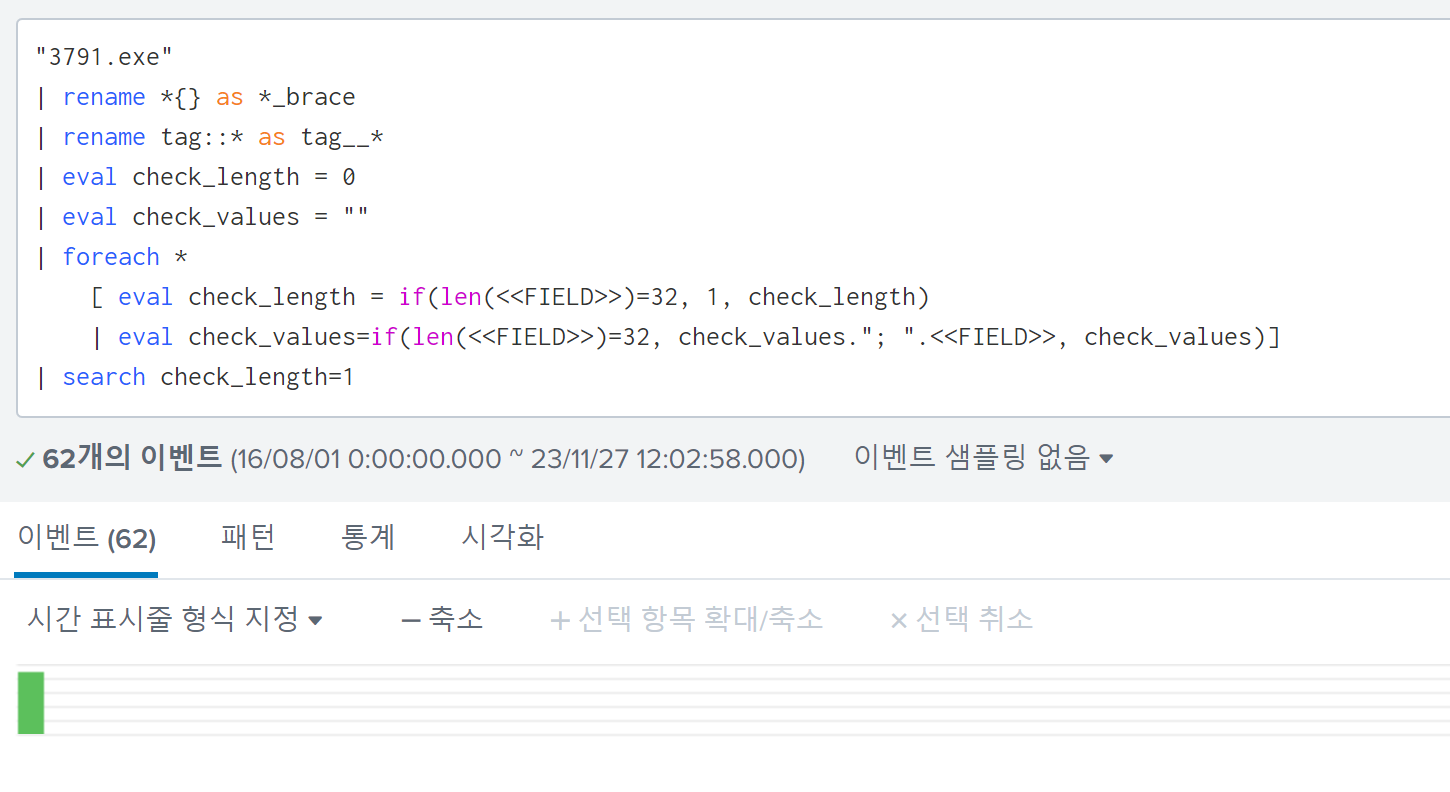
There were 62 search results, each of which had the MD5 field with distinct a value.
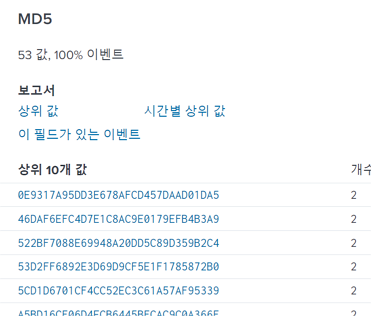
I needed to find the MD5 value of 3791.exe.
After examining other fields, I located an EventDescription field indicating the type of process activity.
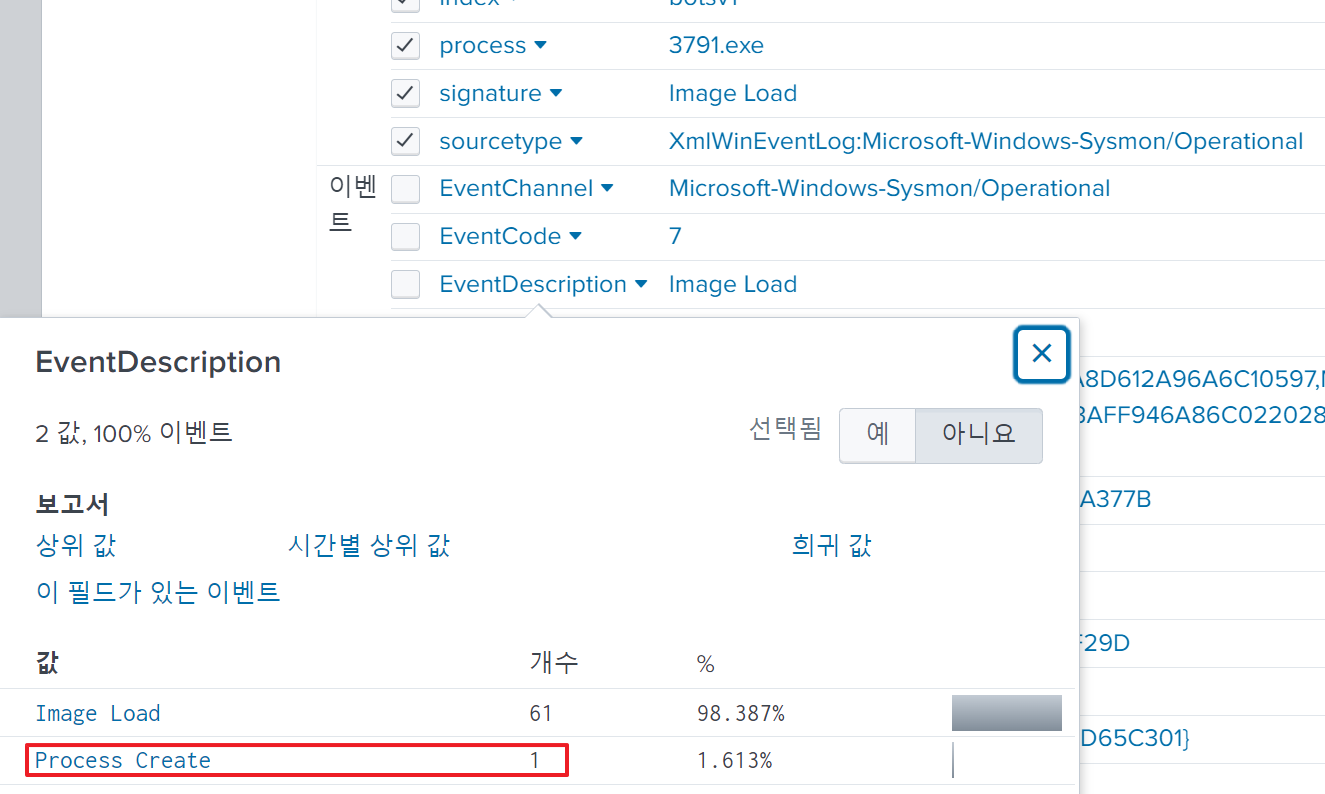
I set this to Process Create and It returned the event log that included the MD5 value of 3791.exe.
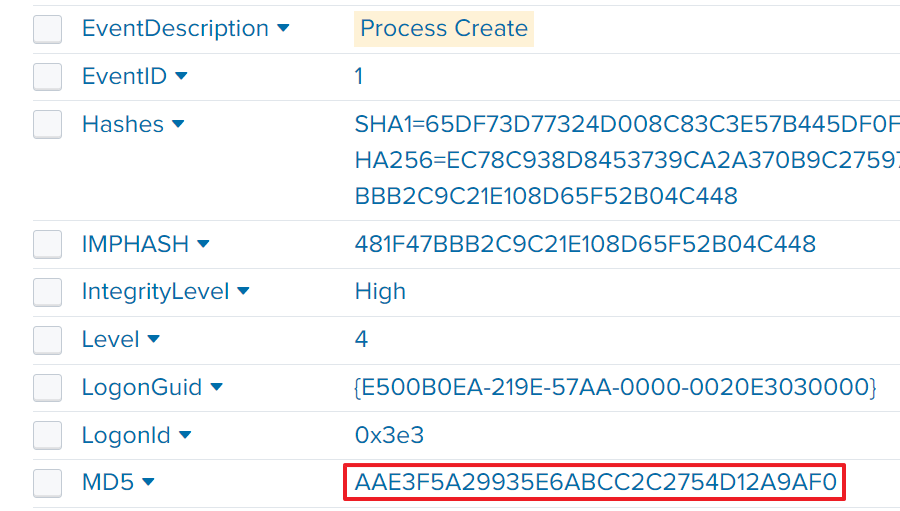
The answer is AAE3F5A29935E6ABCC2C2754D12A9AF0.
Q11. GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vys initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
Q12. What special hex code is associated with the customized malware discussed in question 111?
These questions are related only to research techniques, so I would skip them without solving.
Q14. What was the first brute force password used?
I have already identified what the attacker used for the brute force attack and who had performed the brute force attack in the previous question.
Let's investigate with this information.
I could check several logs.
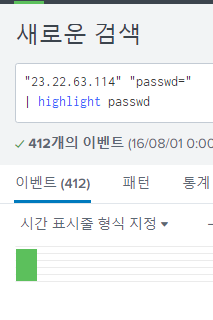
Among them, the correct answer was found in the first transmitted HTTP request.
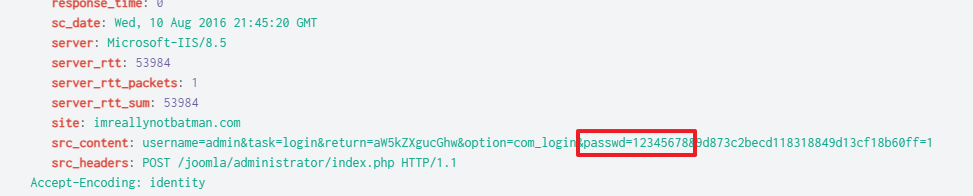
The answer is 12345678.
Q15. One of the passwords in the brute force attack is James Brodsky's favorite Coldplay song. We are looking for a six character word on this one. Which is it?
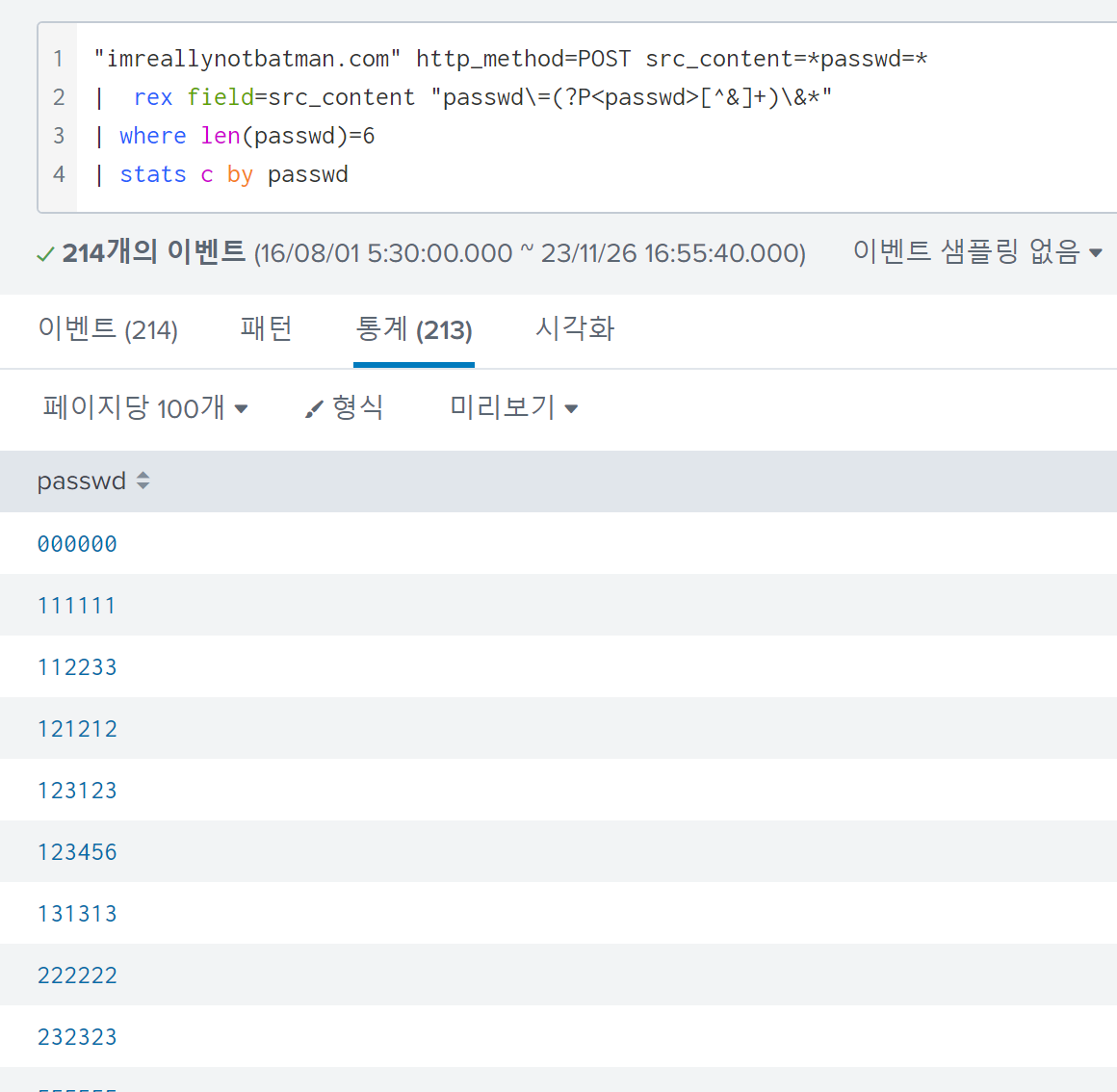
Since I identified the field used for the brute force attack in the previous question, obtaining the word list that the attacker used as a password(with a length of 6) was easy.
Also, I searched for a Coldplay song list on the internet.
Finally, I was able to find the answer to this question by comparing these using Python.
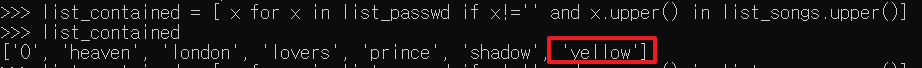
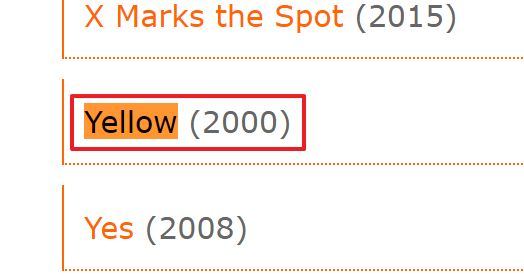
The answer is yellow.
Q16. What was the correct password for admin access to the content management system running "imreallynotbatman.com"?
Initially, I thought the correct answer would be the one with different response code among the brute force HTTP traffics; however, That was a mistaken assumption.
After some consideration, I realized that in typical scenarios, attacker often access the admin page with correct credentials after a brute force attack.
After sorting HTTP traffics in chronological order, it became clearer. Following a brute force attack by 23.22.63.114, the attacker 40.80.148.42 accessed the URL /joomla/administrator/index.php with previously unseen parameters option and view.
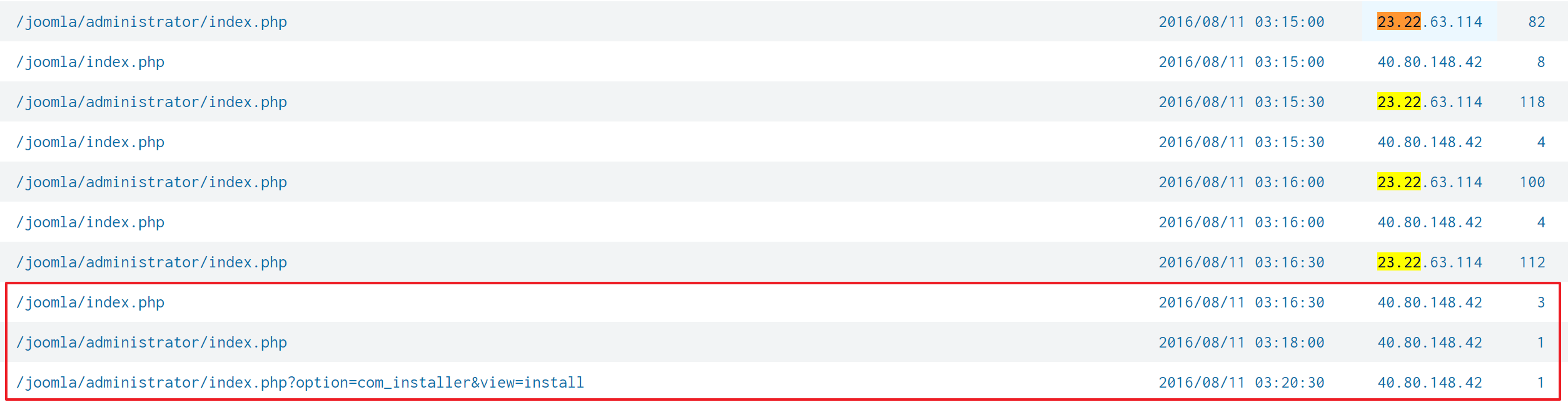
When searched with added conditions that the src_ip is 40.80.148.42 and the URL /joomla/administrator/index.php, there was only one result.
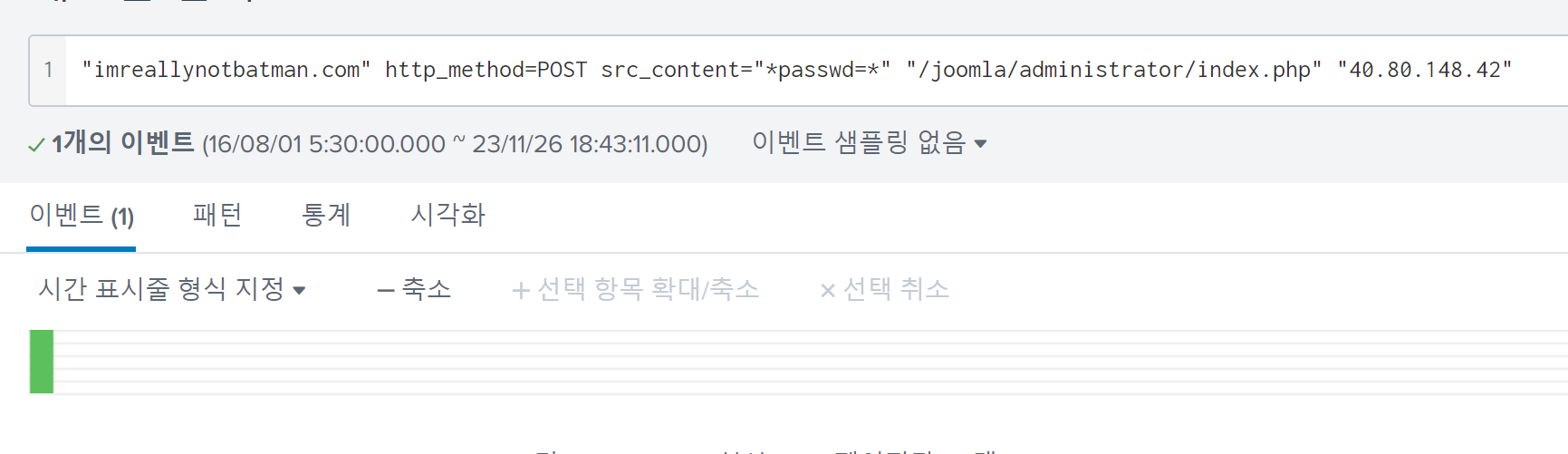
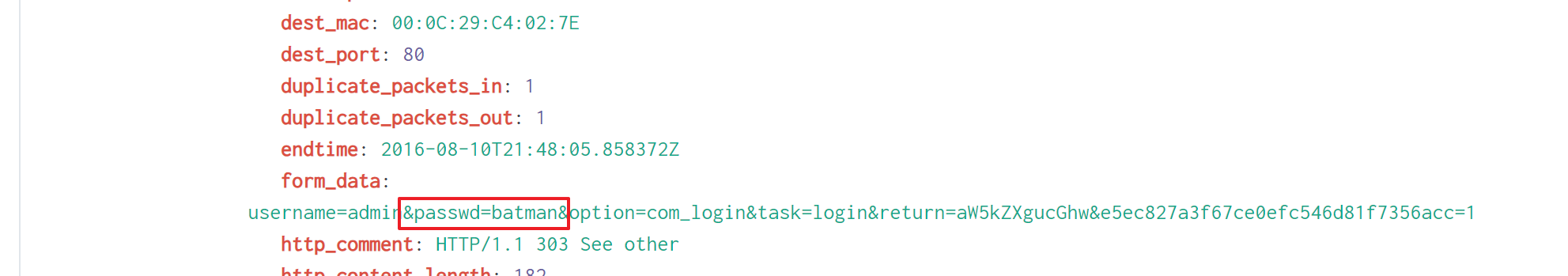
The answer is batman.
Q17. How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login?
Splunk provides avg keyword with the stats command, and I used it to display the average password length.
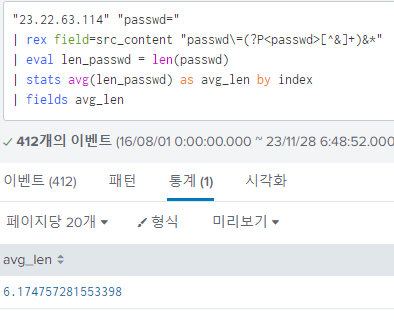
The answer required integer value:6.
Q18. How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login?
Regarding the previous answer, this question inquires about the duration between two login accesses with the password batman.
The duration of two things like this situation can be obtained using the command transaction:
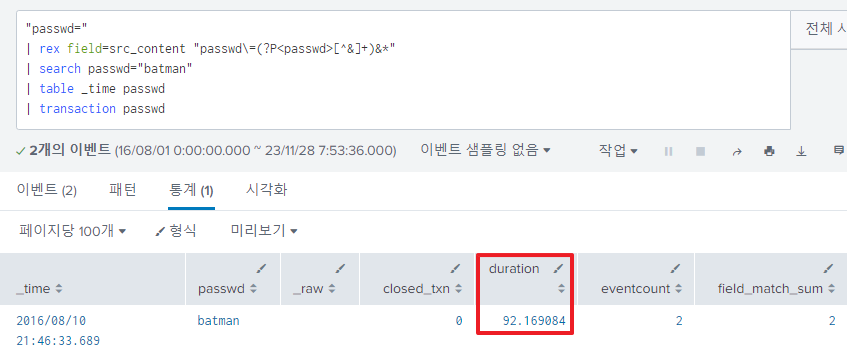
The answer is 92.
Q19. How many unique passwords were attempted in the brute force attempt?
Splunk also provides the dc keyword with the stats command, it returns the count of distinct values.
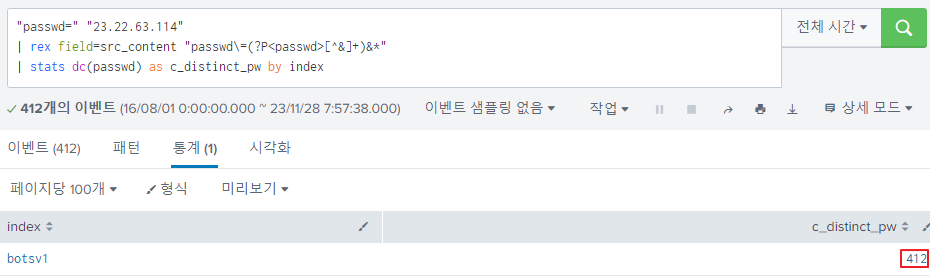
The answer is 412.
