10. standard and applications - Basic Security Protocols (network layer : IPSec)
🌙 CS_security
목록 보기
18/24
Index
- network layer security
- IP security
- Transport Layer Security
- (SSL) Secure Socket Layer
- (TLS) Transport Layer Security
- Operational Security
- Firewall
- (IDS) Intrusion Detection System
- Application Security
- Malicious software(virus, worm, dDos, etc.)
들어가며..
security suites
- suiate A [1]
- 자세히 대중에게 공개되지 않음
- ACCORDION, BATON, FFC, FIREFLY, JOSEKI, etc.
- Suite B [2]
- 대중에게 공개된 알고리즘
- AES, Eliptic Curve Signature Algorithm(ECDSA), Eliptic Curve Diffie-Hellman(ECDH), SHA-256 등
네트워크 모델
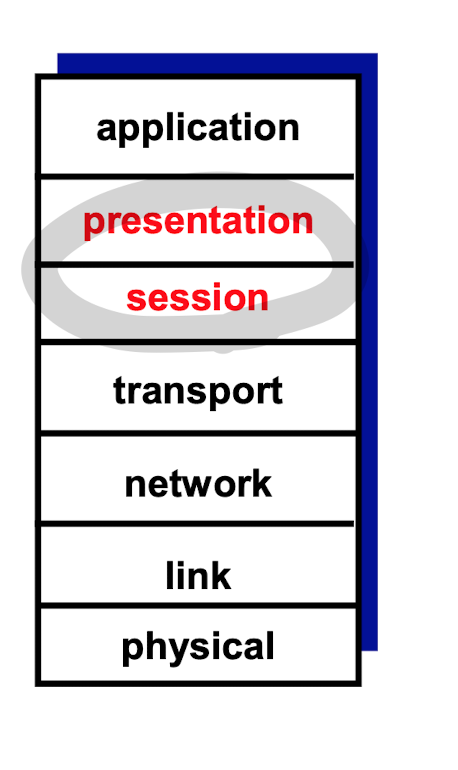
7계층에서 추가되는 계층들
-
presentation
application이 data의 meaning을 interpret하도록 한다.
e.g) encryption, compression, machine-specific conventions -
session
synchronization, check pointing , recovery of data exchange -
encapsulation
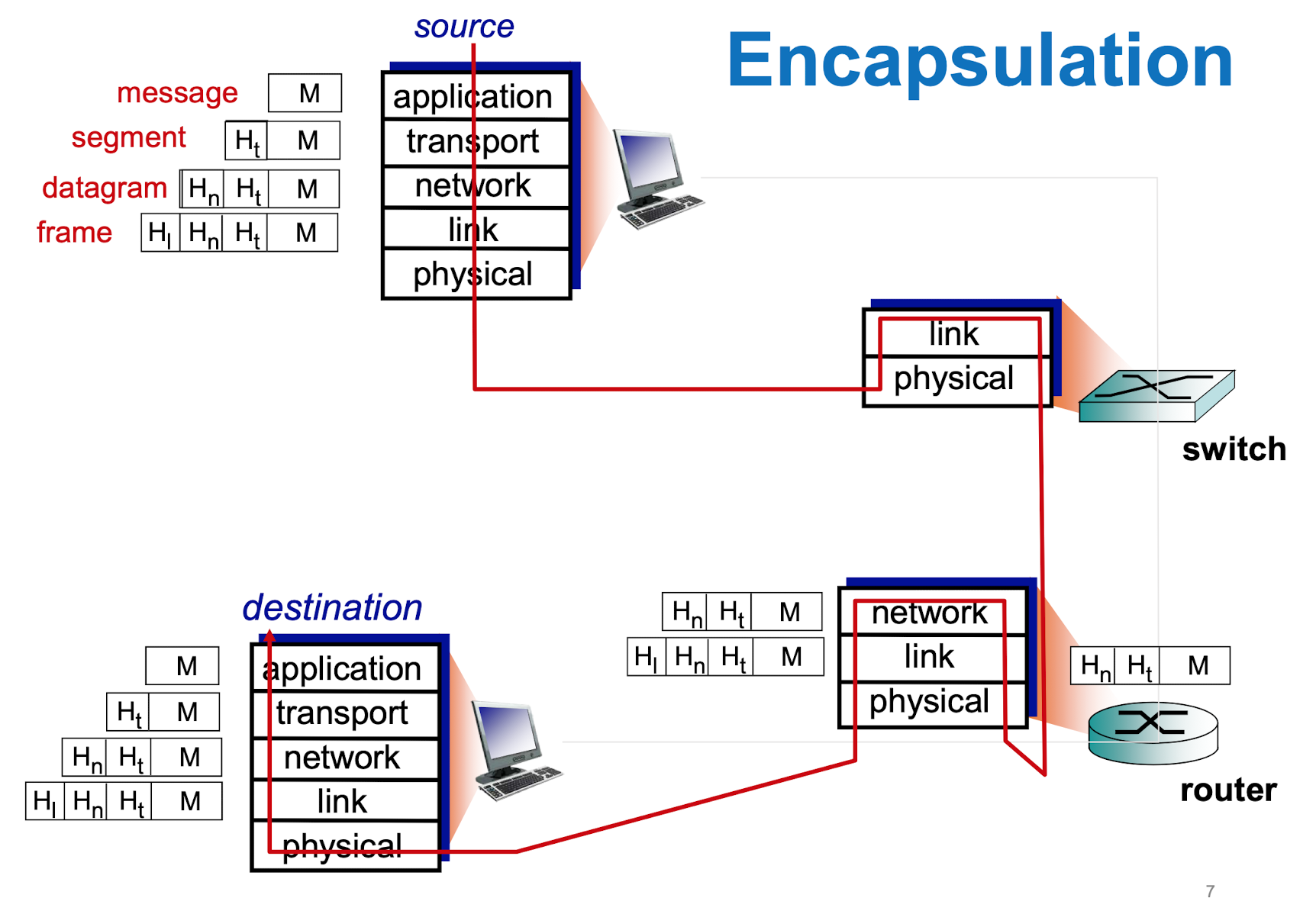
- security는 어떤 계층에 집어 넣을 수 있는가!
- application : S-HTP, S/MIME
- presentation : HTTP, FTP, SMTP
- transport : SSL/TLS
- network : IPSec
Network Layer Security
- network 계층
- connectionless service 제공
- routing (determine path)
- define addressing mechanism
- routing datagrams from source to destination
- IPSec 이 보안을 위해 디자인됨
VPN
- virtual private network
IPSec provides
- data origin authentication
- data content confidentiality
- connectionless data intergrity
- anti-replay protection
- limited traffic flow confidentiality
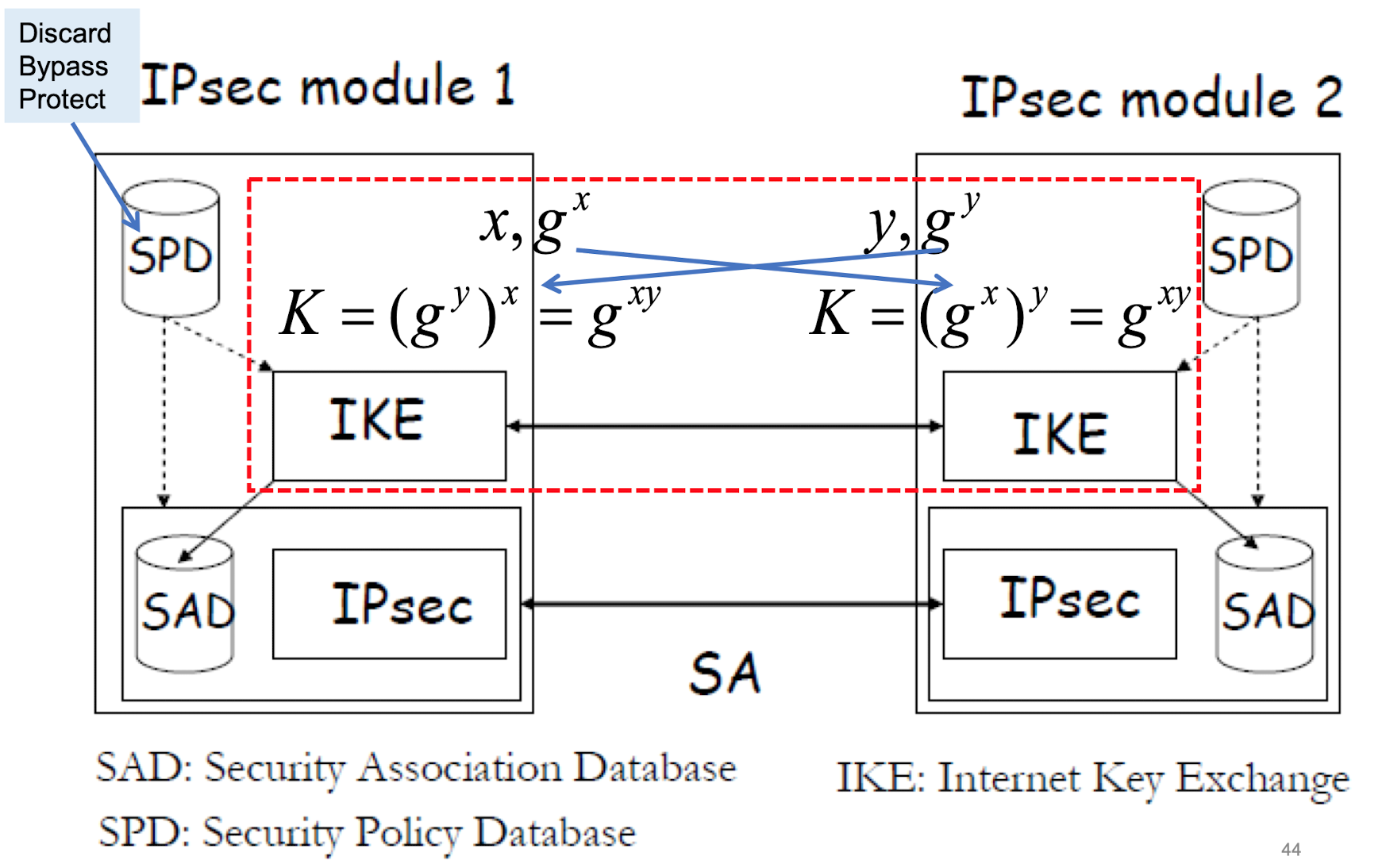
SA (Security Association)
-
목적
- defines security services and mechanism between two end point.
- define parameters, mode of operation, initialization vector
(e.g. confidentiality using ESP with DES in CBC mode with IV initialization vector .. ) - may use either AH(Authentication Header), ESP(Encapsulating Security Payload)
-
저장
- sender와 receiver 사이 one-way relationship의 경우, SAD(security Associated Database)에 저장된다.
-
key와 traffic 은 Protected 된다.
- SPI (Security Parameter Index)
- 해당 SA에 assigned된 bit string
- SPI는 AH(authentication header) 혹은 ESP(Encapsulating Security Payload)에 carried 된다.
- IPSec protocol identifier
- AH or ESP
- Destination address
- direction, firewall, router
- SPI (Security Parameter Index)
-
parameters
- Sequence number counter
- sequence counter overflow
- anti-replay window
- AH information
- ESP information
- Lifetime of this SA
- amount of traffic protected by a limited time or traffic.
- Lifetime{seconds|killobytes}
- IOSec protocol mode (Tunnel, Transport)
- path MTU (maximum size of a packet that can be transmitted without fragmentation)
-
security granularity(기본 단위)
- [user specified] 한 호스트의 모든 유저가 같은 Session key를 공유. Not recommended.
- [user-oriented keying] 한 호스트의 각 유저가 One or more unique session key가짐.
- [session-unique keying] IP addres, upper-layer protocol, port umber 에 single sessino key가 배정된다.
(SPD) Security Policy Database
- defines
- 어떤 traffic이 to be protected
- how to protect
- with whom the protection is shared
- SPD는 entering하거나 leaving하는 모든 각각의 Packet에게 어떤 security mechanism이 적용될지 결정
- action
- disacard : do not let packet in or out
- bypass : do not apply or expect security
- protect : apply/expect secuity
IPSec Protocols
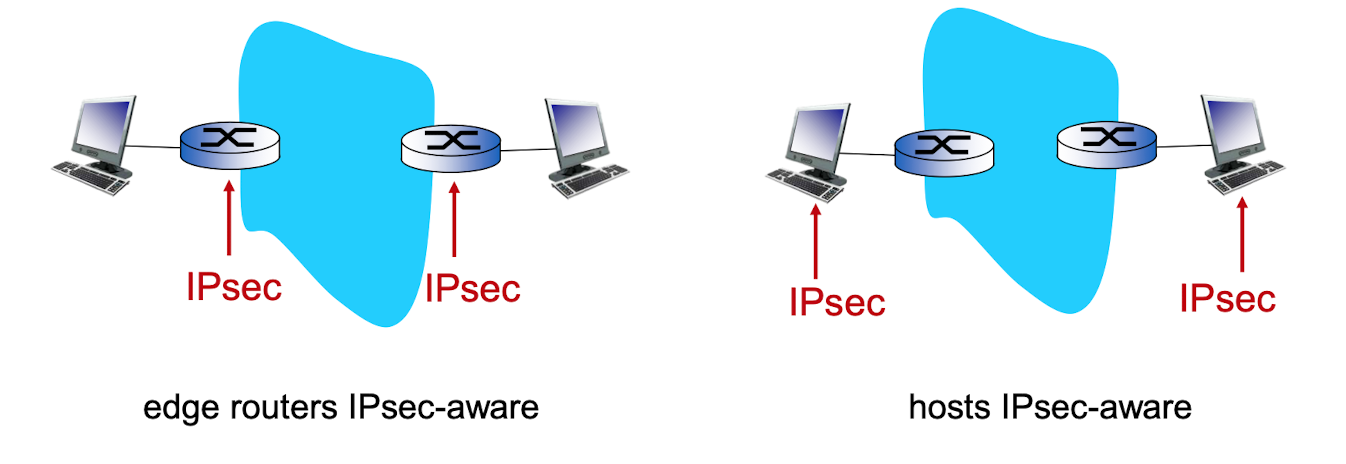
- operation mode
- transport mode
- 왜 사용되는가?
- Protection upper layer protocols
- 언제 사용되는가?
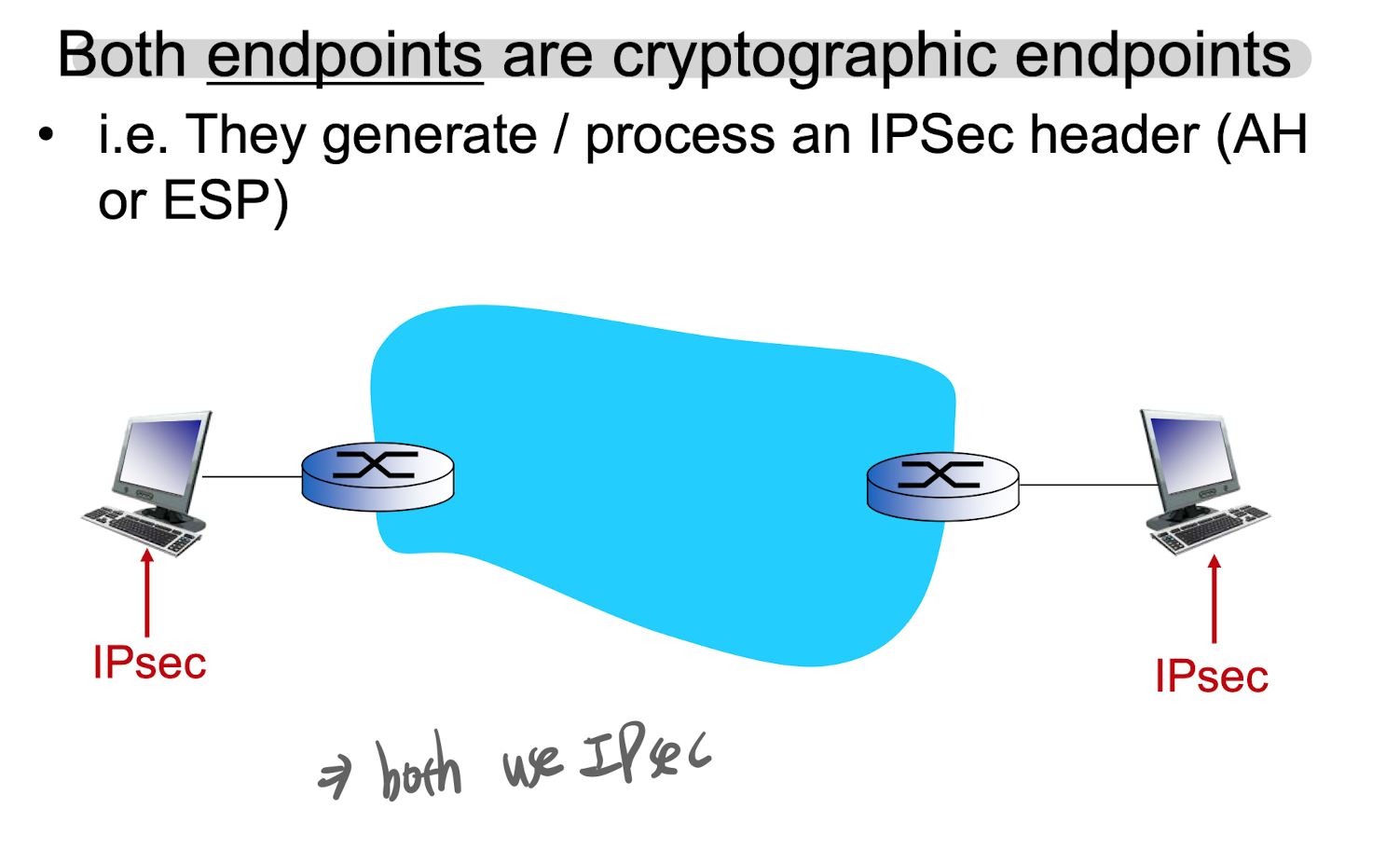
- 어떻게 삽입되는가?
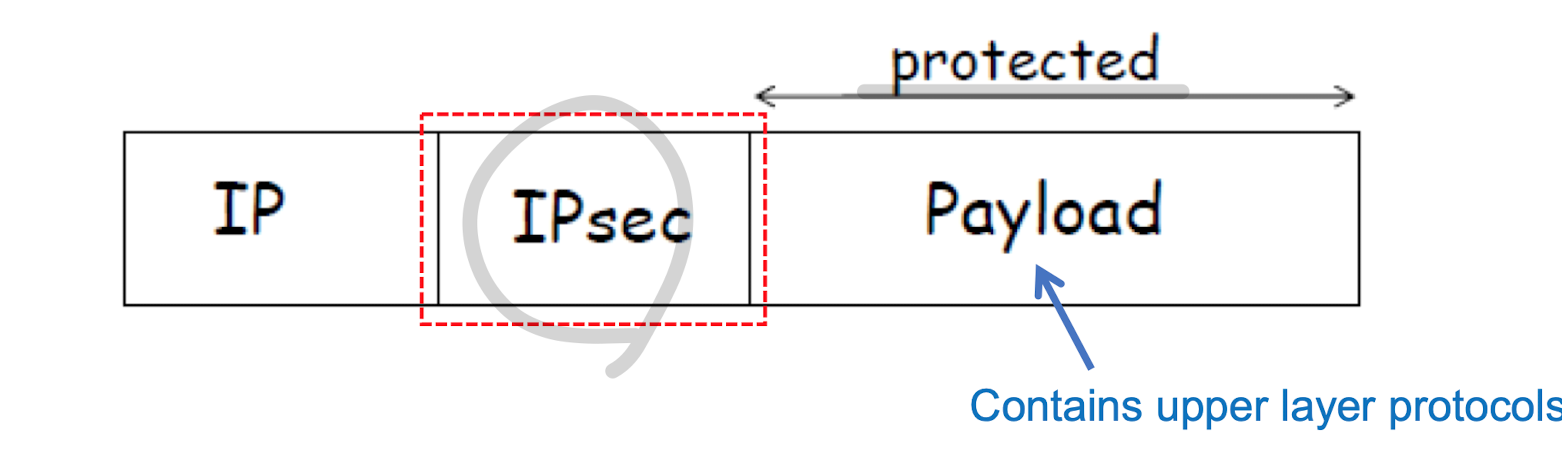
- inserted between ip header <-> upper-layer protocol
- 왜 사용되는가?
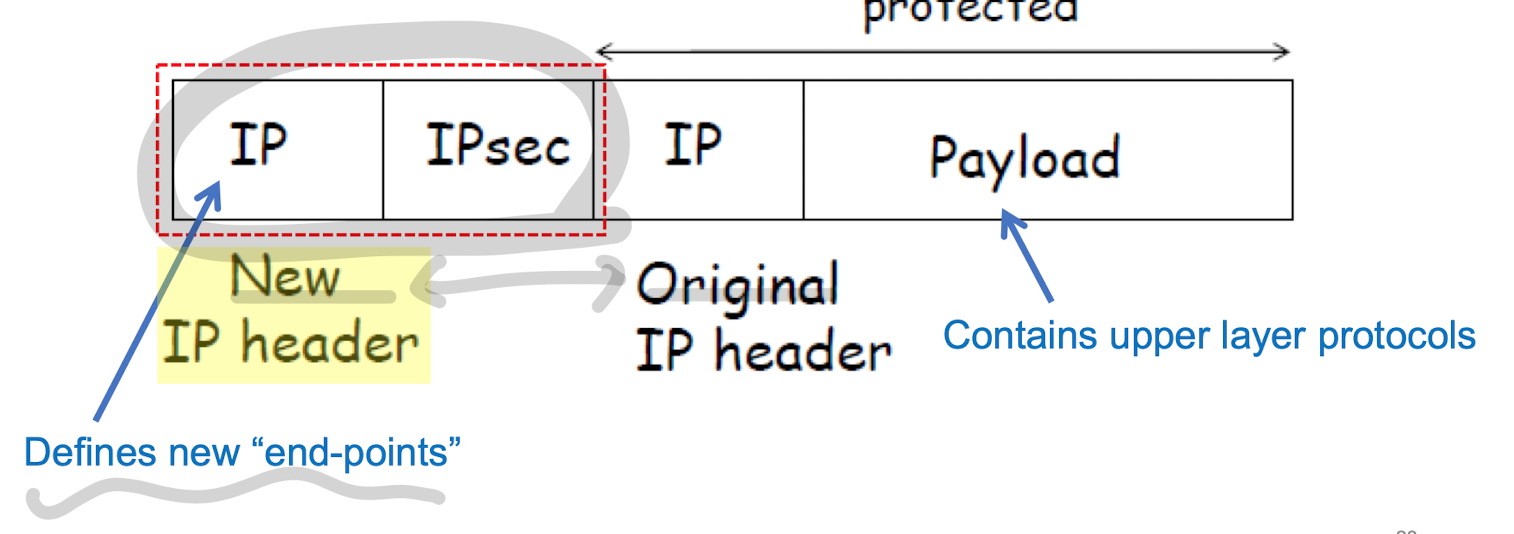
- tunnel mode
- 왜 사용되는가?
- protection entire IP datagram
- 언제 사용되는가?
- 한개 이상의 Point가 communication endpoint가 아닐때
- 한개 이상의 Point가 communication endpoint가 아닐때
- 어떻게 삽입되는가?
- 왜 사용되는가?
- transport mode
- 보통 tunnel mode with ESP 가 가장 자주 쓰인다.
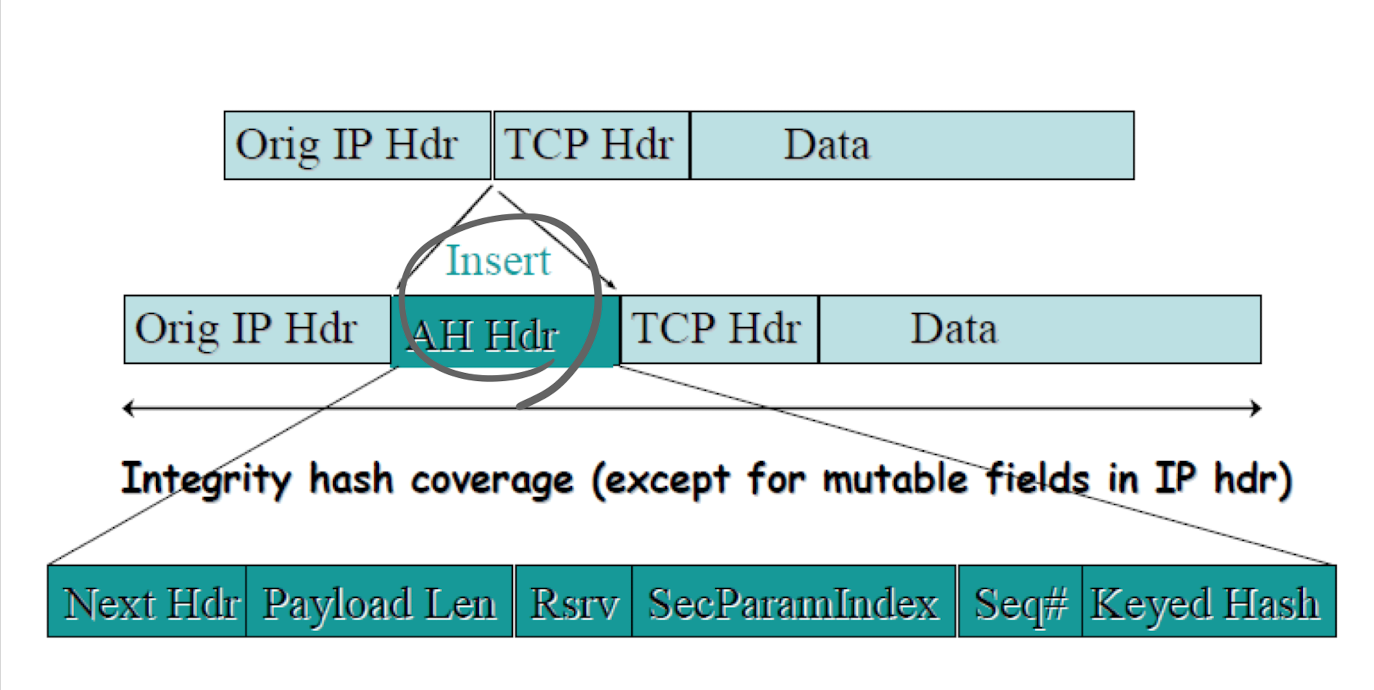
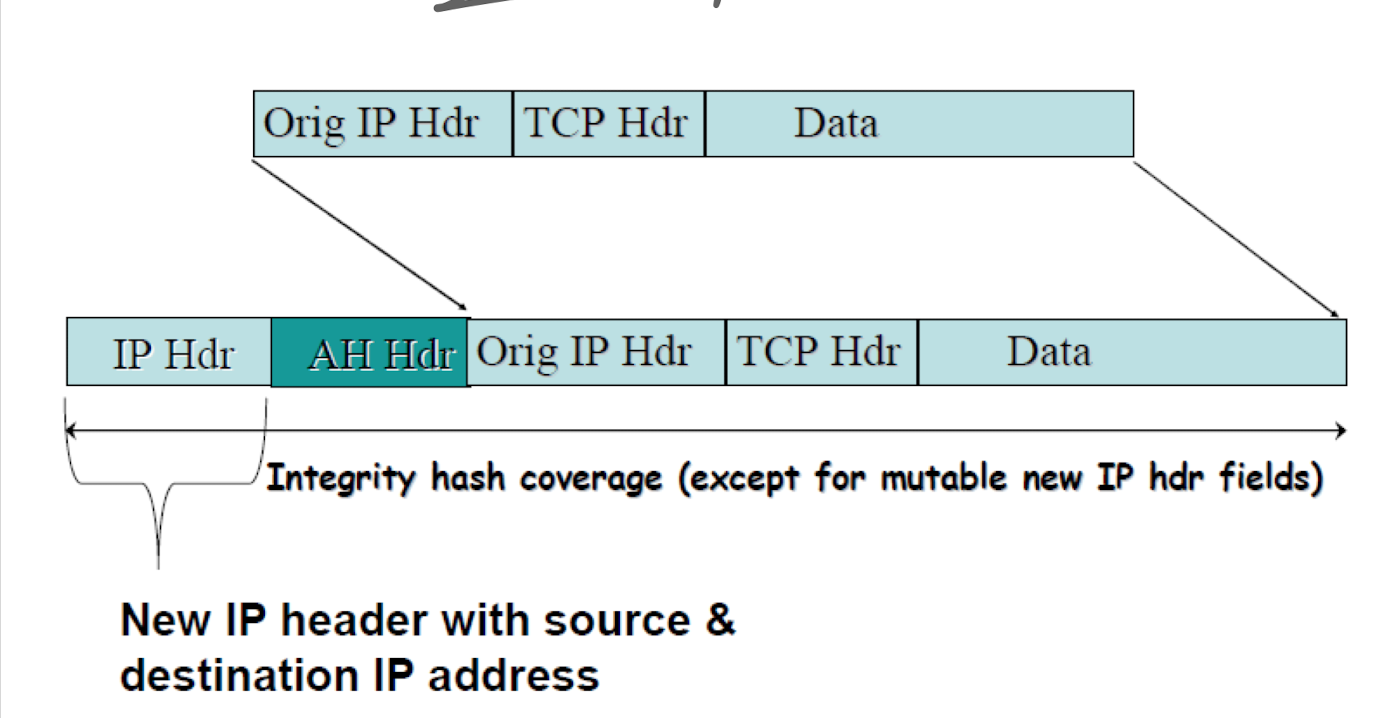
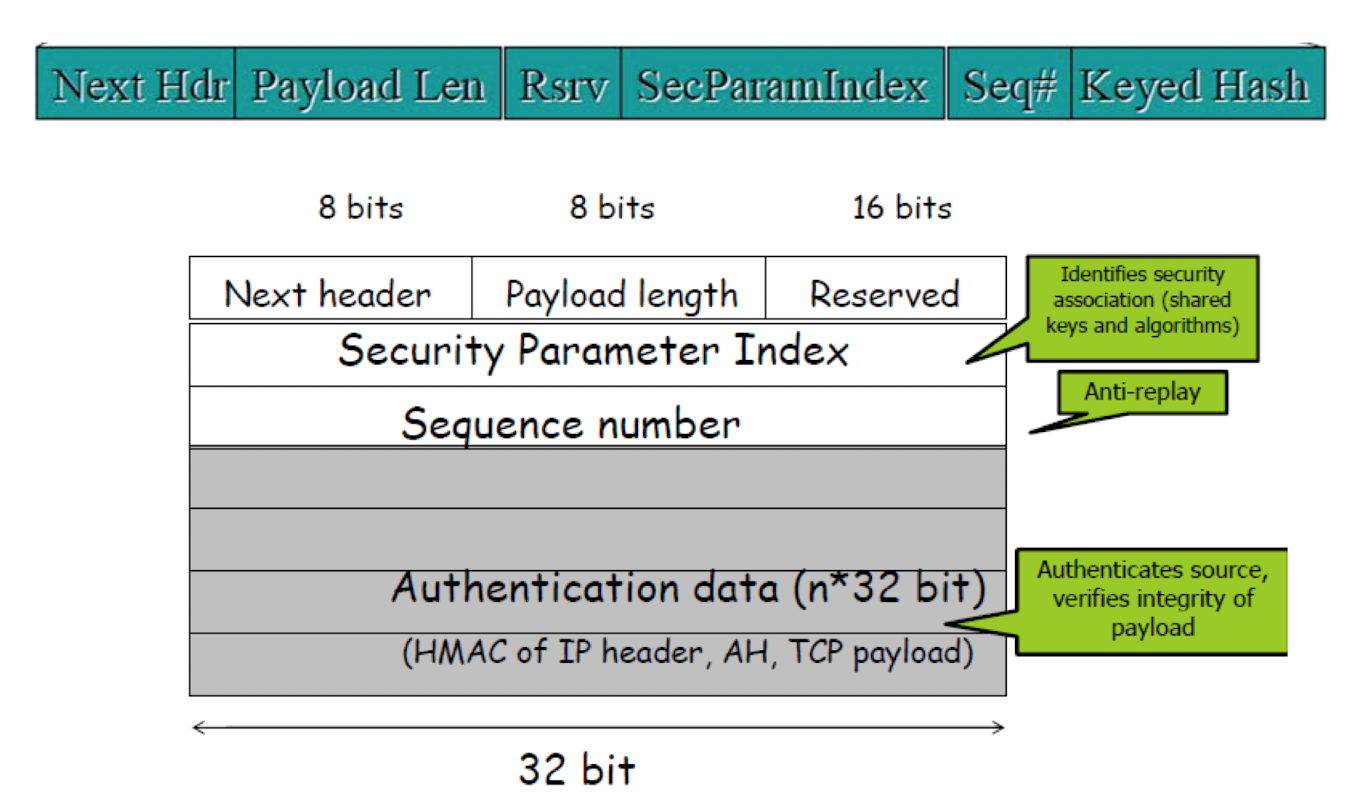
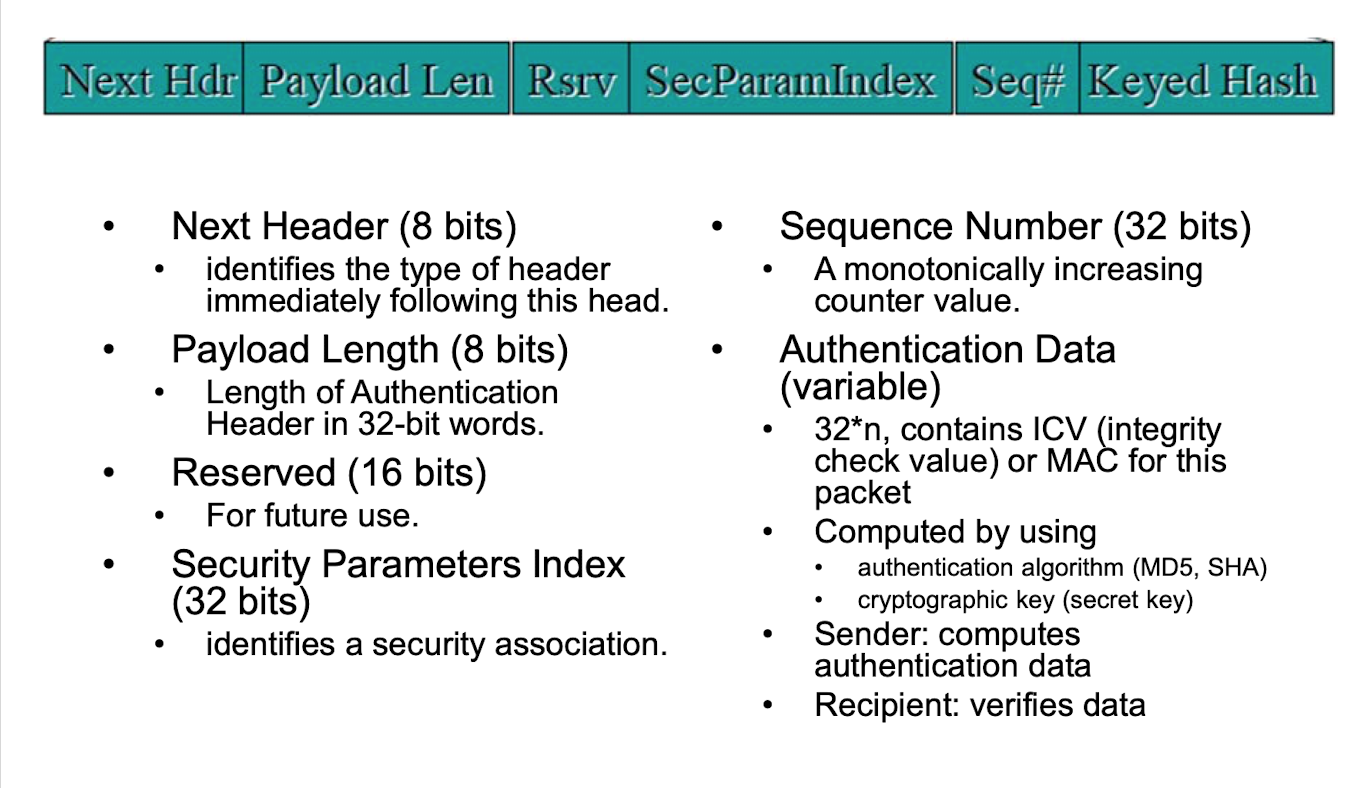
AH : Authentication Header
- 제공
- data origin authentication, connectionless data intergirity
- may 제공
- antiy-replay protection
- non-repudiation
- 제공X
- data confidentiality
- 어떻게 구현된는가가
- transport mode
- turnel mode
- transport mode
- AH header
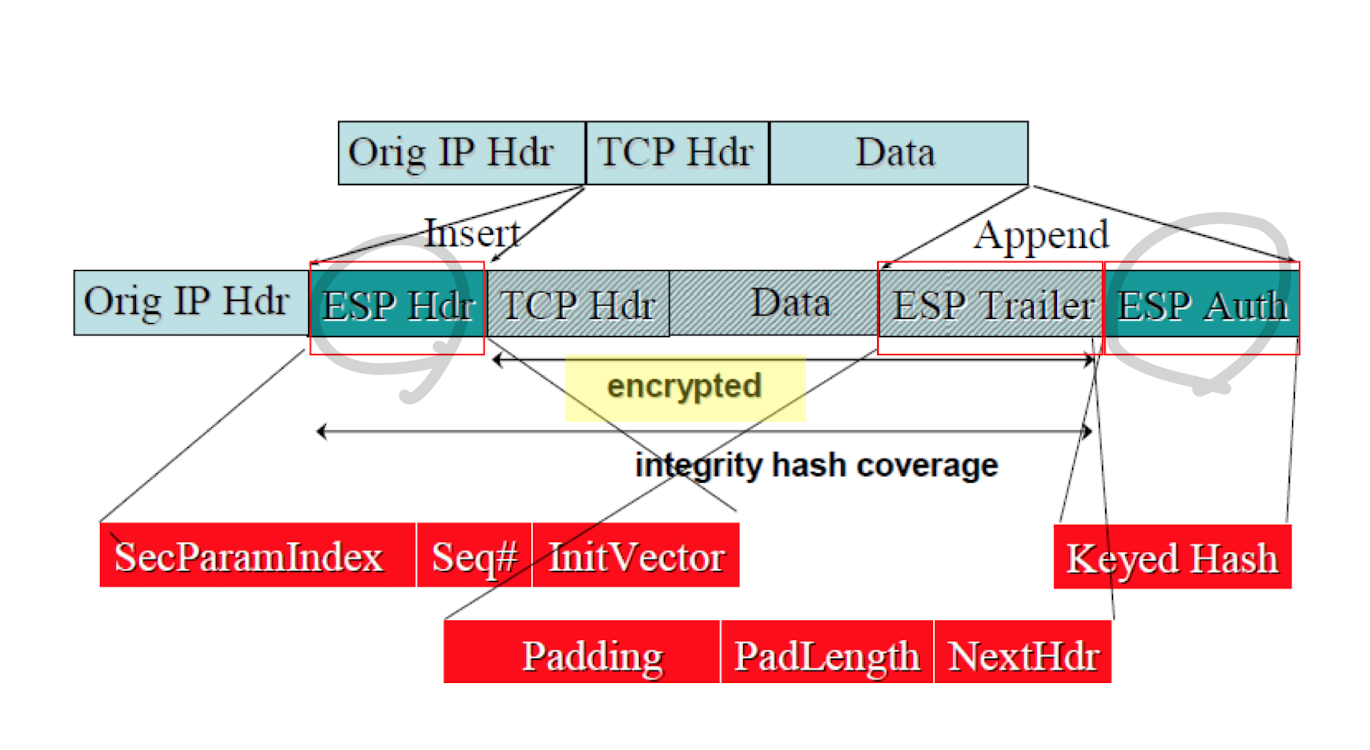
ESP : Encapsulating Security payload
- 제공
- data confidentiality
- limited traffic flow confidentiality
- anti-replay protection
-
in transport mode
-
in tunnel mode
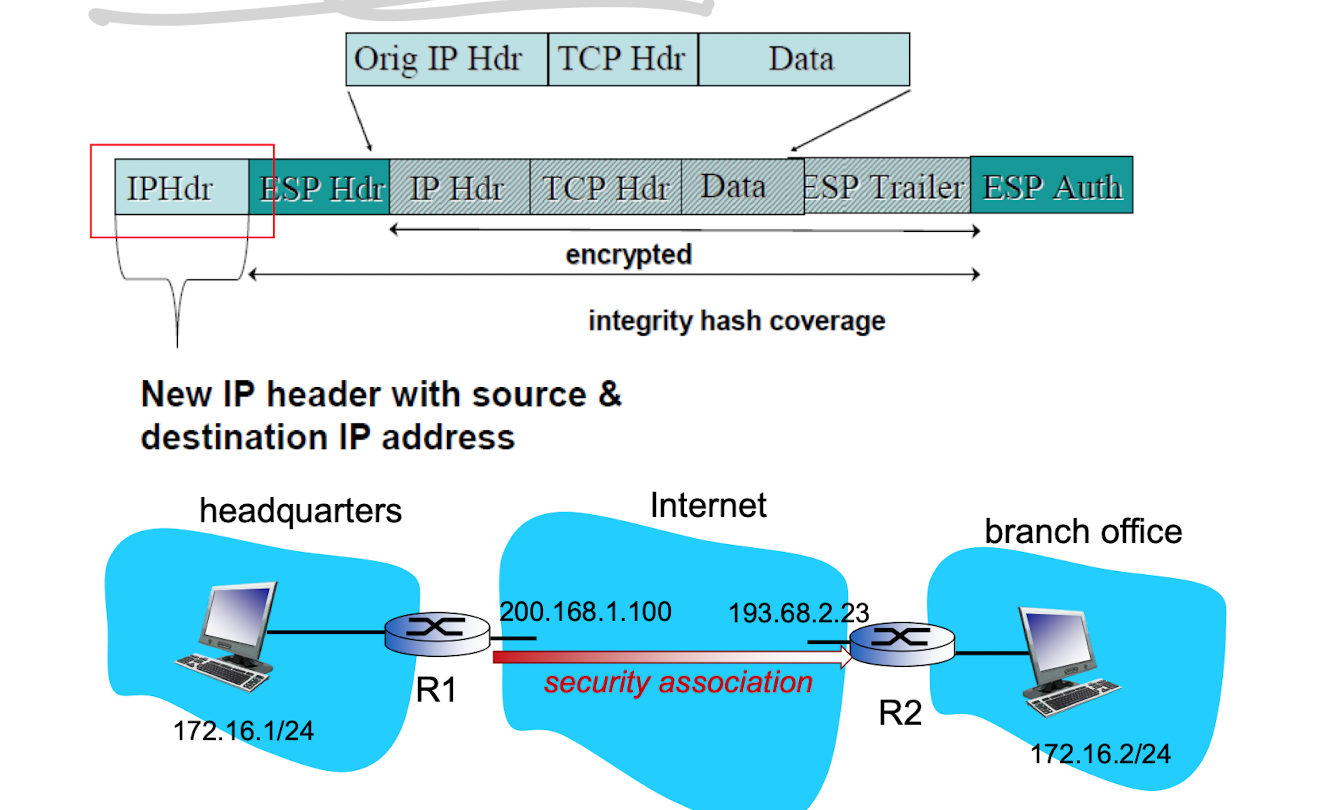
- header(not encrypted) and trailer (usually encrypted)
- heder
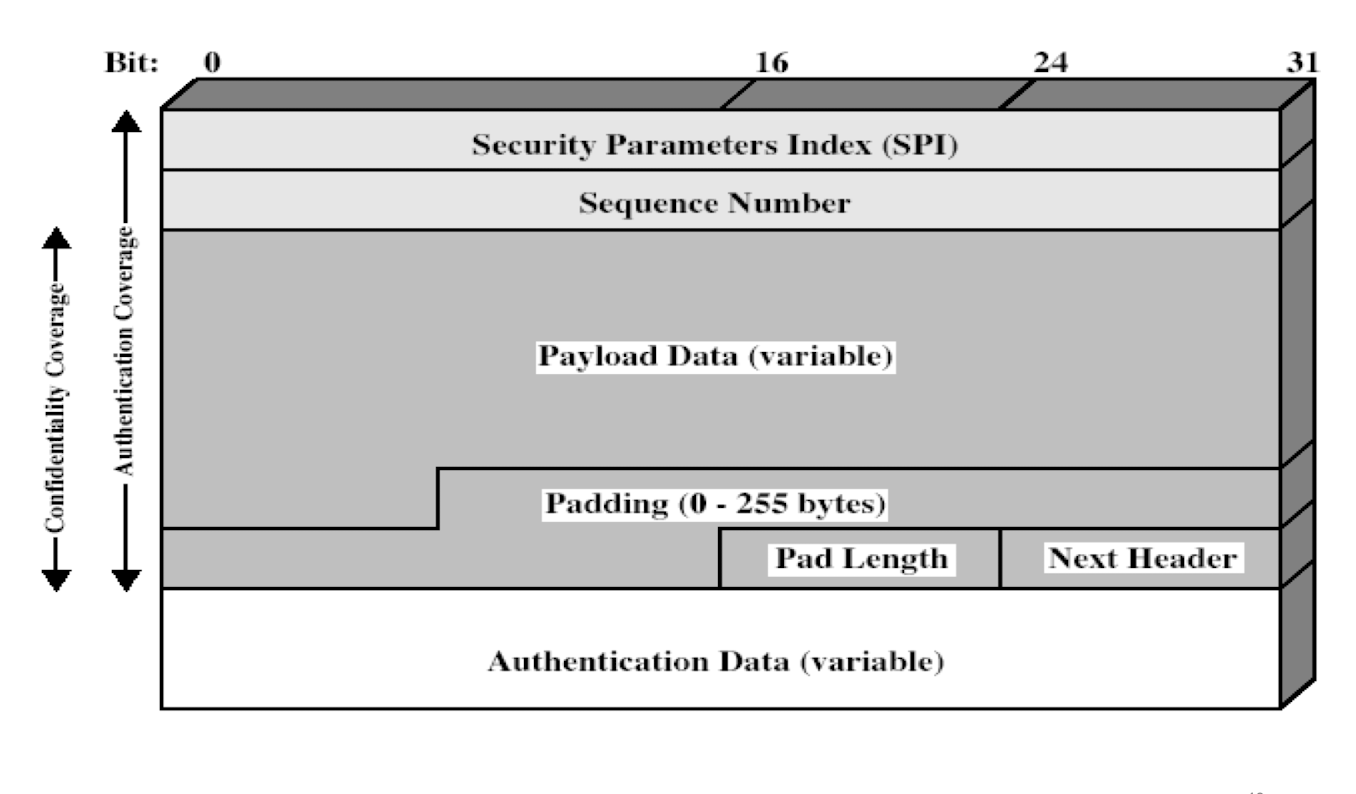
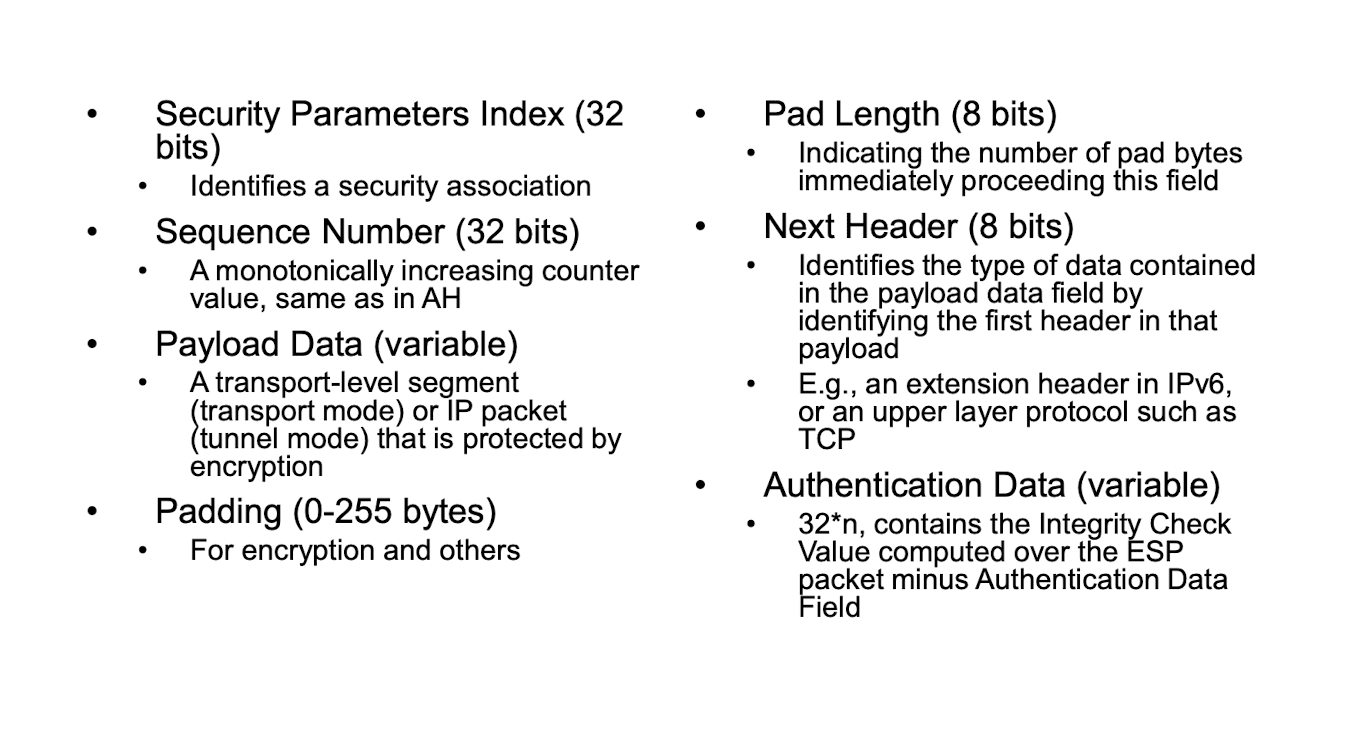
- heder
ESP <- AH
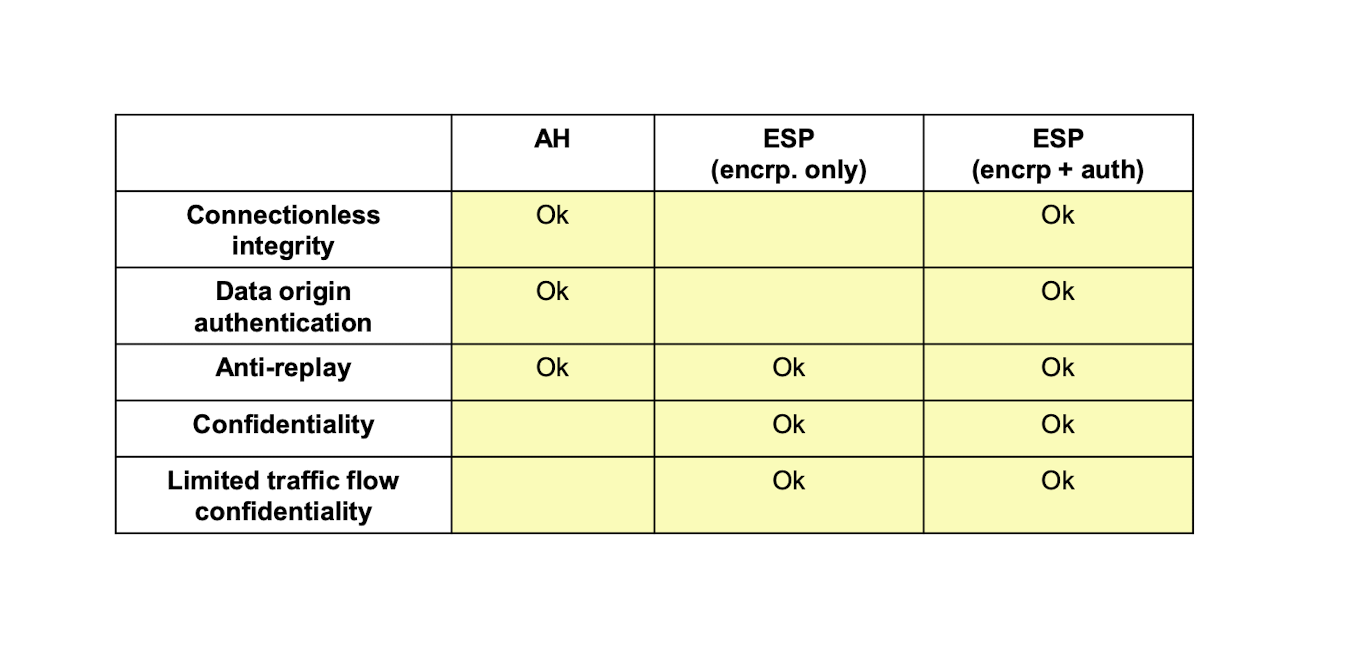
IPSec Architecture
Application
- remote login
- clinet/server
- file transfer
- web access
- etc.
benefit of IPSec
- can be transparent to end user
- no need to train user
- can provide for individiaul application
- by onfiguration, IPSec is applied to only one specified application
