🌙 CS_security
1.학기시작!

학기 : 3학년 2학기교수님 : 최봉준 교수님
2.1. Introduction - Cryptology and its objects

Security RequirementsCryptography and CryptanalysisCryptographic Toolstemper with : to change in a way that it should not to cause damage or harm정보손해의
3.1. Introduction - Basic Cryptographic Tools
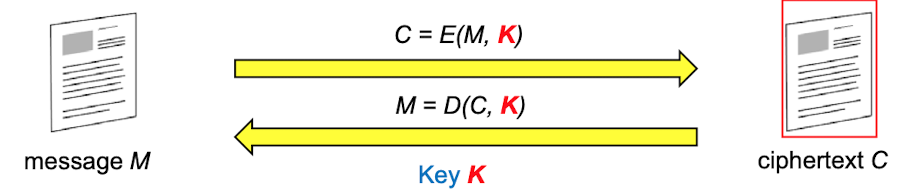
Symmetric Cryptography(Block Ciphers, Stream Ciphers)Asymmetric Cryptography(Public key)C = E(M,K)plain text message M -> Ciphertext C using an unique
4.2. History of Cryptography

🤔 many cryptographic scheme(계획/제도/책략) have 'real world analogues'e.g.) signature -> digital signitures locks and keys -> public/private key수업 ppt 그냥
5.3. Network and Systems
points and types of attacknetwork considerationsimplementation considerations (수행시 고려사항)currently, attacker's job is getting easier(all data types are
6.4. Theory of Secure Communication - part 1
get-in : btd paradox, digital signature susceptibilitymodel of secure system \- condition for perfect secrecyshannon entroyphyequivocation(모호성)perfec
7.4. Theory of Secure Communication - part 2

D = redundancy of language = R - rR = absolute rate of languager = rate of the languageex) So redundancy of english isD = R - r = 4.7 - 1.5 = 3.2 (bit
8.5. Conventional Cryptography Systems (1) - baseground
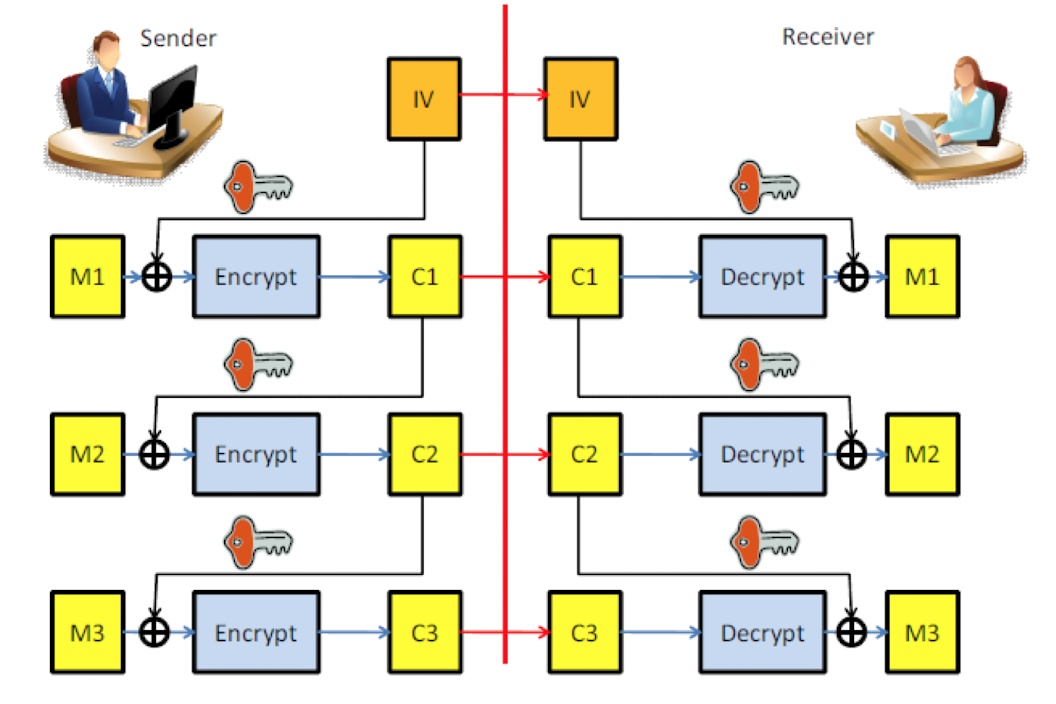
Encryption : $$C = E_K(M)$$Decryption : $$M=D_K(C)$$ConfusionM을 추론하기 어렵게 만드는것ex) 알파벳 몇칸 미루기 등Defusionplain text나 key가 ciphertext내에서 고르게 나타내도록 하는 것unco
9.5. Conventional Cryptography Systems(2) - transposition, substitution, feistel
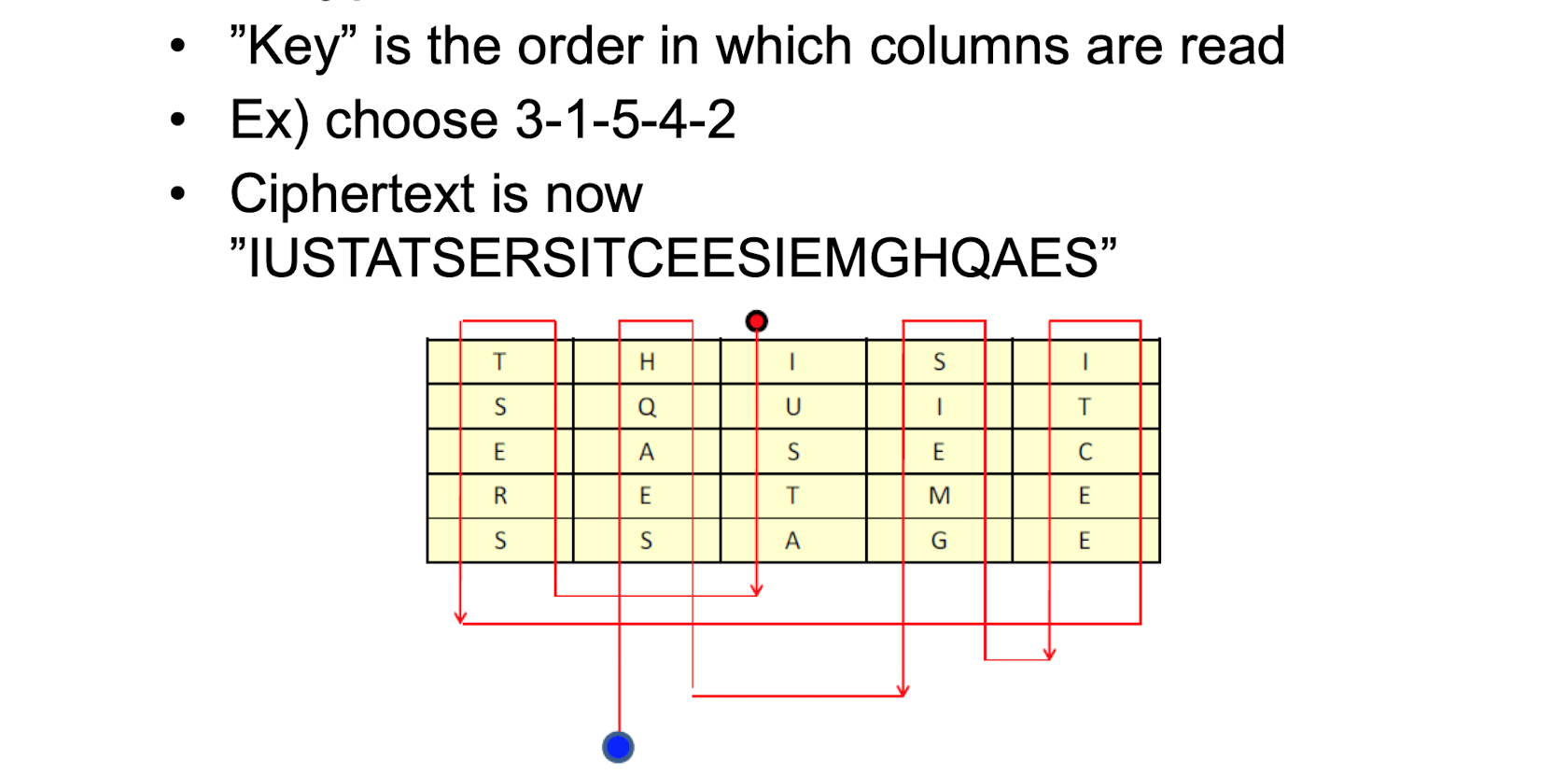
transpositionColumnnar TranspositionsubstitutionShifted Alphabetspolyalphabetic substitutionEnigmaVigenereProduct Cipherfeistel다음 파트의 DES, AES로 연결rear
10.5. Conventional Cryptography Systems(3) - DES, AES
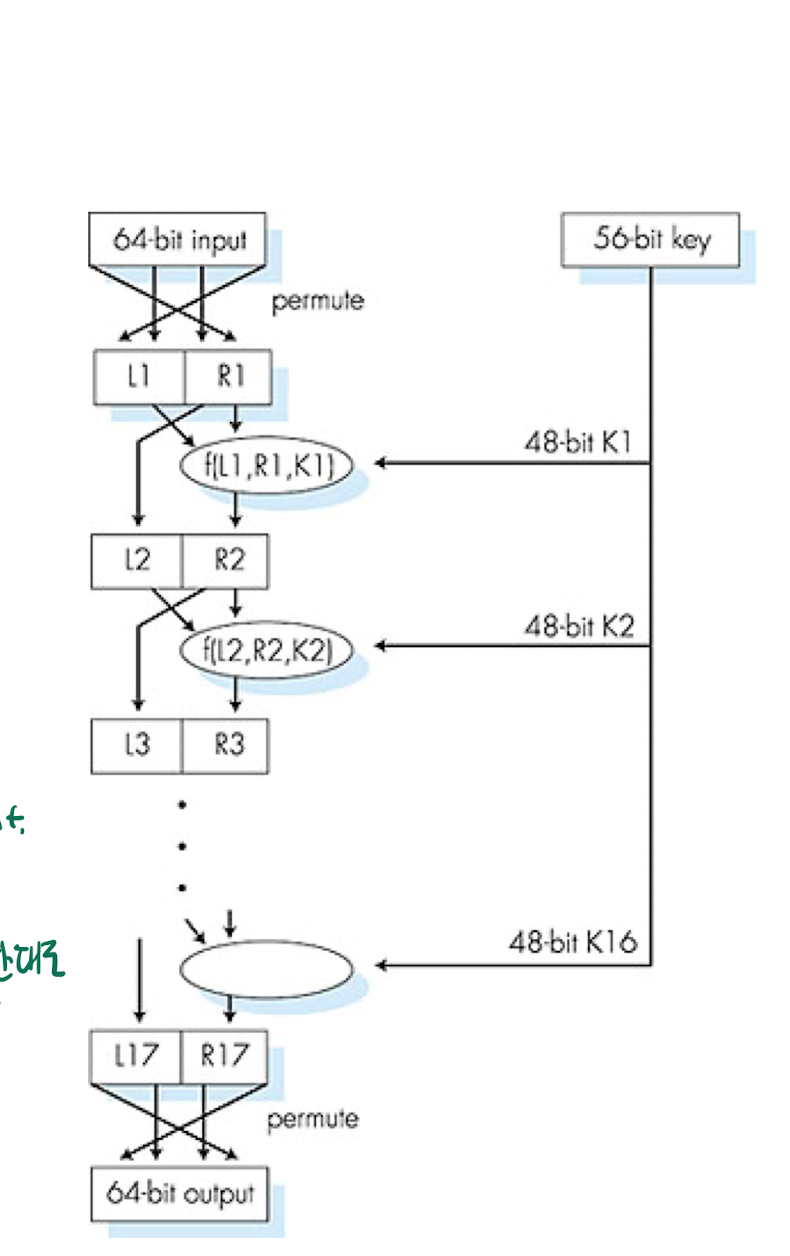
\- 기본 구조block : 64 bitkey : 56 bit\- 과정initial permutation (IP) : 초기치환. 64bit16 rounds of Feistel cipherFinal permutation (IP$$^{-1}$$)Initial key per
11.6. Basic Mathmatics for Cryptography - Euclid's Algorithm & Fermat's Little Theorem & Euler's Theorem
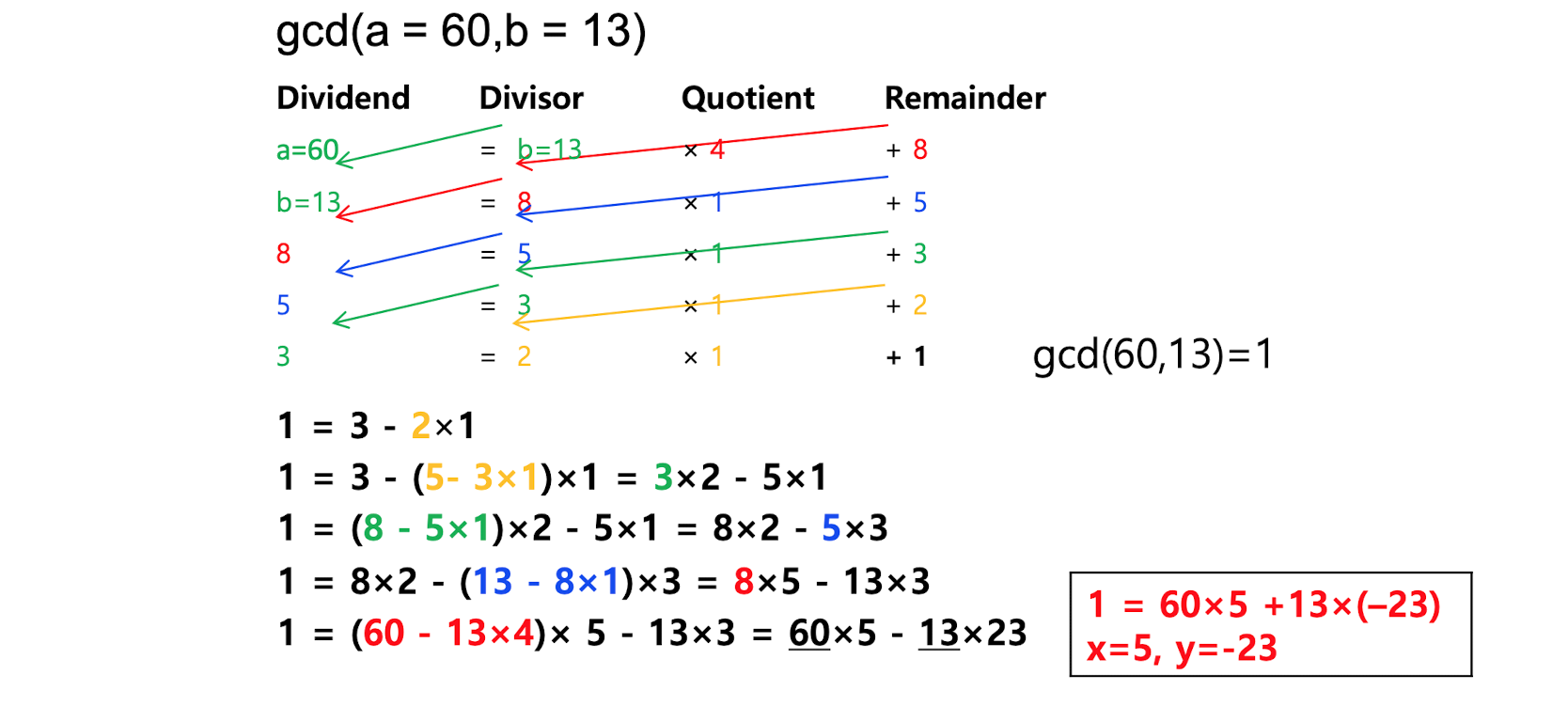
part1 greates common divisor(extended) Euclid's AlgorithmModular ArithmeticEuler's Totient FunctionFermat's TheoremEuler's Theorempart2randomnesstrue
12.6. Basic Mathmatics for Cryptography - randomness
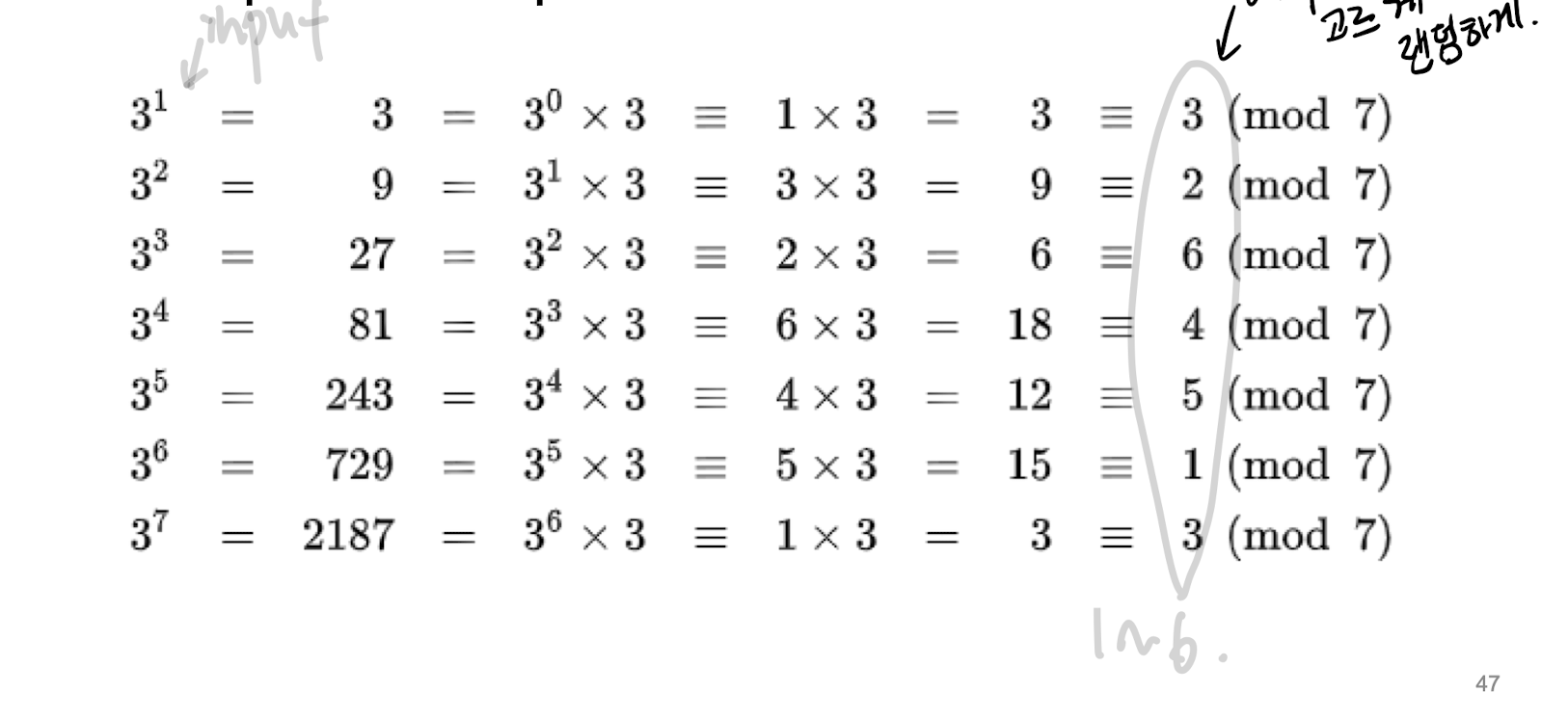
bad casenetscape secure socket layer(SSL)predictable 하다good case (true random number generators)radioactive decaythermal noisepolarization of photonst
13.7. Public Key Cryptography - RSA
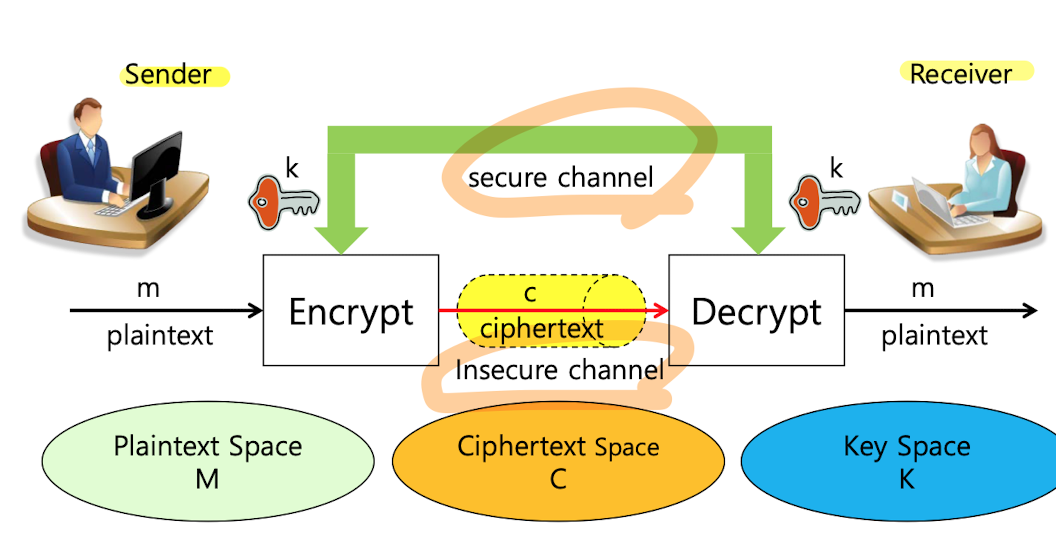
secure channel로 공통 key를 교환insecure channel로 cipertext(C)를 교환용어정리C : ciphertextM : palintext K : key단점사람이 늘어날 수록 1:1로 가지는 공통키 관리가 힘들다
14.7. Public Key Cryptography - Diffie Hellman Key Exchange
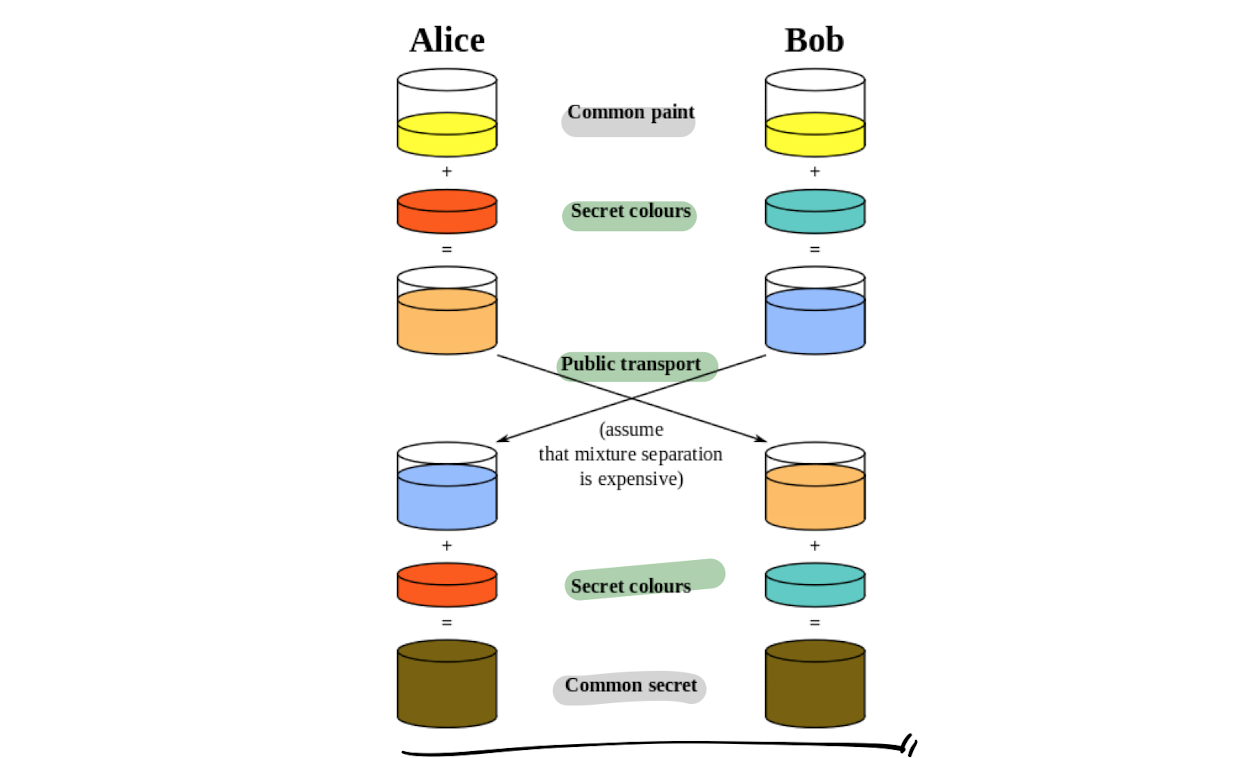
목적 안전하게 key exchage하기 위해 design 됨서로 prior knowledge가 없는 두 쪼기, shared secret key를 안전하게 주고 받기가 가능함! 근간Discrete Logarithmsgiven $$y(=x^a$$ mod $$p), x, p
15.07. Public Key Cryptography - Elgamal public key

정수 a가 있을때 $$a^n$$(mod p) 의 나머지가 모두 0이 아니라면, 이를 Primitive root라고 부른다.$$a^m = n$$ mod $$p , for 1<= n < p$$Ex) 3은 Primitive root이다 기본$$Y=g^x$$ mod
16.07. Public Key Cryptography - Digital Signature
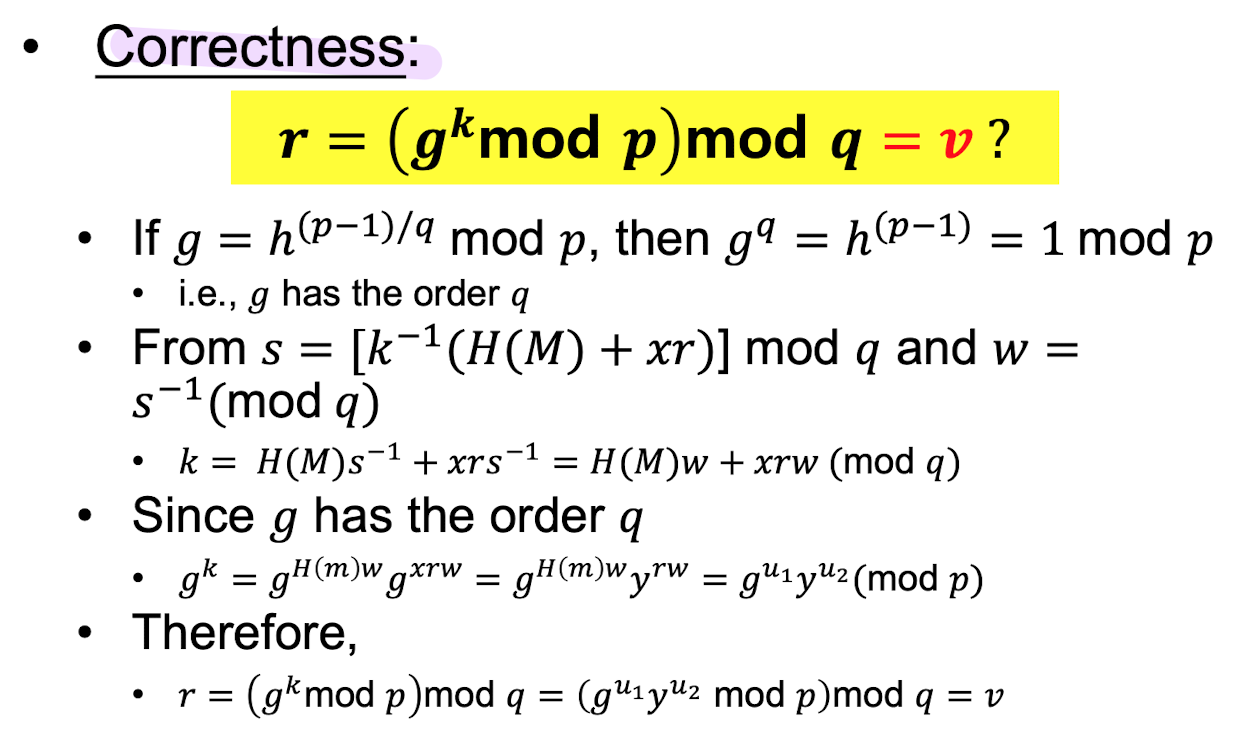
public parameter 생성p : prime number L bits ( 512 <= L <= 1024이면서 64의 배수여야 함)q : prime factor of p-1g : multiplicative order modulo p is q
17.7. Public Key Cryptography - Eliptic curve

$$y^2=x^3+ax+b$$ mod $$p$$(a, b) = curve모양을 결정하는 상수p = prime numG = generator. base point.n = order of point G맨 처음엔 doubling을 사용해야한다. n=151처럼 큰 경우는? -
18.10. standard and applications - Basic Security Protocols (network layer : IPSec)
network layer securityIP security Transport Layer Security(SSL) Secure Socket Layer(TLS) Transport Layer SecurityOperational SecurityFirewall(IDS) Int
19.10. standard and applications - Basic Security Protocols (Transport layer - SSL, TLS)
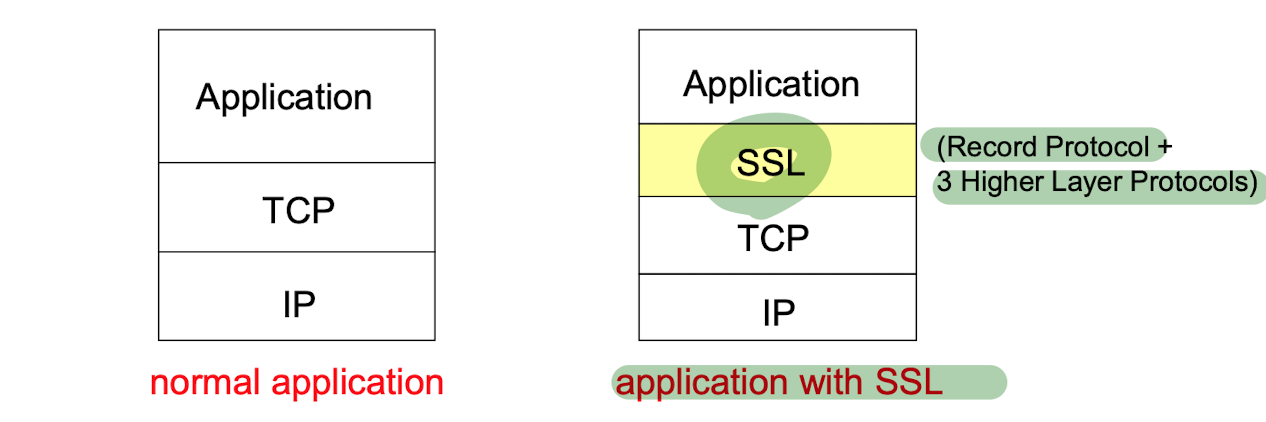
Transport Layerprocess-process data transfer보안 종류SSL (secure socket layer)TLS (transport layer security)특징 TCP 사용구조구성요소SSL Record Protocolmessage inte
20.10. standard and applications - Basic Security Protocols (operational security : firewall, intruders)
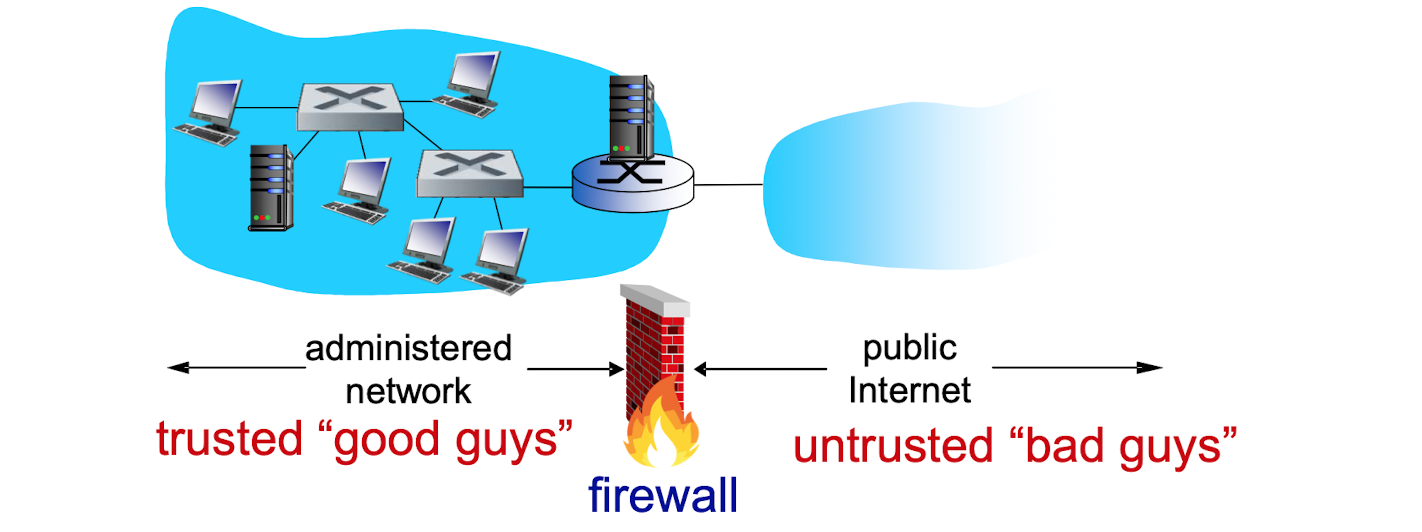
firewall(IDS) intrusion detection system what firewall can dodefine a 'single choke point'keeps unauthorized users out of the protected nteworkprohibi
22.10. Standards and Applications - Distributed System Security Protocols
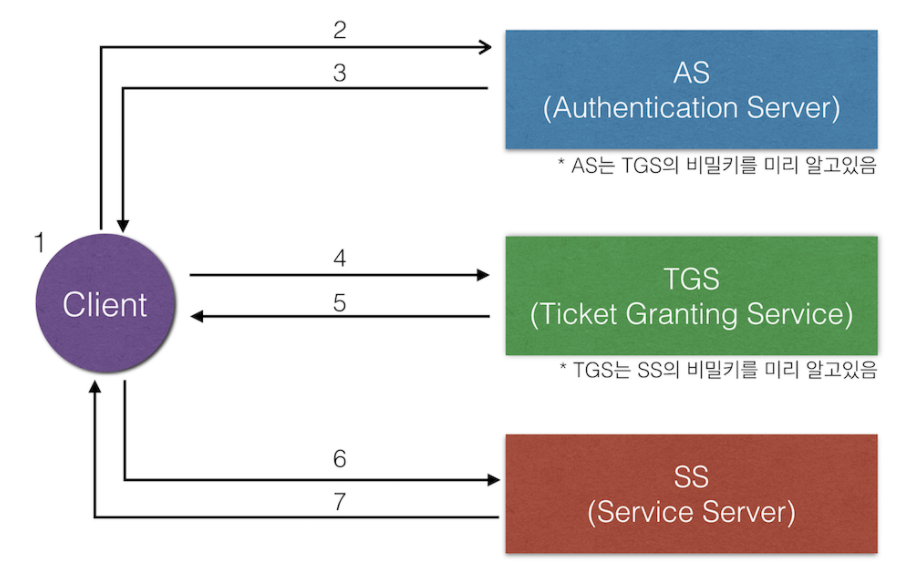
Security Issues in distributed systemsimpersonation of userimpersonation of workstation여기 정리 잘되어있음
23.12. Advanced Crptographic Techniques : Secrete Sharing

k-out-of-n encryptionpadlock들을 다 풀어야만, keyhole에 reach 가능secret sharing insights1\. It is easier to trust the many than the few2\. we like to have redu
24.12. Advanced Cryptographic Techniques : Privacy Preserving Protocols
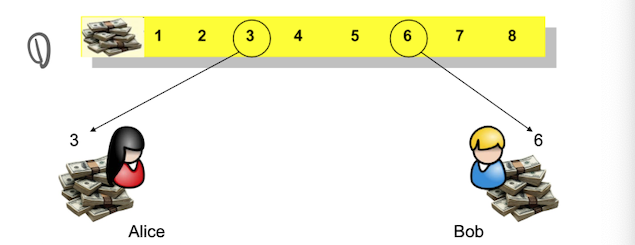
A와 B가 서로 재산을 알리지 않고, 누가 더 재산이 많은지 판단 하려고 한다. initializeAlice는 A={A1, A2, ...}Bob는 B={B1, B2,...}를 만든다. Alice는 RSA를 위해 public key (n,e)와 Private key d를