What is OAuth2.0?
OAuth 2.0 is an open standard authorization framework that allows third-party applications to access user data from a server on behalf of the user without requiring the user to share their credentials (such as username and profile) with the third-party applications. And here, the third-party application implies our service. It provides a secure and standardized method for user authentication and authorization in web and mobile applications.
OAuth 1.0 vs OAuth 2.0
OAuth 1.0 and OAuth 2.0 are both user authentication and authorization protocols, but they have key differences.
-
OAuth 1.0: It uses signed requests for security, ensuring authentication and integrity. The flow involves generating and signing each request, making it more complex.
-
OAuth 2.0: It simplifies the security model by using TLS/SSL for communication and providing a token-based approach. It offers flexibility and scalability, supporting various authentication methods and custom authorization processes. OAuth 2.0 also enhances the user experience and provides a more concise flow.
Terminology
-
Client : The application that requires access to data or permissions.
-
Authorization Server : The server that authenticates the resource owner. Users interact with the authorization server when granting permission to the client. The authorization server prompts users to grant access to their account.
-
Resource Server : The server or API that stores the user's data, which the client app accesses. The resource server validates access tokens and grants access to requested data if the user has authorized it.
-
Redirect URI : The URI to which the authorization server redirects the resource owner after granting permission. Also known as the callback URI.
-
Response Type : Specifies the type of response expected by the client. It informs the authorization server about the desired authorization flow. The common response type is 'code'.
-
Scope : Granular permissions that the client app requests. Applications can request one or more scopes. The scope values are not standardized and depend on the service's internal architecture.
-
Client ID : A unique identifier for the client app.
-
Authorization Code : A short-lived code sent by the authorization server to the client. The client exchanges this code, along with the client secret, for an access token.
-
Access Token : A key used by the client app to make API requests on behalf of the user. It allows the application to access specific user data. The format of access tokens is not standardized in OAuth 2.0, but JSON Web Token (JWT) format is commonly used. Access tokens may have expiration dates for security reasons.
-
Refresh Token : An optional token that can be issued alongside the access token. The refresh token can be used by the client to obtain a new access token without requiring the user to re-authenticate. It provides a way to maintain continuous access to the user's resources.
How OAuth2.0 works?
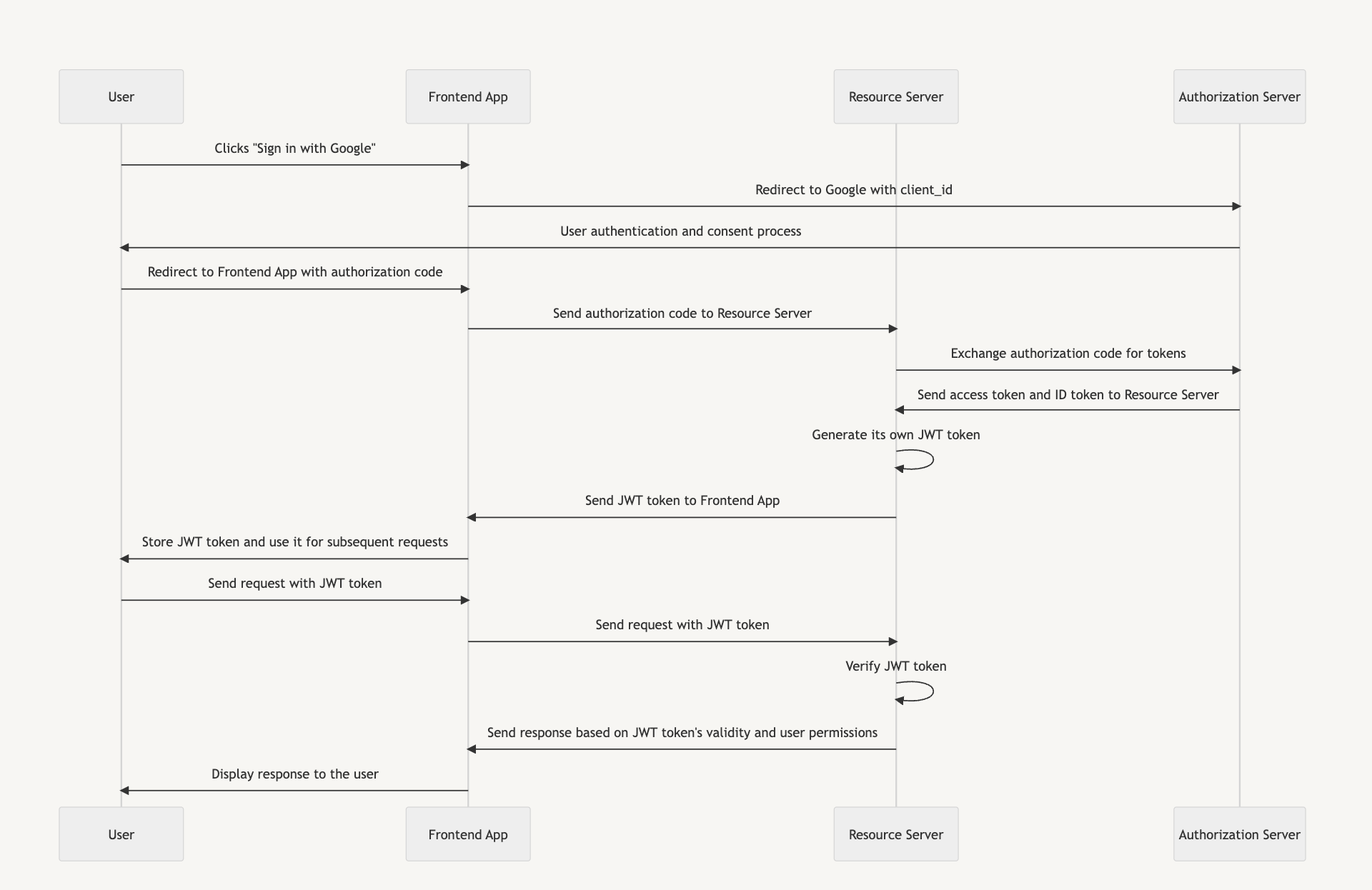
Authorization Code Flow
The Authorization Code Flow is typically used in server-side applications, where the client application can securely store a client secret. It involves the following steps:
- The client application initiates the OAuth flow by redirecting the user to the authorization server.
- The user interacts with the authorization server, authenticates themselves, and grants permission to the client application.
- After granting permission, the authorization server redirects the user back to the client application, providing an authorization code.
- The client application takes the received authorization code and exchanges it with the authorization server for an access token and, optionally, a refresh token.
- With the obtained access token, the client application is now authorized to access the user's resources on the resource server.
In the Authorization Code Flow, the authorization code serves as an intermediate step to obtain the access token. It enhances security by keeping the access token confidential between the client application and the authorization server.
Pros and Cons
Advantages of OAuth 2.0:
-
Enhanced User Experience: OAuth 2.0 enables users to grant limited access to their data without sharing sensitive credentials. This enhances user experience by providing a seamless and secure way to authorize third-party applications.
-
Scalability: OAuth 2.0 is highly scalable and can handle a large number of users and clients. It allows for the delegation of authentication and authorization responsibilities to specialized servers, making it suitable for distributed systems.
-
Security: OAuth 2.0 utilizes access tokens to grant permissions, reducing the exposure of user credentials. Additionally, the use of refresh tokens and token expiration enhances security by limiting the lifetime of access.
-
Standardization: OAuth 2.0 is an open standard, widely adopted and supported by major platforms and service providers. This standardization promotes interoperability and simplifies integration for developers.
Disadvantages of OAuth 2.0:
-
Complexity: The OAuth 2.0 protocol can be complex to implement, especially for developers who are new to the framework. The various flows, tokens, and endpoints require careful consideration and can introduce complexities during development.
-
Lack of Granularity: OAuth 2.0 scopes define the permissions granted to clients, but the granularity of scopes varies across different service providers. This inconsistency can limit the fine-grained control of access to user resources.
-
Trust Dependency: OAuth 2.0 relies on trust between the authorization server, client applications, and resource servers. If any of these components are compromised or misconfigured, it can lead to security vulnerabilities.
-
Token Management: Proper management of access tokens and refresh tokens is crucial. Mishandling or inadequate protection of tokens can result in unauthorized access to user data.
While OAuth 2.0 has its limitations, its advantages in terms of user experience, scalability, security, and standardization make it a widely adopted and trusted framework for enabling secure and controlled access to user data in web and mobile applications.
Incorporating OAuth 2.0 into your application requires careful consideration of its strengths and weaknesses, and implementation best practices to ensure a secure and seamless user experience.

